Father
Professional
- Messages
- 2,602
- Reaction score
- 837
- Points
- 113
Literally every Microsoft Office user is in danger. How do I protect my devices from hacking?
A very worrying situation is brewing in the world of cybersecurity. A hacker under the pseudonym "Cvsp" on one of the cybercrime forums announced the sale of an RCE exploit for a zero-day vulnerability in Microsoft Outlook.
According to the hacker, this exploit allows remote code execution and is guaranteed to work on Microsoft Office 2016, 2019, LTSC 2021 and Microsoft 365 Apps for Enterprise. The tests allegedly showed a 100% success rate, which indicates the high reliability and effectiveness of the exploit in compromising vulnerable systems.
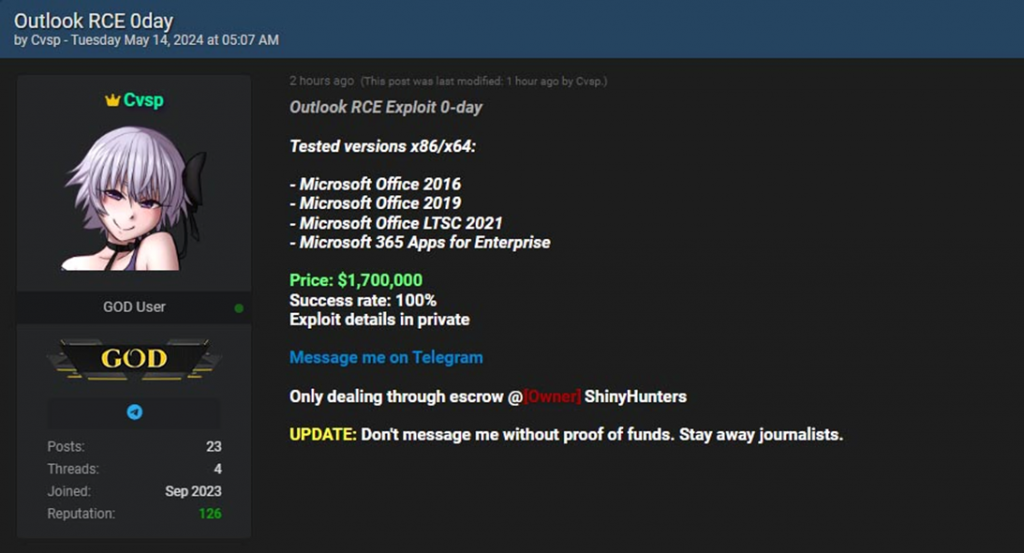
Information about the exploit itself will only be disclosed in private, which emphasizes its secrecy. The attacker said that the transaction will be conducted exclusively through the ShinyHunters escrow service, and asked journalists and other "random passers - by" to stay away.
The price for the exploit is $1,700,000, which at the current exchange rate is almost 156 million rubles. Such an impressive amount reflects the severity of the vulnerability identified by hackers, as well as the potential damage that can be caused to users.
Cybersecurity experts are already expressing serious concerns about the possible consequences. Given that the vulnerability concerns popular office programs installed on almost everyone's computer, many large companies and home users may be at risk of being hacked.
Since information about the vulnerability and how it is used is transmitted privately, it is now extremely difficult to determine in which direction cyber experts should direct their attention in order to quickly identify the breach.
Users are advised to be especially vigilant in this situation: follow the latest news about this vulnerability, do not run any suspicious files, especially those received by email, and regularly check for updates to Microsoft Office in order to protect their systems as soon as possible when the fix becomes available.
A very worrying situation is brewing in the world of cybersecurity. A hacker under the pseudonym "Cvsp" on one of the cybercrime forums announced the sale of an RCE exploit for a zero-day vulnerability in Microsoft Outlook.
According to the hacker, this exploit allows remote code execution and is guaranteed to work on Microsoft Office 2016, 2019, LTSC 2021 and Microsoft 365 Apps for Enterprise. The tests allegedly showed a 100% success rate, which indicates the high reliability and effectiveness of the exploit in compromising vulnerable systems.

Information about the exploit itself will only be disclosed in private, which emphasizes its secrecy. The attacker said that the transaction will be conducted exclusively through the ShinyHunters escrow service, and asked journalists and other "random passers - by" to stay away.
The price for the exploit is $1,700,000, which at the current exchange rate is almost 156 million rubles. Such an impressive amount reflects the severity of the vulnerability identified by hackers, as well as the potential damage that can be caused to users.
Cybersecurity experts are already expressing serious concerns about the possible consequences. Given that the vulnerability concerns popular office programs installed on almost everyone's computer, many large companies and home users may be at risk of being hacked.
Since information about the vulnerability and how it is used is transmitted privately, it is now extremely difficult to determine in which direction cyber experts should direct their attention in order to quickly identify the breach.
Users are advised to be especially vigilant in this situation: follow the latest news about this vulnerability, do not run any suspicious files, especially those received by email, and regularly check for updates to Microsoft Office in order to protect their systems as soon as possible when the fix becomes available.

