Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
Make sure that your Google Firebase is properly configured to avoid leaking personal information.
Due to an error in the Google Firebase configuration, sensitive data from at least 900 sites, including users ' personal information, became publicly available on the Internet.
In total, at least 125 million user records were found to be publicly available. Among the leaked data were payment information and passwords in clear text.
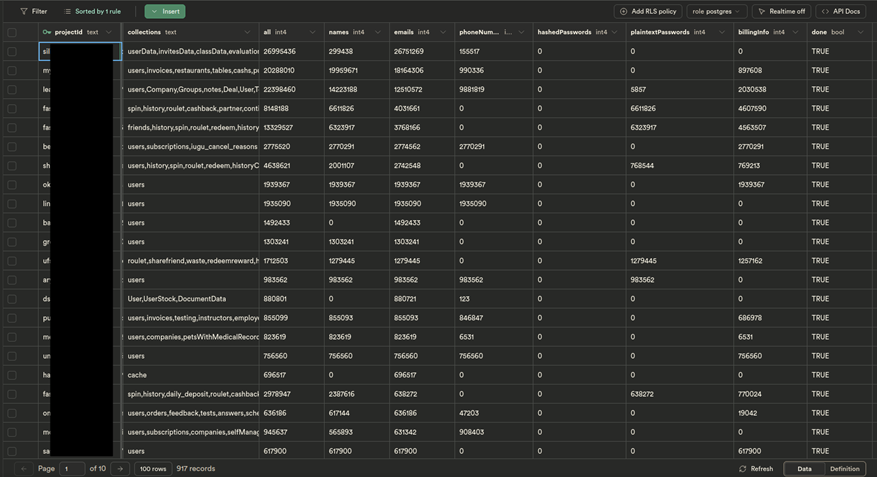
The env research team.fail used the scan tool to detect incorrectly configured Firebase databases for 2-3 weeks, checking 5.2 million domains. As a result, open data was found on more than 900 sites, including:
The researchers also notified 842 site owners about the problems they found, of which only 202 (24%) fixed the incorrect configuration. However, only 8 site owners responded to the notifications, and only 2 owners offered a reward for detecting the vulnerability.
Google Firebase, a popular cloud storage service, offers a set of security rules to protect your data. However, in practice, this is not the first time that problems arise with incorrect configuration of rules. Past incidents have included data leaks from 4,000 Android apps due to bugs in the Firebase implementation.
Problems of this kind have long been common for cloud services, including Amazon AWS, until the company decided to simplify the task of secure default configuration for customers. However, according to OWASP, misconfiguration of security is still among the top five most common vulnerabilities, which highlights the need to raise awareness of security issues among web resource owners.
Due to an error in the Google Firebase configuration, sensitive data from at least 900 sites, including users ' personal information, became publicly available on the Internet.
In total, at least 125 million user records were found to be publicly available. Among the leaked data were payment information and passwords in clear text.

The env research team.fail used the scan tool to detect incorrectly configured Firebase databases for 2-3 weeks, checking 5.2 million domains. As a result, open data was found on more than 900 sites, including:
- 85 million names;
- 106 million email addresses;
- 34 million phone numbers;
- 20 million passwords;
- 27 million payment details.
The researchers also notified 842 site owners about the problems they found, of which only 202 (24%) fixed the incorrect configuration. However, only 8 site owners responded to the notifications, and only 2 owners offered a reward for detecting the vulnerability.
Google Firebase, a popular cloud storage service, offers a set of security rules to protect your data. However, in practice, this is not the first time that problems arise with incorrect configuration of rules. Past incidents have included data leaks from 4,000 Android apps due to bugs in the Firebase implementation.
Problems of this kind have long been common for cloud services, including Amazon AWS, until the company decided to simplify the task of secure default configuration for customers. However, according to OWASP, misconfiguration of security is still among the top five most common vulnerabilities, which highlights the need to raise awareness of security issues among web resource owners.

