Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
Scammers once again targeted gullible users. How not to become their victim?
This is not the first time that fraudulent cryptocurrency wallets disguised as well-known brands have appeared in Canonical's popular Snap Store Linux app store. Earlier, in February of this year, security researchers have already recorded the appearance of similar fake applications. With their help, the attackers managed to steal about 490 thousand dollars in bitcoins from gullible users.
This time, ten fake wallets were uploaded to the Snap Store at once, imitating such popular applications as Exodus, Polygon, Metamask, Tronlink, etc. All of them were published by a dubious publisher with the code name "digisafe00000", but were later republished again from the account"codeshield0x0000".

One of these applications under the identifier "exodus-build-96567" was reviewed in detail by independent researcher Alan Pope. The app disguises itself as a real Exodus wallet, promising users safe storage and exchange of various cryptocurrencies in one user-friendly interface.
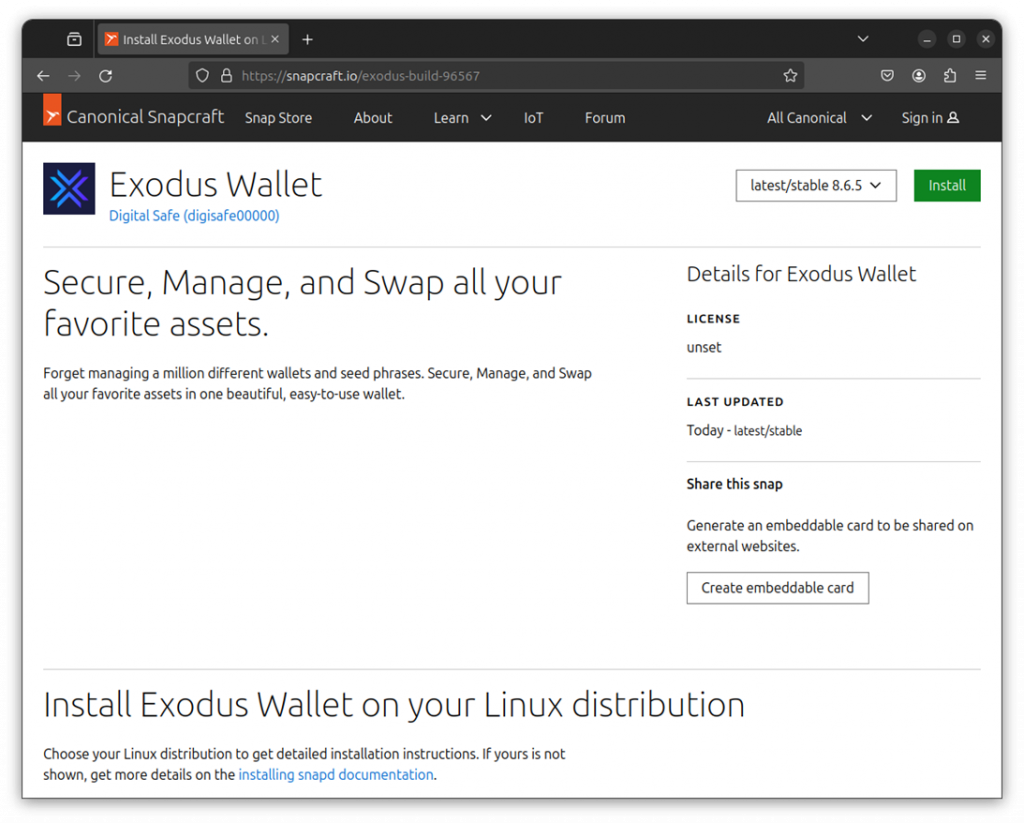
The creators of the fraudulent program did their best, imitating the official app store and using attractive descriptions. "Forget about managing a million different wallets and paraphrases. Securely store, manage and exchange all your favorite assets in one beautiful and easy-to-use wallet," the ad read.
However, to trust these statements was fraught with the most unfortunate consequences. When trying to create a new wallet, the app returned an error, but if you enter a phrase to restore an existing wallet, this critical data was immediately sent to the remote server of fraudsters.
A thorough analysis of the malicious app's code revealed a built-in dictionary containing thousands of valid words used as phrases for recovering crypto wallets. If you entered a valid phrase of 12, 18, or 24 words, this information was immediately transmitted to the attackers via an HTTP request, which allowed them to gain full access to the victim's funds.
Moreover, the fraudulent application periodically pinged the remote server, sending it the specific name of the installed program. This is probably how attackers tracked active users for further attacks or collecting statistics.
After the incident was discovered, the Canonical team was notified, and the fake wallets were promptly removed. However, this victory was only temporary. Just a day later, the fake apps returned, but under a new account (the aforementioned "codeshield0x0000").
Thus, the fight against such applications can continue forever, but the most reasonable solution would be to tighten the verification of applications published in the official Canonical store, especially if these applications are closely related to cryptocurrency and finance.
In the modern world, cybercriminals do not slumber, improving their methods of deception every day. Therefore, it is vital for users to remain vigilant, download programs only from completely trustworthy sources, and never transfer critical data to questionable services.
This is not the first time that fraudulent cryptocurrency wallets disguised as well-known brands have appeared in Canonical's popular Snap Store Linux app store. Earlier, in February of this year, security researchers have already recorded the appearance of similar fake applications. With their help, the attackers managed to steal about 490 thousand dollars in bitcoins from gullible users.
This time, ten fake wallets were uploaded to the Snap Store at once, imitating such popular applications as Exodus, Polygon, Metamask, Tronlink, etc. All of them were published by a dubious publisher with the code name "digisafe00000", but were later republished again from the account"codeshield0x0000".

One of these applications under the identifier "exodus-build-96567" was reviewed in detail by independent researcher Alan Pope. The app disguises itself as a real Exodus wallet, promising users safe storage and exchange of various cryptocurrencies in one user-friendly interface.

The creators of the fraudulent program did their best, imitating the official app store and using attractive descriptions. "Forget about managing a million different wallets and paraphrases. Securely store, manage and exchange all your favorite assets in one beautiful and easy-to-use wallet," the ad read.
However, to trust these statements was fraught with the most unfortunate consequences. When trying to create a new wallet, the app returned an error, but if you enter a phrase to restore an existing wallet, this critical data was immediately sent to the remote server of fraudsters.
A thorough analysis of the malicious app's code revealed a built-in dictionary containing thousands of valid words used as phrases for recovering crypto wallets. If you entered a valid phrase of 12, 18, or 24 words, this information was immediately transmitted to the attackers via an HTTP request, which allowed them to gain full access to the victim's funds.
Moreover, the fraudulent application periodically pinged the remote server, sending it the specific name of the installed program. This is probably how attackers tracked active users for further attacks or collecting statistics.
After the incident was discovered, the Canonical team was notified, and the fake wallets were promptly removed. However, this victory was only temporary. Just a day later, the fake apps returned, but under a new account (the aforementioned "codeshield0x0000").
Thus, the fight against such applications can continue forever, but the most reasonable solution would be to tighten the verification of applications published in the official Canonical store, especially if these applications are closely related to cryptocurrency and finance.
In the modern world, cybercriminals do not slumber, improving their methods of deception every day. Therefore, it is vital for users to remain vigilant, download programs only from completely trustworthy sources, and never transfer critical data to questionable services.

