Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
Now you need to be vigilant, even if you go to the sites of federal services.
Lookout reports that the new CryptoChameleon phishing kit has become a tool for attacks on employees of the Federal Communications Commission( FCC), during which the fake Okta authentication system is used.
The campaign targets users and employees of cryptocurrency platforms, including Binance, Coinbase, Kraken, and Gemini, using phishing pages that mimic Okta, Gmail, iCloud, Outlook, X, Yahoo, and AOL.
Attackers organize sophisticated phishing and social engineering attacks that involve interaction via email, SMS, and voice phishing (vishing) to trick victims into entering confidential information on fake pages – usernames, passwords, and even passport photos.
Attackers prepare an attack by first registering domains that are very similar to the domains of legitimate sites. For example, for the FCC, they created the domain "fcc-okta [.] com", which differs by only one character from the actual FCC Single Sign-On (SSO) page via Okta.
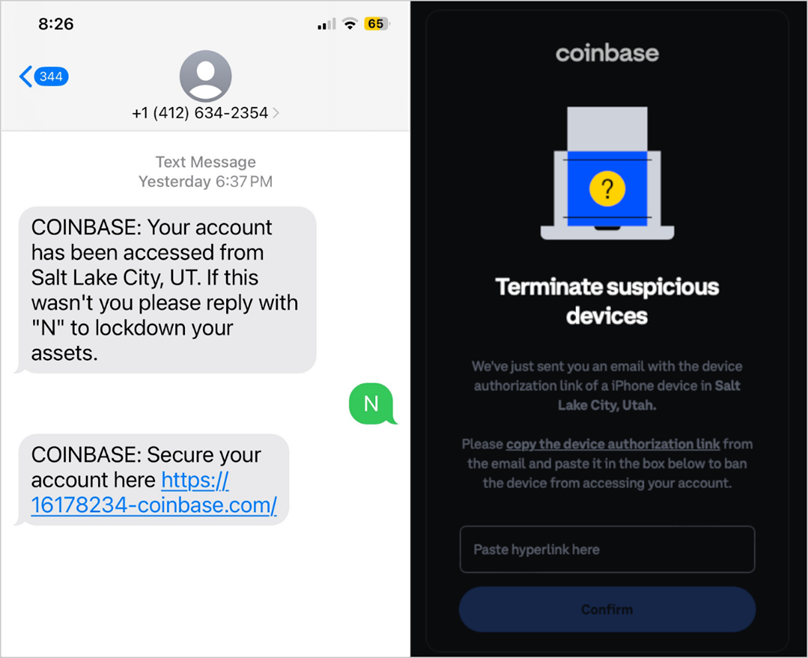
Phishing SMS message (left) and fake page (right)
Attackers can call, email, or TEXT targets pretending to be customer support, and direct them to a phishing site to "restore" their accounts. On the scam site, the victim is met with a CAPTCHA, which, according to Lookout, serves as bot filtering, and also adds credibility to the process. After completing the CAPTCHA, the user sees a well-designed phishing page that looks like an exact copy of the real Okta login page.
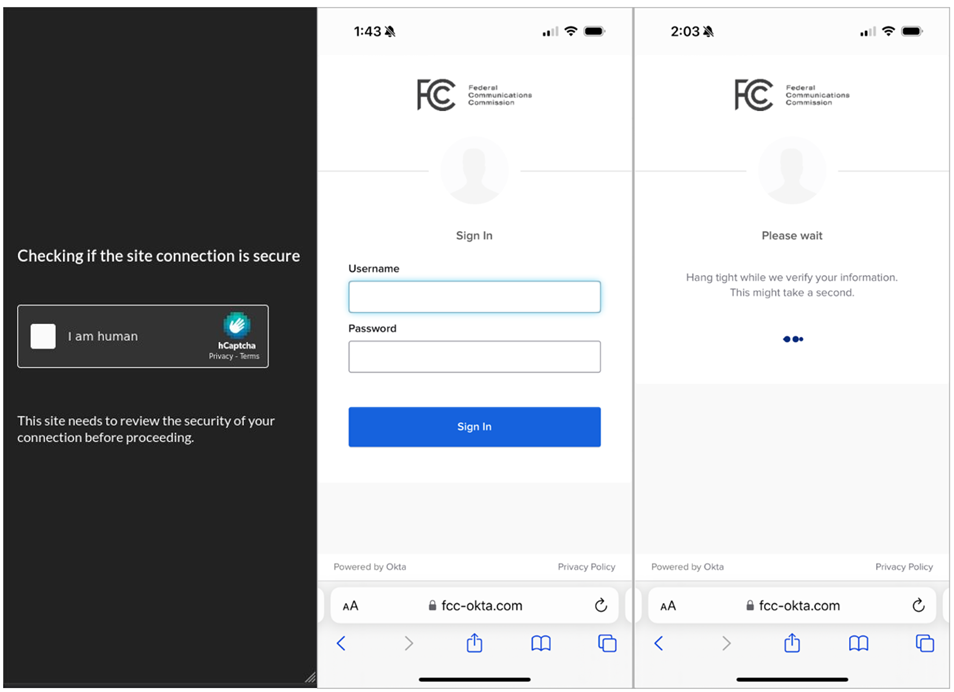
From left to right: CAPTCHA verification page, FCC phishing page, and Fake wait page
The CryptoChameleon phishing suite allows a cybercriminal to interact with victims in real time to facilitate scenarios such as requesting multi-factor authentication (MFA) codes to hijack a target's account.
The central phishing control panel allows an attacker to set up a phishing page, including the victim's phone number numbers, making more plausible requests for the MFA code.
Once the phishing process is complete, the victim may be redirected to a genuine login page or to a fake portal stating that their account is under review. Both referral options are used to reduce suspicion and give the attacker more time to use the stolen information.
Diving deeper, Lookout gained insight into additional targets in the cryptocurrency space by analyzing the phishing kit and finding the appropriate baits. The researchers also obtained short-term access to the attackers ' backend logs, confirming that the campaign resulted in high-value compromises.
According to experts, cybercriminals conducted phishing attacks on more than 100 victims. Many of the sites are still active and continue phishing for more credentials every hour.
The main hosting sites for phishing pages at the end of 2023 were Hostwinds and Hostinger, but later the scammers switched to the RetnNet data network, which offers a longer operational period for such sites.
Lookout was unable to determine whether CryptoChameleon is used exclusively by a single threat actor or rented out to multiple groups. Regardless of who is behind the phishing kit, its advanced nature, targeting strategy and communication methods of operators, as well as the high quality of phishing materials emphasize the impact that the service can have on target organizations.
Lookout reports that the new CryptoChameleon phishing kit has become a tool for attacks on employees of the Federal Communications Commission( FCC), during which the fake Okta authentication system is used.
The campaign targets users and employees of cryptocurrency platforms, including Binance, Coinbase, Kraken, and Gemini, using phishing pages that mimic Okta, Gmail, iCloud, Outlook, X, Yahoo, and AOL.
Attackers organize sophisticated phishing and social engineering attacks that involve interaction via email, SMS, and voice phishing (vishing) to trick victims into entering confidential information on fake pages – usernames, passwords, and even passport photos.
Attackers prepare an attack by first registering domains that are very similar to the domains of legitimate sites. For example, for the FCC, they created the domain "fcc-okta [.] com", which differs by only one character from the actual FCC Single Sign-On (SSO) page via Okta.

Phishing SMS message (left) and fake page (right)
Attackers can call, email, or TEXT targets pretending to be customer support, and direct them to a phishing site to "restore" their accounts. On the scam site, the victim is met with a CAPTCHA, which, according to Lookout, serves as bot filtering, and also adds credibility to the process. After completing the CAPTCHA, the user sees a well-designed phishing page that looks like an exact copy of the real Okta login page.

From left to right: CAPTCHA verification page, FCC phishing page, and Fake wait page
The CryptoChameleon phishing suite allows a cybercriminal to interact with victims in real time to facilitate scenarios such as requesting multi-factor authentication (MFA) codes to hijack a target's account.
The central phishing control panel allows an attacker to set up a phishing page, including the victim's phone number numbers, making more plausible requests for the MFA code.
Once the phishing process is complete, the victim may be redirected to a genuine login page or to a fake portal stating that their account is under review. Both referral options are used to reduce suspicion and give the attacker more time to use the stolen information.
Diving deeper, Lookout gained insight into additional targets in the cryptocurrency space by analyzing the phishing kit and finding the appropriate baits. The researchers also obtained short-term access to the attackers ' backend logs, confirming that the campaign resulted in high-value compromises.
According to experts, cybercriminals conducted phishing attacks on more than 100 victims. Many of the sites are still active and continue phishing for more credentials every hour.
The main hosting sites for phishing pages at the end of 2023 were Hostwinds and Hostinger, but later the scammers switched to the RetnNet data network, which offers a longer operational period for such sites.
Lookout was unable to determine whether CryptoChameleon is used exclusively by a single threat actor or rented out to multiple groups. Regardless of who is behind the phishing kit, its advanced nature, targeting strategy and communication methods of operators, as well as the high quality of phishing materials emphasize the impact that the service can have on target organizations.

