Father
Professional
- Messages
- 2,602
- Reaction score
- 837
- Points
- 113
Will the flaw that allows viruses to be inserted into the code unnoticed be fixed?
BleepingComputer identified a problem in the GitLab platform that allows attackers to distribute malware using comments in repositories. This feature can be used to create traps that look like legitimate files from well-known projects.
According to the study, cybercriminals can attach files in comments to repositories, and these files are uploaded to the GitLab CDN. For example, testing used files that were renamed to give the impression that they were new releases of programs from popular projects such as Inkscape and Wireshark. In fact, they were just ordinary JPG images, renamed to". exe".
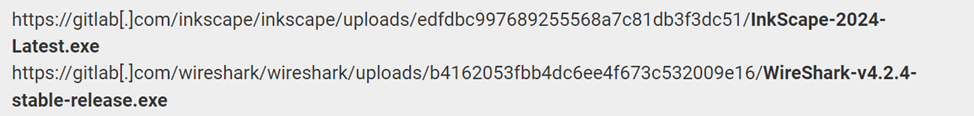
Comments with malicious files
Malicious files receive a URL that includes an MD4 or MD5 hash, which makes it more difficult to identify fake links without special knowledge. Links to such files remain active even after the comment is deleted or if the comment was never published.
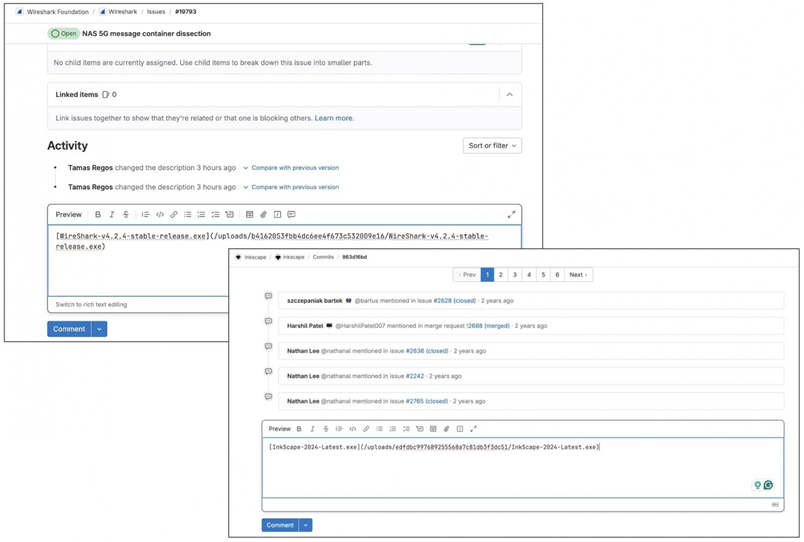
A download link is automatically generated when you add a file to a GitLab comment
This vulnerability can be used to disguise malware as updates or new software versions, which poses a serious security risk. Users who download files, believing that they come from reliable sources, run the risk of becoming victims of fraudsters.
GitLab requires authorization to upload or download files, but this does not prevent malicious users from downloading malicious files. At the time of publication, GitLab did not comment on the issue, but the study raises questions about security and the need for additional security measures on software development platforms.
Note that a similar vulnerability was previously discovered on the GitHub platform, where hackers used comments to spread the Cheat Lab virus, disguising installers as official Microsoft repository files.
The attacks took place via specially generated URLs that pretended to be part of the official code source. This use of the GitHub CDN to host files that do not belong to repositories, but pretend to be such, demonstrates the commonality of the problem between the two platforms.
BleepingComputer identified a problem in the GitLab platform that allows attackers to distribute malware using comments in repositories. This feature can be used to create traps that look like legitimate files from well-known projects.
According to the study, cybercriminals can attach files in comments to repositories, and these files are uploaded to the GitLab CDN. For example, testing used files that were renamed to give the impression that they were new releases of programs from popular projects such as Inkscape and Wireshark. In fact, they were just ordinary JPG images, renamed to". exe".

Comments with malicious files
Malicious files receive a URL that includes an MD4 or MD5 hash, which makes it more difficult to identify fake links without special knowledge. Links to such files remain active even after the comment is deleted or if the comment was never published.

A download link is automatically generated when you add a file to a GitLab comment
This vulnerability can be used to disguise malware as updates or new software versions, which poses a serious security risk. Users who download files, believing that they come from reliable sources, run the risk of becoming victims of fraudsters.
GitLab requires authorization to upload or download files, but this does not prevent malicious users from downloading malicious files. At the time of publication, GitLab did not comment on the issue, but the study raises questions about security and the need for additional security measures on software development platforms.
Note that a similar vulnerability was previously discovered on the GitHub platform, where hackers used comments to spread the Cheat Lab virus, disguising installers as official Microsoft repository files.
The attacks took place via specially generated URLs that pretended to be part of the official code source. This use of the GitHub CDN to host files that do not belong to repositories, but pretend to be such, demonstrates the commonality of the problem between the two platforms.

