Carding
Professional
- Messages
- 2,871
- Reaction score
- 2,372
- Points
- 113
Is your messenger definitely not a fake?
Cybersecurity researchers from ESET have discovered two spy campaigns in which attackers used fake versions of Signal and Telegram. The targets were Android users in the US and Europe.
Experts believe that the Chinese group GREF is involved in the case. Fake apps were placed on Google Play and Samsung Galaxy Stores. They were actively distributed from July 2020 to July 2022.
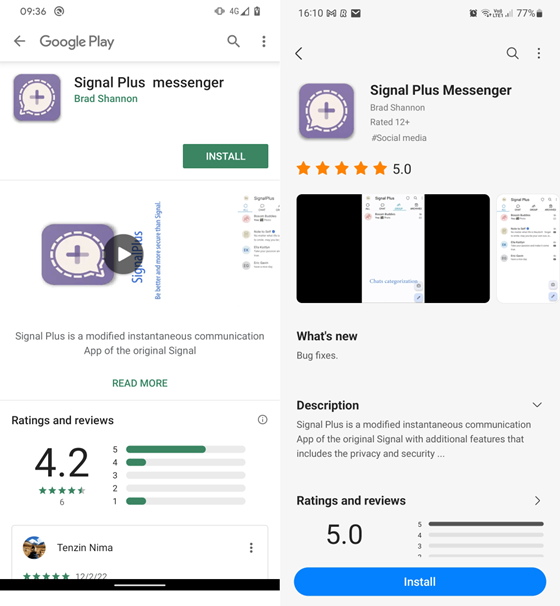
According to ESET, the messengers were downloaded by thousands of people. Hackers called them "Signal Plus Messenger"and " FlyGram". The largest number of downloads was registered in the United States, several EU countries, and Ukraine.

Lukasz Stefanko, the author of the study, explained that the apps supported all the functions of their legal counterparts, but with the deployment of spyware in the background. Experts identified the malicious code that is integrated into encrypted messengers as BadBazaar.
Stefanko clarifies: the main task of BadBazaar is to extract information about the device, contact list, call log and installed applications. The chats themselves were also viewed.
This is the first recorded case of Signal spying, in which a compromised device automatically communicated with the command and control server.
Telegram users were more fortunate — hackers failed to link FlyGram to their original accounts. Consequently, they could not intercept encrypted messages, but they did manage to collect information about the devices. Backup, a function that the victim had to activate independently in FlyGram, helped. ESET has identified about 14,000 such users.
Previously, the GREF group used BadBazaar against Uighurs and other Turkic ethnic minorities outside of China. This fact confirms that the software is effective for tracking and collecting confidential data.
Google has already removed both apps from the Play Store, but other sites may continue hosting them.
Cybersecurity researchers from ESET have discovered two spy campaigns in which attackers used fake versions of Signal and Telegram. The targets were Android users in the US and Europe.
Experts believe that the Chinese group GREF is involved in the case. Fake apps were placed on Google Play and Samsung Galaxy Stores. They were actively distributed from July 2020 to July 2022.
According to ESET, the messengers were downloaded by thousands of people. Hackers called them "Signal Plus Messenger"and " FlyGram". The largest number of downloads was registered in the United States, several EU countries, and Ukraine.

Lukasz Stefanko, the author of the study, explained that the apps supported all the functions of their legal counterparts, but with the deployment of spyware in the background. Experts identified the malicious code that is integrated into encrypted messengers as BadBazaar.
Stefanko clarifies: the main task of BadBazaar is to extract information about the device, contact list, call log and installed applications. The chats themselves were also viewed.
This is the first recorded case of Signal spying, in which a compromised device automatically communicated with the command and control server.

Telegram users were more fortunate — hackers failed to link FlyGram to their original accounts. Consequently, they could not intercept encrypted messages, but they did manage to collect information about the devices. Backup, a function that the victim had to activate independently in FlyGram, helped. ESET has identified about 14,000 such users.
Previously, the GREF group used BadBazaar against Uighurs and other Turkic ethnic minorities outside of China. This fact confirms that the software is effective for tracking and collecting confidential data.
Google has already removed both apps from the Play Store, but other sites may continue hosting them.
