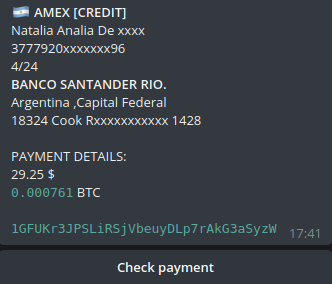
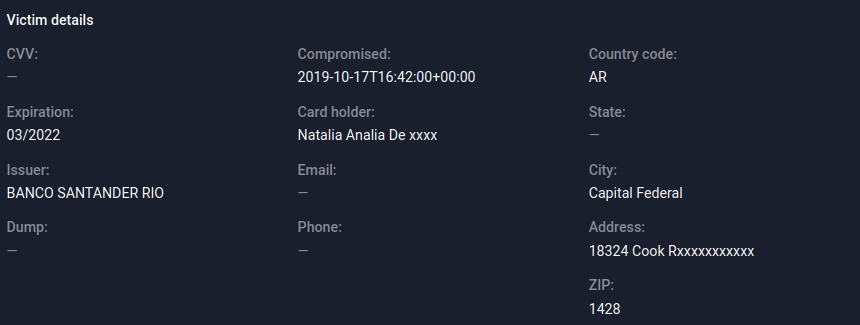
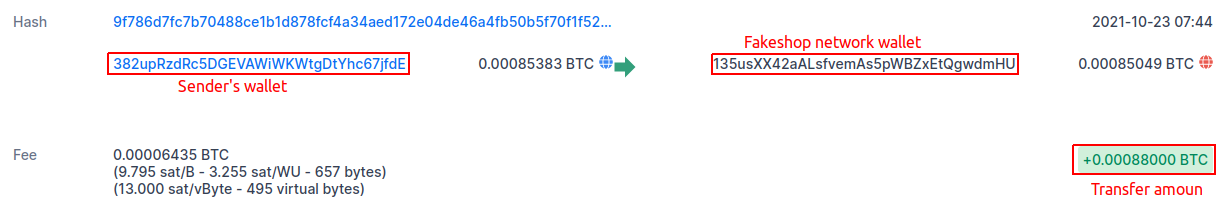
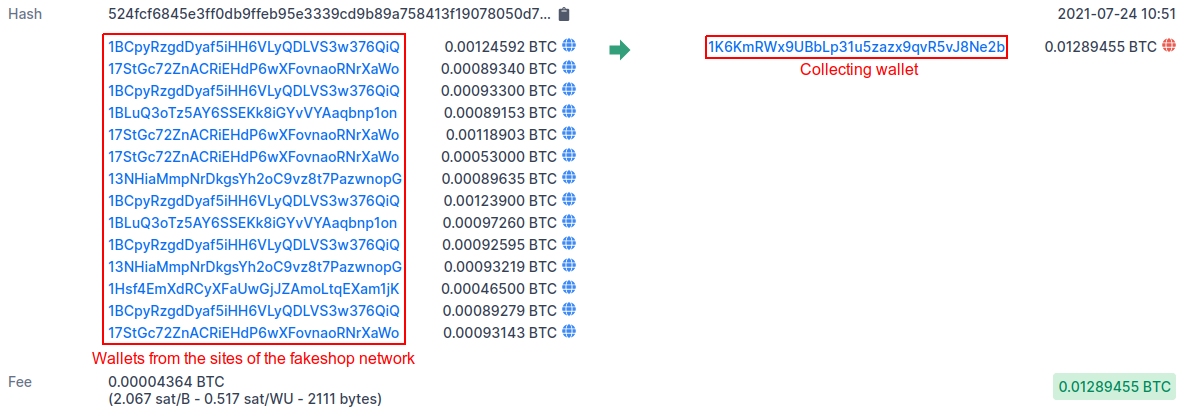
In this post, for the first time, we will explore such a layer of the underground as fake marketplaces for trading bank card data. Carding is a crime. Trading bank card data is a crime. Creating fake stores that copy "original" cardshops is also a crime. We believe that the deeper the underground industry is studied, the more opportunities there are for tracking, studying and combating cybercrime.
That is why we are publishing a study of phishing resources copying cardshops for the first time. In this case, under cardshops, we will understand "original" resources for trading dumps and text data of bank cards. Under "fake shops" — phishing resources that copy cardshops. Under users-buyers of stolen bank card data.
As you probably already understood, there are no "ordinary users" who have become "victims" of scammers in this study. It describes the phenomenon of "cannibalism" in the underground environment, when some attackers profit from others.
Every Internet user regularly encounters phishing sites. Cybercriminals are no exception. Analysts of Group-IB Threat Intelligence managed to identify several large groups of scammers who earn money from novice inexperienced carders by creating and distributing phishing sites for cardshops-underground stores selling compromised payment data. These sites are called fake shops by Group-IB analysts.
A large number of fake shops on the web cause problems not only for users of underground forums — cybercriminals, but can also create difficulties for cyber intelligence specialists. Fake data posted on them can lead to false statistics when monitoring and describing cardshops, and copied designs of original resources can mislead even an experienced anti-fraud analyst.
As a rule, fake shops are not created one at a time. To reach more users (buyers of stolen bank card data), the creators of fake shops advertise on underground forums, Telegram chats and deceive users to follow their links, forcing the creators of original resources, no matter how comical it may sound, to suffer reputational losses, and also combine their sites into giant networks.
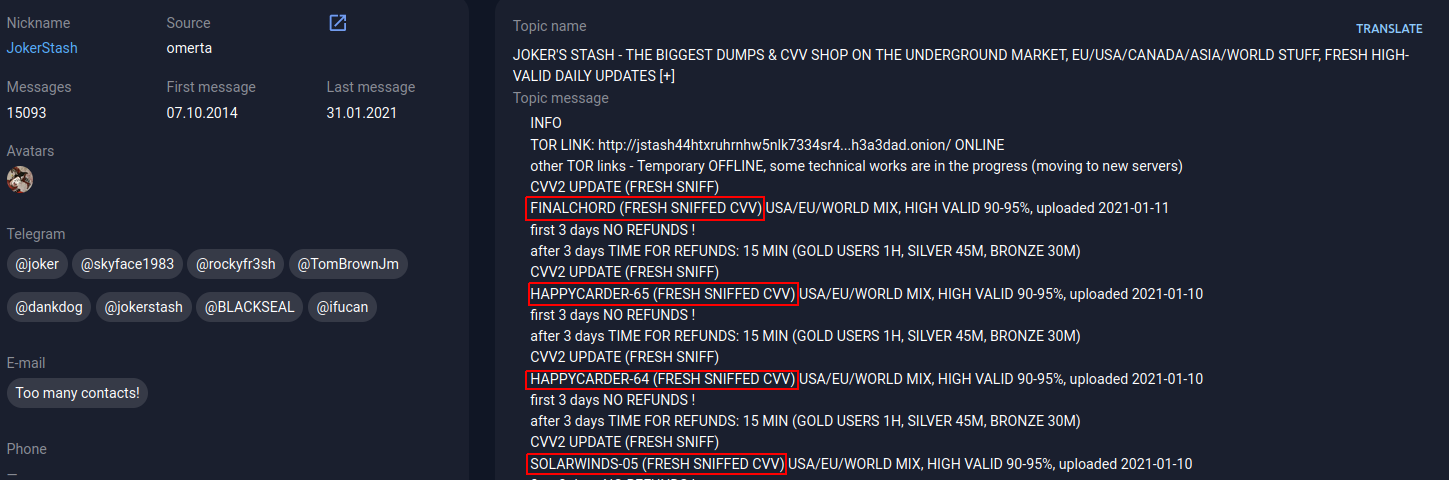
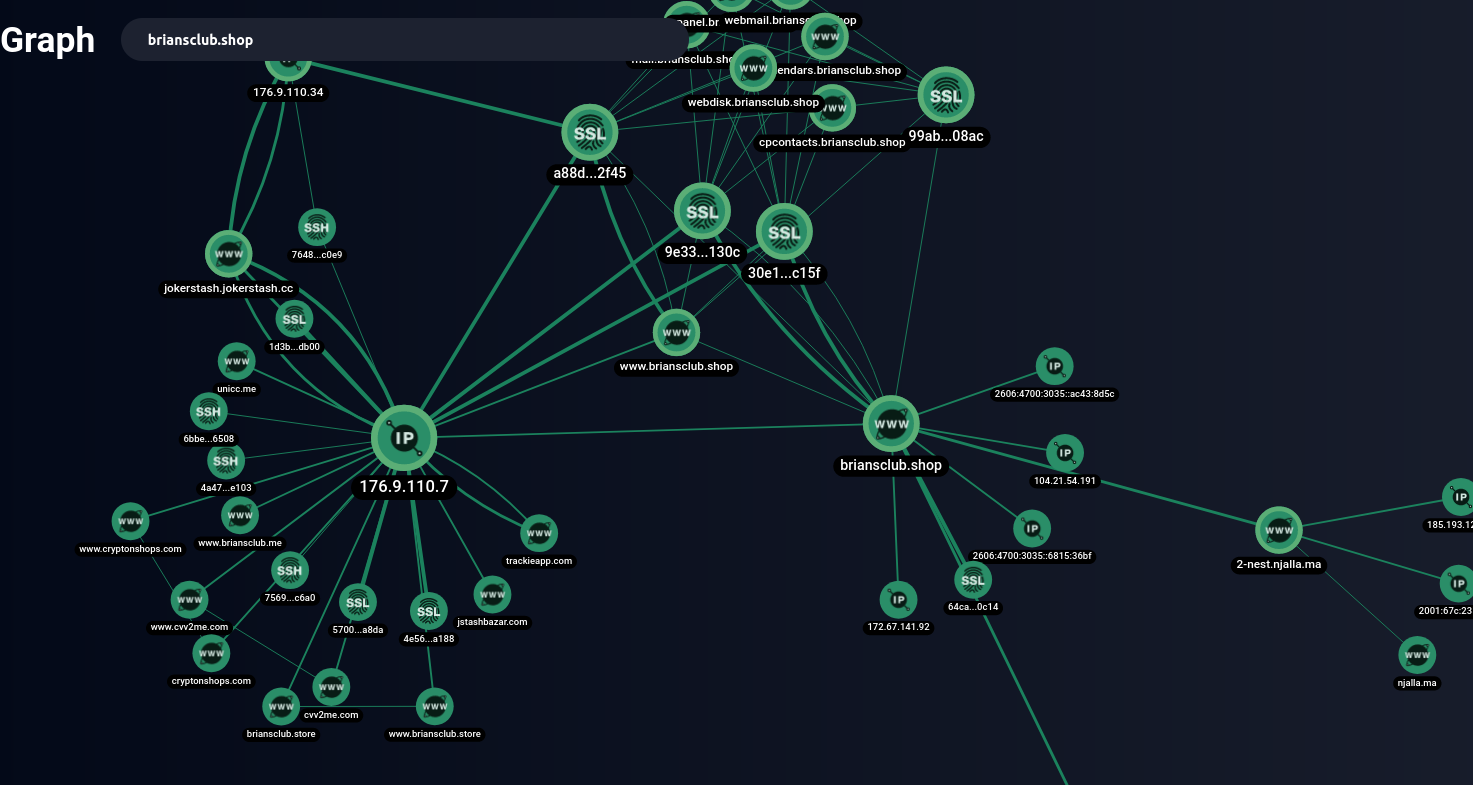
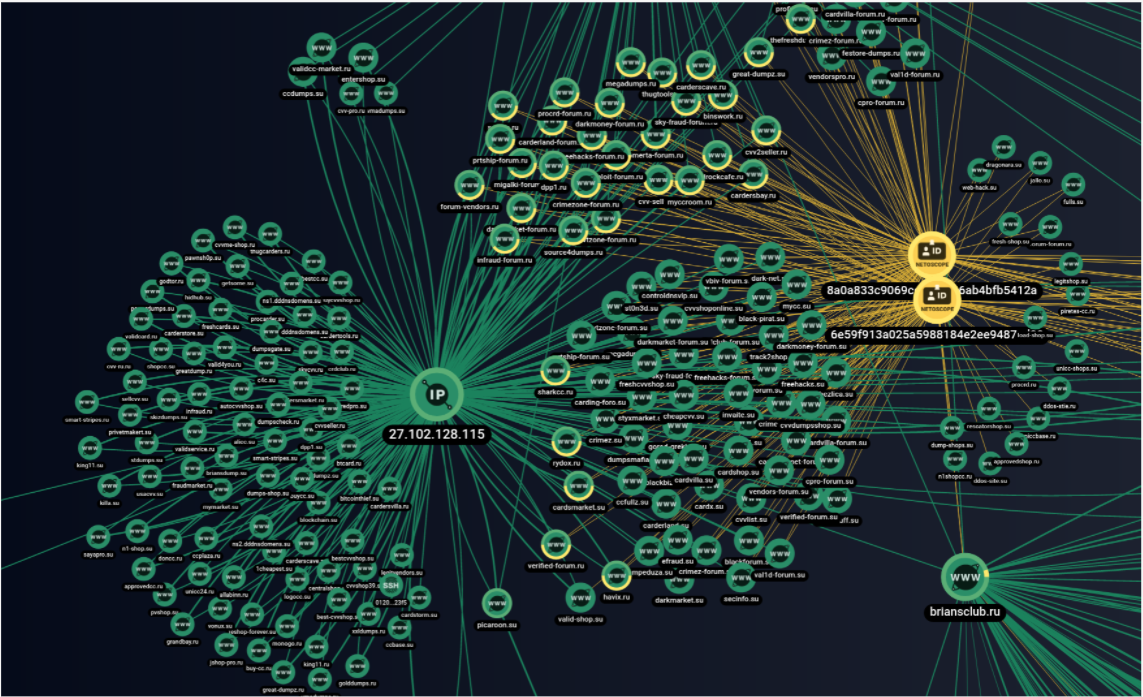
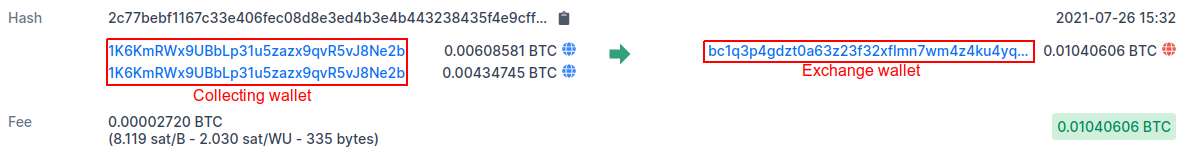
Analysts of Group-IB Threat Intelligence found three major networks of fake shops, which were named UniFake, JokerMantey, and SPAGETTI. The latter-the largest network discovered-has more than 3,000 domain names, many of which are copies of the most popular card sites in the underground, such as: Joker's Stash, BriansClub, Uniq, Ferum shop, ValidCC and others.
The creators of this network managed to receive at least 9,200 incoming transactions to various crypto wallets, totaling more than $1,200,000 (most of which were received in Bitcoin – 23 BTC at the exchange rate on October 12, 2021).
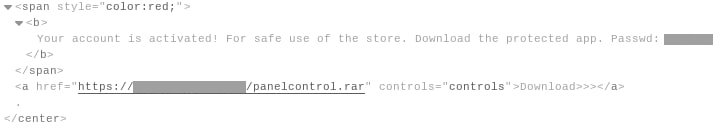
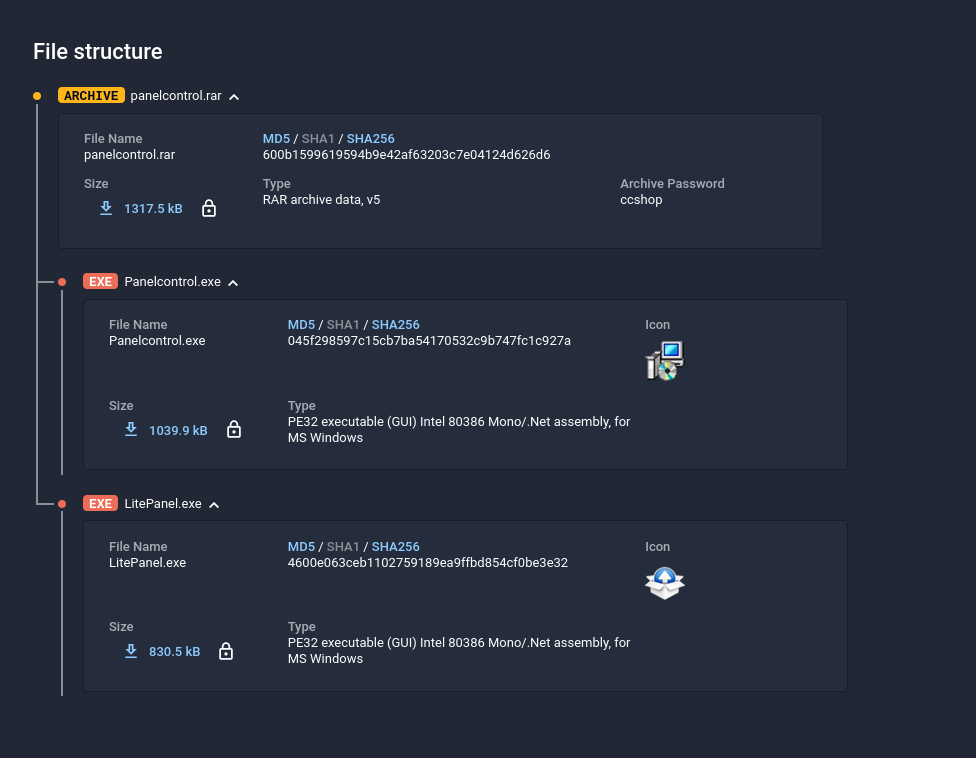
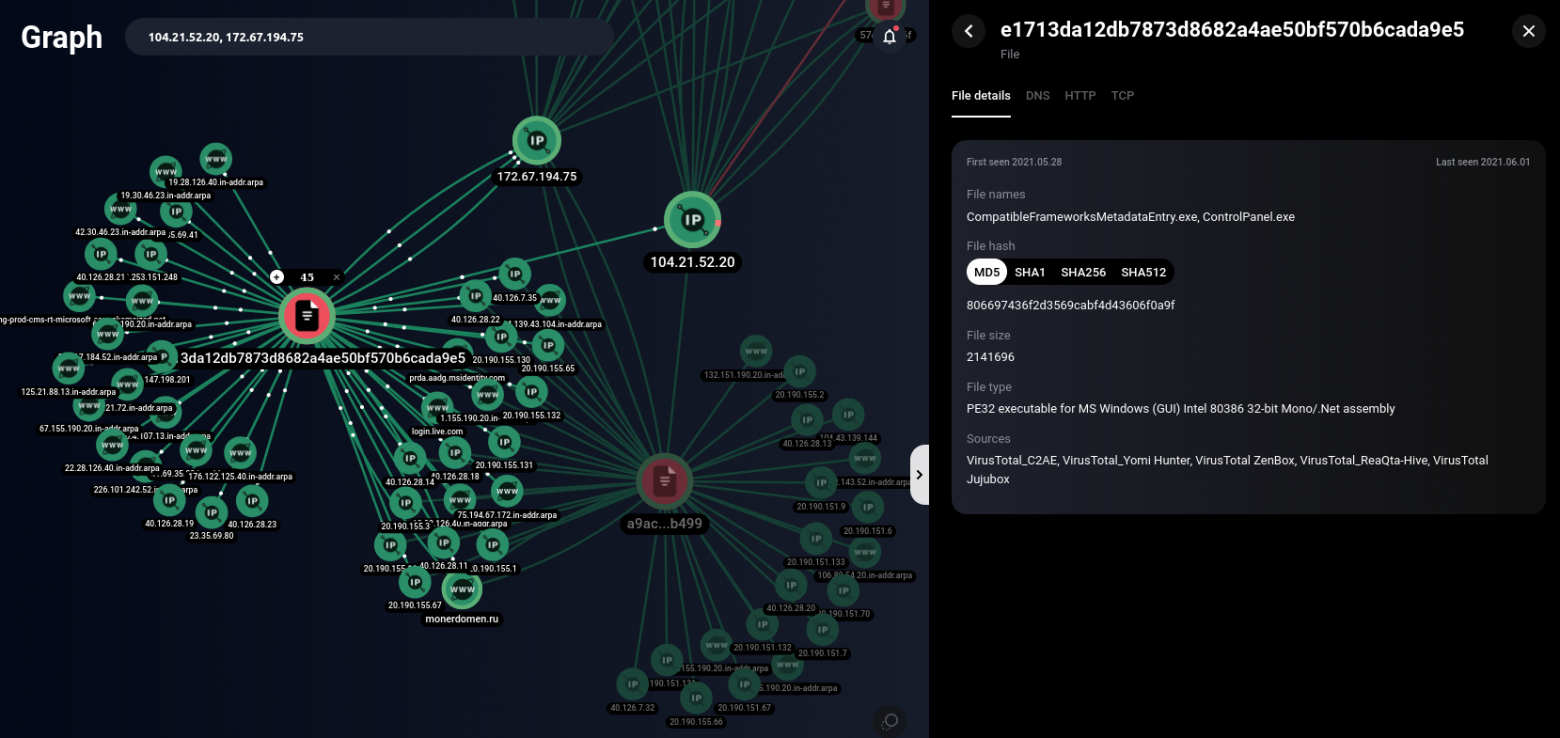
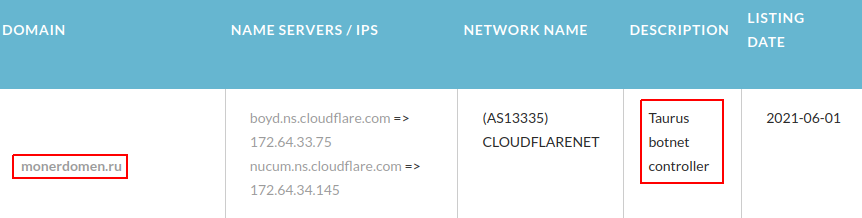
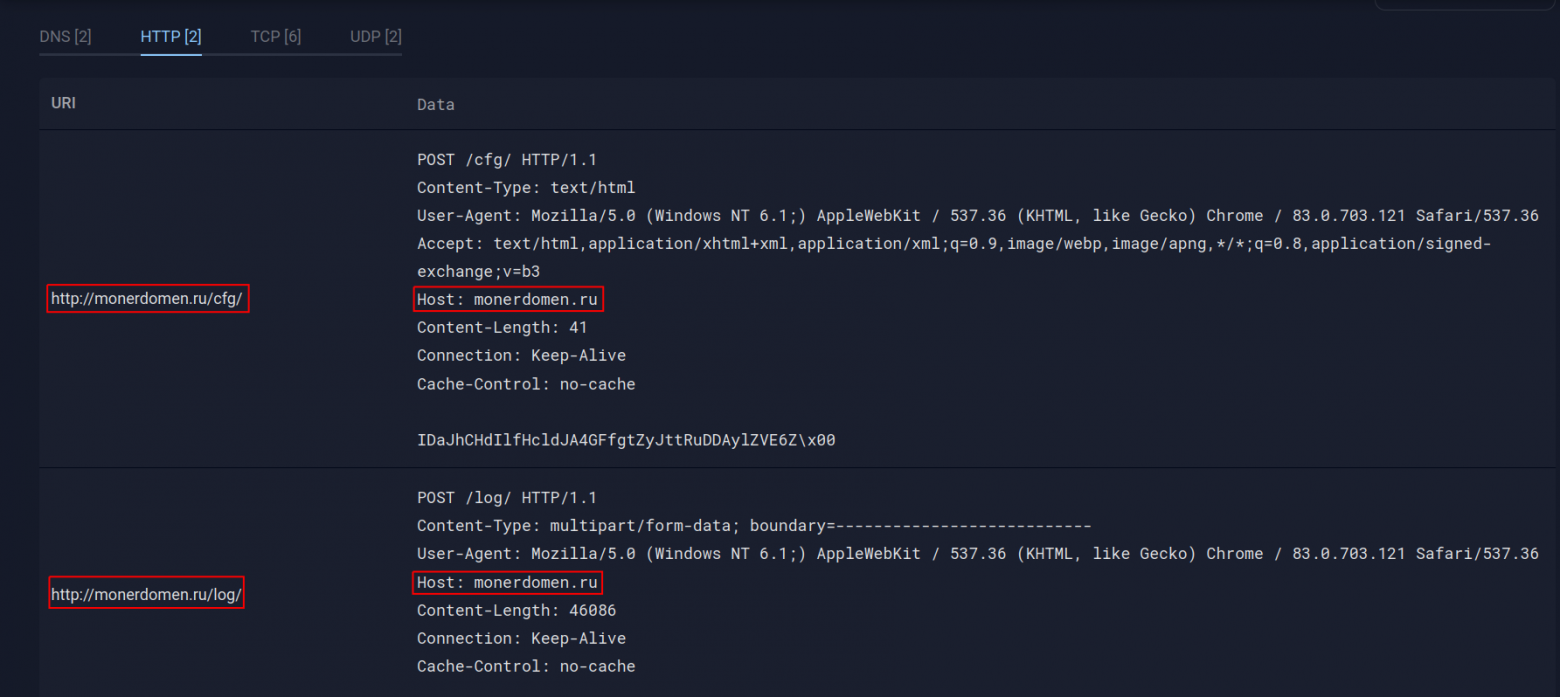
Unlike other networks, SPAGETTI also distributes malware through its websites. The creators of this network have placed the Taurus Project styler on their sites as a downloadable file, thus collecting user data from the browser, usernames and passwords from banking applications, and even crypto wallets.
Group-IB specialists studied how fake shop networks are created and maintained. In the first part of this article, Ruslan Chebesov, head of the Group-IB underground market research group, and Sergey Kokurin, an analyst at Group-IB underground markets, explain how analysts can distinguish an original card shop from a fake one and how to correctly attribute a fake resource. And in the next post, using the Threat Intelligence & Attribution system, they will analyze the largest fake shop networks for example.
What are fake shops?
In the underground sphere of the Internet, there are resources for trading compromised information, such as credit or debit card data, access to user accounts, access to computers via RDP or SSH ports, passport or identification data of citizens of different countries, access to servers and control panels of sites, etc.These resources are called "underground markets".
The main feature of such markets is a large number of sellers on the resource. The sites themselves are analogous to Amazon or Ebay only on the shadow side of the Internet.
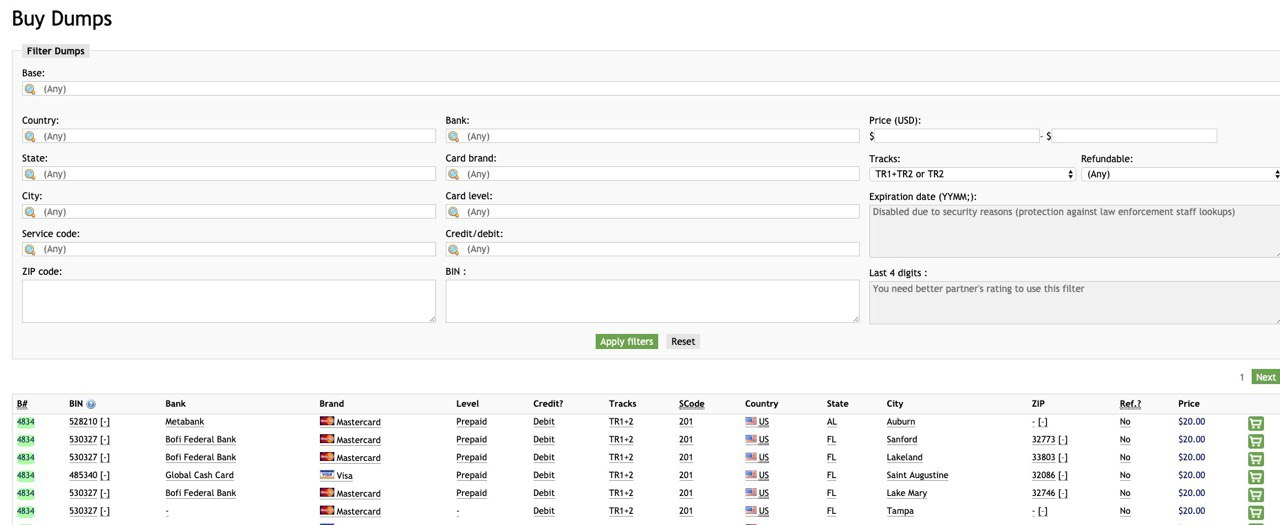
Cardshops are special cases of Yandex. Markets. Stolen bank card data is sold here in the form of text data from the card itself, or in the form of dumps-a saved copy of information from the magnetic stripe. Usually, there are no other types of compromised data sold on cardshops.

Cardshops and markets are the main resources for small-time scammers involved in carding, scamming, spam, and other similar types of cybercrime.
Carding-bank card fraud-is one of the simplest forms of fraud that does not require additional training from the criminal, except for basic computer skills. A low threshold for entering this "industry" creates a high demand for cardshops and marketplaces.
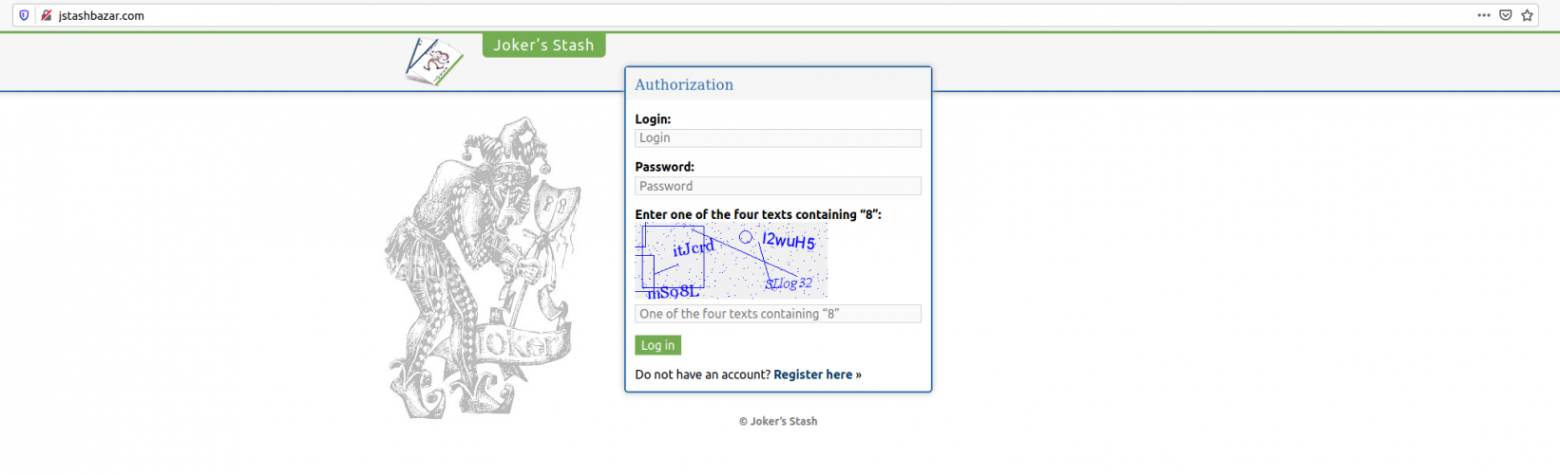
In fact, the high demand and low literacy levels of novice carders creates ideal conditions for scammers who earn money by creating fake shops — sites that pretend to be working cardshops or underground markets. The most important task is to create the illusion of a real resource, so that the user who gets to the site wants to leave their money on it. Additionally, you can use the names of existing underground resources or even completely copy the design of their pages.
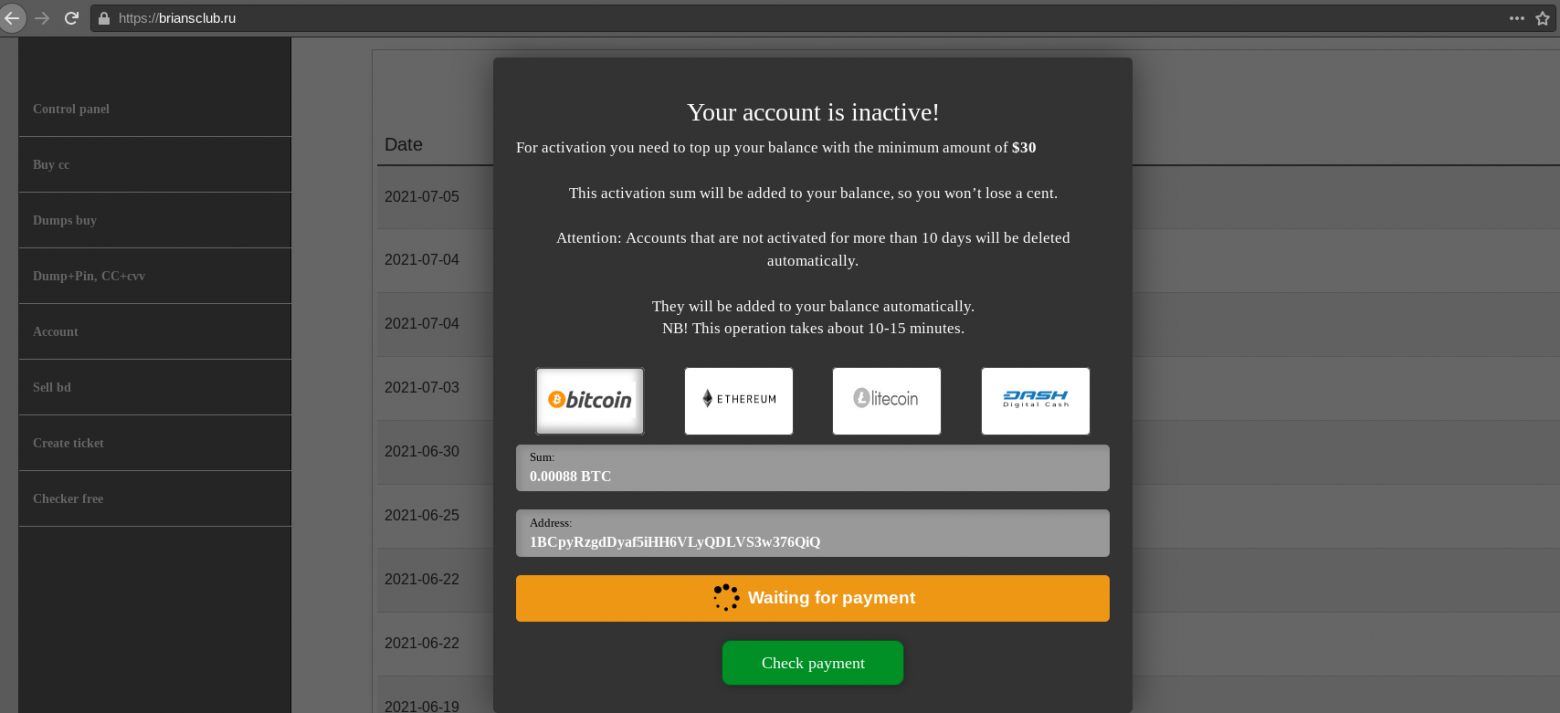
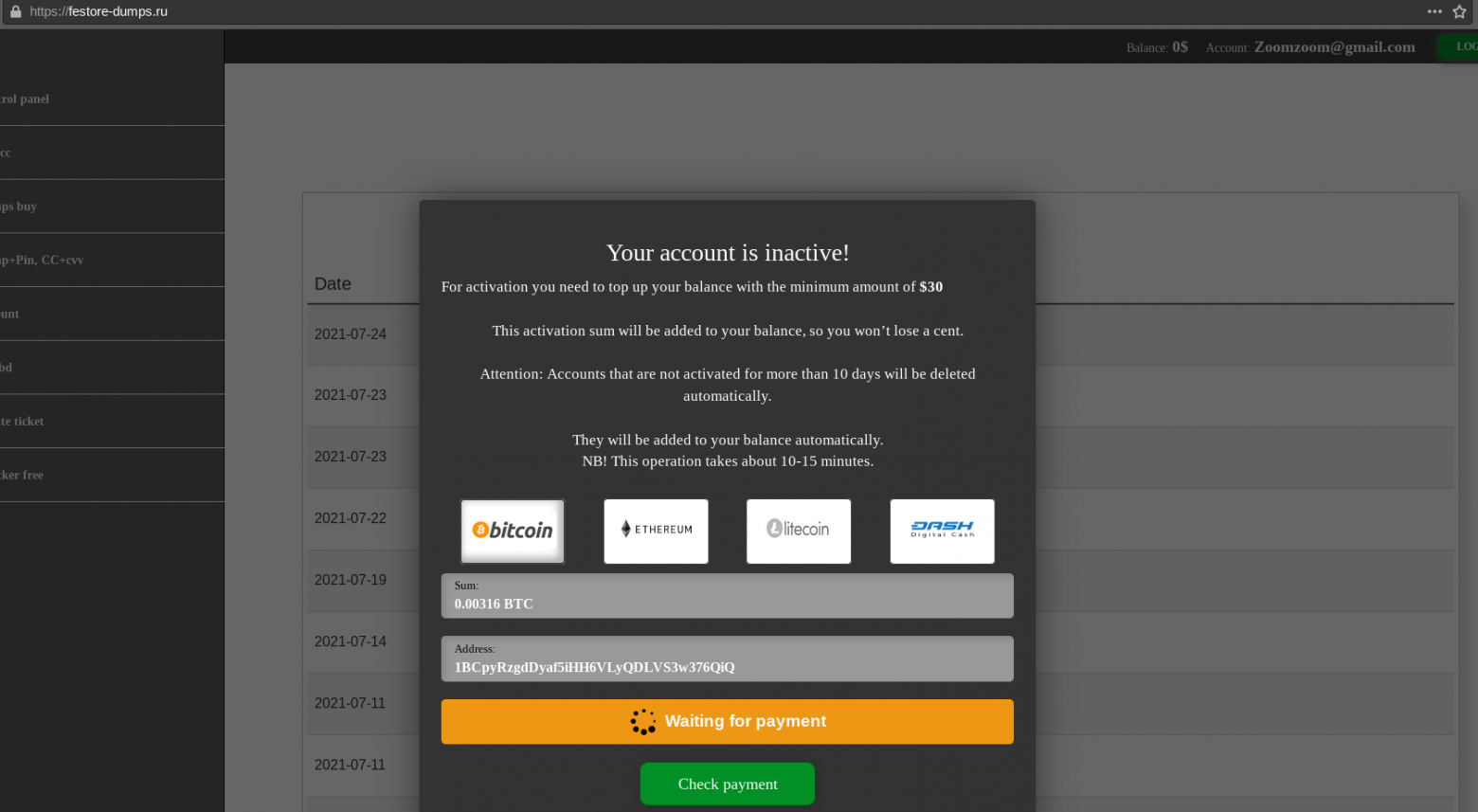
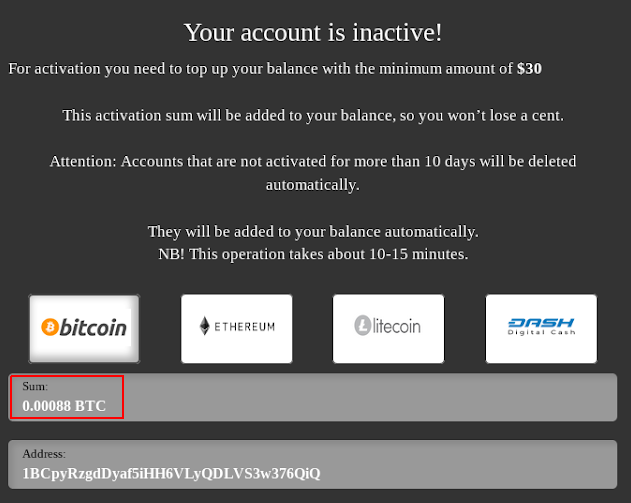
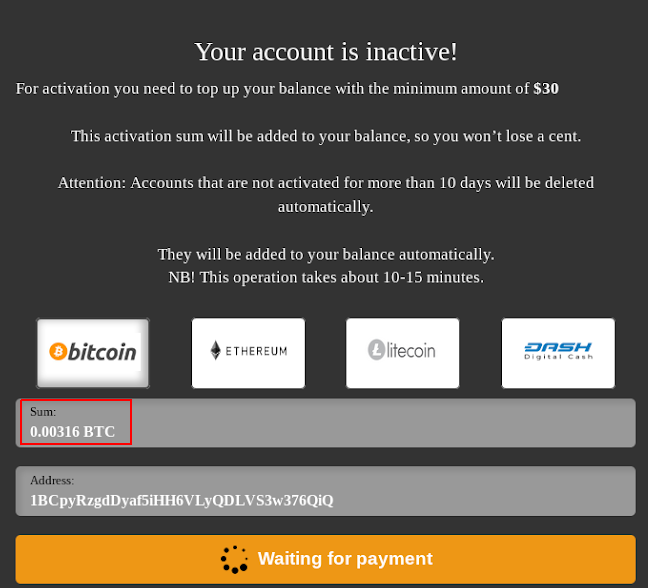
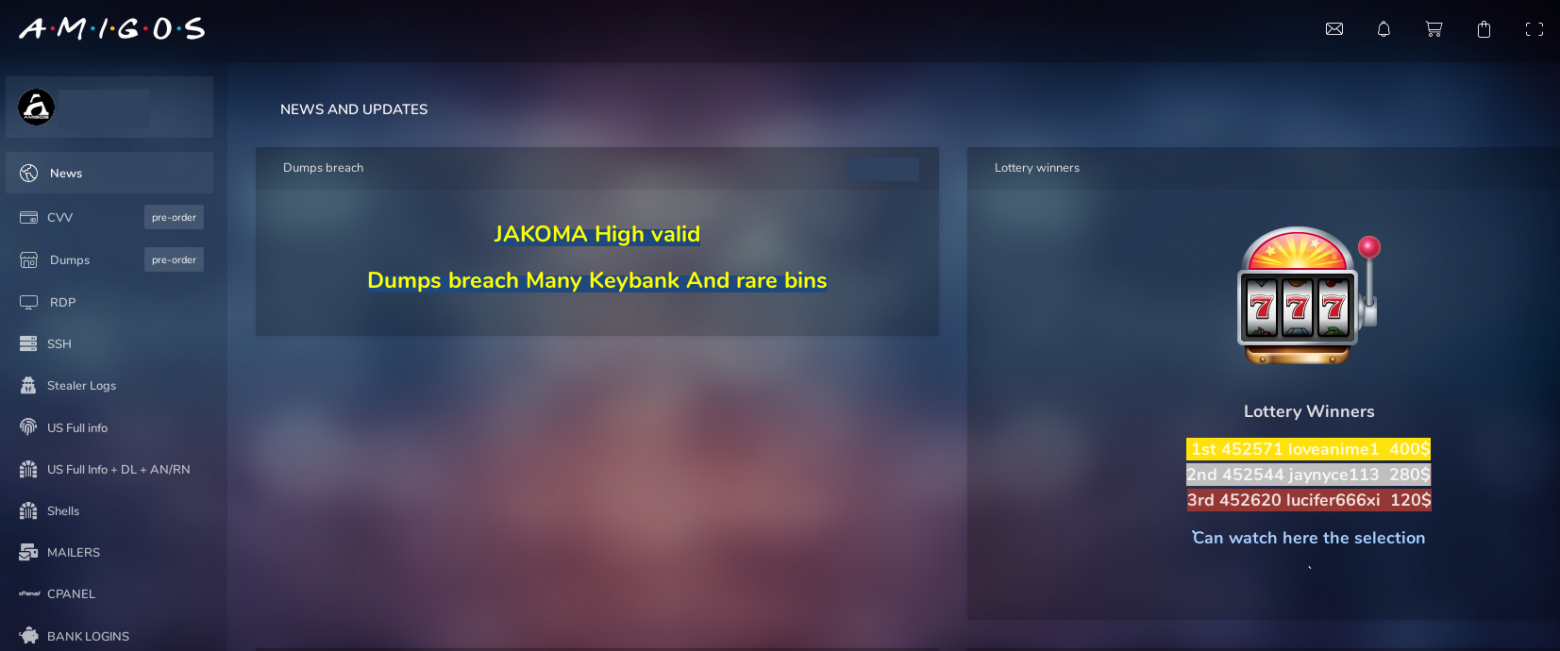
In the case of real cardshops and markets, the user first needs to deposit money to their account in order to use these funds to purchase compromised data. A common practice among cardshops is also paid account activation. For this purpose, after registration, the user must pay from $20 to $200. Fake shops use these well-established pre-payment systems to mislead carders.

Example of activating an account on the Amigos market
All fake shops can be divided into three types:
- Creates the appearance of a new card shop or Yandex. Market. This is the easiest way to cheat. In this case, the attacker creates a resource that creates the impression of a card shop or market with design elements on the site: product database lists, shopping cart, news and updates, support system, etc. Well-established words and abbreviations are also used for the name and domain name itself: "cc", "dump", "cvv", "shop", "carding", "pin", "swipe", "sniff", "money" and others.
Screenshot of the cvvunion fake shop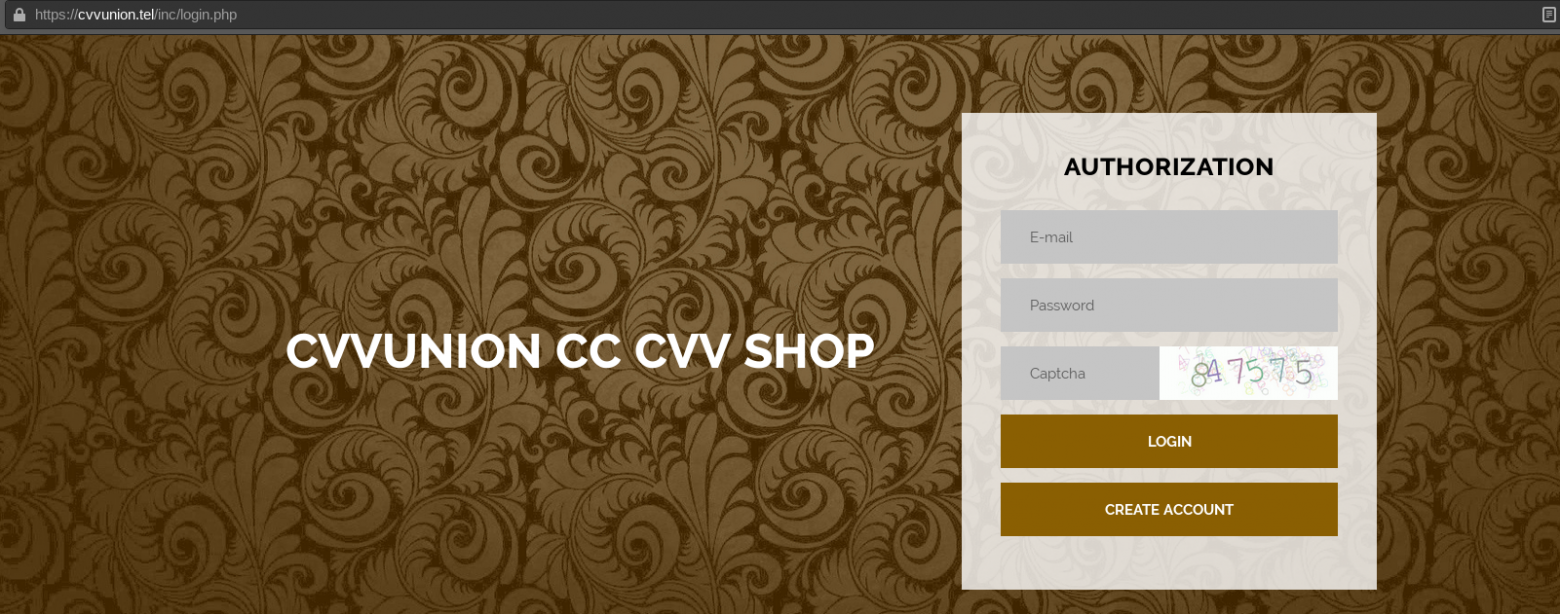
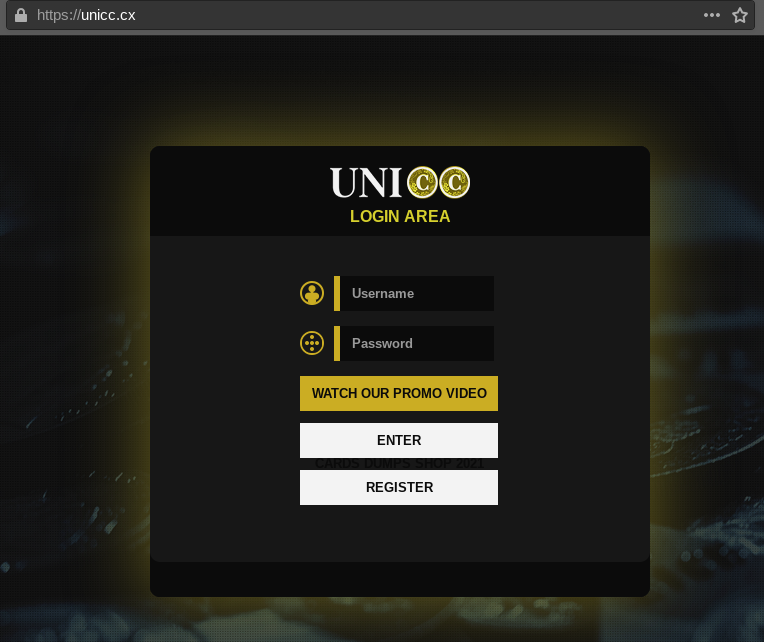
- Creating a phishing resource that mimics the original card shop. To do this, attackers create sites with a domain name that resembles the original one, change the location of letters or words in the name, add abbreviations, make special mistakes, or add some of the phrases from the paragraph above. To further mislead, attackers can copy the design of the original site: html code, css styles, and images. This is not a difficult task, but it increases the victim's confidence in the credibility of such a resource for an inexperienced user.
Screenshot of the main page of the Unicc fake shop, completely copying the original
- "Capture" the domain name of a real cardshop or market. This is one of the most difficult ways to create a fake shop. To do this, attackers need to buy back a domain name that once belonged to cardshop or Yandex. Market. This is quite possible if the site owners did not have time to pay the rent of the domain name to the registrar, or their domain address was split for some reason. In this case, users who have previously visited the resource via this link will be added to the fake shop.
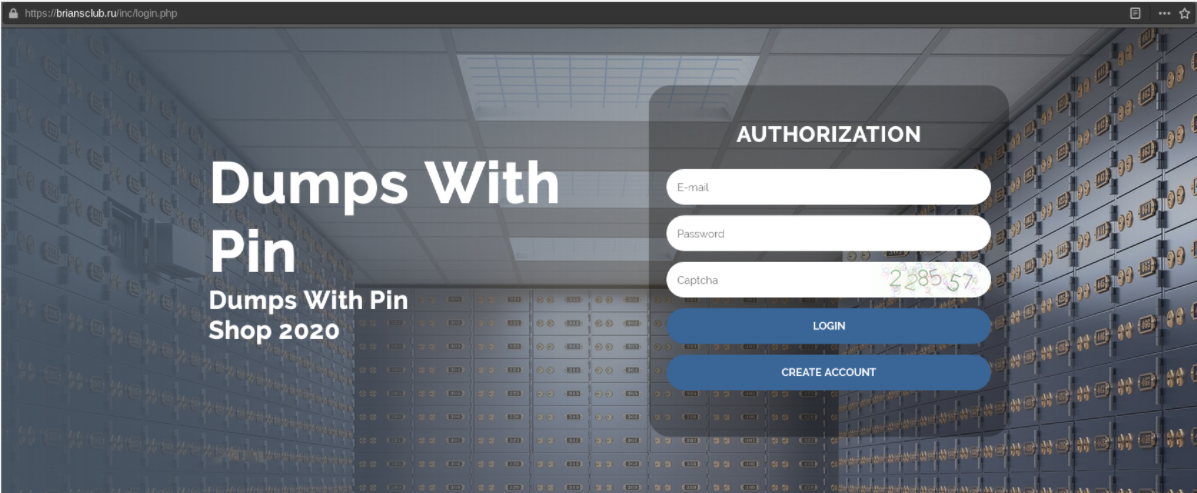
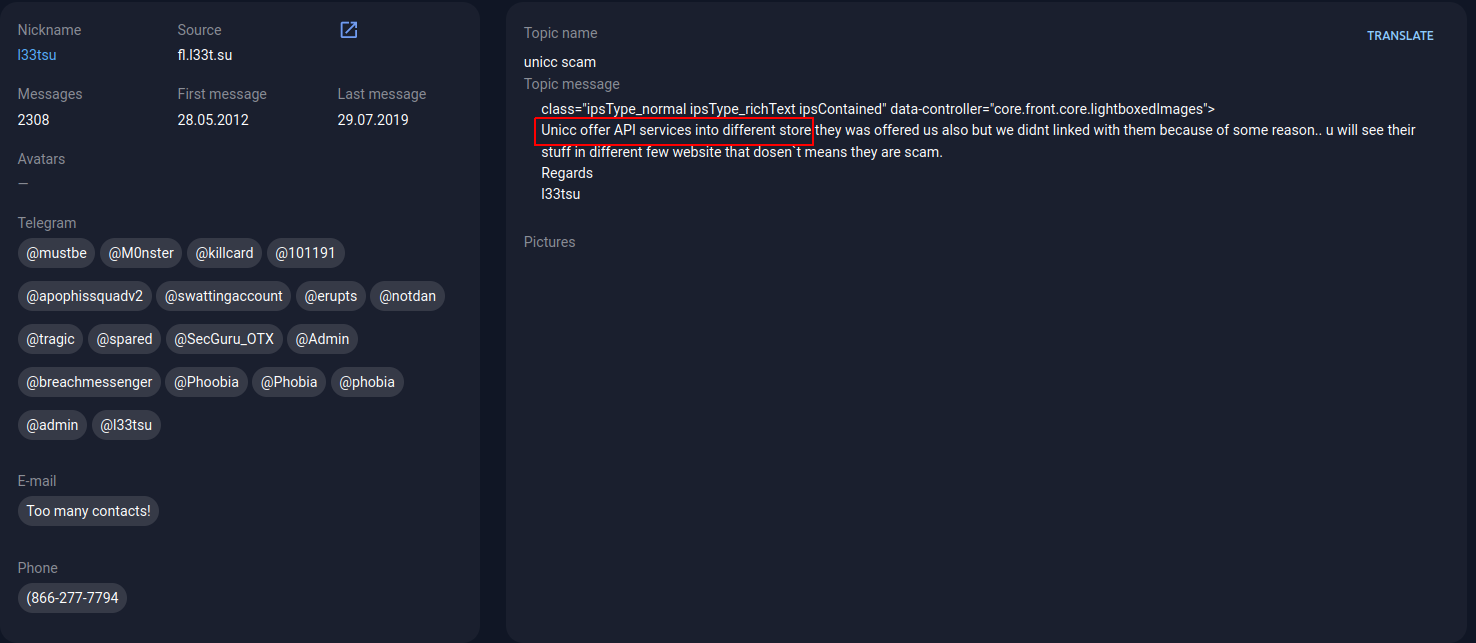
Such examples are unicc [domain hijacking.] cm and briansclub [.] ru. As we can see, outraged users who suspect fraud send messages to the administration of the original cardshops. Often, admins have to additionally inform their users about changing the domain name.
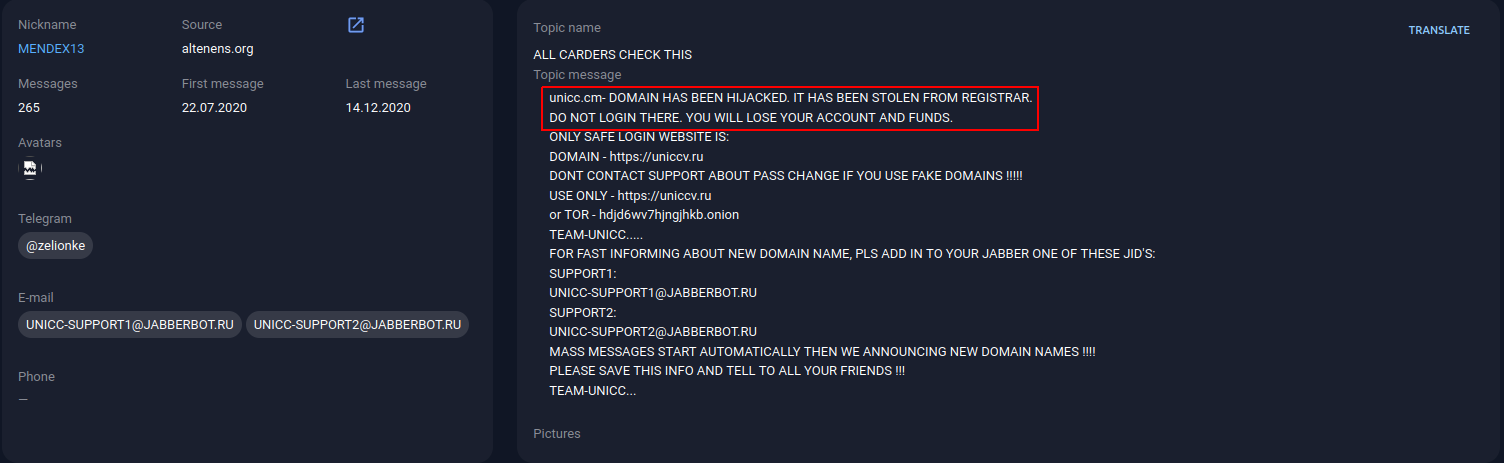
A post on the altenens[.]org forum. Source: Group-IB Threat Intelligence & Attribution
As follows from the message of the BriansClub administrator shown in the screenshot below, the briansclub domain is[.] ru previously belonged to his card shop. However, at the moment there is a fake shop posted there
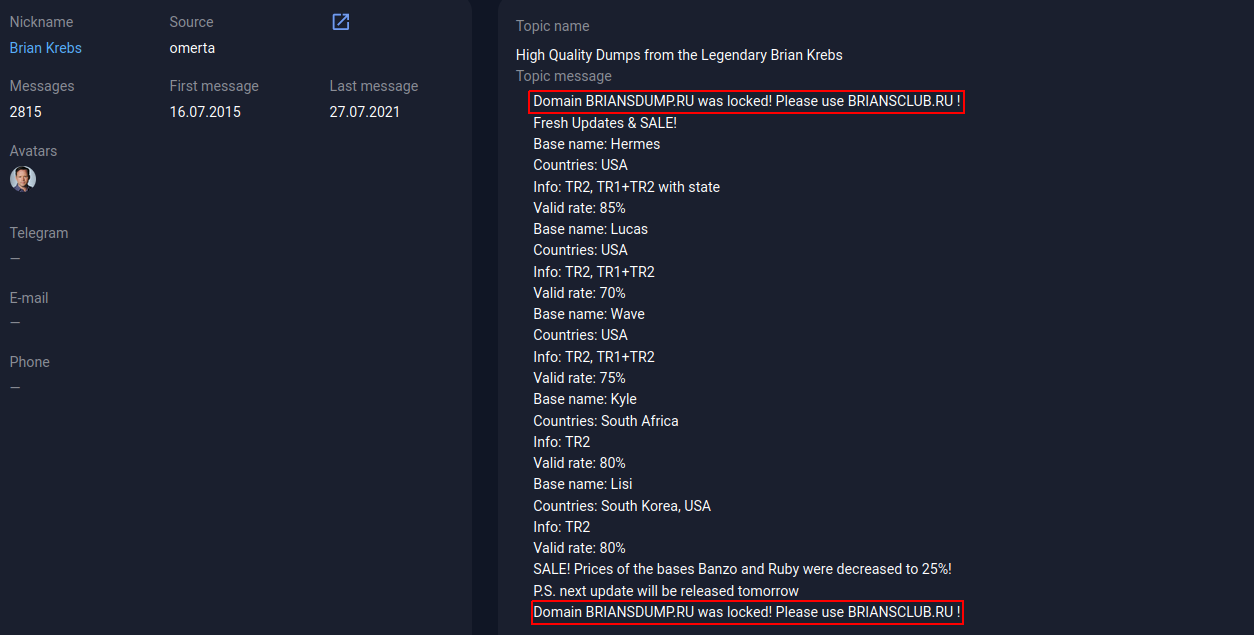
A post on the omerta forum. Source: Group-IB Threat Intelligence & Attribution
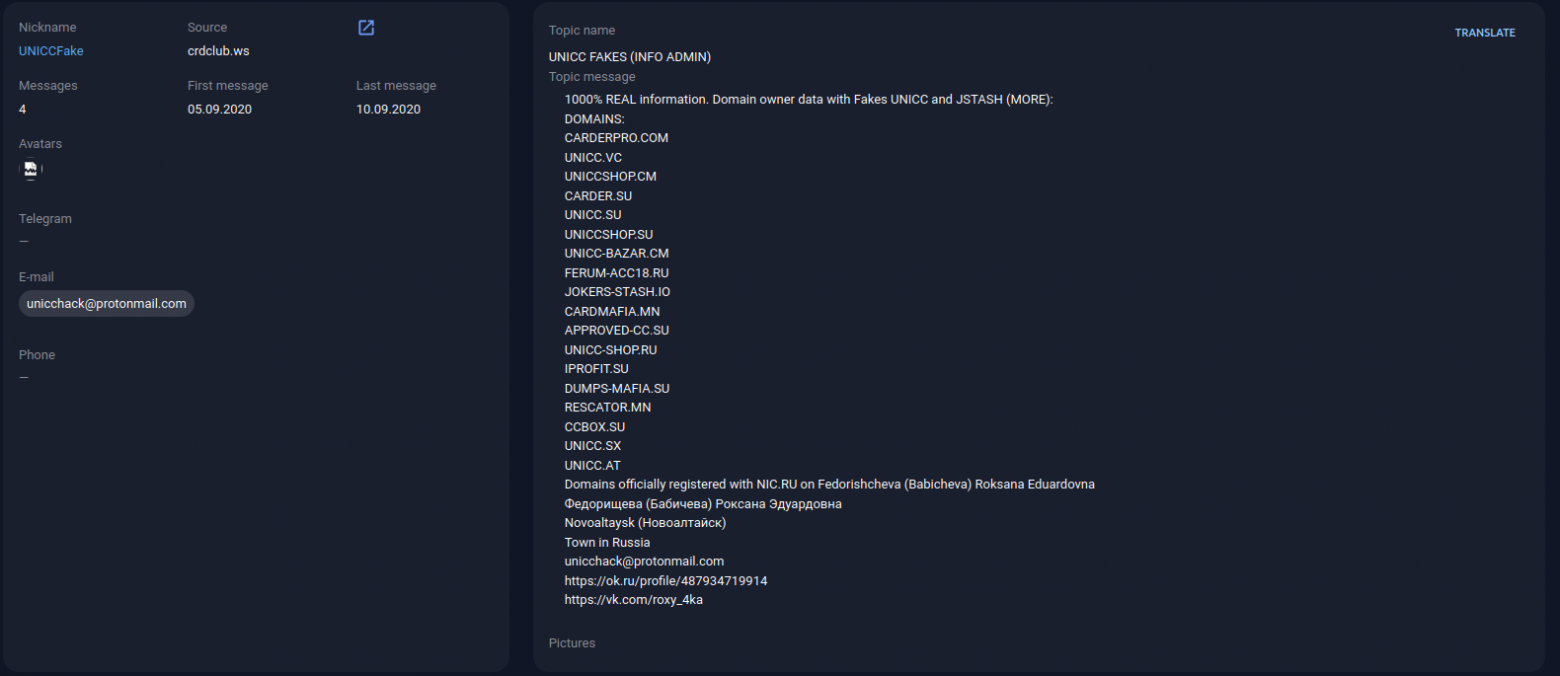
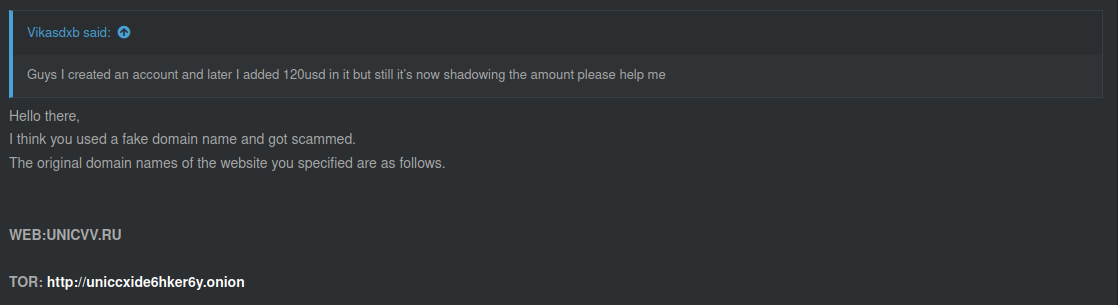
You can often find messages from deceived carders on various forums, as in the screenshot below, where the user deposited money to an account in Yandex. Market, but did not wait for the opportunity to purchase the desired "services".
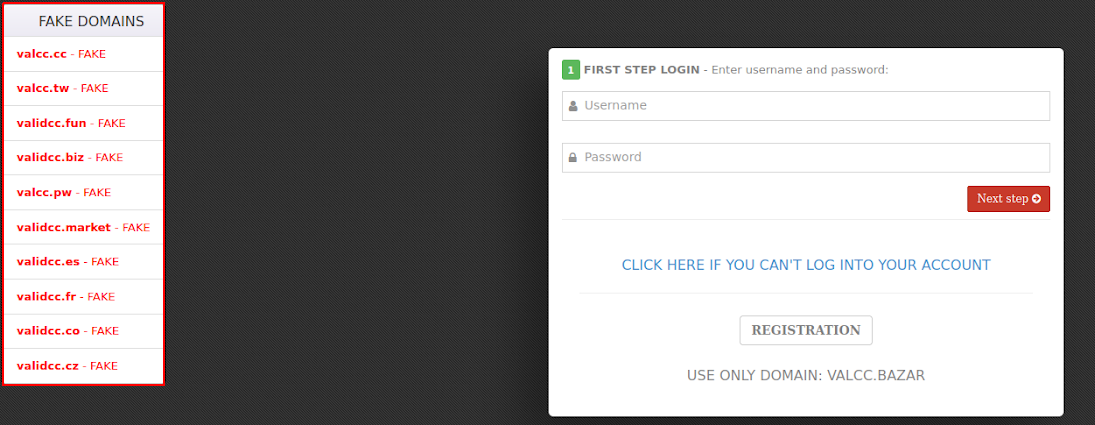
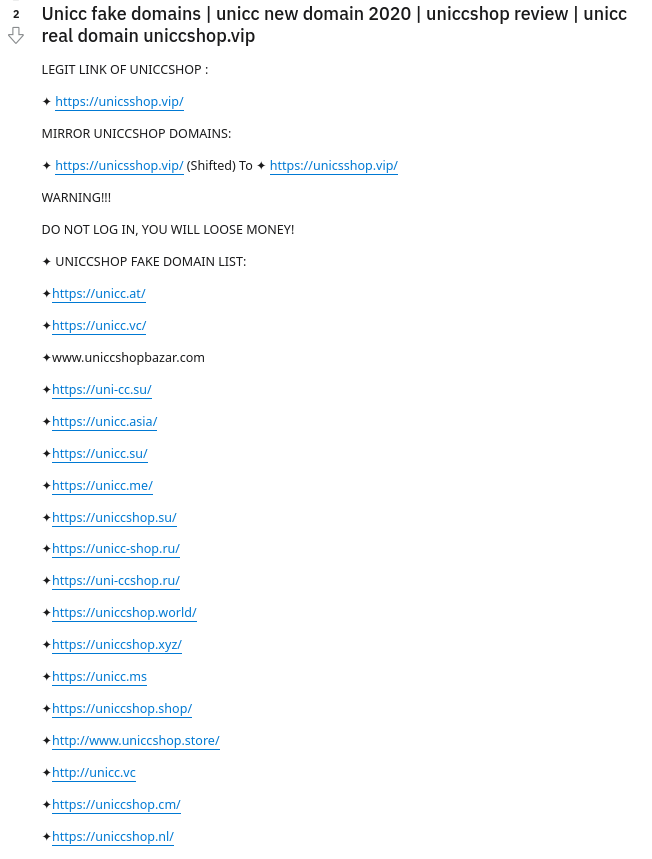
And some resource owners, in an effort to avoid losing their audience and reputation, even indicate a list of fake shops masquerading as them on their resource.
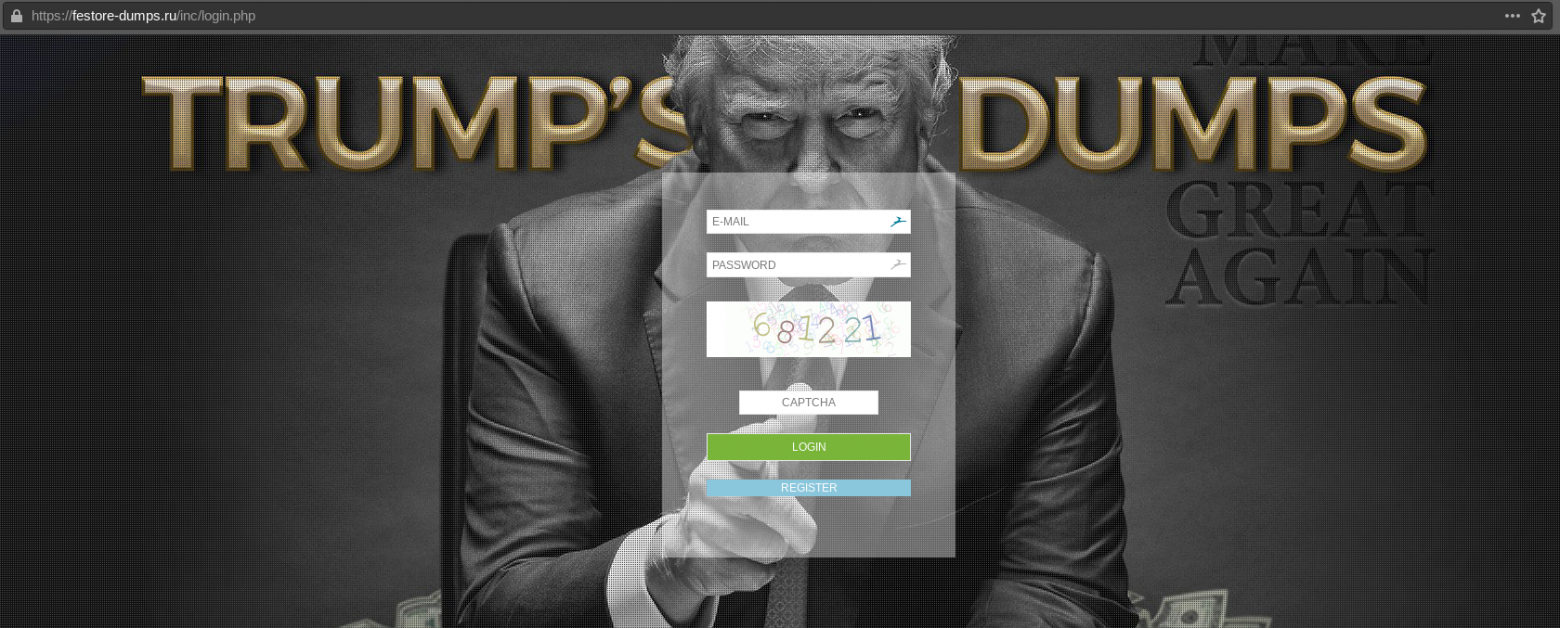
Identifying a real or fake resource is often not easy. Just like the creators of ordinary phishing web pages, the owners of fake shops try to copy the original as accurately as possible. Let's compare the authorization page of a real Ferum-shop and its fake one:
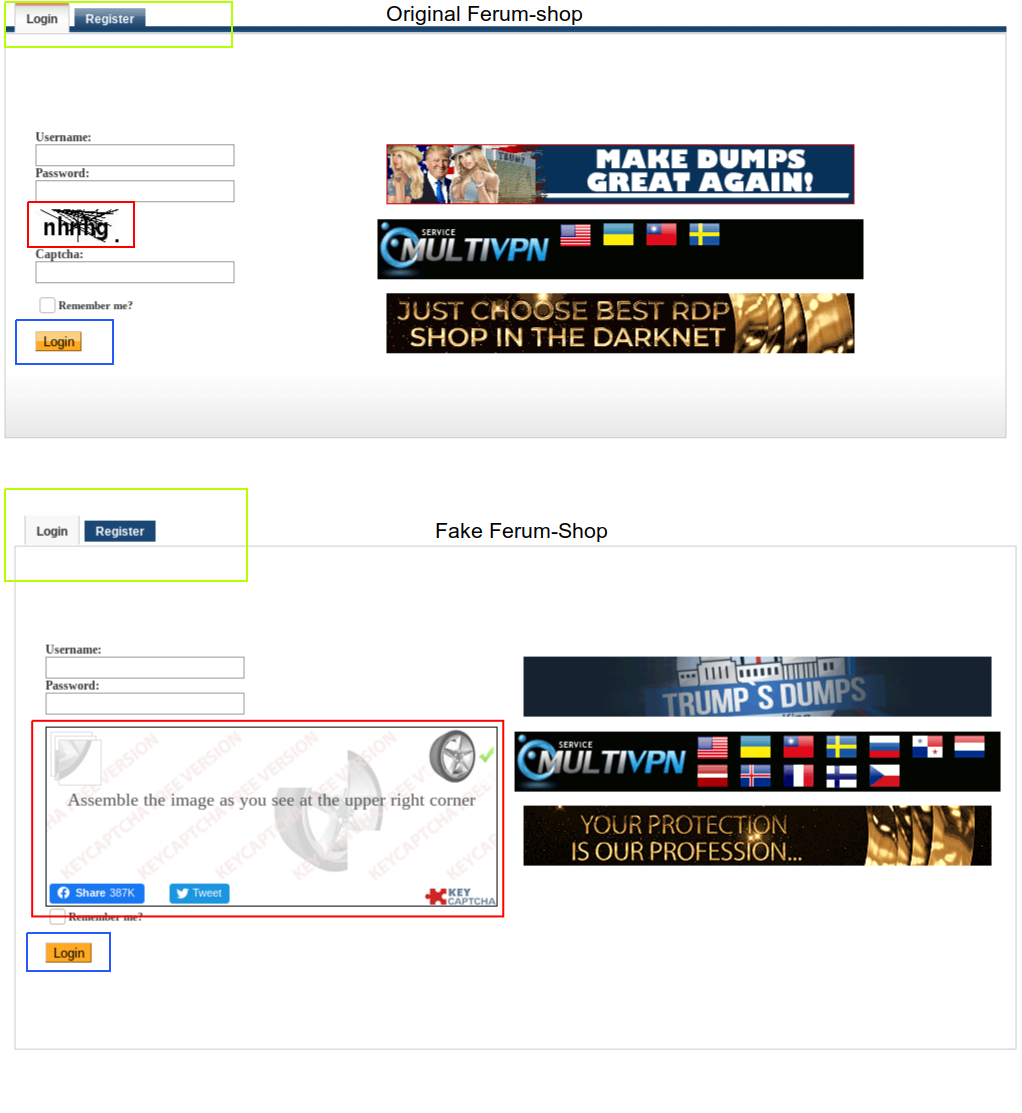
Visually, the differences are almost invisible, for example, banner ads are copied completely. However, you can pay attention to different captcha systems on the original and fake (highlighted in red). The panel designs (highlighted in green) and button designs (highlighted in blue) were also incorrectly transferred.
Such differences can easily mislead an inexperienced user, especially when the creators of the Ferum-Shop fake shop actively advertise on the forums an urgent" change " of the Yandex. Market domain name.
![Post on the sky-fraud[.]ru forum. Source: Group-IB Threat Intelligence & Attribution Post on the sky-fraud[.]ru forum. Source: Group-IB Threat Intelligence & Attribution](https://habrastorage.org/r/w1560/getpro/habr/upload_files/eff/da1/404/effda14044859dfcd951e314a3dcebcf.png)
Post on the sky-fraud.ru forum. Source: Group-IB Threat Intelligence & Attribution
Disclaimer
- The purpose of this study is to provide information on ways to commit illegal acts in order to attract the attention of state regulators and relevant authorized bodies, as well as to minimize the risk of further committing such illegal acts, prevent them in a timely manner and form an appropriate level of legal awareness among users.
- The conclusions contained in this study are made as a result of analysis by Group-IB specialists of information obtained from open sources, and in no part of it are the official position of the competent authorities, including law enforcement agencies of any jurisdiction. Information that became publicly known prior to the publication of this study is listed in its original unspoken form. The study does not contain direct accusations of committing crimes or other illegal actions and is analytical in nature.
- This research is prepared for informational and informational purposes and cannot be used by the reader for commercial or other purposes not related to education or personal non-commercial use.
- The research is subject to copyright and is protected by the norms of intellectual property law.

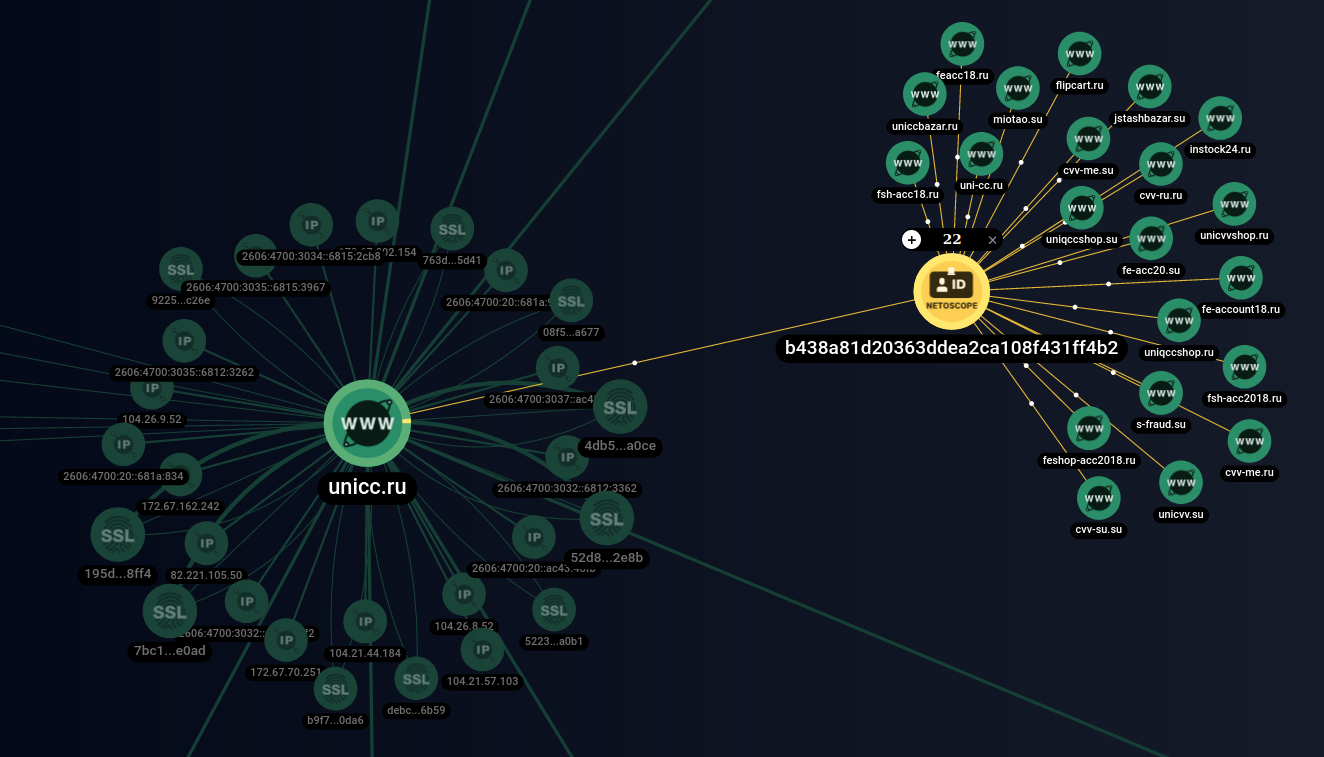
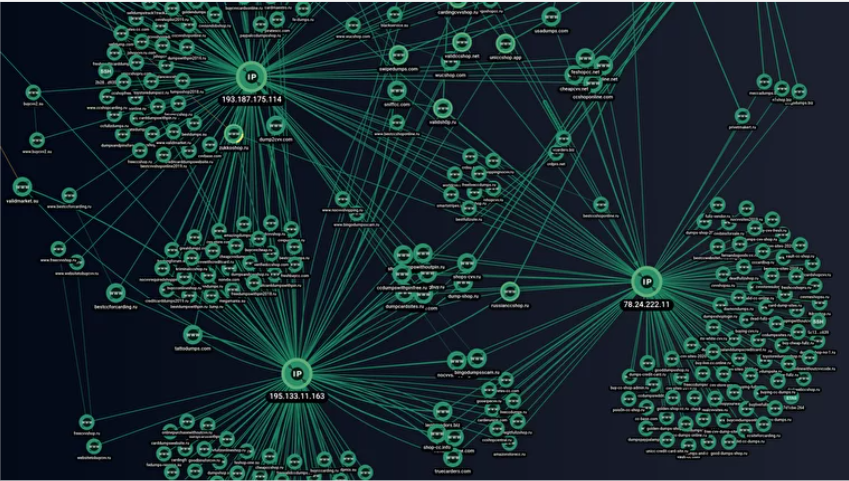
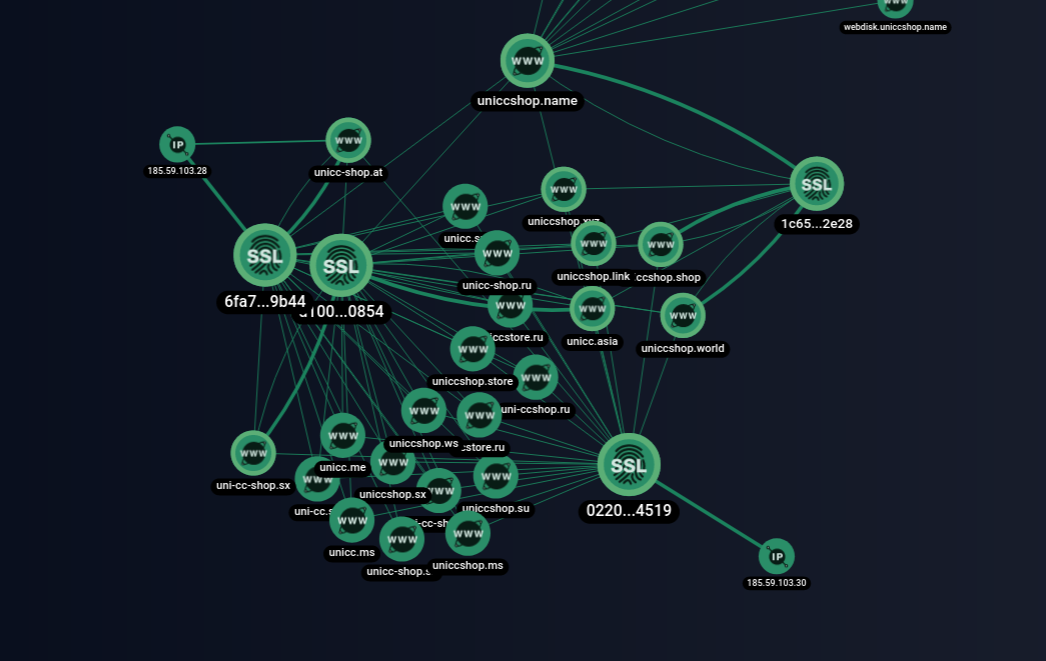
![Post on the wwh-club[.]net forum. Source: Group-IB Threat Intelligence & Attribution Post on the wwh-club[.]net forum. Source: Group-IB Threat Intelligence & Attribution](https://habrastorage.org/r/w1560/getpro/habr/upload_files/c97/b07/1c2/c97b071c2b16a77b0f77ab8df22ea6fd.png)