Social media has been deeply integrated into people's daily lives and has become an indispensable part. Whether it is obtaining information, entertainment, or social interaction and commercial marketing, social media plays a pivotal role. In the overseas expansion journey of cross-border e-commerce, overseas social media marketing platforms play a vital role. They not only provide merchants with a bridge to communicate directly with overseas consumers, but also help brands rise rapidly in overseas markets through precise positioning and wide dissemination. However, the selection, operation skills and rules of different platforms are unique, which brings considerable challenges to marketers. Among them, account blocking is one of the common problems encountered by overseas social media workers, which will not only lead to the interruption of marketing activities, but also may have a negative impact on the brand image. Therefore, how to operate safely on overseas social media platforms and reduce the blocking rate has become the focus of many cross-border e-commerce sellers. To this end, this article will review the popular overseas social media platforms in 2024, and deeply analyze the operating rules and anti-blocking strategies of each platform to help your overseas marketing journey smoother!
1. Overview of popular overseas social media marketing platforms in 2024
With the increasing importance of content strategy, the marketing method of a single platform can no longer meet the needs. Multi-platform, multi-account matrix operation has become a new trend. There are many overseas social media platforms, each with its own characteristics, which can be roughly divided into the following categories:
Video-dominated category: Short videos are gradually becoming a trend in social media, leading the future trend. This type of platform uses short videos as the main content form, focusing on the user's visual experience and interactivity. Among them, TikTok and YouTube are the leaders in this field. They not only have a large user base, but also provide content creators with a broad display space through unique algorithms and recommendation mechanisms. Video e-commerce has also emerged and become the new favorite of cross-border e-commerce.
Social-dominated category: Social e-commerce has always had a high return rate and is easier to achieve fission propagation. This type of platform is centered on social networking and focuses on interaction and sharing between users. Messenger, Twitter, LinkedIn, Snapchat, Zalo, Slack and other platforms have their own characteristics, but the common point is that they all have a large user base and a highly active social atmosphere. Merchants can use these platforms for a variety of marketing activities such as brand promotion, customer service, and market research.
Picture-dominated category: Pictures are one of the most primitive ways of displaying social media and the main way of celebrity marketing. Platforms such as Instagram, Pinterest, and Facebook use pictures as the main content form, focusing on the user's visual experience and aesthetic feelings. These platforms are suitable for a variety of marketing activities such as product display, brand promotion, and celebrity cooperation.
Text-dominated: Text is more suitable for soft text output, and the forum format is easier to target customers. Platforms such as Quora, Reddit, and Discord use text as the main content form, focusing on user thinking and communication. These platforms are suitable for a variety of activities such as knowledge sharing, exchange of views, and community marketing. Merchants can use these platforms to interact and communicate in depth with potential customers to improve brand awareness and reputation.
These platforms have their own characteristics and have different user groups and marketing potential. Cross-border sellers need to have a deep understanding of the characteristics, user portraits, and marketing rules of each platform in order to choose the platform that best suits their product positioning for operation.
2. Interpretation of anti-blocking rules of overseas social media platforms
Most of the blocking problems are caused by the lack of understanding or neglect of platform rules. In order to reduce the blocking rate, merchants must have a deep understanding of and strictly abide by the anti-blocking rules of each platform. The following are the account blocking rules and multi-account strategies of several major platforms:
Facebook: A user is only allowed to have one account. If multiple accounts are detected, all accounts related to the main account will be blocked. Therefore, when operating Facebook, merchants must ensure the independence and compliance of each account.
TikTok: A user is allowed to have up to 3 accounts. There are associations and traffic restrictions between multiple accounts, and the ban has a joint responsibility mechanism. When operating TikTok, merchants need to carefully handle the relationship between multiple accounts to avoid associations and violations.
Instagram: A user is allowed to have up to 5 accounts. Abnormal or detected activities of multiple accounts will result in all accounts related to the main account being blocked. When operating Instagram, merchants need to pay close attention to the activities of each account to ensure compliance.
LinkedIn: A user is only allowed to have one account. If multiple accounts are detected, all accounts related to the main account will be blocked. When operating LinkedIn, merchants need to pay attention to the compliance and professionalism of the account.
Twitter: A user is only allowed to have one account, and multiple accounts with the same activities (such as interacting with the same user, posting the same tweets, etc.) will be blocked. However, when other accounts are suspended for this reason, one account is allowed to be retained. When operating Twitter, merchants need to avoid duplicate content and excessive marketing behavior.
Reddit: In principle, the official allows the use of multiple accounts, but Redditors are often blocked by mistake. If they are reported, there will be a joint responsibility mechanism to block related accounts. When operating Reddit, merchants need to pay attention to the independence and compliance of accounts to avoid being blocked by mistake or being punished by association.
3. Strategies and practices to reduce account blocking rates
In order to reduce account blocking rates, merchants need to adopt a series of effective strategies and practices. Here are some suggestions:
In-depth understanding and compliance with the rules and policies of each platform: This is the basis for reducing the blocking rate. Merchants need to spend time and energy to study the rules and policies of each platform to ensure that their marketing activities meet the requirements of the platform.
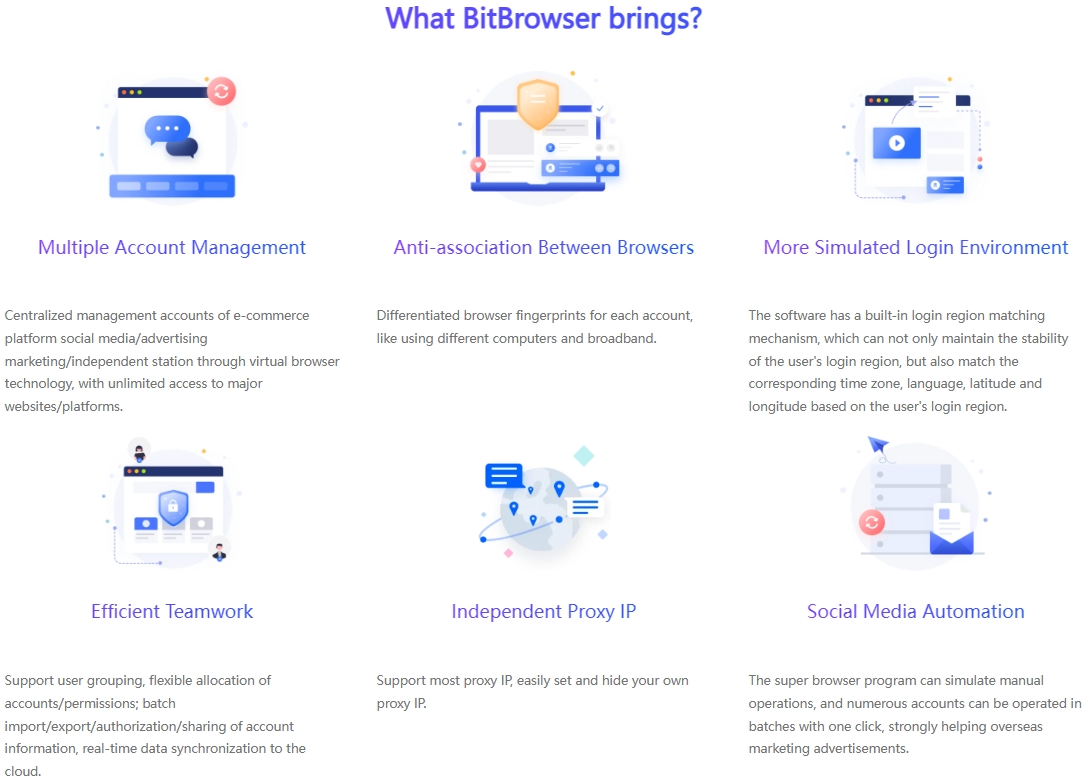
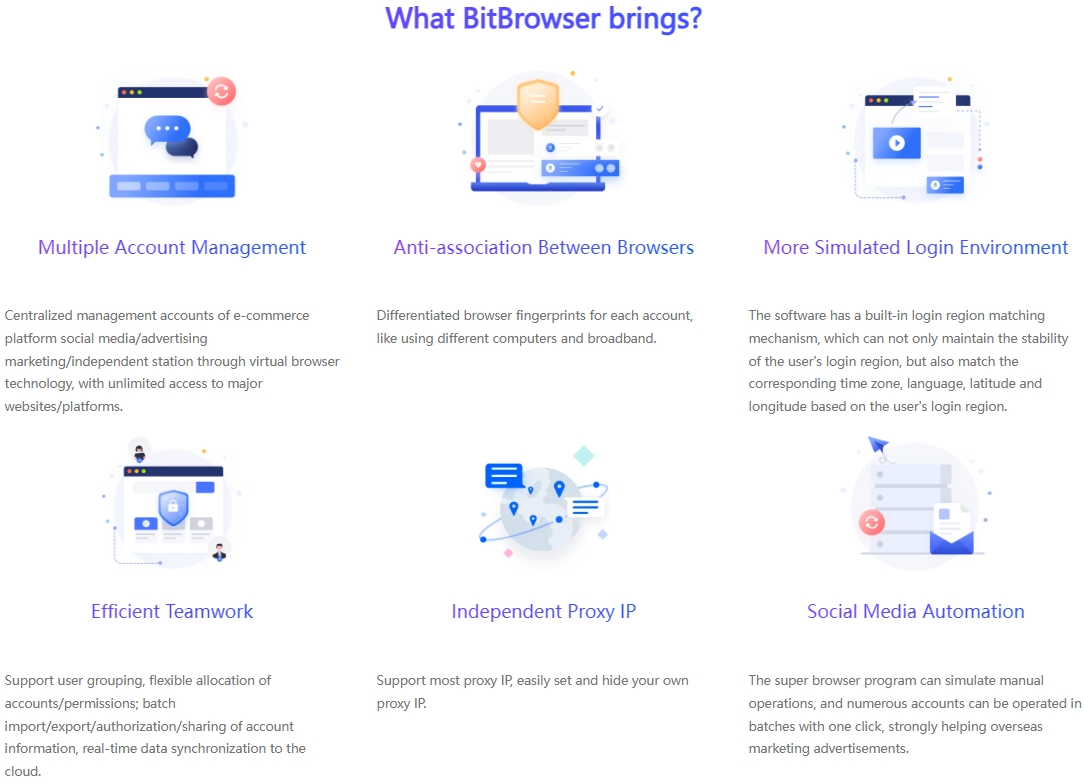
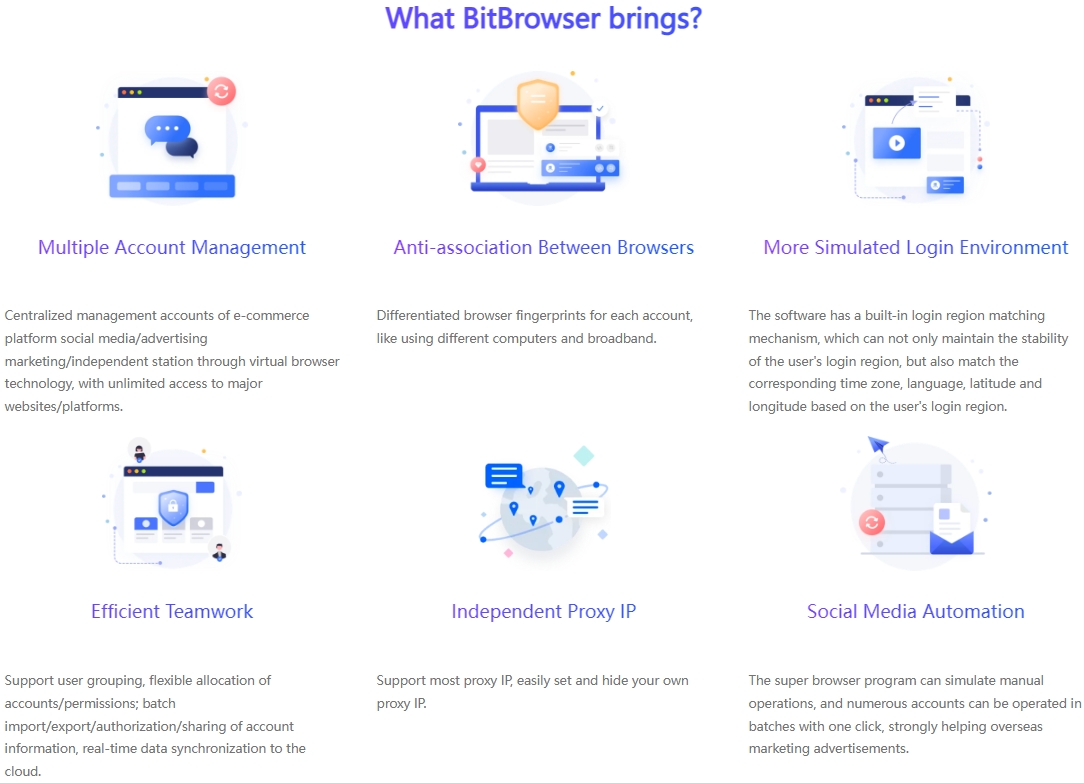
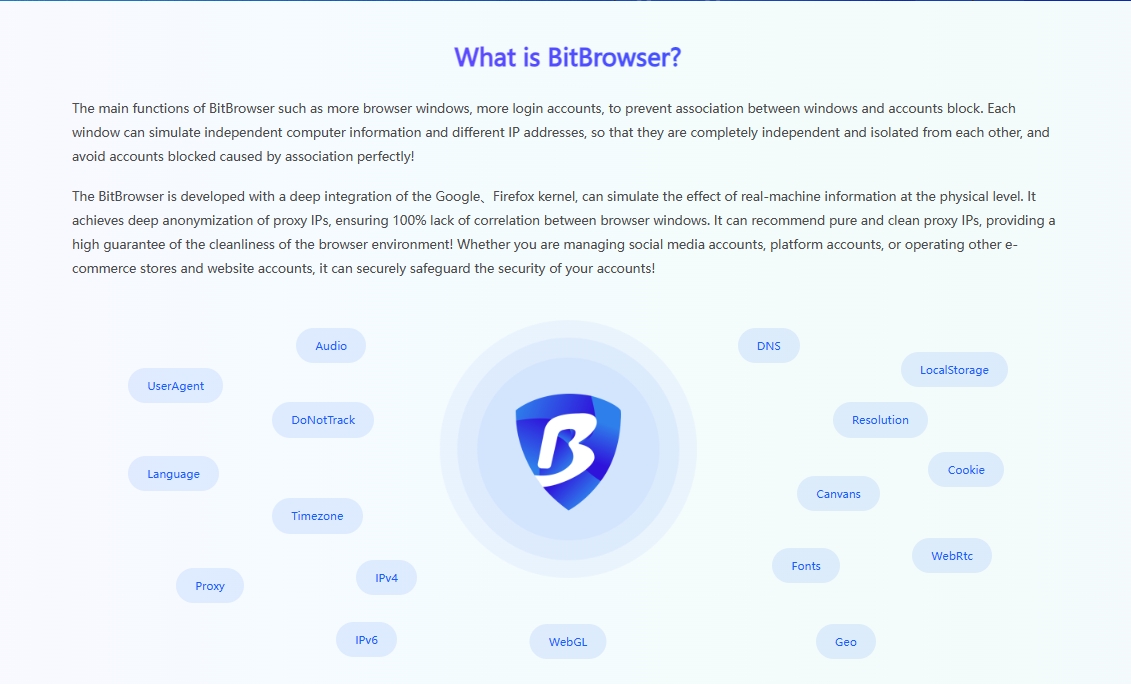
Use professional social media management tools: These tools can help merchants better manage multi-platform and multi-account operations and improve efficiency and compliance. For example, using the fingerprint browser, you can customize the generation of multiple unique and pure fingerprint environments to ensure the uniqueness of the account environment; using IP login to generate associations, on the basis of browser isolation, BitBrowser Fingerprint Browser also recommends a stable and clean IP, which is convenient for everyone to find IP content suitable for their own projects.
If your business has the situation of social media account maintenance, you will inevitably face mechanical and repetitive operations. In the past, these operations were all handled manually, but now, such work can be completed by BitBrowser's RPA robot.
RPA (Robotic Process Automation), that is, robotic process automation. When mentioning robots, processes, and automation, do you think of the factory assembly line, where robots are responsible for completing the operation of each component throughout the process?
BitBrowser Automation (RPA) supports you to achieve tasks that originally required scripting through simple drag-and-drop operations. This low-code model greatly reduces the technical difficulty. Even operators without programming foundation can set up and execute complex automation processes without pressure, such as automatic login, attention, browsing posts, automatic collection of products, etc.
Through the window group control function of BitBrowser Fingerprint Browser, users can open multiple browser pages and perform the same operation in multiple independent browser windows without switching accounts and windows one by one. This greatly improves work efficiency, especially for operators who manage a large number of social accounts.
Summary:
In 2024, using social media for marketing is still a popular solution. Among them, using social media to expand matrix marketing is the choice of most social media marketers, but using multiple accounts for social media matrix marketing will undoubtedly bring the trouble of easy account blocking. BitBrowser solves this problem very well.
BitBrowser Fingerprint Browser uses independent IP and unique browser fingerprint anti-detection technology to completely prevent account association and account blocking, and maximize the protection of social media account security.