Now, let’s discuss the potential of advertising on the TikTok Ads platform. TikTok, a social network, is like a sudden dark horse, rising rapidly in the field of digital advertising. Although it is now sanctioned by the United States, TikTok is still There is huge potential in the international market. Next, we will analyze in detail the strengths and weaknesses of TikTok advertising, and whether it is appropriate for you to invest advertising resources after TikTok is sanctioned by the United States.
What exactly is TikTok advertising?
TikTok Ads, to put it bluntly, is the advertising service provided by the TikTok platform. It allows advertisers to build and control advertising campaigns on TikTok, thereby reaching target groups around the world. In the previous article, we also gave you a detailed analysis of how to build your own brand on TikTok. Click here to visit the original text:
E-commerce How to build a brand on TikTok when going overseas? Detailed strategic analysis. On TikTok, the advertising categories that advertisers can use mainly include the following:
Shocking opening ad: When users open the TikTok app, the first thing that pops into their eyes is this full-screen video ad.
Brand domination of the screen: This is an extremely conspicuous form of advertising that takes up the entire screen when a user launches the app. This type of advertising can be used in conjunction with opening shocks, feeds, and branded hashtags. However, it should be noted that TikTok only accepts one company's brand screen advertising per day, and the starting price is usually US$50,000 per day.
Information feed ads: This ad will appear while users are browsing TikTok content. The video can contain a clear call to action (CTA), which is very suitable for marketers who want to drive sales conversions.
Hashtag Challenge: This is an interactive advertising format that encourages users to participate and create content.
Brand effects: This refers to the video effects and filters with brand characteristics that users can use. This is a way for brands to incentivize TikTok users to create content using specific hashtags.
Advantages of TikTok advertising:
Powerful influence: TikTok’s user base is huge and highly active, providing advertisers with considerable exposure opportunities.
Endless creativity: TikTok provides a variety of advertising formats, allowing advertisers to fully display their creative talents.
High level of participation: Ads on TikTok often trigger active interactions among users and improve advertising effectiveness.
Precise positioning: The TikTok Ads platform has detailed positioning options to help advertisers accurately reach their target audience.
Cooperate with influencers: Cooperating with influencers on TikTok can effectively increase the visibility and influence of advertising.
Disadvantages of TikTok advertising:
Potentially high costs: Compared with other platforms, TikTok’s advertising costs may be higher, especially for certain targeting and advertising types.
Concentration of young users: TikTok’s users are mainly among young people, which may not fit the target audience of all advertisers.
Uncertainty in the regulatory environment: In regions such as the United States, TikTok’s regulatory environment and future development are uncertain, which may bring certain risks to advertisers.
U.S. Sanctions on TikTok:
On May 7, TikTok resolutely submitted a lawsuit to the U.S. Federal Court, strongly requesting the court to judge that the "Protecting Americans from Foreign Adversaries Controlled Applications Act" that intends to ban TikTok is contrary to the U.S. Constitution, and To stop the enforcement of this law.
TikTok complained that the "sell or ban" law passed by the US government has seriously infringed on users' rights under the First Amendment and has also caused great harm to small, medium and micro enterprises that rely on TikTok to survive.
Do you still want to do advertising and marketing on TikTok?
First of all, be sure to stay calm and don’t panic!
Regarding this incident, although it is difficult to draw a clear conclusion in the short term, related news and popularity will inevitably continue during this period. At the same time, as far as TikTok is concerned, its traffic and popularity are likely to increase. Another round of growth ushered in. It is expected that users' usage time and frequency of use will increase to a certain extent. Whether they are TikTok users or companies that use this platform to carry out commercial activities, they all hope to benefit from it and usher in more development opportunities, and carry out multi-channel Operations can help companies reduce the risk of relying on a single platform. In addition, it is also critical to always maintain a flexible and innovative mindset and actively explore new ways to attract users.
Whether you still want to market on TikTok depends mainly on your company goals, budget, and target audience. If you hope to attract a young and highly engaged audience, and are willing to try new and innovative advertising forms, then TikTok advertising is a no-brainer is an option worth considering. However, if your target audience is primarily located on other platforms, or if you wish to avoid the uncertainty associated with regulatory risks, then some careful consideration may be required.
How should a marketer respond?
1. Strategic changes
Once TikTok faces difficulties due to policy changes, merchants must act immediately to explore new sales channels to ensure the smooth sustainability of their business. In this case, e-commerce platforms such as Shopify, Shopline or Shopyy become very good alternatives. The focus is on how to ensure that transactions conducted on these new platforms are both safe and efficient.
2. Optimize traffic planning
Increase advertising efforts: With the help of TikTok’s advertising system, precise positioning and extensive coverage of target audiences, products can be quickly introduced to the market.
Carefully create short video content: closely combine the characteristics of the product with the preferences of the target audience to produce a highly attractive short video, and display the product in the form of a story to attract users' attention.
Create an atmosphere of enthusiastic purchase: While displaying products, through social interaction and word-of-mouth communication, create an atmosphere where everyone is buying, thereby enhancing users' desire to purchase.
3. Multi-account operation
Rapidly spread brand information: Through the multi-account operation model, companies can quickly convey brand information to a wider range of people, enhancing brand exposure and awareness.
The powerful performance of
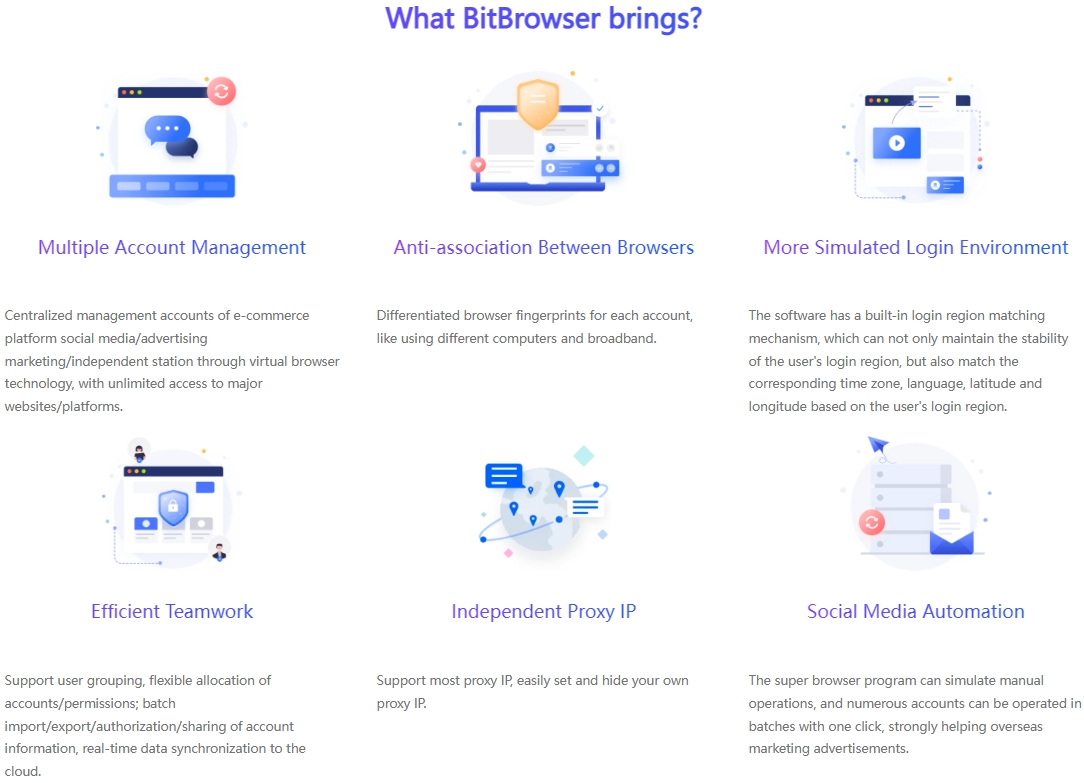
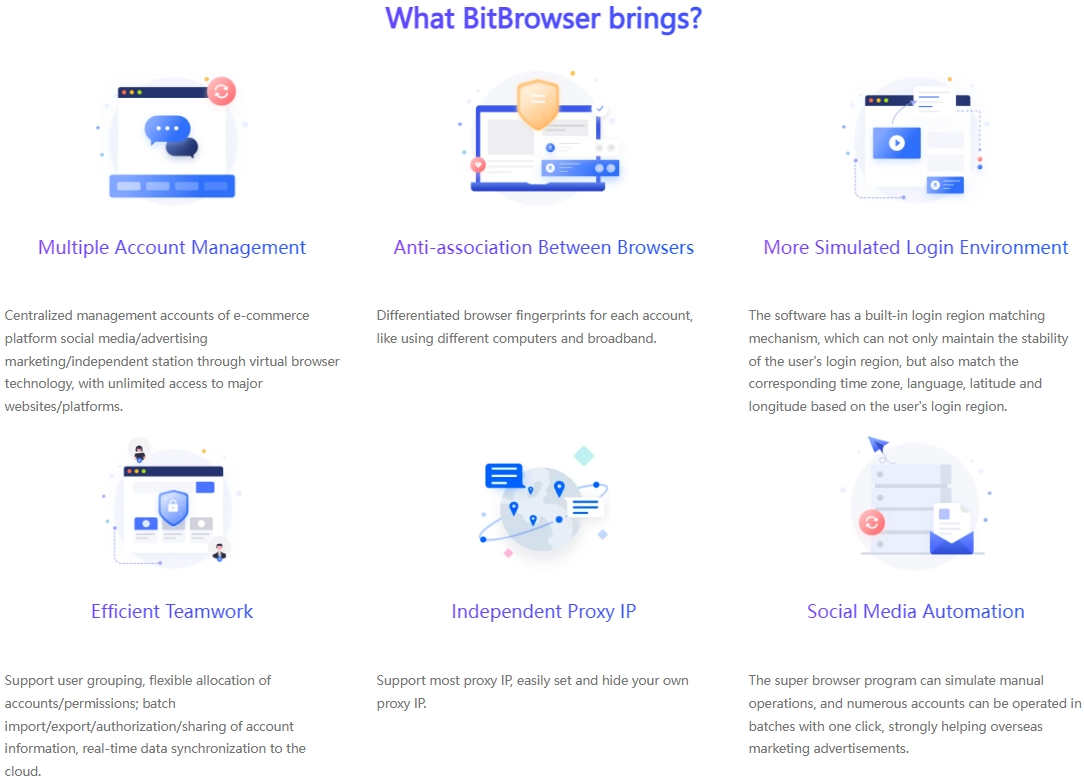
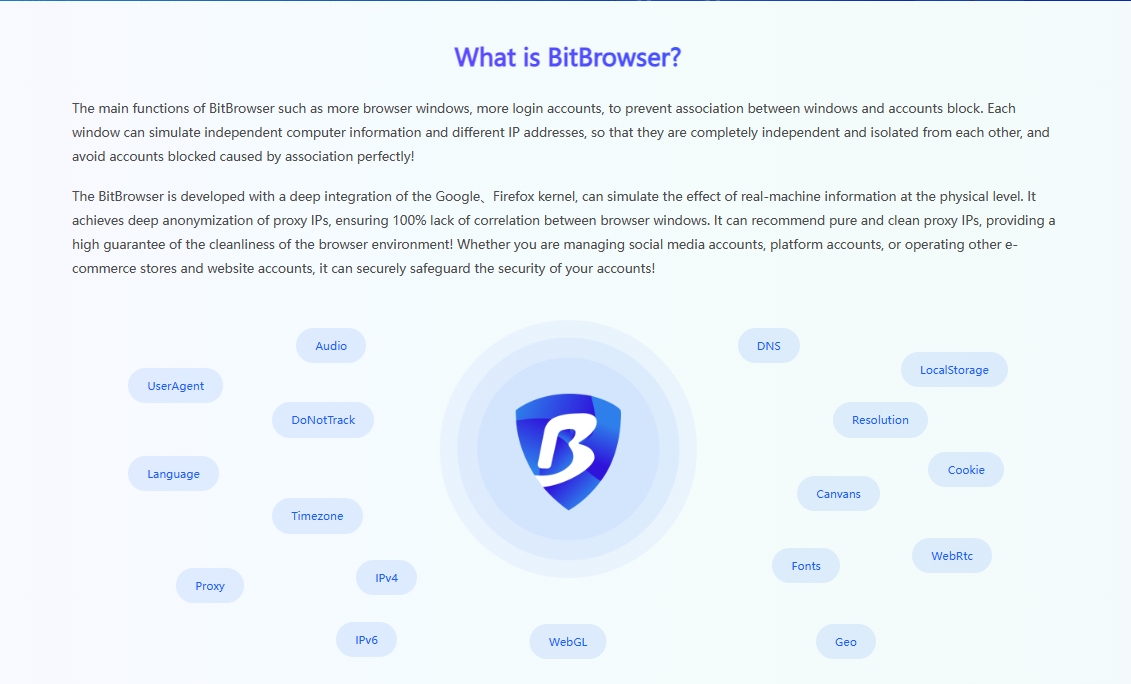
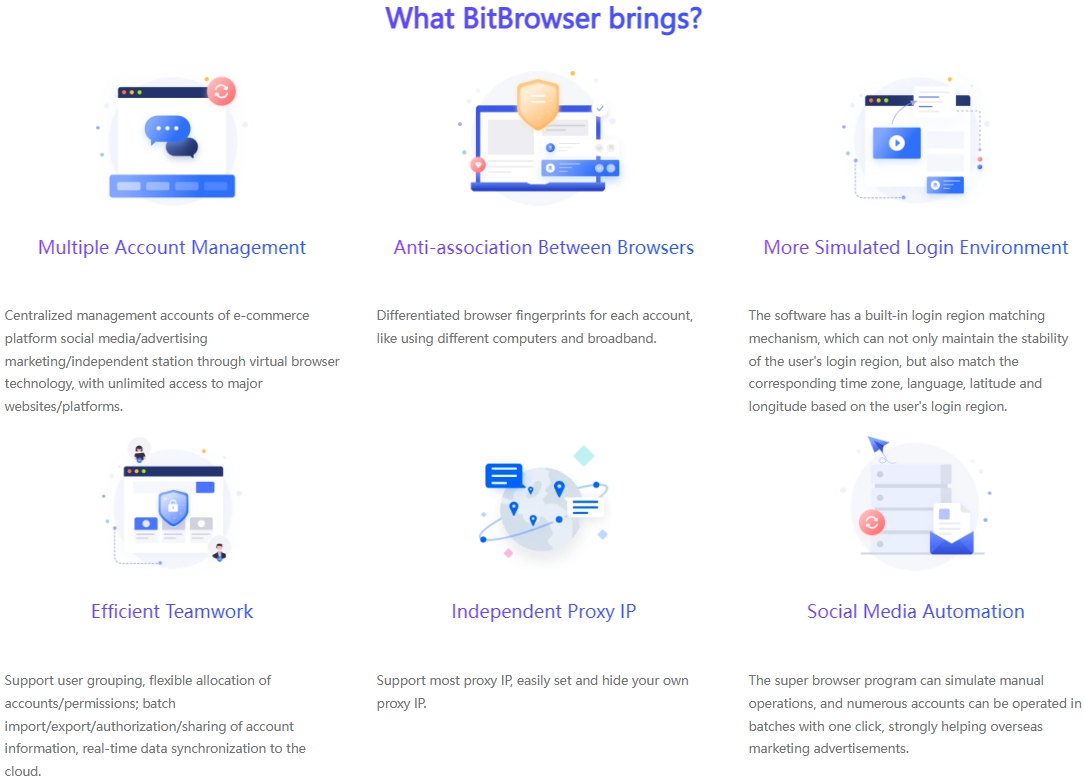
BitBrowser: Using the group control system of BitBrowser, multiple windows can be controlled at the same time to achieve synchronized mouse and keyboard operations, which greatly improves operational efficiency. Moreover, its fingerprint management function can generate numerous virtual identities and deeply hide users' cookies, effectively avoiding the risk of account suspension caused by association between accounts.
Ensure the sustained and steady development of business: By operating multiple accounts, companies can diversify risks. Even if there is a problem with one account, it will not have a big impact on the overall business. At the same time, it can continue to enhance the influence of the brand. Visit BitBrowser here Learn the in-depth details of the multi-account matrix in this article:
Building a TikTok account matrix, a multi-account rapid traffic drainage solution.
Summarize:
TikTok ads provide advertisers with a new channel to interact with young, highly engaged audiences. U.S. sanctions have had an uncertain impact on the development of TikTok, but this does not affect TikTok’s development in the global market. TikTok ads are still a Open up important channels for overseas markets.
Finally, before deciding to invest, be sure to evaluate your business goals, budget, region, and target audience, and use multiple advertising accounts through
BitBrowser, and continue to try and adjust, you can get the best advertising effect on TikTok .