Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
RCS messages - a new loophole for attacks on Android and iPhone users.
Netcraft has discovered a new phishing service called Darcula, which uses more than 20,000 domains to mimic popular brands and steal the credentials of Android and iPhone users in more than 100 countries.
The PHAAS service Darcula stands out from other similar services for its approach to distributing phishing messages: instead of traditional SMS, attackers use RCS protocols (Rich Communication Services) for Google Messages and iMessage, which makes messages look more convincing and circumvent some security measures.
The service offers its customers more than 200 templates for creating phishing pages that mimic the interfaces of well-known organizations, including financial institutions, government services, telecommunications companies and airlines. The created pages are of high quality and use local languages, logos, and content.
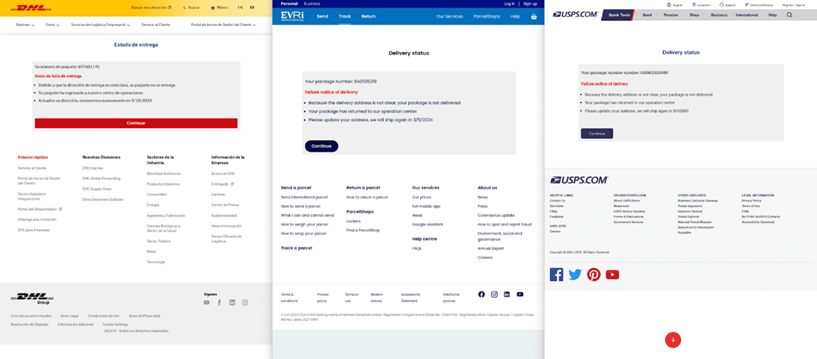
Phishing templates for various services
Cybercriminals choose a brand to imitate and run an installation script that deploys the corresponding phishing site in the Docker environment. The system uses the open Harbor container registry for hosting the Docker image, and the sites themselves are developed on React.
Netcraft analysts note that Darcula typically uses the ".top" and ".com " top-level domains to host phishing attacks, with about a third of them protected by Cloudflare. A total of 20,000 Darcula-related domains were identified, located on 11,000 IP addresses. It is noted that about 120 new domains are added daily.
Moving away from SMS and switching to RCS and iMessage makes phishing messages less susceptible to content-based blocking thanks to End-to-End encryption (E2EE) support. Innovations in legislation aimed at combating cybercrime via SMS, most likely, stimulated the transition to such protocols.
The advantage of using RCS is that recipients are more likely to believe the message by relying on additional guarantees that are not available in SMS.
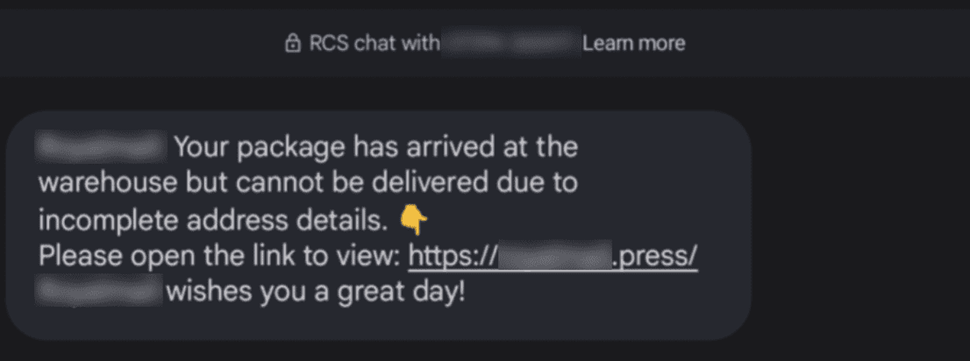
RCS message that directs victims to a phishing site
Users should be careful with all incoming messages that encourage them to click on links, especially if the sender is unknown. Grammar inaccuracies, spelling mistakes, overly attractive sentences, or urgent calls to action should arouse suspicion.
Netcraft has discovered a new phishing service called Darcula, which uses more than 20,000 domains to mimic popular brands and steal the credentials of Android and iPhone users in more than 100 countries.
The PHAAS service Darcula stands out from other similar services for its approach to distributing phishing messages: instead of traditional SMS, attackers use RCS protocols (Rich Communication Services) for Google Messages and iMessage, which makes messages look more convincing and circumvent some security measures.
The service offers its customers more than 200 templates for creating phishing pages that mimic the interfaces of well-known organizations, including financial institutions, government services, telecommunications companies and airlines. The created pages are of high quality and use local languages, logos, and content.

Phishing templates for various services
Cybercriminals choose a brand to imitate and run an installation script that deploys the corresponding phishing site in the Docker environment. The system uses the open Harbor container registry for hosting the Docker image, and the sites themselves are developed on React.
Netcraft analysts note that Darcula typically uses the ".top" and ".com " top-level domains to host phishing attacks, with about a third of them protected by Cloudflare. A total of 20,000 Darcula-related domains were identified, located on 11,000 IP addresses. It is noted that about 120 new domains are added daily.
Moving away from SMS and switching to RCS and iMessage makes phishing messages less susceptible to content-based blocking thanks to End-to-End encryption (E2EE) support. Innovations in legislation aimed at combating cybercrime via SMS, most likely, stimulated the transition to such protocols.
The advantage of using RCS is that recipients are more likely to believe the message by relying on additional guarantees that are not available in SMS.

RCS message that directs victims to a phishing site
Users should be careful with all incoming messages that encourage them to click on links, especially if the sender is unknown. Grammar inaccuracies, spelling mistakes, overly attractive sentences, or urgent calls to action should arouse suspicion.

