Teacher
Professional
- Messages
- 2,669
- Reaction score
- 827
- Points
- 113
Zero-Click Attacks or 0-click attacks are an interesting form of cyberattack that attackers implement without any user interaction. What is the risk of data compromise on a mobile device running iOS or Android when using wireless communication channels (GSM, Wi-Fi, NFC)? How can I protect myself from an attack that is not visible and the beginning of which is almost impossible to track?
Introduction
The proliferation of mobile networks, Wi-Fi, and contactless payment (Near Field Communication, NFC) capabilities, the complexity of mobile application functionality, and the availability of processing, receiving, and storing confidential and personal information make various gadgets attractive to an attacker due to the large attack area. A mobile device can be compromised by sending an SMS / MMS message with a special set of data, via a wireless Wi-Fi network, an NFC chip, or a messenger application such as WhatsApp, iMessages, or Viber.
In turn, the user may not realize that their mobile device has been attacked or hacked, that control over it has been lost, and that the attacker is able to remotely control some application functions — or at least read data stored in the device's memory.
It is worth noting that the 0-click problem has reached significant proportions in recent years. For example, in May 2020, it became known that a similar breach affects all Samsung smartphones released since 2014. And just a week ago, information appeared about Zero-Click in Hikvision firmware, which already threatened more than 100 million IoT devices. There was also a lot of concern about the 0-click worm in Microsoft Teams, which allowed malicious code to be executed remotely.
The main problem with protecting against this type of attack is that the user does not need to take any actions to succeed. In most scenarios, it is sufficient for the mobile device to be within wireless range or for the attacker to have the phone number of the target.
What is known about Zero-Click attacks
The basis of the Zero-Click attack is to gain control of the victim's mobile device without her noticing it, without using social engineering mechanisms. The human factor is excluded both on the part of the attacker and on the part of the attacked person. Article Published by ZecOps specialists, it reveals the topic of a Zero-Click attack based on the MobileMail iOS app: specialists managed to gain remote access to email on the device under test, while hiding traces of infection and deleting their emails. Also in 2015, Edward Snowden warned that interested government agencies have the ability to develop and create previously unknown spyware programs that can infect a user's device through ordinary text messages. Well-known examples of attack implementation include the following:
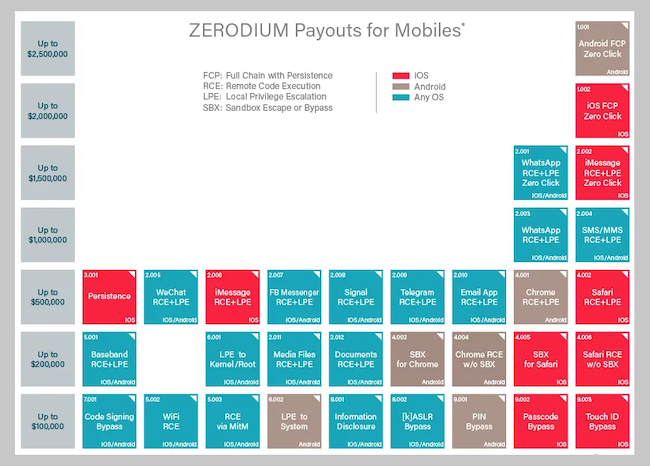
Price list for ready-made exploits for mobile operating systems
Basic principles of the Zero-Click attack
Zero-Click attacks in most cases target applications that exchange text and media messages or allow the use of VoIP voice calls, since such programs do not analyze incoming information. Attackers use specially generated data, such as a special text or media file with embedded hidden code that is executed when processing a message even before the user reads it.
When exploiting vulnerabilities in a particular application, an attacker will only gain access to the attacked program, without achieving control of the entire device as a whole. To extend rights on the victim's device, it is necessary to exploit other vulnerabilities — at the level of the operating system or the peripheral or central processor responsible for processing data from a specific application.
How to implement a Zero-Click attack
There are few examples of implementing Zero-Click attacks, because it may be impossible to track the attack itself — as well as to get evidence that control over the device or data leakage occurred precisely because of it. For example, in the final report of criminologists in the case of Jeff Bezos ' mobile phone, there are no facts of using the Zero-Click attack, only the facts that the outgoing traffic of the device increased after receiving a suspicious media file are indicated.
The main facts of real or potential use of exploits transmitted using 0-click attacks are vulnerabilities discovered and published in the framework of research on applications, mobile operating systems, and hardware. In particular, the BlackHat USA 2019 forum published materials on a possible attack on the FaceTime app and Qualcomm chips, and the CVE-2019-2009 vulnerability was published regarding the Bluetooth data transmission channel, which allows you to increase privileges on an Android device without the end user's participation up to the 9th OS version.
The main steps of the attack can be described in three points:
Of the current incidents, it is worth highlighting the distribution of the Pegasus spy program, which was found on the mobile devices of French journalists. Methods of its distribution also include Zero-Click attacks.
How to protect yourself from Zero-Click attacks
Experts report that the dominance of iOS over Android in terms of information security has long ended and Google pays much more attention to protecting the Chrome browser and the Android OS as a whole than Apple pays to the Safari browser. On average, the price of a non-interactive exploit in the shadow market is 30% higher for Android than for iOS. Experts also specify that finding vulnerabilities for privilege escalation on Android in general is a more complex and expensive task.
You can give some general tips on how to minimize the likelihood of being exposed to this type of attack:
Conclusions
Currently, we can conclude that non-interactive attacks, if successful, are critically dangerous for the attacker, but the risk of their implementation is low due to the complexity of creating workable exploits. It is also worth noting that protection against Zero-Click attacks should be primarily concerned with the heads of private or public companies, as well as those who have confidential information at their disposal on personal or corporate mobile devices.
Introduction
The proliferation of mobile networks, Wi-Fi, and contactless payment (Near Field Communication, NFC) capabilities, the complexity of mobile application functionality, and the availability of processing, receiving, and storing confidential and personal information make various gadgets attractive to an attacker due to the large attack area. A mobile device can be compromised by sending an SMS / MMS message with a special set of data, via a wireless Wi-Fi network, an NFC chip, or a messenger application such as WhatsApp, iMessages, or Viber.
In turn, the user may not realize that their mobile device has been attacked or hacked, that control over it has been lost, and that the attacker is able to remotely control some application functions — or at least read data stored in the device's memory.
It is worth noting that the 0-click problem has reached significant proportions in recent years. For example, in May 2020, it became known that a similar breach affects all Samsung smartphones released since 2014. And just a week ago, information appeared about Zero-Click in Hikvision firmware, which already threatened more than 100 million IoT devices. There was also a lot of concern about the 0-click worm in Microsoft Teams, which allowed malicious code to be executed remotely.
The main problem with protecting against this type of attack is that the user does not need to take any actions to succeed. In most scenarios, it is sufficient for the mobile device to be within wireless range or for the attacker to have the phone number of the target.
What is known about Zero-Click attacks
The basis of the Zero-Click attack is to gain control of the victim's mobile device without her noticing it, without using social engineering mechanisms. The human factor is excluded both on the part of the attacker and on the part of the attacked person. Article Published by ZecOps specialists, it reveals the topic of a Zero-Click attack based on the MobileMail iOS app: specialists managed to gain remote access to email on the device under test, while hiding traces of infection and deleting their emails. Also in 2015, Edward Snowden warned that interested government agencies have the ability to develop and create previously unknown spyware programs that can infect a user's device through ordinary text messages. Well-known examples of attack implementation include the following:
- The alleged hacking of the mobile phone of Amazon founder Jeff Bezos in 2018 through a specially prepared video file transmitted to him in the WhatsApp messenger. After that, the phone began to "leak" large amounts of data for several months, until the leak was discovered and the phone was handed over for examination.
- Exploiting WhatsApp vulnerabilities to install malware by calling the victim using IP telephony (VoIP) in 2019. The fact that the vulnerability is present and exploitable has led to a lawsuit between Facebook (the owner of WhatsApp) and the spyware vendor.

Price list for ready-made exploits for mobile operating systems
Basic principles of the Zero-Click attack
Zero-Click attacks in most cases target applications that exchange text and media messages or allow the use of VoIP voice calls, since such programs do not analyze incoming information. Attackers use specially generated data, such as a special text or media file with embedded hidden code that is executed when processing a message even before the user reads it.
When exploiting vulnerabilities in a particular application, an attacker will only gain access to the attacked program, without achieving control of the entire device as a whole. To extend rights on the victim's device, it is necessary to exploit other vulnerabilities — at the level of the operating system or the peripheral or central processor responsible for processing data from a specific application.
How to implement a Zero-Click attack
There are few examples of implementing Zero-Click attacks, because it may be impossible to track the attack itself — as well as to get evidence that control over the device or data leakage occurred precisely because of it. For example, in the final report of criminologists in the case of Jeff Bezos ' mobile phone, there are no facts of using the Zero-Click attack, only the facts that the outgoing traffic of the device increased after receiving a suspicious media file are indicated.
The main facts of real or potential use of exploits transmitted using 0-click attacks are vulnerabilities discovered and published in the framework of research on applications, mobile operating systems, and hardware. In particular, the BlackHat USA 2019 forum published materials on a possible attack on the FaceTime app and Qualcomm chips, and the CVE-2019-2009 vulnerability was published regarding the Bluetooth data transmission channel, which allows you to increase privileges on an Android device without the end user's participation up to the 9th OS version.
The main steps of the attack can be described in three points:
- An attacker discovers a new vulnerability in the mobile application, in the data transmission channel, in the mobile OS, and in general in what can be used to transmit information to a mobile device. In some cases, a vulnerability can be exploited that was discovered earlier, but was not considered as a tool for Zero-Click attacks.
- In accordance with the channel, a data package is created for exploiting the vulnerability and implementing a malicious program (payload) on the victim's device.
- After fixing the spyware program in the device OS, the initial message is deleted, removing any traces of compromise.
Of the current incidents, it is worth highlighting the distribution of the Pegasus spy program, which was found on the mobile devices of French journalists. Methods of its distribution also include Zero-Click attacks.
How to protect yourself from Zero-Click attacks
Experts report that the dominance of iOS over Android in terms of information security has long ended and Google pays much more attention to protecting the Chrome browser and the Android OS as a whole than Apple pays to the Safari browser. On average, the price of a non-interactive exploit in the shadow market is 30% higher for Android than for iOS. Experts also specify that finding vulnerabilities for privilege escalation on Android in general is a more complex and expensive task.
You can give some general tips on how to minimize the likelihood of being exposed to this type of attack:
- Without knowing about you, the attacker will not detect you. A small number of individuals, sites, and apps that know your phone number reduces the risk of an attack, and if your device is compromised, it narrows the circle of suspects.
- No communication channel — no transmission capability. If you are not currently (or in principle) using Wi-Fi, NFC, or Bluetooth, then disable them. Disable automatic pairing of Bluetooth devices and automatic Wi-Fi connectivity when access points are detected.
- Do not jailbreak or root your device. This significantly increases the risk of not only elevating privileges for third-party software, but also working on behalf of the system without exploiting vulnerabilities.
- Use only the official app stores. This will significantly reduce the risk of downloading an app with a backdoor or built-in spyware.
- Fewer apps means fewer attack vectors. Every unnecessary program on the device increases the likelihood that there will be a vulnerability somewhere that can be exploited.
- Regular updates. Software developers fix vulnerabilities (even if not always promptly) in supported products. You also need to check for updates at the device OS level.
- Separate device functions. It is not recommended to use a personal device to perform work duties and store confidential information. Let the compromise of a corporate device lead to a leak of only business data, and a possible hacking of a personal gadget will affect only you.
- You are already compromised. Use your mobile device as if you've already been hacked. Discuss cases in person, and do not store personal and confidential information or business correspondence on your device. This strategy will reduce the damage caused by a 0-click attack to steal information.
Conclusions
Currently, we can conclude that non-interactive attacks, if successful, are critically dangerous for the attacker, but the risk of their implementation is low due to the complexity of creating workable exploits. It is also worth noting that protection against Zero-Click attacks should be primarily concerned with the heads of private or public companies, as well as those who have confidential information at their disposal on personal or corporate mobile devices.

