Father
Professional
- Messages
- 2,601
- Reaction score
- 836
- Points
- 113
Note: This article does not claim to be a super manual. These are just my thoughts and notes that can help many find a new direction for themselves.
Good afternoon dear friends.
I have seen many different trends in the field of carzh.
Clamping the Add Money button in PP
CardingEbay with purchased cc and brut Amazon
Refs Boom in hotel and aviation topics and many many other relevant areas for work.
But all the topics someday die or temporarily become irrelevant, due to stagnation and lack of knowledge of the solution to the task (verif, fraud, lack of mat). Although from the above, almost all themes work. Only the approach has changed, and they have become not as widespread as then.
Today, I want to share my thoughts on working with logs.
I chose this direction for myself last year and completely devoted myself to studying and looking for loopholes in it. To this day, my groupmates and I show excellent results in this direction. I always try to teach to bet on "What would work, you need to treat business like work." For example, observe some nuances in work:
Wake up early in the morning in order to have time to buy fresh material
Check the work done every few hours, so as not to miss some detail and many other nuances that must be observed in order to increase the% of success. That is, if each nuance I observe will add 5-10% to success, then out of 10 completed works I will have a profit not from 1-2, but from 3-4, for example, which will be an excellent result and will be good compensation for the work done me a job.
I know that some people who work with logs are currently experiencing a problem both with the quality of the purchased material and with the degree of completion of this log before you.
As for me, this is due to the fact that most sellers of installations, as well as logs from our forum and not only, are uploaded in a circle at the same exchanges (publishers).
Also, there are unscrupulous sellers of logs who like to CRUSH 1 log into 2-3 requests and sell.
What to do and how to be?
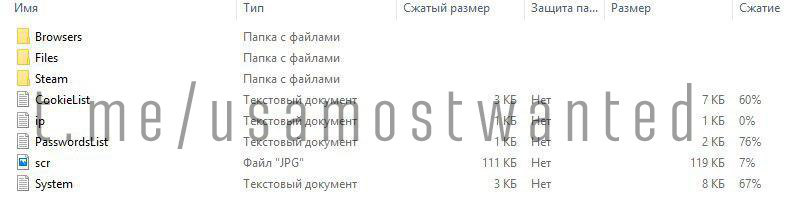
There is one direction that many people underestimate. Namely - to work with logs + purchased CC. That is, we take the most screwed up log, where there is access to at least some used mail from the owner of the log, register any shop with which we will work with it (I do not advise taking very large stores likeAmazOn, ebay ). Further, we register on some public services such as tweeter, redirect, or use the links that are in the log. We fill cookies in the shop with which we will work, and on social sites.
You ask why and what is the difference between self-registration and this method?
The answer is simple - Cookies. Most of the sites you visit (they even sometimes offer to agree with their cookie control rules at the bottom or top of the site) read your cookies and see where you went, which sites you visited before. Using mail from logs in work, where there are already real cookies, gives% to the passability, which I wrote about above.
The next nuance that I would like to tell you about is acting.
Yes, you heard exactly the acting. Try to imagine for the duration of your work that this or that lot that you will buy really needs you. How would you buy it? I am sure that you would not go to the site, find something in the search that costs more than $ 200-500 and would buy it within 5-10 minutes.
Acting, another nuance that should be observed when working not only with logs, but in all directions. For example, Google compares which sites you visited yesterday and the day before yesterday and a month ago and how you behave today. Makes a report and issues it on request via cookies.
For example, if we do 2-3 days of monotonous work such as checking mail, fb, youtube, tweeter, tweeter, redirecting, as well as browsing other sites with a description of the product that we are going to buy, this will give us 100% + in karma to this order.
Let me tell you a little secret about PP. If during the payment with PP it asks you to enter an SMS confirmation code, you can leave it for rest and try in 1-2 days. I have more than 50% of the time I get to work around this by relaxing and stuffing cookies. Cookies get used to it.
Also, a big nuance that must be observed is the proximity of your IP with a zip from under the inserted material (in our case, ss or pp).
According to my statistics, I will tell you this - it is better to choose an IP for a zip of a drop or material than to search for a transparently clean IP of which there are almost no left.
Under the zip of the material - when we work under the redirect or hold
Under the drop - when we work with the drive on the drop or in the middle.
Another nuance for you to increase your profit
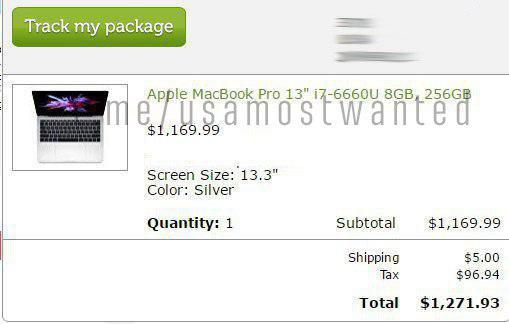
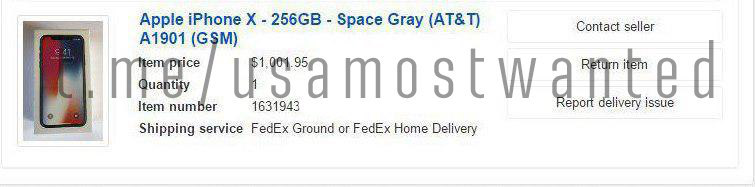
Stop thinking that it is always profitable to drive Apple and liquid staff, for which there is Additional Fraud in almost all shops. Yes, it's an additional one. Not only do you need to go through the anti-fraud shop and bank to write off, but also the fraud for super liquid goods.
Work with buyers who have a good% for non-liquid assets. Illiquid products - taps, fans, dog vacuum cleaners, digital locks, perfumes, pipes, water and pool filters, chairs, and so on. All this is included at least 30% better than top liquidity or electronics.
Total what we get
By observing a few simple tricks, you can increase cross-country ability and open up new horizons for work. Do not throw out a log with a spent Amazon or ebay. And continue to work on these cookies as on the giving platform
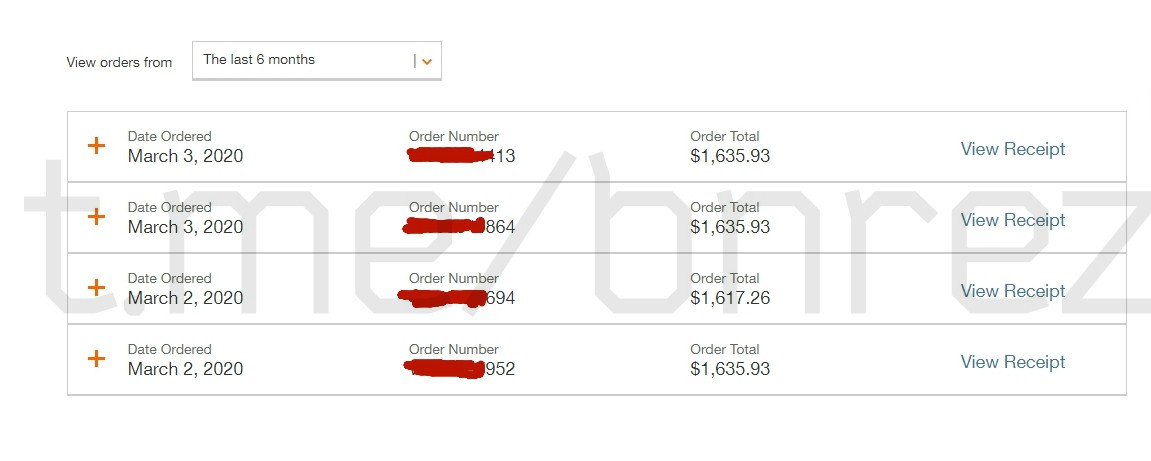
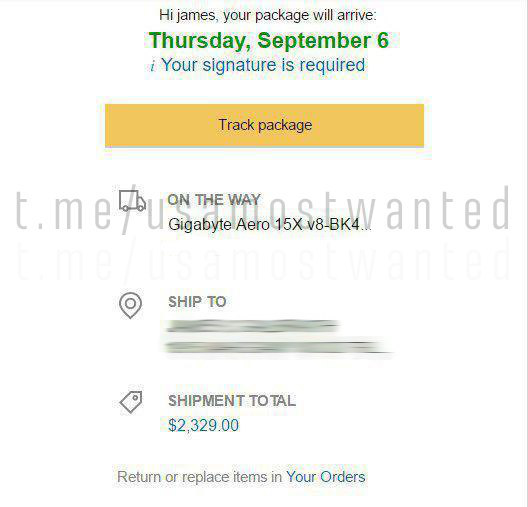
He worked with a chain store in the USA.
Out of 10 made such materials, 4 fired, of which 1 gives the 4th order in a row.
Expenses:
10 spent logs with live mail - $ 0
10 CC - $ 80-180
10-20 socks - $ 10-20
week of work 2 hours a day
~ $ 200.
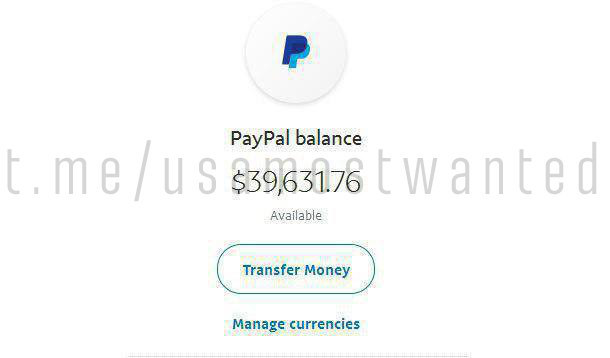
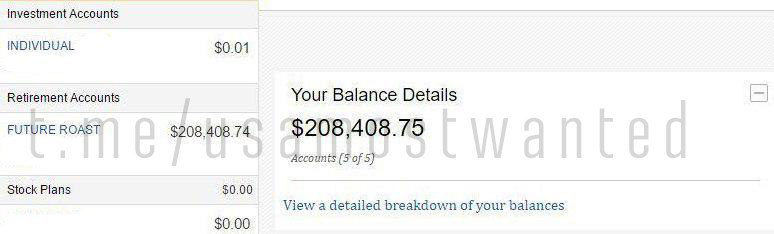
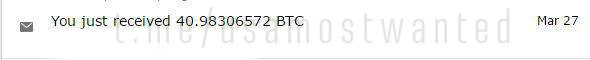
Profit from only one screen covers all costs and displays +
Don't forget to warm up the logs. All profit.
Good afternoon dear friends.
I have seen many different trends in the field of carzh.
Clamping the Add Money button in PP
Carding
Refs Boom in hotel and aviation topics and many many other relevant areas for work.
But all the topics someday die or temporarily become irrelevant, due to stagnation and lack of knowledge of the solution to the task (verif, fraud, lack of mat). Although from the above, almost all themes work. Only the approach has changed, and they have become not as widespread as then.
Today, I want to share my thoughts on working with logs.
I chose this direction for myself last year and completely devoted myself to studying and looking for loopholes in it. To this day, my groupmates and I show excellent results in this direction. I always try to teach to bet on "What would work, you need to treat business like work." For example, observe some nuances in work:
Wake up early in the morning in order to have time to buy fresh material
Check the work done every few hours, so as not to miss some detail and many other nuances that must be observed in order to increase the% of success. That is, if each nuance I observe will add 5-10% to success, then out of 10 completed works I will have a profit not from 1-2, but from 3-4, for example, which will be an excellent result and will be good compensation for the work done me a job.
I know that some people who work with logs are currently experiencing a problem both with the quality of the purchased material and with the degree of completion of this log before you.
As for me, this is due to the fact that most sellers of installations, as well as logs from our forum and not only, are uploaded in a circle at the same exchanges (publishers).
Also, there are unscrupulous sellers of logs who like to CRUSH 1 log into 2-3 requests and sell.
What to do and how to be?
There is one direction that many people underestimate. Namely - to work with logs + purchased CC. That is, we take the most screwed up log, where there is access to at least some used mail from the owner of the log, register any shop with which we will work with it (I do not advise taking very large stores like
You ask why and what is the difference between self-registration and this method?
The answer is simple - Cookies. Most of the sites you visit (they even sometimes offer to agree with their cookie control rules at the bottom or top of the site) read your cookies and see where you went, which sites you visited before. Using mail from logs in work, where there are already real cookies, gives% to the passability, which I wrote about above.
The next nuance that I would like to tell you about is acting.
Yes, you heard exactly the acting. Try to imagine for the duration of your work that this or that lot that you will buy really needs you. How would you buy it? I am sure that you would not go to the site, find something in the search that costs more than $ 200-500 and would buy it within 5-10 minutes.
Acting, another nuance that should be observed when working not only with logs, but in all directions. For example, Google compares which sites you visited yesterday and the day before yesterday and a month ago and how you behave today. Makes a report and issues it on request via cookies.
For example, if we do 2-3 days of monotonous work such as checking mail, fb, youtube, tweeter, tweeter, redirecting, as well as browsing other sites with a description of the product that we are going to buy, this will give us 100% + in karma to this order.
Let me tell you a little secret about PP. If during the payment with PP it asks you to enter an SMS confirmation code, you can leave it for rest and try in 1-2 days. I have more than 50% of the time I get to work around this by relaxing and stuffing cookies. Cookies get used to it.
Also, a big nuance that must be observed is the proximity of your IP with a zip from under the inserted material (in our case, ss or pp).
According to my statistics, I will tell you this - it is better to choose an IP for a zip of a drop or material than to search for a transparently clean IP of which there are almost no left.
Under the zip of the material - when we work under the redirect or hold
Under the drop - when we work with the drive on the drop or in the middle.
Another nuance for you to increase your profit
Stop thinking that it is always profitable to drive Apple and liquid staff, for which there is Additional Fraud in almost all shops. Yes, it's an additional one. Not only do you need to go through the anti-fraud shop and bank to write off, but also the fraud for super liquid goods.
Work with buyers who have a good% for non-liquid assets. Illiquid products - taps, fans, dog vacuum cleaners, digital locks, perfumes, pipes, water and pool filters, chairs, and so on. All this is included at least 30% better than top liquidity or electronics.
Total what we get
By observing a few simple tricks, you can increase cross-country ability and open up new horizons for work. Do not throw out a log with a spent Amazon or ebay. And continue to work on these cookies as on the giving platform

He worked with a chain store in the USA.
Out of 10 made such materials, 4 fired, of which 1 gives the 4th order in a row.
Expenses:
10 spent logs with live mail - $ 0
10 CC - $ 80-180
10-20 socks - $ 10-20
week of work 2 hours a day
~ $ 200.
Profit from only one screen covers all costs and displays +
Don't forget to warm up the logs. All profit.