Brother
Professional
- Messages
- 2,590
- Reaction score
- 533
- Points
- 113
Finally, you can secure your site only by installing the update immediately.
WordPress, the most popular content management system used on more than 800 million websites, has released an update to version 6.4.2. This update addresses a zero-day vulnerability that allows arbitrary PHP code to be executed on the target website.
The vulnerability discovered by the project security team is related to the Property Oriented Programming (POP) technique, which appeared in the WordPress core version 6.4. This vulnerability can lead to arbitrary PHP code execution under certain conditions.
A special feature of the POP chain is the need for the attacker to control all the properties of the deserialized object, which is possible thanks to the PHP unserialize () function. This can lead to intercepting the application flow by controlling the values sent to so-called magic methods, such as"_wakeup ()".
To successfully implement an attack on the target site, you must have a PHP object injection vulnerability, which may be present, for example, in a plugin or theme add-in.
WordPress security experts from Wordfence provided additional technical details. The problem is related to the "WP_HTML_Token" class introduced in WordPress 6.4 to improve HTML parsing in the block editor. This class contained the magic method "__destruct", which used" call_user_func "to execute the function defined in the" on_destroy "property with the"bookmark_name" argument.
An attacker using an object injection vulnerability could control these properties to execute arbitrary code.
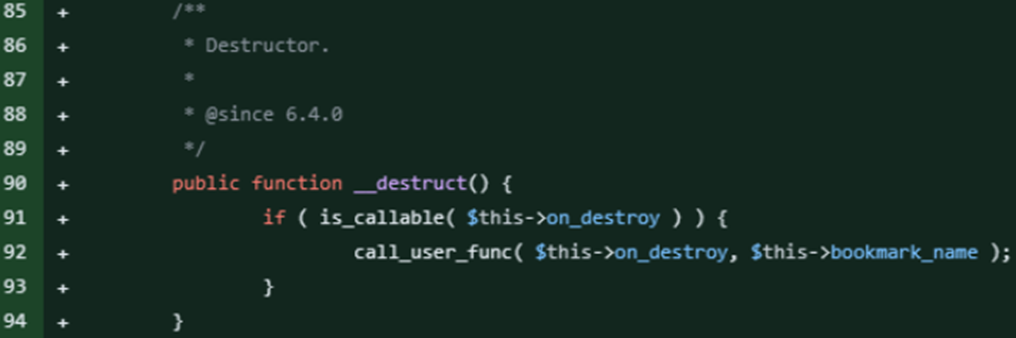
A class destructor that conditionally executes a callback function
Although the vulnerability itself is not critical, the presence of an exploitable POP chain in the WordPress core significantly increases the overall risk for sites based on it.
According to PatchStack, a chain of exploits for this problem was uploaded to GitHub a few weeks ago and later added to the PHPGGC library used for testing the security of PHP applications.
Researchers recommend that administrators upgrade to the latest version of WordPress, despite the fact that certain conditions are required to exploit the vulnerability. It is critically important for website administrators to eliminate any security risks in a timely manner so that hackers do not have the slightest opportunity to attack.
WordPress, the most popular content management system used on more than 800 million websites, has released an update to version 6.4.2. This update addresses a zero-day vulnerability that allows arbitrary PHP code to be executed on the target website.
The vulnerability discovered by the project security team is related to the Property Oriented Programming (POP) technique, which appeared in the WordPress core version 6.4. This vulnerability can lead to arbitrary PHP code execution under certain conditions.
A special feature of the POP chain is the need for the attacker to control all the properties of the deserialized object, which is possible thanks to the PHP unserialize () function. This can lead to intercepting the application flow by controlling the values sent to so-called magic methods, such as"_wakeup ()".
To successfully implement an attack on the target site, you must have a PHP object injection vulnerability, which may be present, for example, in a plugin or theme add-in.
WordPress security experts from Wordfence provided additional technical details. The problem is related to the "WP_HTML_Token" class introduced in WordPress 6.4 to improve HTML parsing in the block editor. This class contained the magic method "__destruct", which used" call_user_func "to execute the function defined in the" on_destroy "property with the"bookmark_name" argument.
An attacker using an object injection vulnerability could control these properties to execute arbitrary code.

A class destructor that conditionally executes a callback function
Although the vulnerability itself is not critical, the presence of an exploitable POP chain in the WordPress core significantly increases the overall risk for sites based on it.
According to PatchStack, a chain of exploits for this problem was uploaded to GitHub a few weeks ago and later added to the PHPGGC library used for testing the security of PHP applications.
Researchers recommend that administrators upgrade to the latest version of WordPress, despite the fact that certain conditions are required to exploit the vulnerability. It is critically important for website administrators to eliminate any security risks in a timely manner so that hackers do not have the slightest opportunity to attack.

