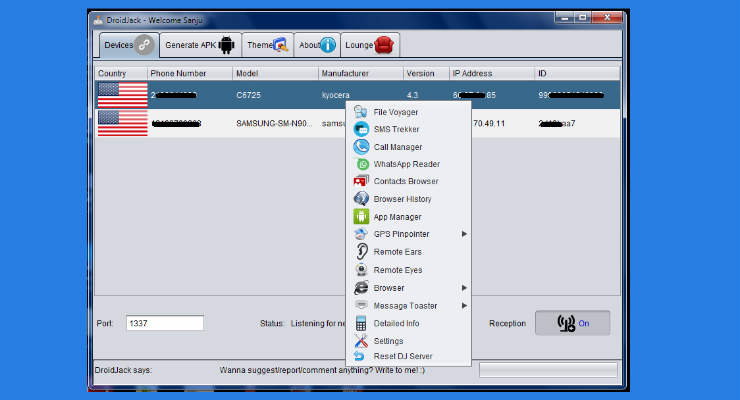
Hello, who have already watched my past video, now they know what a RAT is. Today I will tell you about the most famous and effective remote access Trojans. Don't even think about using them =)
For those who have forgotten, RAT is a remote access Trojan. In simple words, it is malware that allows a hacker to take full control of an infected device. That is, an attacker can either draw genitals in your paint or extort a ransom for stolen confidential data. RAT is a very powerful tool that opens up a wide range of actions. I think this is, so, understandable, so let's move on to the most outstanding representatives.

Back orifice
The whole movement started back in 1998, although many claim that RAT is just over 10 years old. It was at that bearded time that the grandfather of all modern rats, Back Orifice, appeared. It was created by members of the legendary hacker group "Cult of the Dead Cow", about which I will probably release a separate post. Initially, the Trojan was released for Windows 95 (then there were versions for 98 and XP) and it made a lot of noise, as it allowed full remote access to the victim's computer, and even had a nice interface. In general, the program itself is harmless at first glance. It would seem like an ordinary Team Viewer, if not for one thing. After the inconspicuous bo2k.exe file got on the computer, it gradually penetrated into all system files and seized control over them completely unnoticed by the user. The most interesting, BO provides a user with more options on a remote Windows computer than the user of that computer has. Quite ironic, so it is not surprising that it was quickly classified as a Trojan, and the creators were not too shy.
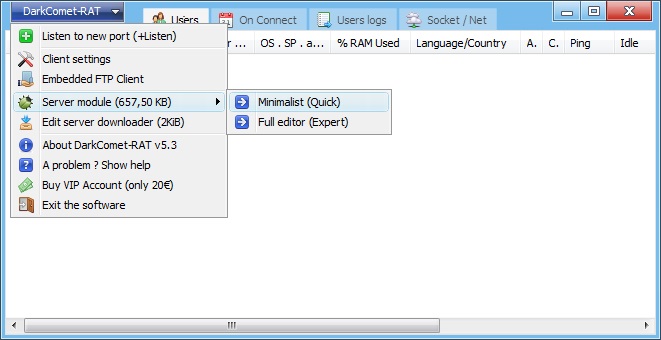
Dark comet
One of the first "modern" Trojans, which was created in 2008 by the French hacker Jean-Pierre Lesuer. He successfully sold his invention to Africans who tried to break the computers of the American government, after which he still had to pay attention to the malware. The functionality of this rat is not so extensive. From the key one can write a screen and collect passwords, and from the secondary one can turn on and off the computer remotely. Interestingly, Dark Comet was used by the Syrian government to spy on citizens.
Mirage
The invention of the Chinese Communist Party sponsored hackers. The most politicized RAT, as it was used mainly for spying on foreign governments, as well as sabotage in large companies in the period from 2009-2015. It got to computers via email newsletter with an attached PDF file with a surprise. An updated version of this Trojan is still being recorded, so the Chinese are not asleep.
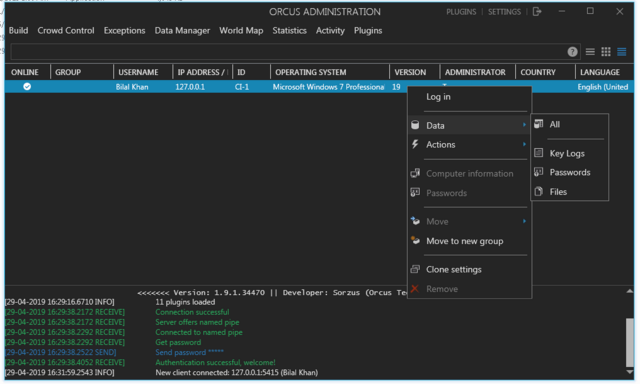
Orcus
In 2016, a couple of cunning entrepreneurs from Canada founded Orcus Technologies, whose main product was an analogue of the ORcus teamviewer. But the software turned out to be not so harmless, because it can be installed without the knowledge of the computer owner. The authorities missed the topic and issued a not sickly fine to the creators, and even a criminal offense to boot. Nevertheless, Orcus is still one of the most popular RATs, providing excellent functionality and a user-friendly interface. Through it you can do absolutely everything, only on someone else's computer.
For those who have forgotten, RAT is a remote access Trojan. In simple words, it is malware that allows a hacker to take full control of an infected device. That is, an attacker can either draw genitals in your paint or extort a ransom for stolen confidential data. RAT is a very powerful tool that opens up a wide range of actions. I think this is, so, understandable, so let's move on to the most outstanding representatives.

Back orifice
The whole movement started back in 1998, although many claim that RAT is just over 10 years old. It was at that bearded time that the grandfather of all modern rats, Back Orifice, appeared. It was created by members of the legendary hacker group "Cult of the Dead Cow", about which I will probably release a separate post. Initially, the Trojan was released for Windows 95 (then there were versions for 98 and XP) and it made a lot of noise, as it allowed full remote access to the victim's computer, and even had a nice interface. In general, the program itself is harmless at first glance. It would seem like an ordinary Team Viewer, if not for one thing. After the inconspicuous bo2k.exe file got on the computer, it gradually penetrated into all system files and seized control over them completely unnoticed by the user. The most interesting, BO provides a user with more options on a remote Windows computer than the user of that computer has. Quite ironic, so it is not surprising that it was quickly classified as a Trojan, and the creators were not too shy.

Dark comet
One of the first "modern" Trojans, which was created in 2008 by the French hacker Jean-Pierre Lesuer. He successfully sold his invention to Africans who tried to break the computers of the American government, after which he still had to pay attention to the malware. The functionality of this rat is not so extensive. From the key one can write a screen and collect passwords, and from the secondary one can turn on and off the computer remotely. Interestingly, Dark Comet was used by the Syrian government to spy on citizens.
Mirage
The invention of the Chinese Communist Party sponsored hackers. The most politicized RAT, as it was used mainly for spying on foreign governments, as well as sabotage in large companies in the period from 2009-2015. It got to computers via email newsletter with an attached PDF file with a surprise. An updated version of this Trojan is still being recorded, so the Chinese are not asleep.

Orcus
In 2016, a couple of cunning entrepreneurs from Canada founded Orcus Technologies, whose main product was an analogue of the ORcus teamviewer. But the software turned out to be not so harmless, because it can be installed without the knowledge of the computer owner. The authorities missed the topic and issued a not sickly fine to the creators, and even a criminal offense to boot. Nevertheless, Orcus is still one of the most popular RATs, providing excellent functionality and a user-friendly interface. Through it you can do absolutely everything, only on someone else's computer.
P.S. If you liked this post, please unsubscribe in the comments. In this case, I will release a sequel, with software for Android, as well as a guide to protect against RAT.