Lord777
Professional
- Messages
- 2,576
- Reaction score
- 1,551
- Points
- 113
To work on the network, many users need to replace their fingerprint - a set of data about the device, browser, and connection. Using the example of Dolphin{anty}, we will tell you what data browsers can substitute for anti-detection, what it means, and why it is needed.
Useragent is used to:
All popular anti-detection browsers are compatible with any type of proxy. For example, this is the window for adding proxies to Dolphin{anty}.
Canvas is not a unique parameter and can be repeated among users. Therefore, if you need to simulate the fingerprint of a regular user, as a rule, browser developers recommend not to change this parameter.
In Dolphin{anty}, you can choose one of the following options: disable WebRTC, replace it, show the real one, or configure it manually.
It is better to check with the anti-detection developer which WebRTC mode to choose depending on your tasks.
In addition to the ability to work with various graphics, WebGL significantly speeds up the loading speed of web pages, including since it works without third-party plugins.
According to available data, various sites use WebGL data to get your device's fingerprint, bypassing all encryption. To protect this data, anti-detection browsers offer three options to choose from:
Like other parameters, you can change geolocation manually in Dolphin{anty} or set automatic selection.
There are two key protocol types for ports:
How to check the reliability of browser anti-detection
To evaluate the quality of spoofing, some users check the quality of anti-detection through special digital fingerprint scanners. Inseparate articlewe made a selection of such services.
However, it is important to consider:
What to pay attention to when choosing anti-detect browser
We have collected some basic parameters that may be important when choosing an anti-detect browser:
 Quality, quantity, and type of substitutions
Quality, quantity, and type of substitutions
For example, some anti-detect browsers have a function that simulates the connection of a mobile device. However, the truth is that due to the strong differences in the settings of phones and PCs, sites always see which device the user logs in from. For this reason, it is best not to try to simulate using a mobile device from a PC.
,Frequency and speed of browser updates
All anti-detection tools work on the basis of some popular browser: Chrome, Chromium, or Firefox. When visiting sites, security systems see which browser version the user is using. If the version is too old, for example, Chromium currently has version 101, but the user logs in from 80, anti-fraud systems may suspect that something is wrong with the user.
To avoid such problems, it is important that the anti-detection browser is quickly updated to the latest versions of the main browser. As a rule, developers publish data about current versions on their website or in news channels of their product.
How anti-detection works with bugs and crashes
Like any other program, anti-detection software crashes. All failures can be divided into two types:
Обратите внимание, как компания реагирует на обращения пользователей, каким образом отвечает на негатив, удаляет ли комментарии или аргументированно отвечает на критику и помогает пользователям решить проблему.
For example, in 2022, many services and companies in the Russian Federation faced problems due to periodic failures and restrictions on connecting to specific servers.
It is important to understand that by crashes, we mean problems on the browser side. Often, problems with work can arise due to the actions of users themselves: incorrect proxies, problems on the side of the Internet provider, etc. For example, in a separate article, we analyzed what basic mistakes arbitrageurs make when working with detect browsers.
In a separate article, we have compiled the basic parameters by which anti-fraud systems understand that user is replacing digital fingerprints.
What parameters does Dolphin{anty} replace?
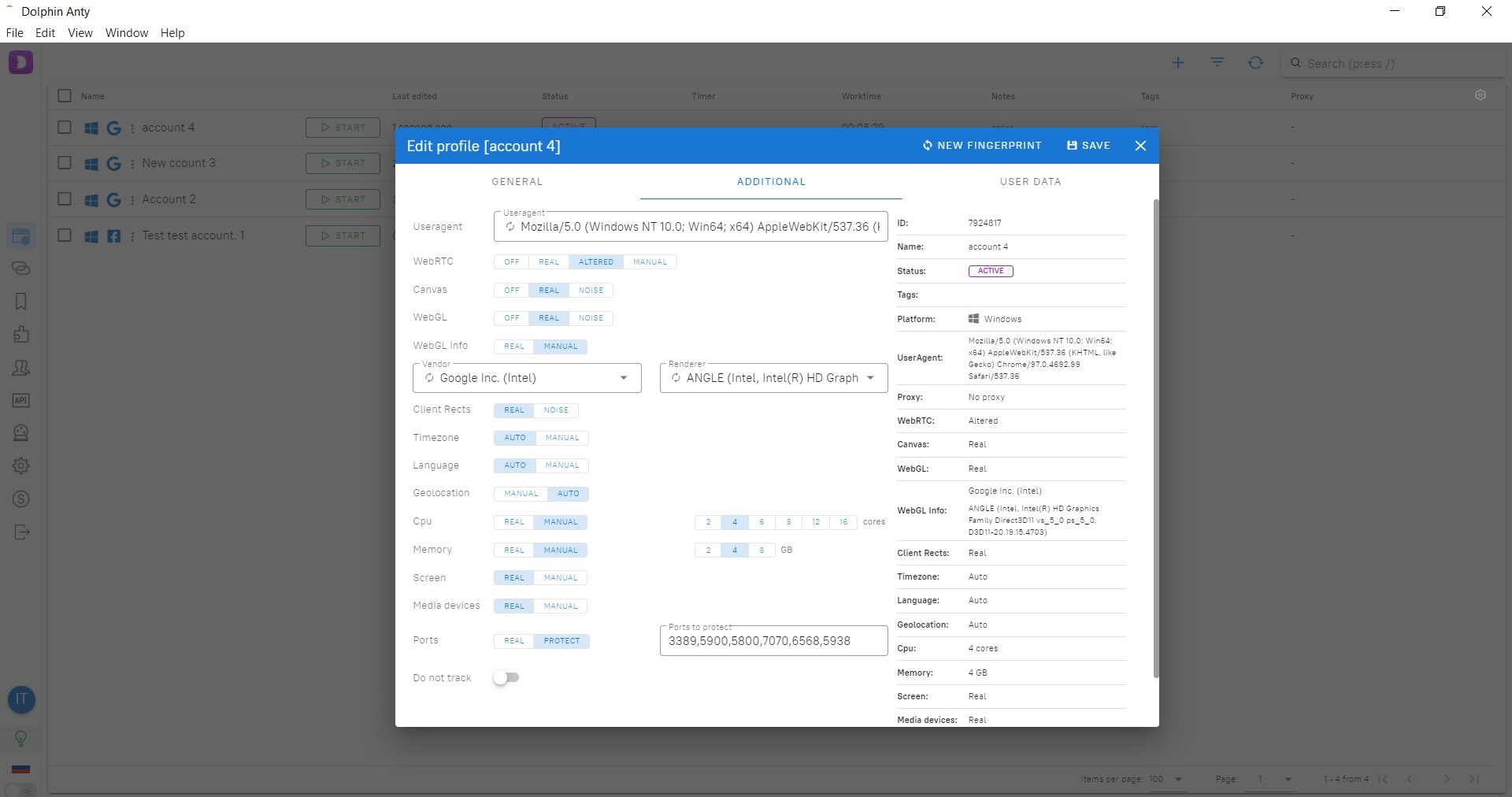
Anti-detection Dolphin{anty} browser replaces more than 20 parameters of your device and browser. This includes:- Useragent
- Canvas
- WebRTC
- WebGL
- Time zone
- Language
- Geolocation
- CPU
- Memory
- Screen
- Media devices
- Ports
- IP address

Why replace digital fingerprints at all
Fingerprint substitution may be required for different tasks:- Anonymity in the network. For example, to protect your data from systems that collect user data in order to identify them later.
- Simulates the data of a regular user. It is important not to confuse anonymity with imitation. In the first case, the program hides your real data. In the second case, it replaces data so that you don't stand out among millions of regular users and don't attract the attention of anti-fraud systems. To do this, the fingerprint must not be unique, but similar to other prints. It is the latter task that is more difficult.
- Simultaneous work with dozens of accounts on the same site. For example, for betting, working with social networks, running ads, etc.
- Visiting blocked resources.
- Testing interfaces. For example, if you need to test the site's performance in different countries.
What do different fingerprint parameters mean ?
Each of the parameters has an important role in shaping the overall impression of the browser and the system as a whole. Let's look at each of them.Useragent
Useragent — a program element of the browser. If you use multiple browsers from the same device, the useragent will be slightly different for each of them. From the useragent data, you can find out, for example, the name and version of the browser, language, device type, name and version of the operating system, and so on.Useragent is used to:
- Correctly show you data for a specific resource.
- Find out your device and browser data to identify you online.
IP address
This is one of the basic parameters that even the simplest antifraud systems analyze. It is used by anti-fraud systems to get information about your location and provider in order to exchange data between the device and servers. To change the IP address and be as similar as possible to a regular user, use high-quality proxies.All popular anti-detection browsers are compatible with any type of proxy. For example, this is the window for adding proxies to Dolphin{anty}.
Canvas
Canvas is an HTML5 element that creates and defines a zone for creating an image. It literally translates as "canvas". This element is used to display various charts, animations, games, graphics, etc.Canvas is not a unique parameter and can be repeated among users. Therefore, if you need to simulate the fingerprint of a regular user, as a rule, browser developers recommend not to change this parameter.
WebRTC
This is a special plugin that supports transmitting video and audio on a web page. To speed up your work, this plugin gives web resources access to your media devices. For example, to your headphones and camera. This parameter can be used to show your real IP address, even if you are using a proxy.In Dolphin{anty}, you can choose one of the following options: disable WebRTC, replace it, show the real one, or configure it manually.
It is better to check with the anti-detection developer which WebRTC mode to choose depending on your tasks.
WebGL
This is a web-based JavaScript library that allows you to connect to a video card to create 2D and 3D graphics. WebGL works in conjunction with Canvas.In addition to the ability to work with various graphics, WebGL significantly speeds up the loading speed of web pages, including since it works without third-party plugins.
According to available data, various sites use WebGL data to get your device's fingerprint, bypassing all encryption. To protect this data, anti-detection browsers offer three options to choose from:
- don't change WebGL
- disable WebGL
- add noise.
Time zone
This data shows your time zone. When choosing a time zone, make sure that it matches your IP address data. Otherwise, anti-fraud systems will notice even faster that you are replacing your real data.Language
By analogy with the time zone, it is better to choose a language based on the IP address and geo-location used. This is especially important if you work with social media accounts. In this case, the browser language should ideally match the account language.Geolocation
Although it may seem that the sites get this data from the IP address, in reality, the information can also be collected through the API. This is due to the fact that users can often change their IP address, for example, if the provider changes or the device is restarted.Like other parameters, you can change geolocation manually in Dolphin{anty} or set automatic selection.
CPU
In Dolphin{anty}, you can manually select the number of processor cores: 4, 6, 8, 12, or 16.Memory
This parameter specifies the amount of RAM on the device. At the time of writing this article, you can install 2, 4, and 8 GB of memory, or select automatic selection of this data.Screen
This parameter reflects the screen resolution. You can use automatic selection of this parameter or configure it manually.Media devices
This parameter includes data about the number of microphones, speakers, and cameras that your device has and is connected to. In Dolphin{anty}, you can select data from 0 to 3.Ports
These are network ports that are used for data exchange and transmission. You can imagine that a network port is an address where specific applications communicate with each other.There are two key protocol types for ports:
- TCP is a transport protocol that provides continuous data exchange between two devices.
- UDP is a protocol that provides a fast connection.
How to check the reliability of browser anti-detection 
To evaluate the quality of spoofing, some users check the quality of anti-detection through special digital fingerprint scanners. Inseparate articlewe made a selection of such services.However, it is important to consider:
- The scanner data is of a general informational nature. This means that they can be used as one of the verification elements, but you should not rely on them completely. Moreover, given that each scanner checks a different amount of data using its own algorithms, sometimes one scanner does not detect the fact of substitution, and the other sees it.
- Each site has algorithms for verifying user data. Because of this, what some security systems pay attention to, others ignore. If you've previously worked with different anti-detection browsers, you may have noticed that on high volumes, one anti-detection may work perfectly with Facebook, while the other may be better suited for working with cryptocurrencies or search engines.
What to pay attention to when choosing anti-detect browser 
We have collected some basic parameters that may be important when choosing an anti-detect browser:For example, some anti-detect browsers have a function that simulates the connection of a mobile device. However, the truth is that due to the strong differences in the settings of phones and PCs, sites always see which device the user logs in from. For this reason, it is best not to try to simulate using a mobile device from a PC.
,Frequency and speed of browser updates
All anti-detection tools work on the basis of some popular browser: Chrome, Chromium, or Firefox. When visiting sites, security systems see which browser version the user is using. If the version is too old, for example, Chromium currently has version 101, but the user logs in from 80, anti-fraud systems may suspect that something is wrong with the user.
To avoid such problems, it is important that the anti-detection browser is quickly updated to the latest versions of the main browser. As a rule, developers publish data about current versions on their website or in news channels of their product.
How anti-detection works with bugs and crashes
Like any other program, anti-detection software crashes. All failures can be divided into two types:
- Local ones. When a small number of users encounter difficulties, for example, from a specific city.
- Mass production. When a large number of users encounter problems. For example, due to a large-scale failure of the servers running the browser.
Обратите внимание, как компания реагирует на обращения пользователей, каким образом отвечает на негатив, удаляет ли комментарии или аргументированно отвечает на критику и помогает пользователям решить проблему.
For example, in 2022, many services and companies in the Russian Federation faced problems due to periodic failures and restrictions on connecting to specific servers.
It is important to understand that by crashes, we mean problems on the browser side. Often, problems with work can arise due to the actions of users themselves: incorrect proxies, problems on the side of the Internet provider, etc. For example, in a separate article, we analyzed what basic mistakes arbitrageurs make when working with detect browsers.
Additional features
There are no clear criteria here, because different parameters are important for users. For example, it may be important for companies that the browser supports the ability to work together and distribute different access rights. For other users, the key factor is the convenience and simplicity of the interface.In a separate article, we have compiled the basic parameters by which anti-fraud systems understand that user is replacing digital fingerprints.

