BadB
Professional
- Messages
- 1,708
- Reaction score
- 1,695
- Points
- 113
Hola, hacker, once wanted to find out what is hidden behind a compiled application? Today we will look at a way to reverse a compiled (pyinstaller) exe-shnik. Go!
We steal someone else's code. Reverse engineering Python.
What do we need?
First, download the Extractor script. Then install Uncompyle6 using pip:
Installing UnCompyle6.
Now we can start reverse.
I got my hands on a RATNIK in python, compiled by pyinstaller. Actually, the order of actions will not differ from any other file. Let's get started.
First, we need to get all files / libraries / dlls from the executable. For this we need pyExtractor. We run the script as follows:
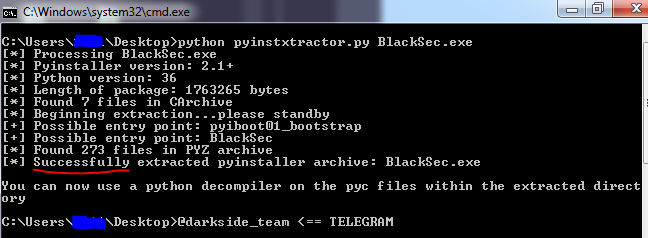
An example of successful execution.
A folder was created next to the exe-shnik:
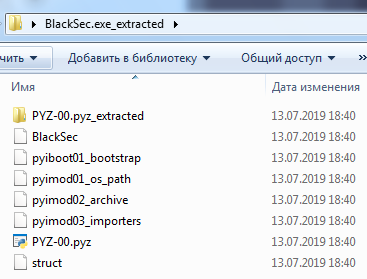
Here, in my case, I need the BlackSec file, otherwise it will be the file name without the extension. (For example your file was named build.exe, after Extractor the final file will be just build).
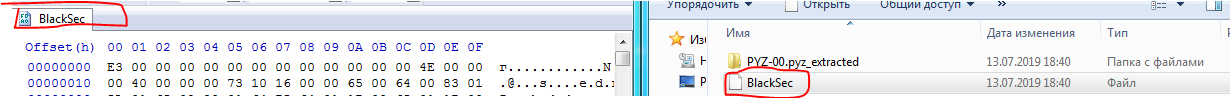
BlackSec file is pyc without magic number.
We need to get the pyc file to get the code. To do this, launch the HEX editor and transfer the file there without the extension, in my case it is BlackSec:
Now we need to assign a magic number to our file, we will take it from the neighboring files in the folder PYZ-00.pyz_extracted. Copy any file from the folder, (I always use the __future__.pyc)editor in the HEX:
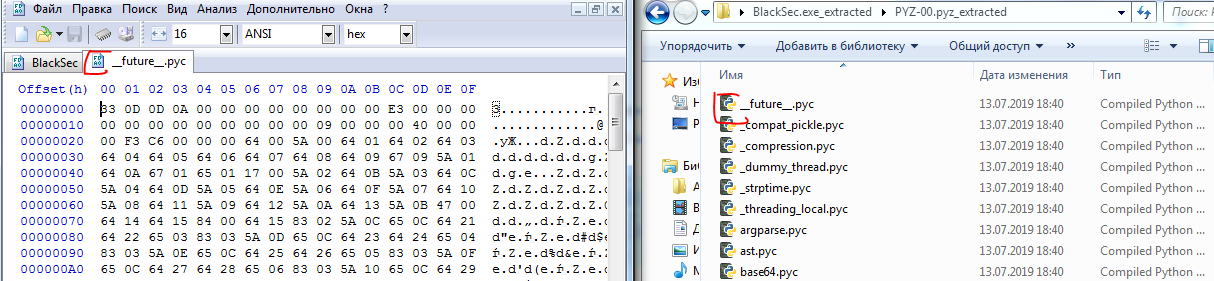
Now we need to copy the bytes that contain the magic number, for everything to be successful, we need the first line of the two files (BlackSec & __future __. Pyz) to be the same. Copy the first 12 bytes:
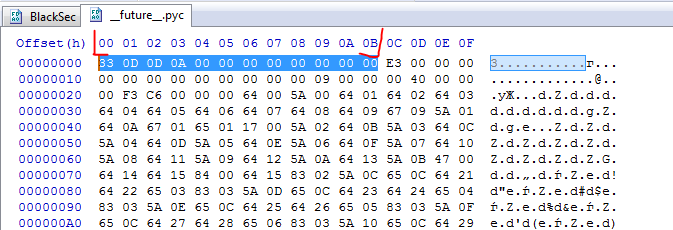
And insert at the beginning of our file:
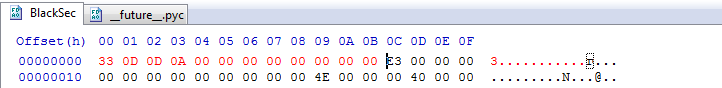
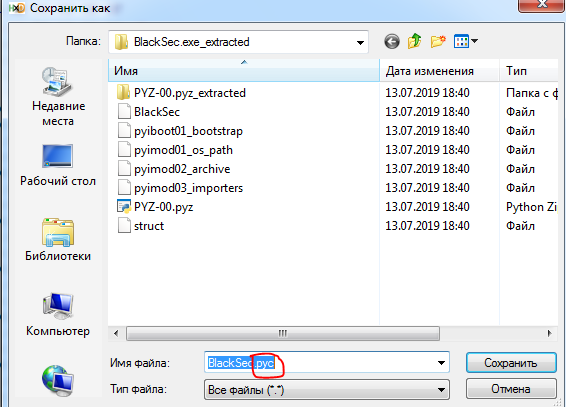
Next, click on: File => Save As ... And save with the extension .pyc:
In fact, everything is almost ready, it remains to decompile the .pyc file using uncompyle, for this we run the command in cmd:
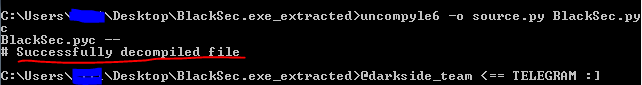
That's it, a file containing the exe-shnik code appeared near our pyc file.
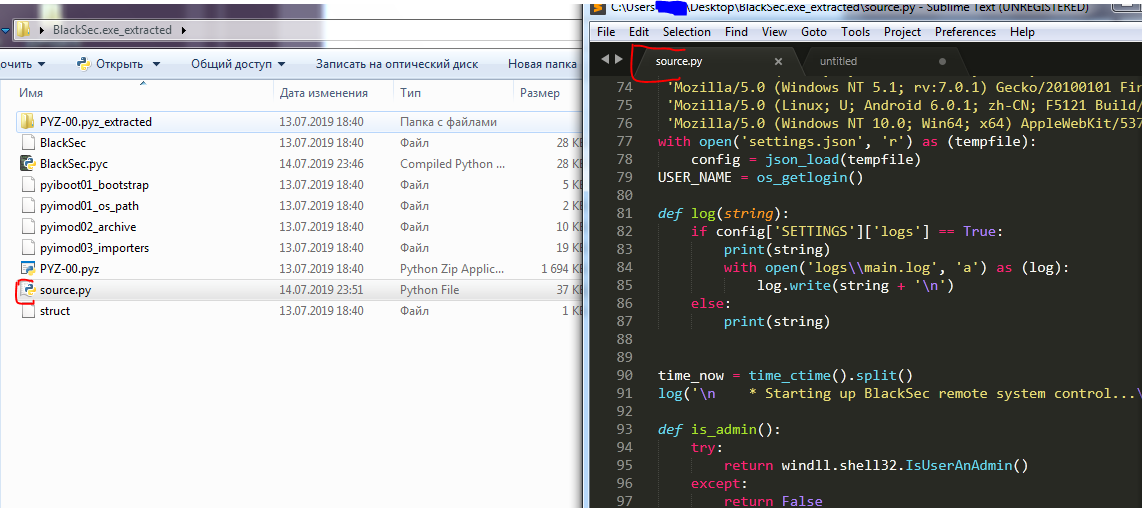
Mission Passed!
Conclusion.
As you can see, hacker, python also lends itself to decompilation. In the direction of protecting the code, you should use obfuscators / protectors, for python I recommend pyArmor, it turns the code into an "incomprehensible" set of characters.
This concludes the article, before communication, hacker.
We steal someone else's code. Reverse engineering Python.
What do we need?
- PyInstaller Extractor.
- Uncompyle6.
- HxD / Or another HEX editor.
First, download the Extractor script. Then install Uncompyle6 using pip:
Code:
pip install uncompyle6
Installing UnCompyle6.
Now we can start reverse.
I got my hands on a RATNIK in python, compiled by pyinstaller. Actually, the order of actions will not differ from any other file. Let's get started.
First, we need to get all files / libraries / dlls from the executable. For this we need pyExtractor. We run the script as follows:
Code:
python pyinstxtractor.py filename.exe
An example of successful execution.
A folder was created next to the exe-shnik:
Code:
File.exe_extracted
Here, in my case, I need the BlackSec file, otherwise it will be the file name without the extension. (For example your file was named build.exe, after Extractor the final file will be just build).
BlackSec file is pyc without magic number.
I won't say what a "magic" number is, but here's a link to Vika, she will tell you everything.pyc - This is the compiled bytecode. If you are importing a module, python will build a file *.pycthat contains the bytecode to make it easier to import
We need to get the pyc file to get the code. To do this, launch the HEX editor and transfer the file there without the extension, in my case it is BlackSec:

Now we need to assign a magic number to our file, we will take it from the neighboring files in the folder PYZ-00.pyz_extracted. Copy any file from the folder, (I always use the __future__.pyc)editor in the HEX:

Now we need to copy the bytes that contain the magic number, for everything to be successful, we need the first line of the two files (BlackSec & __future __. Pyz) to be the same. Copy the first 12 bytes:

And insert at the beginning of our file:

Next, click on: File => Save As ... And save with the extension .pyc:

In fact, everything is almost ready, it remains to decompile the .pyc file using uncompyle, for this we run the command in cmd:
Code:
uncompyle6 -o source.pyYourFileName.pyc
That's it, a file containing the exe-shnik code appeared near our pyc file.

Mission Passed!
Conclusion.
As you can see, hacker, python also lends itself to decompilation. In the direction of protecting the code, you should use obfuscators / protectors, for python I recommend pyArmor, it turns the code into an "incomprehensible" set of characters.
This concludes the article, before communication, hacker.
