Man
Professional
- Messages
- 3,225
- Reaction score
- 1,014
- Points
- 113
A Step-by-Step Guide for Beginner Cyber Detectives.
Hello everyone, dear friends!
Today we will talk about what information can be obtained from a web resource for subsequent use in OSINT. What services are there for this and what specific information they will dig up for us.
OSINT website research can be used to address a number of issues:

There are a lot of WHOIS services. Therefore, we will list only a few popular ones:

However, on the sad side... After the introduction of the GDPR regulations, we had to forget about the open publication of personal data of domain name owners. And for searching old WHOIS records in which personal data was stored, we can recommend a couple more useful resources:
Let's continue with the sad stuff. As you know, there is a company called Cloudflare, which allows you to additionally hide data about website owners when using its services.
Well, sometimes its anonymity can be slightly opened. For this we use such an open source product as CrimeFlare:

It also exists in the web interface at the link: https://crimeflare.herokuapp.com. CrimeFlare allows you to do a little, but important - get the real IP address of a site hidden behind Cloudflare.
Here are a couple more resources where you may come across leaked passwords from various online services. The site you are researching may be among the latter:
As we all know, a website is not just a domain name. A website must be physically located somewhere. Its location is hosting.

Hosting data for a particular site can also be found in open sources:
The following selection of services will help you understand what advertising tracking technologies (and not only) are present on the site:
However, you can open the source code of the web page and then search for advertising identifiers manually using the following keywords:
AdSense: Pub- или ca-pub
Analytics: UA-
Amazon: &tag=
AddThis: #pubid / pubid
Metrika: mc.yandex / ym
Rambler: top100
Mail.ru: Top.Mail.Ru
If we have found the code of one of the metrics, we can open its public statistics. To do this, enter the metric ID in one of the following hyperlinks:
 metrika.yandex.ru
metrika.yandex.ru

 top100.rambler.ru
top100.rambler.ru

The public metric is interesting because it will show the administrator who put it on the web resource as the first visitor to the site. This could be the site owner. Then we will receive information about his gender, age and city of residence. You can check this on the following Yandex metric https://metrika.yandex.ru/dashboard?id=55694881.
In addition, metric codes or advertising identifiers allow you to find additional sites on the network that use it in their code. For this, you can use the following services:
You can use reverse IP lookup by website hosting address using the following resources:
You can also perform a reverse search to match related email addresses:
You can also reverse search a site's SSL certificate:
Let's move on to collecting contacts. Some of the contact information of the web resource owner is posted on the site or when registering a domain name. Let's try to find the maximum number of contacts (e-mail addresses) using services such as:

Let's smoothly move on to DNS analysis.
DNS (Domain Name System) is used to obtain an IP address from a hostname, obtain information about mail routing and/or service nodes for protocols in a domain. This data will also be useful to us when studying a website:
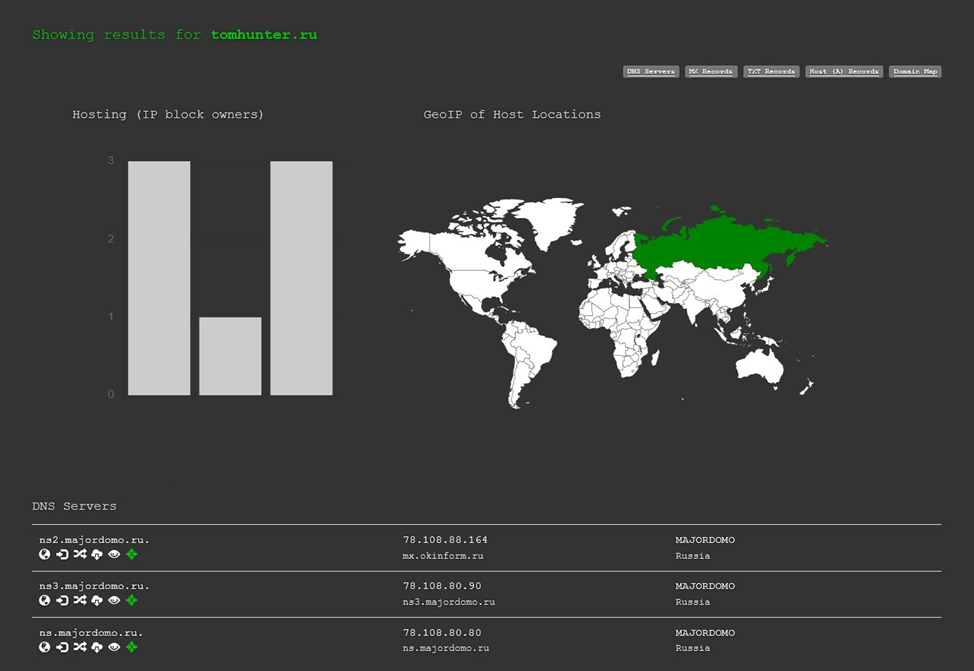
Historical DNS data can be viewed at the link:
https://osint.sh/dnshistory
Old copies of web pages and sites (web archives) will also be useful in the investigation. You never know what was written on the site a couple of years ago. Links to popular web archives are below:
Useful collections of additional services for studying websites can be found here:
And also, as a sweet treat, complex services for conducting investigations on web resources. Let's start with the modular service Spiderfoot, which allows you to do 3 checks per month absolutely free.
And don't forget about Maltego with its free modules and a bunch of free APIs. It's quite a cool tool.
Well, that's all for today. We hope that the information will be profitable and useful for you!
Hello everyone, dear friends!
Today we will talk about what information can be obtained from a web resource for subsequent use in OSINT. What services are there for this and what specific information they will dig up for us.
This information and methods will also be useful toordinarypeople who are not connected with the IT sphere, as they will help to determine “by eye” the reliability of a particular site before entering your bank card details on it…
OSINT website research can be used to address a number of issues:
- identification of owners or administrators;
- monitoring price changes;
- competitor analysis;
- SEO or keywords used etc.

There are a lot of WHOIS services. Therefore, we will list only a few popular ones:
- https://whois.domaintools.com/
- https://whoer.net/ru/checkwhois
- https://www.iana.org/whois
- https://lookup.icann.org/

Of course, if an online store promises you incredibly low prices and generally “WE HAVE BEEN ON THE MARKET FOR 10 YEARS!”, but its domain was registered 2-3 days ago, then you should think about whether it is a scam…
However, on the sad side... After the introduction of the GDPR regulations, we had to forget about the open publication of personal data of domain name owners. And for searching old WHOIS records in which personal data was stored, we can recommend a couple more useful resources:
Let's continue with the sad stuff. As you know, there is a company called Cloudflare, which allows you to additionally hide data about website owners when using its services.
Well, sometimes its anonymity can be slightly opened. For this we use such an open source product as CrimeFlare:

It also exists in the web interface at the link: https://crimeflare.herokuapp.com. CrimeFlare allows you to do a little, but important - get the real IP address of a site hidden behind Cloudflare.
Here are a couple more resources where you may come across leaked passwords from various online services. The site you are researching may be among the latter:
As we all know, a website is not just a domain name. A website must be physically located somewhere. Its location is hosting.

Hosting data for a particular site can also be found in open sources:
- https://www.whoishostingthis.com/
- https://hostingchecker.com/
- https://hostadvice.com/tools/whois/
- https://2ip.ru/guess-hosting/
The following selection of services will help you understand what advertising tracking technologies (and not only) are present on the site:
However, you can open the source code of the web page and then search for advertising identifiers manually using the following keywords:
AdSense: Pub- или ca-pub
Analytics: UA-
Amazon: &tag=
AddThis: #pubid / pubid
Metrika: mc.yandex / ym
Rambler: top100
Mail.ru: Top.Mail.Ru
If we have found the code of one of the metrics, we can open its public statistics. To do this, enter the metric ID in one of the following hyperlinks:
Authorization

Рейтинг сайтов «Все темы» - Рамблер Топ-100
Рейтинг сайтов категории «Все темы». Бесплатная аналитика для вашего сайта: сплиты, отчеты в реальном времени, карта кликов и другие инструменты веб-аналитики.

The public metric is interesting because it will show the administrator who put it on the web resource as the first visitor to the site. This could be the site owner. Then we will receive information about his gender, age and city of residence. You can check this on the following Yandex metric https://metrika.yandex.ru/dashboard?id=55694881.
In addition, metric codes or advertising identifiers allow you to find additional sites on the network that use it in their code. For this, you can use the following services:
- https://intelx.io/tools?tab=adsense
- https://dnslytics.com/reverse-analytics
- https://analyzeid.com
- https://osint.sh/adsense
You can use reverse IP lookup by website hosting address using the following resources:
- https://2ip.ru/domain-list-by-ip
- https://www.cy-pr.com/tools/oneip
- https://hackertarget.com/reverse-ip-lookup
- https://mxtoolbox.com/reverselookup.aspx
- https://osint.sh/reverseip
You can also perform a reverse search to match related email addresses:
You can also reverse search a site's SSL certificate:
Let's move on to collecting contacts. Some of the contact information of the web resource owner is posted on the site or when registering a domain name. Let's try to find the maximum number of contacts (e-mail addresses) using services such as:
- https://phonebook.cz
- https://hunter.io
- https://www.mailshunt.com
- https://2ip.ru/domain-list-by-email

Let's smoothly move on to DNS analysis.
DNS (Domain Name System) is used to obtain an IP address from a hostname, obtain information about mail routing and/or service nodes for protocols in a domain. This data will also be useful to us when studying a website:
- https://dnsdumpster.com
- https://hackertarget.com/dns-lookup/
- https://securitytrails.com/
- https://crt.sh/
- https://osint.sh/dns/
- https://suip.biz/?act=alldns

Historical DNS data can be viewed at the link:
https://osint.sh/dnshistory
Old copies of web pages and sites (web archives) will also be useful in the investigation. You never know what was written on the site a couple of years ago. Links to popular web archives are below:

Useful collections of additional services for studying websites can be found here:
- https://osint.sh
- https://suip.biz
- https://hackertarget.com/ip-tools
- https://abhijithb200.github.io/investigator
And also, as a sweet treat, complex services for conducting investigations on web resources. Let's start with the modular service Spiderfoot, which allows you to do 3 checks per month absolutely free.

And don't forget about Maltego with its free modules and a bunch of free APIs. It's quite a cool tool.
Well, that's all for today. We hope that the information will be profitable and useful for you!
