BadB
Professional
- Messages
- 1,962
- Reaction score
- 2,014
- Points
- 113

Predator TT

Number of purses
You can download logs only with wallets by clicking in the search bar header

Panel header Select wallets and set to one

Choose what we will look for.
Click search and create a copy.

All logs with crypto wallets Download the backup by selecting the button of the same name in the header and click on the download icon

Here are all backups
All logs with wallet.dat

Our logs
We choose any, but only this folder is needed, files from all found wallets on the PC are stored there

This is what the log looks like
The file will contain one or more files with the dat extension

Now you need this file to work, which is located in the wallets folder. If your name is not Bitcoin, then it's okay. We do everything the same

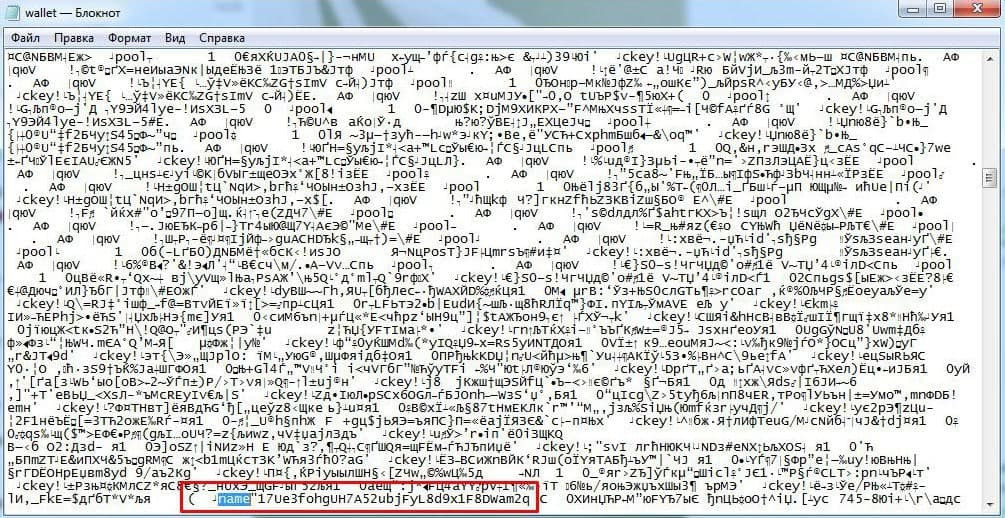
Unzip it and click Edit with Notepad ++ (I hope where to get it, no questions asked). We get into the wallet itself, press ctrl + f. Find name

And we find such a prick. This address is the identifier of our wallet.
Now, if you have one of the popular coins (names on the screen), then go to this site https://live.blockcypher.co m and type the wallet address into the window

We look at the balik. Well, that's all. If it's okay, then download the cold wallet itself (I don't recommend it, you will kill a lot of time) or, we turn to these guys https://vlmi.su/threads/vskroem-vashi-wallet-dat.23716/

We drive the name of the coin into this window and click on (behind) the magnifying glassIf you had some kind of NN coin, then go to this site https://coinmarketcap.com

Now we find the explore and click on any one you like (there can be two or one).

There we find some kind of window and drive in the address of the wallet there

Everything. Now we know the balance, you can download a cold wallet and replace the file in it.
--
WALLET.DAT (CRYPTO WALLETS)
Today we will analyze the processing of cold crypto-wallets.
For those who do not yet know what it is, I explain:
In addition to online wallets and credentials in the log in the form of a login and password + a link to the site, there are cold crypto wallets - this is when the wallet user pumps out the entire cryptocurrency network to his computer, and uses the wallet through the program. So, the key file in this case is the wallet.dat file, which contains data from the wallet, thanks to which you can check the balance on the wallet and even fly into it if the wallet dat file and log are fresh.
So, today we will talk about how to process such wallets. Also, we will also touch on partially working with exchanges and online crypto wallets.
Our mini plan for today
STEP 1 - WALLET.DAT FILES.
- 1.1 - What the log looks like and what you should pay attention to.
- 1.2 - How to find out the wallet address from wallet.dat
- 1.3 - How to find out the balance at the wallet address.
- 1.4 - How to withdraw this balance.
- 1.5 - Notes and recommendations, pros and cons.
STAGE 2 - BYPASSING 2FA ON EXCHANGE.
- 2.1 - Find out the balance of the wallet on the exchange.
- 2.2 - bypassing 2fa on the exchange.
- 2.3 - Help from specialists.
STAGE 3 - MINING CRYPTO LOGS, WHERE TO GET, WHAT IS BETTER AND AVERAGE PROFIT.
The current log for today must contain the following data:
(required in the log) PasswordList.txt - key file. There the stealer virus records all logins and passwords from the victim's computer and browsers.
(required in the log) ip.txt - the ip address of the victim's computer so that we can find the location in 911
(required in the log) System.txt - information about the resolution of the victim’s computer screen, operating system, etc. (needed if you use an antidetect browser)
(required in the log) CookieList.txt - a file that contains all the .sites visited by the victim.
(required in the log) Screen.jpg - screenshot of the victim's desktop
(required in the log) Browsers folder - contains browser cookies in .txt format, which you will need to reformat into json format.
(not always in the log) The Coins (Crypto) folder is a treasured folder that contains folders in itself. Each folder is called the name of the cryptocurrency, and inside the folder - wallet.dat files.
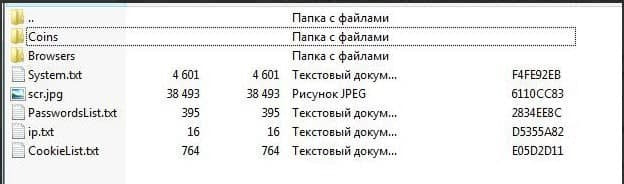
We need the coveted Coins folder. Go into it and see the following folders:
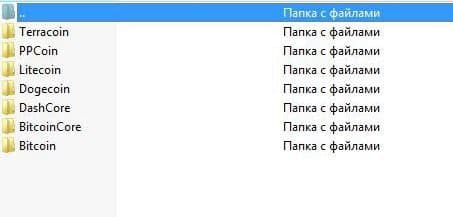
Go to the Bitcoin folder and see this.
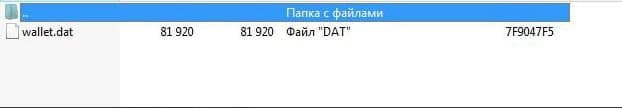
Pay attention to the weight of the file. Pacifiers usually weigh very little. That is, if the file weighs a couple of bytes or kilobytes, you can not waste time on it and move on.
Actually, what you should pay attention to: there can be a lot of cryptocurrencies in the Coins folder, BUT, you should not grab onto everything at once.
Yes, the balance may be there, but you will not have enough resources and memory on your computer to work out 100-200 logs a day.
The main crypto wallets that I steal are:
BTC / BCH / ETH / ETC / XRP / DOGE / LTC / RAVENCOIN / DASH / MONERO
These 10 wallets should be written down and learned by heart, these wallets are the easiest to steal coins from. For the rest, the principle is almost the same.
- 1.2 - How to find the wallet address from wallet.dat?
We take our wallet.dat file and for convenience you can transfer it to your desktop.
Rename the file to wallet.txt
It should look the same as in the screenshot
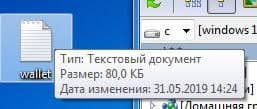
In a big family, they don’t snap fucking. Go ahead.
Now we just open the file with a notepad, and we see an incomprehensible fucked up, from which, naturally, I will teach you how to pull the wallet address.
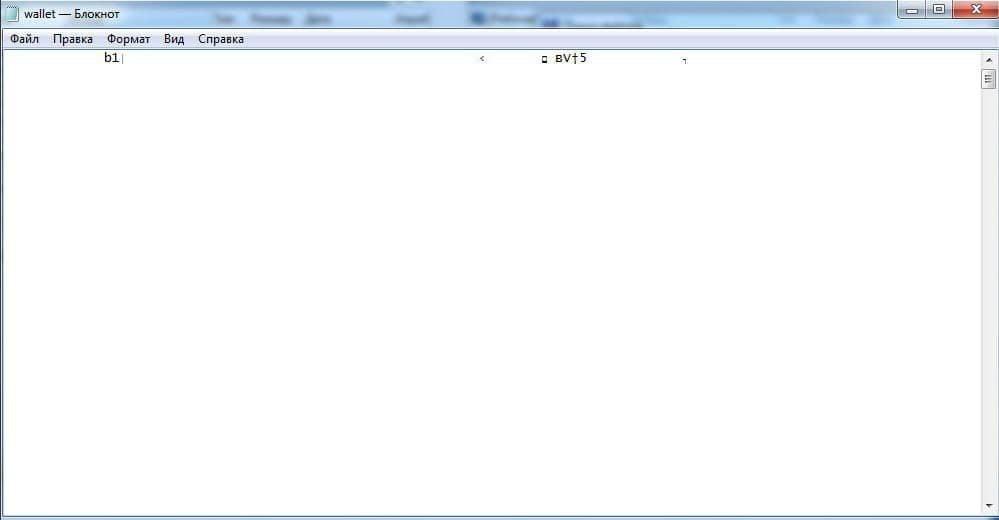
When the file is open, press the Ctrl + F hotkeys to open the search in the file.
A window should open, as in the screenshot
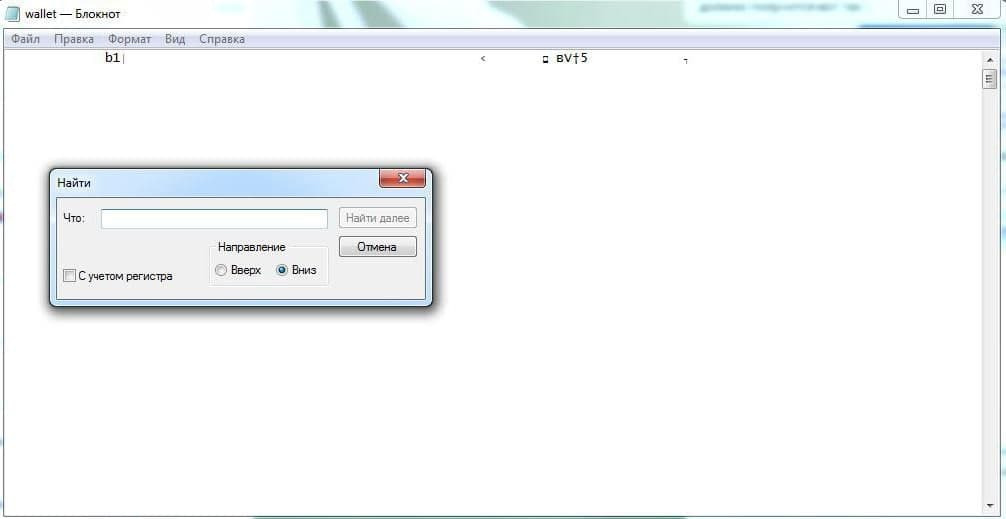
In the line "What:" we enter the word name.
Click the "Find Next" button and get our cherished wallet address
It all looks like this:
Save this address in order to break through the wallet balance in the future.
Checking the balance on the wallet
Go here https://www.blockchain.com/search?search (or any explorer, depending on the wallet you received (btc / doge / xrp, etc.)
We are now examining an example of btc, and it's the easy, but in order to get the same RAVENCOIN, Google Explorer Raven Coin and go to the site resulting in all purses everything the same way.
We see the following (on the screenshot)
We take the wallet address and paste it into the Search tab.
Click Search.
We see 2 wallets, BTC and BCH
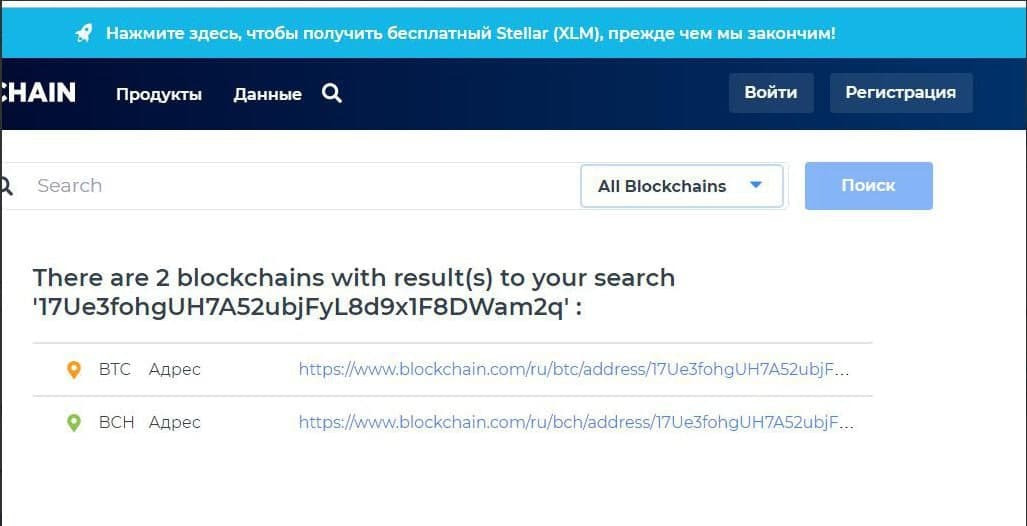
We process the btc wallet and select it accordingly.
We see in the item Total received the number of transactions and the amount that were on the wallet.
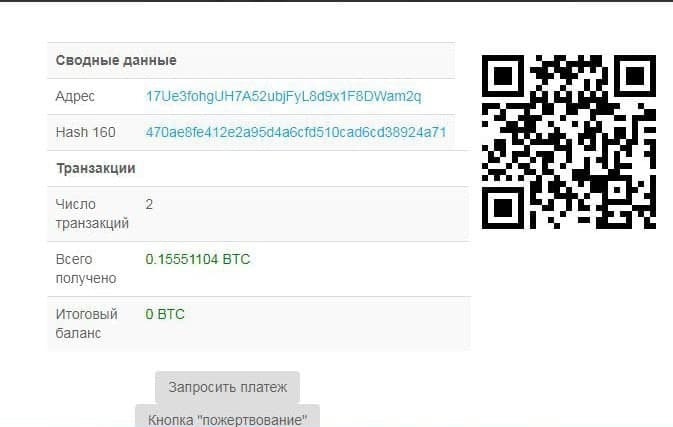
The final balance is empty, which means the wallet is without money. We
- 1.4 - How to withdraw balance.
Despite the fact that we have an empty wallet, we will touch upon the moment of how to get to the wallet and withdraw money, if they are there.
People who are closely involved crypto wallets already have separate dedicated servers, or on your PC - NETWORK bulging BTC and other popular cryptocurrency
In writing google: Download Network "NAME crypto"
For example, the cue ball, just give a link https://bitcoin.org
As we can read there, the blockchain network is the most difficult, for its storage you need a little more than 200 GB on your hard disk, there are three options:
- Download to the main machine.
- Buy an external hard drive and upload it to it.
- Rent a Dedicated Server with a suitable memory (about $ 180-200 per month rent).
After we have downloaded the entire btc network (or another coin), we replace the wallet.dat files in the root folder of the network and launch our wallet.
Synchronization and entry to the wallet depends on the power of the computer, for me it is 2-3 hours on the strength.
But not always and everything is so simple.
After the wallet is fully synchronized with the network, we will have two options:
1 - We are admitted into the wallet and the balance is drained.
2 - We are required to enter the password from the wallet (it was encrypted).
How to bypass the password on the wallet and withdraw money from there?
If, after all the work, you are asked for a password, by and large it does not matter.
All we need is to go to our PasswordList.txt and see what passwords the wallet holder used, just try everything one by one, it often helps.
If the brute force was unsuccessful, there are craftsmen on the forums who brute wallets, contact them, and they will open this wallet for you for a percentage, mostly 50/50 within 48 hours.
We are smoothly moving to STAGE 2, by removing 2fa from the exchanges.
Let's start by checking the balance and entering the wallet, and we will analyze it using the example of the coinbase exchange.
We take our log, by ip in the ip.txt file we look at its GEO location (country) We will
try to break into coinbase by login and password thanks to the PasswordList.txt file
1. Install the same Portable version of the browser as the text file with cookies (who is in the tank, I explain - in the PasswordList, in addition to the login and password, the browser from which the authorization took place is indicated. In the Browsers folder, we find the cookies of this browser)
2. We cut 911 and select clean ip, similar in geolocation to the victim's ip.
3. Check the ip on whatleaks.com (everything should be green)
4. We also grab the login and password from the mail and first of all we enter it (the mail is the same as the coinbase account). Even if coinbase asks you for 2fa, you can easily bypass it using mail.
5. Going to the mail, we look for all letters from the coinbase exchange (in the search bar we write coinbase.com) replenishment, withdrawals, wallet addresses. We take the wallet and go to punch it as described in the first stage of our training on wallet.dat
I sent the code to the phone, or the code from 2fa in the mail does not let you in, we think whether it is worth spending money on calling the service and drawing for the sake of balance.
Yes, yes, sometimes you need to use calling services, and drawing documents (passports or other documents to prove that you are the owner of the account)
. Collect information about the account owner using all kinds of sites with PasswordList, social. networks, personal correspondence, etc.
How to find wallet dat files and cryptologists
The first is crypto-related forums, we register and make topics for help in recovering wallet.dat
You will be quickly contacted.
Second - Telegram (start page 2) offer people wherever you can open wallet.dat for a percentage + a report on each log.
Conditions 60/40, in any case they took it free of charge, it turned out to be opened - well done! Stuck somewhere? They gave it to the services for autopsy, they give 50 to 50.
10% is also money, but at the start we need it.
As for the development of wallet.dat, it is
worth taking, preferably from the development or old clouds of logs.
The priority is 2015-2016-2017, while passwords were not put on wallets yet, it's just a bomb if you find such. Now the approximate price of one wallet.dat is $ 1 per working off, you can pick up from me in bulk only at $ 0.5 per piece from 20 pieces.
As far as exchanges are concerned, we need fresh logs, cookies + valid mail! Sold without valid mail, ask for a replacement.
As for my requests in the logs.
Here I did not cite anything, since all exchanges are suitable for everyone and you need to select the giving sites / exchanges.
We are looking for crypto exchanges through Google, create a list of sites for yourself that you met in your logs and were associated with crypto, crypto games, casinos and bets.
Recently, I have become addicted to crypto casinos and am actively leaking them, look in requests for stake.com / primedice.com / bitsler.com
That's all for today, friends. This is just an introduction and a grain of sand in the ocean of everything you learn about crypto wallets. We will return to this topic more than once. The information is not new and not completely relevant, but this is the first step and a new direction that has opened for you today.
And also, for those who still came to the end - in the following topics there will be lectures with detailed analyzes of how to work with logs. How to import cookies, which bindings are relevant in work, which ip is better to use and how to set up 911.
Gather a list of sites for cryptomats, crypto wallets, casinos and affiliate programs. Sometimes the logs contain so much money that even the same PayPal or bank is bullshit, in comparison with what is on the NoName site.
And imagine how offended you bitch will be when you don't even pay attention to this site and try to enter it?
P.S. Under these sites, they also write in the future brutus, but this, my dear friend, is a completely different story.
