CISA and NIST are losing their grip, but the private sector is saving the day.
In May 2024, recorded 103 vulnerabilities (CVE) that were publicly disclosed as exploitable for the first time. Compared to April, this number increased by 90.7%, which corresponds to an overall increase in the number of exploited vulnerabilities. Meanwhile, Verizon's 2024 report shows a 180% increase in the number of exploitable vulnerabilities from 2022 to 2023.
Of the 103 vulnerabilities with existing evidence of exploitation identified in May, 58 software vendors were linked to 73 unique products. Among them, the leaders are Google Chrome (7 vulnerabilities), Microsoft Windows (5), Apple Safari (5) and Adobe Acrobat Reader (3). Microsoft Exchange, Oracle JDK and phpMyAdmin also stand out with two vulnerabilities each. Newcomers to the list are TP-Link TL-R600VPN and Arcserve Unified Data Protection.
The significant increase in disclosure of new exploits of vulnerabilities is due to several factors. Among them — the publication of reports by Fortinet, CheckPoint and Aqua Security, which provided data on 49 unique vulnerabilities. This indicates the willingness of vendors to share broader operational information, which is a positive trend for security teams.
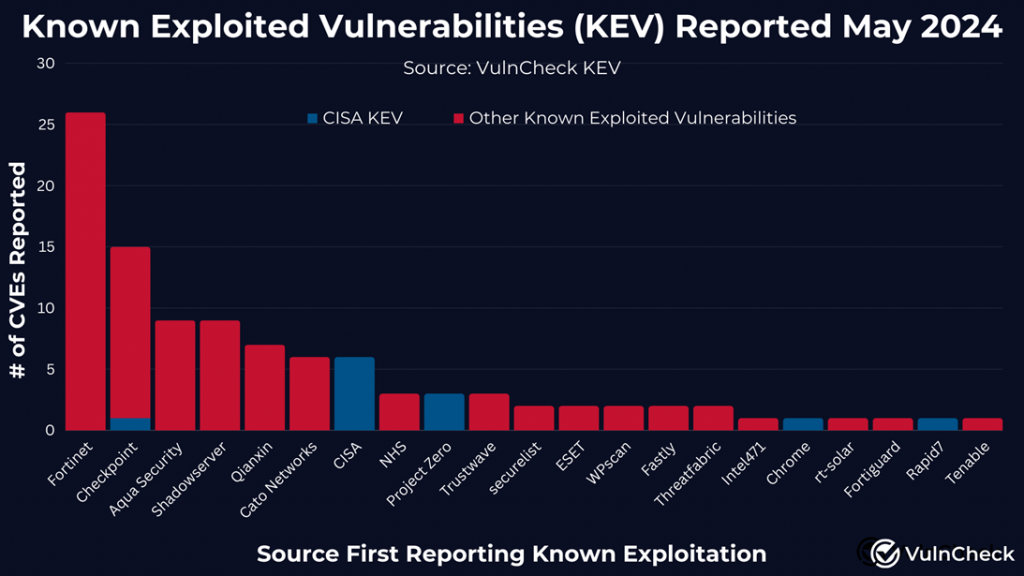
VulnCheck itself also notes a significant decline in the productivity of such mastodons in the information security world as CISA and NIST. So, in May, CISA added only 14 actively exploited vulnerabilities to its KEV list, which is 13.6% of the number of such vulnerabilities detected by VulnCheck during this period.
Meanwhile, NIST added only 22 of the 103 vulnerabilities reported by VulnCheck to its NVD database. And even out of those 22 vulnerabilities, 10 were still awaiting analysis at the end of May.
In the field of American cybersecurity, which has often been an example in organizing and calculating vulnerabilities for the whole world, a significant shift of forces is now taking place right before our eyes. Private companies are coming to the fore, showing a significant gap from government agencies in detecting and reporting exploited vulnerabilities.
These commercial players are showing greater efficiency and willingness to share up-to-date data, while traditional leaders such as CISA and NIST are significantly behind in their ability to track and report threats in a timely manner.
This shift highlights the growing role of the private sector in ensuring cybersecurity and the need for close cooperation between commercial and government entities to effectively counter the ever-changing cyber threats.
In May 2024, recorded 103 vulnerabilities (CVE) that were publicly disclosed as exploitable for the first time. Compared to April, this number increased by 90.7%, which corresponds to an overall increase in the number of exploited vulnerabilities. Meanwhile, Verizon's 2024 report shows a 180% increase in the number of exploitable vulnerabilities from 2022 to 2023.
Of the 103 vulnerabilities with existing evidence of exploitation identified in May, 58 software vendors were linked to 73 unique products. Among them, the leaders are Google Chrome (7 vulnerabilities), Microsoft Windows (5), Apple Safari (5) and Adobe Acrobat Reader (3). Microsoft Exchange, Oracle JDK and phpMyAdmin also stand out with two vulnerabilities each. Newcomers to the list are TP-Link TL-R600VPN and Arcserve Unified Data Protection.
The significant increase in disclosure of new exploits of vulnerabilities is due to several factors. Among them — the publication of reports by Fortinet, CheckPoint and Aqua Security, which provided data on 49 unique vulnerabilities. This indicates the willingness of vendors to share broader operational information, which is a positive trend for security teams.

VulnCheck itself also notes a significant decline in the productivity of such mastodons in the information security world as CISA and NIST. So, in May, CISA added only 14 actively exploited vulnerabilities to its KEV list, which is 13.6% of the number of such vulnerabilities detected by VulnCheck during this period.
Meanwhile, NIST added only 22 of the 103 vulnerabilities reported by VulnCheck to its NVD database. And even out of those 22 vulnerabilities, 10 were still awaiting analysis at the end of May.
In the field of American cybersecurity, which has often been an example in organizing and calculating vulnerabilities for the whole world, a significant shift of forces is now taking place right before our eyes. Private companies are coming to the fore, showing a significant gap from government agencies in detecting and reporting exploited vulnerabilities.
These commercial players are showing greater efficiency and willingness to share up-to-date data, while traditional leaders such as CISA and NIST are significantly behind in their ability to track and report threats in a timely manner.
This shift highlights the growing role of the private sector in ensuring cybersecurity and the need for close cooperation between commercial and government entities to effectively counter the ever-changing cyber threats.
