Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
Kaspersky Lab has tested how safe developing electronics are.
In the era of technological progress, when smart devices are becoming an integral part of our everyday life, manufacturers of children's toys also do not stand aside, offering young users learning robots with Internet access.
However, as Kaspersky Lab's research has shown, innovation does not always go hand in hand with security. Experts have identified vulnerabilities in the software of one of these robots, which is a "tablet on wheels" with many functions: from training applications to video calls.
Analysis of the device revealed several potential attack vectors. In particular, it was found that the parent app needed to communicate with the robot allows you to track the child's activity and learning progress, which makes it an attractive target for attackers. An investigation of the robot's internal structure confirmed the presence of many debugging interfaces and a USB connector (signed as "Android"), which simplifies access to the system.
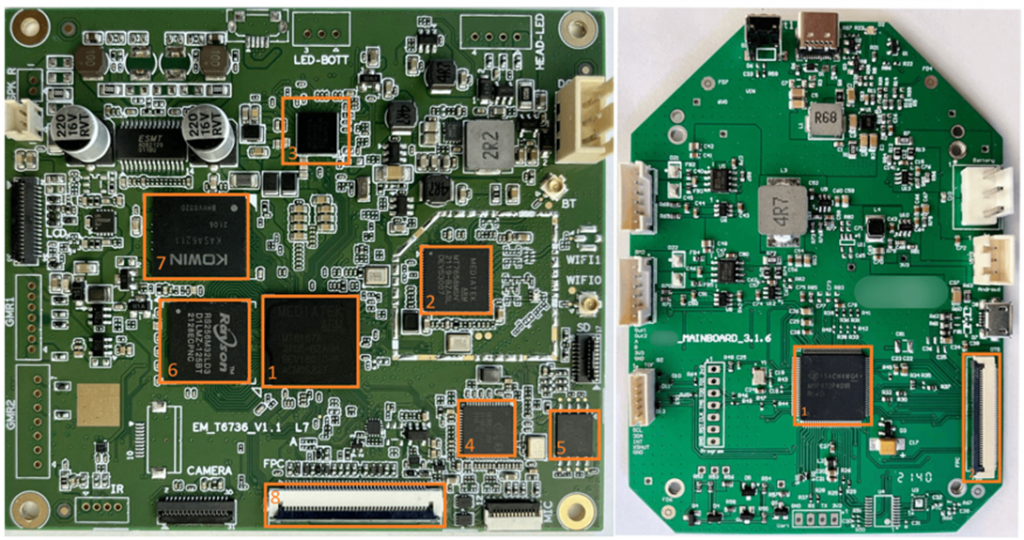
The main fee. Top view (left) and peripherals management board with USB connector (right)
Special attention was paid to the analysis of network traffic, which showed that when the robot first connects to the Internet, it transmits sensitive data (the child's name and age) in clear text, which allows it to be intercepted using specialized software. In addition, the possibility of gaining access to the robot by exploiting vulnerabilities in the authentication system and device configuration was identified.
The study also revealed a vulnerability that allows attacks on the software update process, which can lead to remote execution of commands on a device with superuser rights. A separate alarm is caused by the possibility of" re-linking " the robot to the attacker's account, which leads to the loss of control over the device by the rightful owner.
In addition, experts noted that the attacker can make video calls to the child without the knowledge of the parents. This opportunity is opened by using the Agora service for organizing video calls, which, as it turned out, does not require strict authentication to establish a connection. The robot IDs required for the call turned out to be quite simple to find, which, combined with the lack of server-side checks, makes the device vulnerable to unauthorized video calls.

Incoming video call to the robot
This type of attack not only violates privacy, but also exposes children to the risk of encountering unwanted content or manipulation. An attacker can use a video call to lure a child out of the house or persuade them to commit dangerous actions. The lack of proper security measures in the video communication mechanism highlights the seriousness of the threat posed by smart toys without the proper level of protection.
The manufacturer, having received a report on the problems found, took measures to eliminate them, which emphasizes the importance of timely software updates to protect sensitive data. The study highlights the need to thoroughly test smart toys for safety and inform consumers about potential risks, and parents are encouraged to take a more careful approach to choosing such devices for their children.
In the era of technological progress, when smart devices are becoming an integral part of our everyday life, manufacturers of children's toys also do not stand aside, offering young users learning robots with Internet access.
However, as Kaspersky Lab's research has shown, innovation does not always go hand in hand with security. Experts have identified vulnerabilities in the software of one of these robots, which is a "tablet on wheels" with many functions: from training applications to video calls.
Analysis of the device revealed several potential attack vectors. In particular, it was found that the parent app needed to communicate with the robot allows you to track the child's activity and learning progress, which makes it an attractive target for attackers. An investigation of the robot's internal structure confirmed the presence of many debugging interfaces and a USB connector (signed as "Android"), which simplifies access to the system.

The main fee. Top view (left) and peripherals management board with USB connector (right)
Special attention was paid to the analysis of network traffic, which showed that when the robot first connects to the Internet, it transmits sensitive data (the child's name and age) in clear text, which allows it to be intercepted using specialized software. In addition, the possibility of gaining access to the robot by exploiting vulnerabilities in the authentication system and device configuration was identified.
The study also revealed a vulnerability that allows attacks on the software update process, which can lead to remote execution of commands on a device with superuser rights. A separate alarm is caused by the possibility of" re-linking " the robot to the attacker's account, which leads to the loss of control over the device by the rightful owner.
In addition, experts noted that the attacker can make video calls to the child without the knowledge of the parents. This opportunity is opened by using the Agora service for organizing video calls, which, as it turned out, does not require strict authentication to establish a connection. The robot IDs required for the call turned out to be quite simple to find, which, combined with the lack of server-side checks, makes the device vulnerable to unauthorized video calls.

Incoming video call to the robot
This type of attack not only violates privacy, but also exposes children to the risk of encountering unwanted content or manipulation. An attacker can use a video call to lure a child out of the house or persuade them to commit dangerous actions. The lack of proper security measures in the video communication mechanism highlights the seriousness of the threat posed by smart toys without the proper level of protection.
The manufacturer, having received a report on the problems found, took measures to eliminate them, which emphasizes the importance of timely software updates to protect sensitive data. The study highlights the need to thoroughly test smart toys for safety and inform consumers about potential risks, and parents are encouraged to take a more careful approach to choosing such devices for their children.

