Father
Professional
- Messages
- 2,601
- Reaction score
- 831
- Points
- 113
Memory Corruption is no longer terrible, and information security specialists can sleep in peace.
Google has introduced an innovation in its open-source Chromium browser designed to combat vulnerabilities related to memory corruption. Integrated into the web browser, the V8 is designed to minimize the risks associated with the most common vulnerabilities of the V8 JavaScript engine.
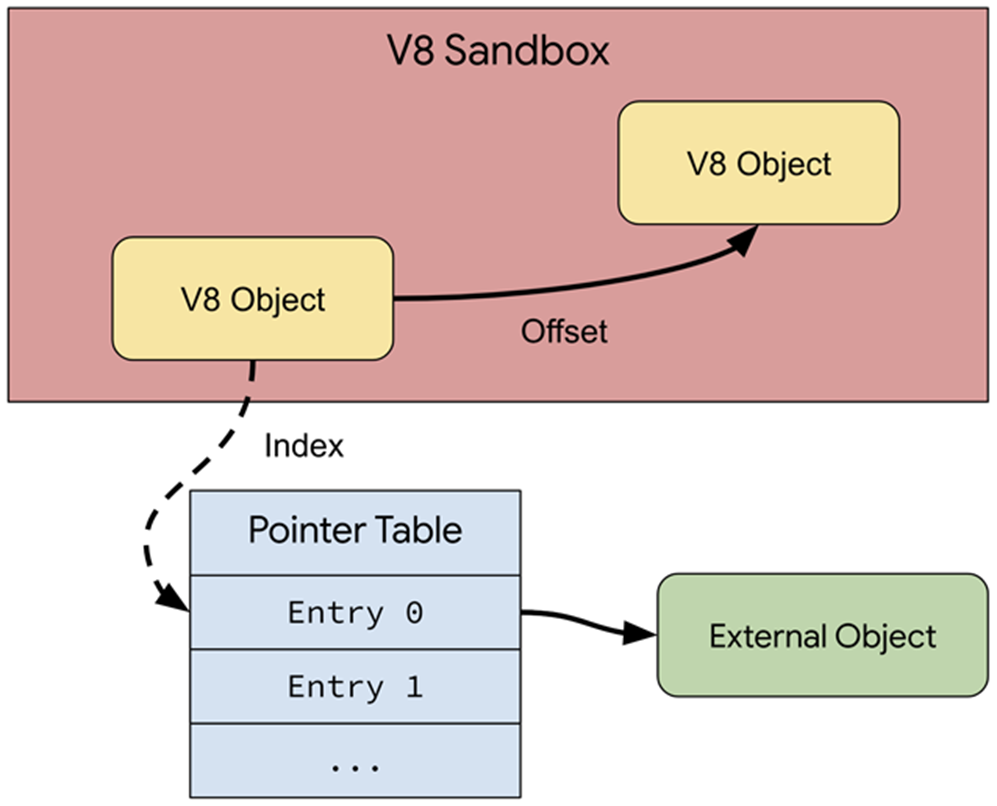
According to Samuel Gross, technical head of V8 security, the main task of the new sandbox is to prevent the spread of memory corruption within the workflow. The sandbox restricts code executed by the V8 engine to running in an isolated part of the process's virtual address space.
A significant part of the zero-day vulnerabilities that Google encountered from 2021 to 2023 were related to V8. A specialized sandbox assumes that an attacker can change any part of the memory inside the sandbox address space, but this will not lead to malicious activity going beyond it.
Gross emphasized that switching to memory-safe programming languages, such as Rust, or using hardware-based approaches to memory security does not solve the problem of V8 vulnerabilities due to subtle logic errors that can be exploited by hackers.
The new security measure is designed to isolate the heap Memory of the V8 engine so that any memory corruption cannot spread beyond the established boundaries. For this purpose, alternative data types are introduced that do not allow access to memory outside the sandbox. The sandbox is activated by a separate "v8_enable_sandbox" setting in the GN parameters.
Testing showed that the innovation introduces a load of about 1% on typical workflows, which makes it possible to implement it directly in Chrome in the near future. Experts suggest that this will happen in the 123rd version of the browser on various platforms, including Android, ChromeOS, Linux, macOS and Windows. Currently, the sandbox requires a 64-bit system with the ability to reserve one terabyte of virtual address space, but the developers plan to reduce these requirements in the future.
The initiative is part of Google's efforts to improve memory security and protect against vulnerabilities. Earlier, the company's specialists emphasized the role of Kernel Address Sanitizer (KASan) in detecting memory errors in machine code, saying that they themselves use compiler-based tools for this purpose.
Google's approach, in general, demonstrates a very responsible attitude to ensuring the security of its products, and the new sandbox for V8 is a clear example of this.
Google has introduced an innovation in its open-source Chromium browser designed to combat vulnerabilities related to memory corruption. Integrated into the web browser, the V8 is designed to minimize the risks associated with the most common vulnerabilities of the V8 JavaScript engine.
According to Samuel Gross, technical head of V8 security, the main task of the new sandbox is to prevent the spread of memory corruption within the workflow. The sandbox restricts code executed by the V8 engine to running in an isolated part of the process's virtual address space.
A significant part of the zero-day vulnerabilities that Google encountered from 2021 to 2023 were related to V8. A specialized sandbox assumes that an attacker can change any part of the memory inside the sandbox address space, but this will not lead to malicious activity going beyond it.

Gross emphasized that switching to memory-safe programming languages, such as Rust, or using hardware-based approaches to memory security does not solve the problem of V8 vulnerabilities due to subtle logic errors that can be exploited by hackers.
The new security measure is designed to isolate the heap Memory of the V8 engine so that any memory corruption cannot spread beyond the established boundaries. For this purpose, alternative data types are introduced that do not allow access to memory outside the sandbox. The sandbox is activated by a separate "v8_enable_sandbox" setting in the GN parameters.
Testing showed that the innovation introduces a load of about 1% on typical workflows, which makes it possible to implement it directly in Chrome in the near future. Experts suggest that this will happen in the 123rd version of the browser on various platforms, including Android, ChromeOS, Linux, macOS and Windows. Currently, the sandbox requires a 64-bit system with the ability to reserve one terabyte of virtual address space, but the developers plan to reduce these requirements in the future.
The initiative is part of Google's efforts to improve memory security and protect against vulnerabilities. Earlier, the company's specialists emphasized the role of Kernel Address Sanitizer (KASan) in detecting memory errors in machine code, saying that they themselves use compiler-based tools for this purpose.
Google's approach, in general, demonstrates a very responsible attitude to ensuring the security of its products, and the new sandbox for V8 is a clear example of this.

