CarderPlanet
Professional
- Messages
- 2,549
- Reaction score
- 724
- Points
- 113
The DinodasRAT backdoor did its job perfectly, giving hackers access to the target network.
In February 2023, ESET researchers discovered a targeted phishing attack that led to the deployment of a previously unknown C++ backdoor called DinodasRAT.
This cyber espionage operation was called "Jacana" and was directed at one of the government agencies of Guyana, a small state in South America bordering Venezuela.
The Slovak company believes that an APT group of Chinese origin is behind the detected attack. Such conclusions were made mainly due to hackers use of the PlugX Trojan (also known as Korplug), which is usually used by Chinese cybercriminals.
In a detailed report, ESET notes: "This campaign was targeted because the attackers created their emails specifically to attract their chosen victim organization."
The attack chain starts with a phishing email sent to the target address. The subjects of the emails included in the malicious mailing list were different, but they were related to Guyana in one way or another. One of these letters reported a certain " Guyanese fugitive in Vietnam." The link inside this phishing email led to a legitimate domain "fta.moit.gov[.] vn", which indicates that a Vietnamese government website has been compromised.
When you click on a link to a potential victim's computer, a ZIP archive containing an executable EXE file disguised as a Microsoft Word document is downloaded. Running this "document" infects the DinodasRAT computer and further compromises the target network.
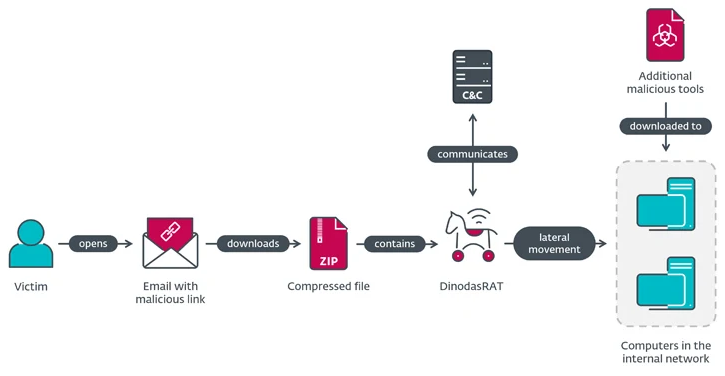
Complete chain of attack of "Operation Zhakan"
In addition to encrypting the transmitted information using the Tiny Encryption Algorithm (TEA), DinodasRAT has the ability to extract system metadata, files, manipulate Windows registry keys, and execute remote commands.
In the campaign reviewed, hackers deployed tools for lateral movement in the victim's network, including the aforementioned Korplug, as well as the SoftEther VPN client. The latter, by the way, was also used by one of the hacker groups associated with China. Microsoft tracks these criminals under the pseudonym Flax Typhoon.
ESET researcher Fernando Tavella said: "Based on the phishing emails used to gain initial access to the victim's network, it is safe to say that hackers track the geopolitical activities of their victims in order to increase the probability of success of the operation."
As this attack shows, even small countries like Guyana can become targets for sophisticated cyber-espionage operations by foreign powers. To protect yourself from such attacks, you need to invest in reliable cybersecurity systems and staff training.
In February 2023, ESET researchers discovered a targeted phishing attack that led to the deployment of a previously unknown C++ backdoor called DinodasRAT.
This cyber espionage operation was called "Jacana" and was directed at one of the government agencies of Guyana, a small state in South America bordering Venezuela.
The Slovak company believes that an APT group of Chinese origin is behind the detected attack. Such conclusions were made mainly due to hackers use of the PlugX Trojan (also known as Korplug), which is usually used by Chinese cybercriminals.
In a detailed report, ESET notes: "This campaign was targeted because the attackers created their emails specifically to attract their chosen victim organization."
The attack chain starts with a phishing email sent to the target address. The subjects of the emails included in the malicious mailing list were different, but they were related to Guyana in one way or another. One of these letters reported a certain " Guyanese fugitive in Vietnam." The link inside this phishing email led to a legitimate domain "fta.moit.gov[.] vn", which indicates that a Vietnamese government website has been compromised.
When you click on a link to a potential victim's computer, a ZIP archive containing an executable EXE file disguised as a Microsoft Word document is downloaded. Running this "document" infects the DinodasRAT computer and further compromises the target network.

Complete chain of attack of "Operation Zhakan"
In addition to encrypting the transmitted information using the Tiny Encryption Algorithm (TEA), DinodasRAT has the ability to extract system metadata, files, manipulate Windows registry keys, and execute remote commands.
In the campaign reviewed, hackers deployed tools for lateral movement in the victim's network, including the aforementioned Korplug, as well as the SoftEther VPN client. The latter, by the way, was also used by one of the hacker groups associated with China. Microsoft tracks these criminals under the pseudonym Flax Typhoon.
ESET researcher Fernando Tavella said: "Based on the phishing emails used to gain initial access to the victim's network, it is safe to say that hackers track the geopolitical activities of their victims in order to increase the probability of success of the operation."
As this attack shows, even small countries like Guyana can become targets for sophisticated cyber-espionage operations by foreign powers. To protect yourself from such attacks, you need to invest in reliable cybersecurity systems and staff training.

