Brother
Professional
- Messages
- 2,590
- Reaction score
- 525
- Points
- 113
AhnLab described the process of obtaining access and further activity of hackers on SSH servers.
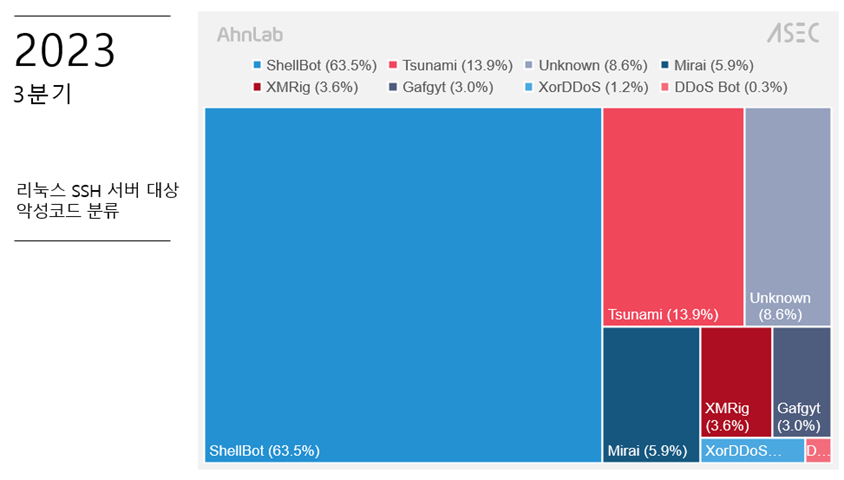
Experts at the AhnLab Security Emergency Response Center (ASEC) warn of an increase in attacks targeting poorly managed Linux SSH servers, primarily aimed at installing DDoS bots and the CoinMiner cryptocurrency miner.
At the intelligence stage, attackers perform a scan of IP addresses in search of servers with SSH service activated or port 22, and then launch a brute-force or dictionary attack to obtain credentials. Cybercriminals can also install malware for scanning, perform brute-force attacks, and sell hacked IP addresses and credentials on the darknet.
Common malware used to attack poorly managed Linux SSH servers includes ShellBot, Tsunami, ChinaZ DDoS Bot, and XMRig cryptominer.
After successfully logging in, the attacker first executed the following command to check the total number of CPU cores.
> grep -c ^processor /proc/cpuinfo
Using this command assumes that the attacker has evaluated the computing power of the system, possibly to understand its ability to run certain types of malware or attack tools.
The cybercriminal then logged in again using the same credentials and uploaded the compressed file. The compressed file contains a port scanner and an SSH dictionary attack tool. In addition, you can see commands accidentally entered by the attacker, such as "cd /ev / network" and "unaem 0a".
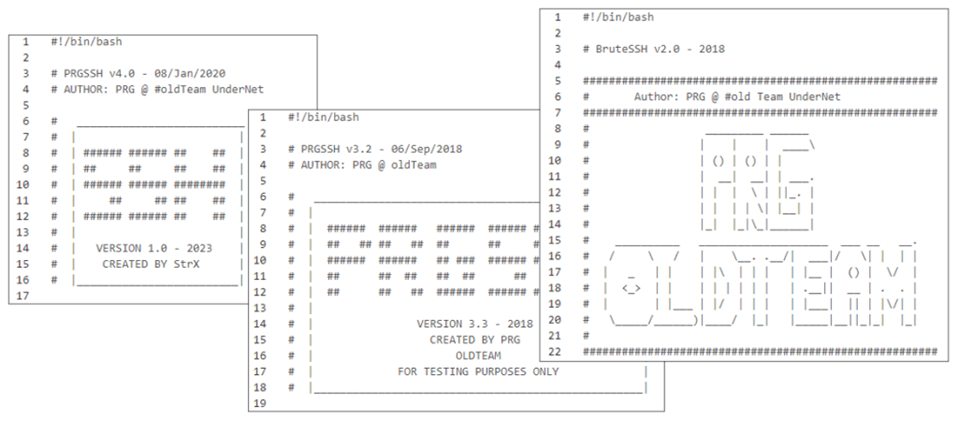
ASEC believes that the tools used in the attacks are based on tools created by the old PRG team. Each attacker created their own version of the tools by modifying them.
Experts recommend that administrators:
It should also be taken into account that cybercriminals are constantly improving their methods and tools, so administrators and information security specialists should always stay up to date with the latest trends and developments in the field of cybersecurity. Understanding how attackers carry out their attacks will allow you to counter them more effectively and protect valuable data and resources.
Experts at the AhnLab Security Emergency Response Center (ASEC) warn of an increase in attacks targeting poorly managed Linux SSH servers, primarily aimed at installing DDoS bots and the CoinMiner cryptocurrency miner.
At the intelligence stage, attackers perform a scan of IP addresses in search of servers with SSH service activated or port 22, and then launch a brute-force or dictionary attack to obtain credentials. Cybercriminals can also install malware for scanning, perform brute-force attacks, and sell hacked IP addresses and credentials on the darknet.
Common malware used to attack poorly managed Linux SSH servers includes ShellBot, Tsunami, ChinaZ DDoS Bot, and XMRig cryptominer.

After successfully logging in, the attacker first executed the following command to check the total number of CPU cores.
> grep -c ^processor /proc/cpuinfo
Using this command assumes that the attacker has evaluated the computing power of the system, possibly to understand its ability to run certain types of malware or attack tools.
The cybercriminal then logged in again using the same credentials and uploaded the compressed file. The compressed file contains a port scanner and an SSH dictionary attack tool. In addition, you can see commands accidentally entered by the attacker, such as "cd /ev / network" and "unaem 0a".
ASEC believes that the tools used in the attacks are based on tools created by the old PRG team. Each attacker created their own version of the tools by modifying them.

Experts recommend that administrators:
- use strong passwords that are difficult to guess and change them periodically;
- regularly update the software to the latest version to prevent attacks that exploit known vulnerabilities;
- use firewalls for servers accessible from outside to restrict access by intruders.
It should also be taken into account that cybercriminals are constantly improving their methods and tools, so administrators and information security specialists should always stay up to date with the latest trends and developments in the field of cybersecurity. Understanding how attackers carry out their attacks will allow you to counter them more effectively and protect valuable data and resources.
