Man
Professional
- Messages
- 3,079
- Reaction score
- 615
- Points
- 113
Various tools and methods have been developed for these purposes, such as Pluggable Transports and Project V. But schemes using FHE (fully homomorphic encryption) are of particular interest, since this is the most advanced frontier in the development of cryptographic science. In a nutshell, FHE allows you to perform calculations on encrypted data without decrypting it. This opens up completely new possibilities. For example, you can process confidential user data on the server without disclosing it to the server.
Fully Homomorphic Encryption (FHE) is sometimes called the Holy Grail of cryptography.
It is “absolute encryption” in the sense that it provides quantum-safe computation on encrypted data, ensuring that the plaintext data and the computational results derived from it are never revealed and remain secure from modification and/or tampering, even in the case of a compromised infrastructure.
Most FHE schemes are based on lattices that are resistant to quantum computing and are considered PQC (post-quantum cryptography).

Array with different levels of Gaussian noise, source
Main characteristics of FHE:
The FHE scheme is based on standard public-key cryptography (PKE) and supports all asymmetric encryption features.
According to experts, commercial application of FHE is not far off. Among other things, the following options for using this scheme can be highlighted:
Currently, the main problem on the way to the implementation of homomorphic encryption is the high resource intensity of such schemes. Academic research is being conducted in this area, including for the creation of FHE hardware accelerators.
After the widespread implementation of FHE, access to data will be completely separated from its processing, which will immediately transform hosting and cloud computing services.
In recent years, the first examples of real-world use of homomorphic encryption have begun to appear. For example, the Spiral Wiki service for private reading of Wikipedia.
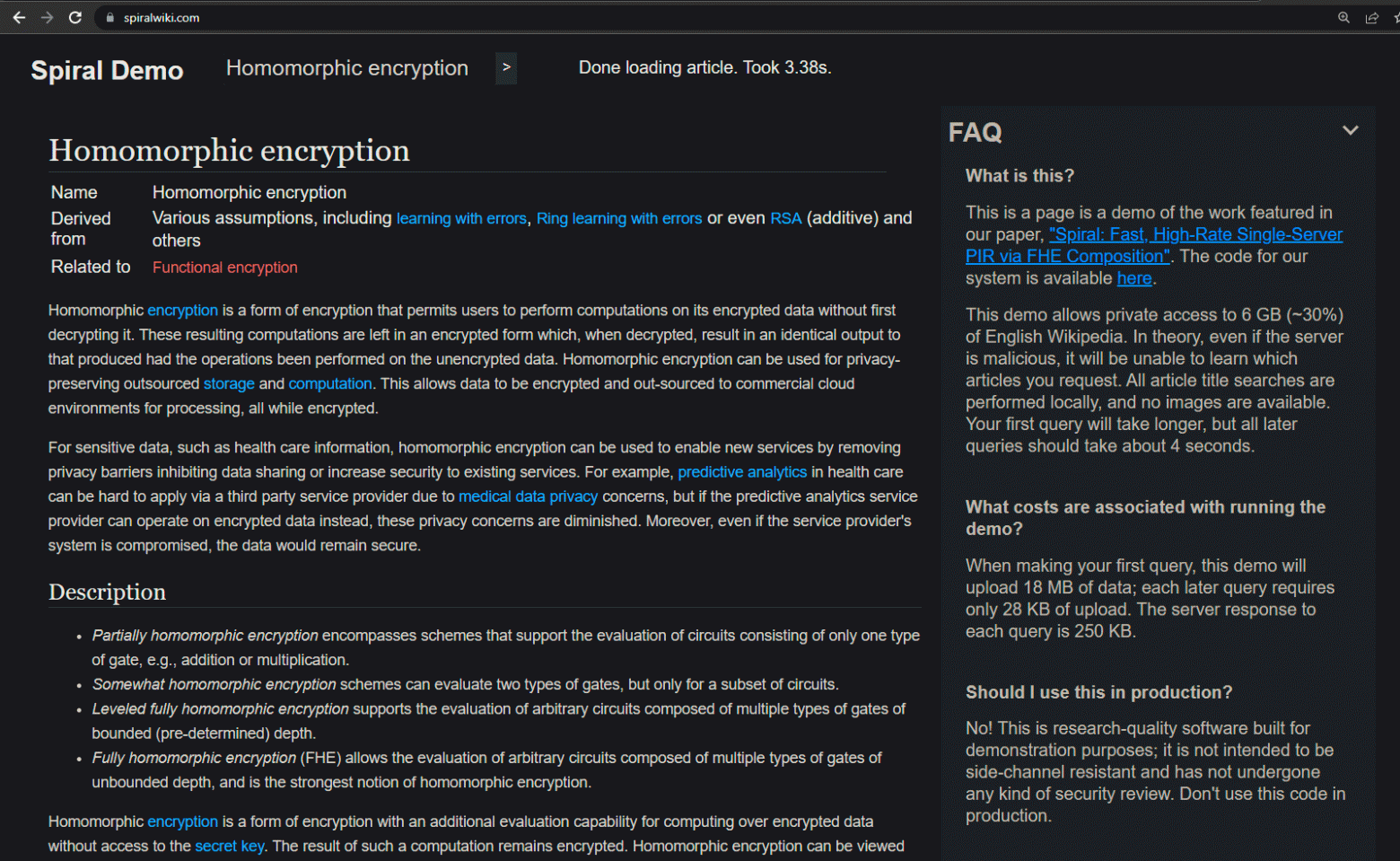
Spiral Wiki
This is just a demo page for FHE. In the future, services for encrypting access to websites and obfuscating all traffic using Spiral technology may be implemented this way.

Server processing of a Spiral request, source
The Spiral technology is described in more detail in a scientific article , the client and server code is published here.
The IETF is currently considering a new standard, Oblivious HTTP, to redirect encrypted HTTP requests in such a way that the server cannot distinguish between clients, as if "forgetting" them immediately after servicing a particular request.
That is, from the server's point of view, all requests to it will appear equally "anonymous", and may belong to one or more clients. This is done to better protect users from surveillance.
According to some experts, the widespread commercial application of FHE can be compared to the invention of computer databases, cloud computing, PKE and artificial intelligence. It will bring about major changes in the way confidential information is protected, processed and exchanged, and will fundamentally change the development of computing.
Source
Homomorphic encryption is a form of encryption that allows certain mathematical operations to be performed on encrypted text and produce an encrypted result that matches the result of the operations performed on the plaintext. For example, one person could add two encrypted numbers together without knowing the decrypted numbers, and then another person could decrypt the encrypted sum—obtaining the decrypted sum without knowing the decrypted numbers.
A fully homomorphic system (as opposed to a partial one) supports all homomorphism functions.
Fully homomorphic encryption
Fully Homomorphic Encryption (FHE) is sometimes called the Holy Grail of cryptography.
It is “absolute encryption” in the sense that it provides quantum-safe computation on encrypted data, ensuring that the plaintext data and the computational results derived from it are never revealed and remain secure from modification and/or tampering, even in the case of a compromised infrastructure.
Most FHE schemes are based on lattices that are resistant to quantum computing and are considered PQC (post-quantum cryptography).

Array with different levels of Gaussian noise, source
Main characteristics of FHE:
- Data, including computed derivatives, remains encrypted both at rest and throughout its lifecycle and is only decrypted in a secure, trusted environment.
- Valuable insights can be extracted from data using artificial intelligence (AI), big data and analytics, all without revealing data, secret keys or code.
The FHE scheme is based on standard public-key cryptography (PKE) and supports all asymmetric encryption features.
Application of FHE
According to experts, commercial application of FHE is not far off. Among other things, the following options for using this scheme can be highlighted:
- Evidence-based security models as a mandatory requirement for IT infrastructure design.
- Increasing regulatory requirements and the widespread adoption of quantum computers will make post-quantum cryptography mandatory in the public and commercial sectors.
- Aggregating sensitive data from multiple sources without disclosing it will open up new ways for organizations to partner, stimulating the development of the information economy.
- Valuable intellectual property will be protected from disclosure even when working on untrusted platforms (e.g. someone else's hosting or PC).
- Ensuring data integrity throughout the entire sensor-processing-execution chain (additional information protection in the Internet of Things).
- New revenue models from licensing confidential data without disclosing it.
Currently, the main problem on the way to the implementation of homomorphic encryption is the high resource intensity of such schemes. Academic research is being conducted in this area, including for the creation of FHE hardware accelerators.
After the widespread implementation of FHE, access to data will be completely separated from its processing, which will immediately transform hosting and cloud computing services.
Private reading of Wikipedia
In recent years, the first examples of real-world use of homomorphic encryption have begun to appear. For example, the Spiral Wiki service for private reading of Wikipedia.

Spiral Wiki
This is just a demo page for FHE. In the future, services for encrypting access to websites and obfuscating all traffic using Spiral technology may be implemented this way.

Server processing of a Spiral request, source
The Spiral technology is described in more detail in a scientific article , the client and server code is published here.
"Forgetful" server
The IETF is currently considering a new standard, Oblivious HTTP, to redirect encrypted HTTP requests in such a way that the server cannot distinguish between clients, as if "forgetting" them immediately after servicing a particular request.
That is, from the server's point of view, all requests to it will appear equally "anonymous", and may belong to one or more clients. This is done to better protect users from surveillance.
The Future of FHE
According to some experts, the widespread commercial application of FHE can be compared to the invention of computer databases, cloud computing, PKE and artificial intelligence. It will bring about major changes in the way confidential information is protected, processed and exchanged, and will fundamentally change the development of computing.
Source
