Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,036
- Points
- 113
Hello everyone! Just a couple of years ago, Android POS and other payment terminals with a touch screen instead of a traditional keyboard were a rarity. But everything is changing, and now the usual terminals in many stores have become history forever.
I have been repeatedly asked how keys are protected in such devices and whether they exist at all, so I got hold of several of these devices in order to finally figure it out.
So, in today's article, we will talk about Android POS and how such devices differ from regular terminals. At the same time, we will disassemble such a specimen and see how it is designed and what protection methods it has.
A long time ago I wrote about how protection against opening is arranged and how key management works in a regular payment terminal. But recently, stores have been flooded with touch terminals.
Here is the most popular example - Kozen P12, massively installed by Sberbank absolutely everywhere, from large supermarkets to retail kiosks. Everyone has seen it, many scolded it because of its disgusting UX, but many do not even realize that this box on a leg works on the most ordinary Android, on which the payment application is launched in Kiosk Mode.

Another representative, Kozen P10F.

The list, obviously, does not end with these two models. For example, aQsi 5F, which is in my city in almost every small store. In fact, there are a lot of examples, the request "online cash register with built-in acquiring" gives dozens of models. For the most part, all these devices are not just cash registers, but full-fledged payment terminals.

Of course, large vendors (VeriFone, Ingenico, PAX) have not moved away from this topic either.
After their widespread distribution, some people have legitimate concerns about whether they are safe. What if some fake application is installed there and instead of a real PIN request, some window similar to it is displayed? And is there any kind of protection system there at all, like in regular terminals? This is exactly what we are going to find out now.
So, I got my hands on two such terminals. One of them is working, and we will disassemble the second one a little later and see how it works.

The first in line is this device, known to us as Kassatka-Mini-F.

In fact, of course, the domestic stuff here is mainly cash register software, while the “real” name of this terminal is Telpo TPS900. There are quite a lot of manufacturers of such hardware, some of them also produce traditional POS. All these Telpo, Wizarpos, Sunmi, Ciontek, Aisino, Nexgo and a bunch of other companies are imported to Russia in bulk, where they are labeled, cash register and banking software is installed, a fiscal storage device is connected and sold under more resonant names, while offering additional services and providing support.

On the back there is a camera for reading barcodes, a speaker and a battery.

Under the battery there are slots for SIM and SAM cards, a slot for microSD and a compartment for the fiscal storage device covered with a lid.

The battery is unexpectedly disassemblable, I have not seen one like this for a long time.

Inside it there are two lithium-polymer cans and a protection board.

The protection board is separate.

And here is another device, aQsi 5F, known to the world as Ciontek CS10.

If I got that one as if it was dead, then this device even works and lets you into the menu. It was purchased for some symbolic amount for experiments with the FN emulator.

Even the keys are still in place.

On the back there is a camera and (judging by the icon in the battery compartment) a laser scanner window.

Under the lid there is a battery and a fiscal storage device cable.

This time the battery consists of two 18650 cans in heat shrink.

The card slots are the same. Next to the fiscal storage device cable connector there is a place for another one, apparently for some other fiscal countries.
Since the blue terminal was declared non-working, let's take it apart.
So, let's start disassembling. To do this, you need to unscrew the screws at the bottom of the case and the battery compartment and remove the printer cover (it is difficult to remove, but if you do not do this, it will simply break when dividing the case into two halves).

And here is the filling. The black plate on which the SAM card slots sit is clearly part of the protection against opening.

The tamper contact rubber.

And this solder slap is a former tamper. Yes, yes, this is what you thought. At one time, someone tried to revive this device and did not come up with anything better than to fill the tampers with tin. Moreover, he filled them frankly crookedly, affecting also the outer ring and thereby short-circuiting the safety circuit to ground.

Cellular modem antennas.

Fiscal storage cable.

Let's remove the plate. Three groups with three contact pads connect it to the safety circuit. SAM cards are connected via a ribbon cable.

And here is the motherboard. The heart of the device is the SoM SC20-E from Quectel. This module is not protected in any way, this thing is general purpose. In fact, this is the same GSM module as the Siemens/Cinterion MC55i, which was widely installed in similar devices, or the SIM800L, which is popular among Arduino enthusiasts, only this one is much cooler - it has a full-fledged Android, it has LVDS for connecting the matrix, a touchscreen controller, USB, several UARTs and other interfaces. But there is no secure key storage or anything like that. That is, despite the fact that this module is located inside the controlled area, it is not responsible for the pin pad, but the touchscreen is connected directly to it. What is important is that the module supports Secure Boot, however, the software and detailed documentation are under NDA, so it is completely unknown how to replace the keys and whether it is possible to do it at all.
Also visible on the board is a slot for chip cards, a battery, and contact pads through which the security circuit was connected to the top plate. Once there were anisotropic rubber bands, but now they are long gone. The cause of the breakdown is also visible - a torn off microUSB connector stuck to the speaker.

And here is the filling of the module. It is built on the SoC Qualcomm MSM8909, known to the world as Snapdragon 210.

Magnetic head.

GPS and Wi-Fi antennas.

The front part of the case. The rubber bands of the tampers have also long been lost.
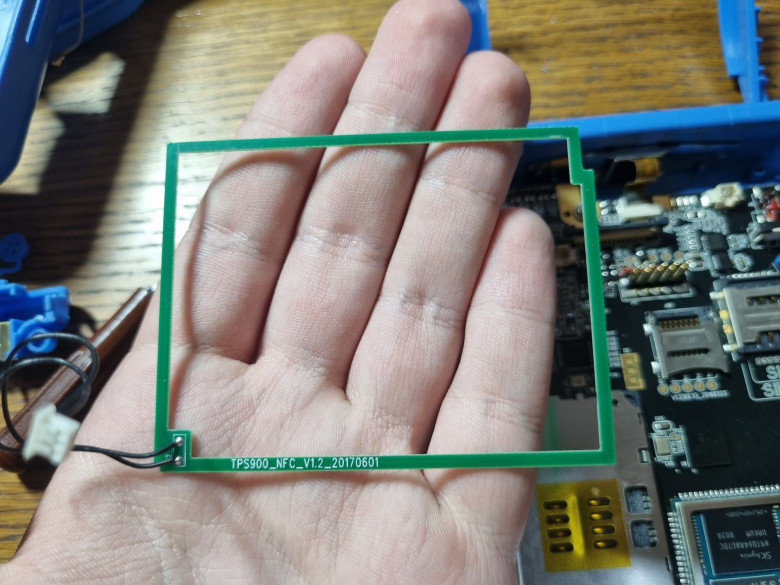
And this thing is an antenna for contactless payments. The reader itself is built on the PN5180 chip.

The back side of the board.
As we have just found out, the SoM here is of a completely general purpose and does not participate in the process of storing long-term keys and generating the PIN block. So let's look at the other chips on the board.

MP2639A is a charge controller for two lithium cells.

DRV8833 is a stepper motor driver.

FE1.1 is a four-port USB hub.
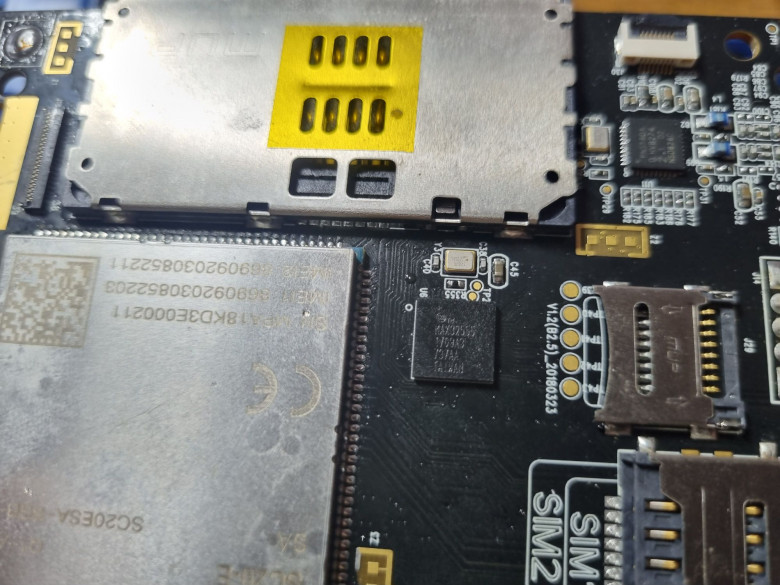
And finally, the most interesting thing is MAX32555. This is a protected microcontroller that implements all the functions of the pin pad.

The datasheet, as usual, is under malicious NDA, but some things are still available. As you can see, the MK implements almost all the "payment" functions: key storage, encryption, hardware random number generator, smart card interfaces, a three-track magnetic reader (it is enough to connect the head itself to it, the preamplifier and F/2F decoder are already inside), tampers, temperature and power control (suddenly an intruder decides to fill the chip with nitrogen or cause glitches with power supply interference). There is also a built-in protected matrix keyboard controller on board and a bunch of GPIO, so in fact, a full-fledged pin-pad with minimal strapping can be implemented on this chip (perhaps this is done in some Chinese pin-pads, but I have not disassembled them, so I cannot say for sure), and if you add a Bluetooth module, you will get an mPOS terminal. In this device, the chip is used exclusively as a key receptacle.
The whole problem was in the torn off microUSB connector. As I was told, this connector was broken after several months of work, after which it was taken to an unknown place for repairs, where they were unable to revive the device. Well, let's try to do something too.

We put the connector back in place. We supply power, wait until the battery charges at least a little, press the button, and ...

To my surprise, the screen lit up and Android began loading.

And after half a minute of waiting, the most ordinary lock screen appears. Did the disassembly really leave no trace for this thing?

No, it didn't. There is a message on the screen about some hardware error that cannot be removed. Obviously, the reason for it is the tamper that has been triggered. It is also easy to understand that no service will take this device for repairs after such abuse.

The under-screen buttons work. You can even open running applications, but this message will not go away.

You can get to the cash register application from the lock screen. As you might guess, the acquiring activation was lost along with the keys.

The unsigned button on the right opens this menu.

You can also open the dialer for an emergency call from the lock screen.

However, all service combinations are disabled. Even *#06# does not work, as well as on other Android devices. You can't even enter Recovery on this terminal; if you try to hold down the volume button when turning on, the device simply freezes on the splash screen. And trying to upload your firmware from a computer is useless: due to Secure Boot enabled, loading an unsigned image will brick the terminal.
Of course, the FSK mentioned in that error is not frequency coding, but some low-level key like IngeTrust in Ingenico terminals.

Telpo support does not answer questions related to this.
Here is a video from YouTube, so if a white screen is displayed instead, you know what to do.
The boot process itself is here. However, as expected, the author of the video does not share details, it is possible that this is a scam.
Now there are no payment terminals left where the user can reset the tamper himself. Everywhere you need software available from the manufacturer. Depending on the model, the tamper is reset in different ways, but the essence is the same: you need special keys, which are usually generated for a specific serial number of the terminal or downloaded from the server at the time of boot activation.

Unlike "traditional" pin pads, there are many more attack opportunities here, for example, removing the screen by simply warming it up with a heat gun is not controlled by anything here. Also, no one prevents you from simply unsoldering the SoM installed there and replacing it with a module with a different firmware, where Secure Boot is not activated, thereby turning the protected terminal into a regular phone with a built-in printer. Unlike traditional POS, where for such manipulation it was necessary to throw out all the standard stuffing and assemble your own (by the way, this is not fantasy, such cases have been described, although they are rare), re-soldering a single module is a matter of fifteen minutes, ten of which will be spent on disassembling the device and removing the board.
Of course, the design shown here is not the only possible option.
This is the American Square Terminal. It also loads and gives an error after opening.
But the most interesting thing is located on the encryption module made on a separate board. There is a separate touchscreen controller, allowing the crypto processor not to receive data on presses from the main processor, but to read them itself. That is, at the moment of the PIN request, the device displays a picture with a keyboard on the screen, and reading and processing of keystrokes and encryption of the PIN is performed by the crypto processor, the system only receives a ready PIN block from it. Next to this chip there is an analog multiplexer, allowing to completely disconnect the sensor from the "android" part at the moment of the PIN request.
It works even more interestingly in aQsi (Ciontek) - when opened, the device simply stops loading, and does not respond to anything when turned on. This is due to the fact that one of the sections on the Flash is encrypted with keys that are taken from the pin-pad controller and are erased when opened.
SDK and toolkit for payment equipment are usually under NDA, so the only way to download them is to look for leaks, which I could not find for this device. However, for one of the devices (Wizarpos) I did find something interesting in the form of code samples and applications. I do not know the hardware structure of this pin-pad, but I found a code sample for working with it (as I was able to find out, most other vendors have a similar principle):
As you can see, Android does not interact with the pin pad directly, but only gives a command to request a PIN and waits for a callback that the PIN has been entered and that a PIN block can be obtained. The encryption here remains exactly the same, how it works, I already told with examples in the previous post about pin pads.
It turns out that many of these devices are as secure as traditional POS. As with them, a significant portion of the security is provided by signing applications, the hardware has also adapted to touch screens, although the basic principles remain the same. However, I am sure that all the holes have not yet been plugged, so in the future, with the wider distribution of such devices, we will learn many more interesting things, as it once happened with VeriFone and Ingenico.
That's how things are.
I have been repeatedly asked how keys are protected in such devices and whether they exist at all, so I got hold of several of these devices in order to finally figure it out.
So, in today's article, we will talk about Android POS and how such devices differ from regular terminals. At the same time, we will disassemble such a specimen and see how it is designed and what protection methods it has.
❯ The gist is this
A long time ago I wrote about how protection against opening is arranged and how key management works in a regular payment terminal. But recently, stores have been flooded with touch terminals.
Here is the most popular example - Kozen P12, massively installed by Sberbank absolutely everywhere, from large supermarkets to retail kiosks. Everyone has seen it, many scolded it because of its disgusting UX, but many do not even realize that this box on a leg works on the most ordinary Android, on which the payment application is launched in Kiosk Mode.

Another representative, Kozen P10F.

The list, obviously, does not end with these two models. For example, aQsi 5F, which is in my city in almost every small store. In fact, there are a lot of examples, the request "online cash register with built-in acquiring" gives dozens of models. For the most part, all these devices are not just cash registers, but full-fledged payment terminals.

Of course, large vendors (VeriFone, Ingenico, PAX) have not moved away from this topic either.
❯ About the safety of these devices
After their widespread distribution, some people have legitimate concerns about whether they are safe. What if some fake application is installed there and instead of a real PIN request, some window similar to it is displayed? And is there any kind of protection system there at all, like in regular terminals? This is exactly what we are going to find out now.
❯ Equipment overview
So, I got my hands on two such terminals. One of them is working, and we will disassemble the second one a little later and see how it works.

The first in line is this device, known to us as Kassatka-Mini-F.

In fact, of course, the domestic stuff here is mainly cash register software, while the “real” name of this terminal is Telpo TPS900. There are quite a lot of manufacturers of such hardware, some of them also produce traditional POS. All these Telpo, Wizarpos, Sunmi, Ciontek, Aisino, Nexgo and a bunch of other companies are imported to Russia in bulk, where they are labeled, cash register and banking software is installed, a fiscal storage device is connected and sold under more resonant names, while offering additional services and providing support.

On the back there is a camera for reading barcodes, a speaker and a battery.

Under the battery there are slots for SIM and SAM cards, a slot for microSD and a compartment for the fiscal storage device covered with a lid.

The battery is unexpectedly disassemblable, I have not seen one like this for a long time.

Inside it there are two lithium-polymer cans and a protection board.

The protection board is separate.

And here is another device, aQsi 5F, known to the world as Ciontek CS10.

If I got that one as if it was dead, then this device even works and lets you into the menu. It was purchased for some symbolic amount for experiments with the FN emulator.

Even the keys are still in place.

On the back there is a camera and (judging by the icon in the battery compartment) a laser scanner window.

Under the lid there is a battery and a fiscal storage device cable.

This time the battery consists of two 18650 cans in heat shrink.

The card slots are the same. Next to the fiscal storage device cable connector there is a place for another one, apparently for some other fiscal countries.
❯ Internals
Since the blue terminal was declared non-working, let's take it apart.
Attention! Opening any modern POS terminal leads to its damage. It will most likely be impossible to restore it, the official service will most likely refuse to revive it after this.
So, let's start disassembling. To do this, you need to unscrew the screws at the bottom of the case and the battery compartment and remove the printer cover (it is difficult to remove, but if you do not do this, it will simply break when dividing the case into two halves).

And here is the filling. The black plate on which the SAM card slots sit is clearly part of the protection against opening.

The tamper contact rubber.

And this solder slap is a former tamper. Yes, yes, this is what you thought. At one time, someone tried to revive this device and did not come up with anything better than to fill the tampers with tin. Moreover, he filled them frankly crookedly, affecting also the outer ring and thereby short-circuiting the safety circuit to ground.

Cellular modem antennas.

Fiscal storage cable.

Let's remove the plate. Three groups with three contact pads connect it to the safety circuit. SAM cards are connected via a ribbon cable.

And here is the motherboard. The heart of the device is the SoM SC20-E from Quectel. This module is not protected in any way, this thing is general purpose. In fact, this is the same GSM module as the Siemens/Cinterion MC55i, which was widely installed in similar devices, or the SIM800L, which is popular among Arduino enthusiasts, only this one is much cooler - it has a full-fledged Android, it has LVDS for connecting the matrix, a touchscreen controller, USB, several UARTs and other interfaces. But there is no secure key storage or anything like that. That is, despite the fact that this module is located inside the controlled area, it is not responsible for the pin pad, but the touchscreen is connected directly to it. What is important is that the module supports Secure Boot, however, the software and detailed documentation are under NDA, so it is completely unknown how to replace the keys and whether it is possible to do it at all.
Also visible on the board is a slot for chip cards, a battery, and contact pads through which the security circuit was connected to the top plate. Once there were anisotropic rubber bands, but now they are long gone. The cause of the breakdown is also visible - a torn off microUSB connector stuck to the speaker.

And here is the filling of the module. It is built on the SoC Qualcomm MSM8909, known to the world as Snapdragon 210.

Magnetic head.

GPS and Wi-Fi antennas.

The front part of the case. The rubber bands of the tampers have also long been lost.

And this thing is an antenna for contactless payments. The reader itself is built on the PN5180 chip.

The back side of the board.
❯ What is the key storage made of?
As we have just found out, the SoM here is of a completely general purpose and does not participate in the process of storing long-term keys and generating the PIN block. So let's look at the other chips on the board.

MP2639A is a charge controller for two lithium cells.

DRV8833 is a stepper motor driver.

FE1.1 is a four-port USB hub.

And finally, the most interesting thing is MAX32555. This is a protected microcontroller that implements all the functions of the pin pad.

The datasheet, as usual, is under malicious NDA, but some things are still available. As you can see, the MK implements almost all the "payment" functions: key storage, encryption, hardware random number generator, smart card interfaces, a three-track magnetic reader (it is enough to connect the head itself to it, the preamplifier and F/2F decoder are already inside), tampers, temperature and power control (suddenly an intruder decides to fill the chip with nitrogen or cause glitches with power supply interference). There is also a built-in protected matrix keyboard controller on board and a bunch of GPIO, so in fact, a full-fledged pin-pad with minimal strapping can be implemented on this chip (perhaps this is done in some Chinese pin-pads, but I have not disassembled them, so I cannot say for sure), and if you add a Bluetooth module, you will get an mPOS terminal. In this device, the chip is used exclusively as a key receptacle.
❯ First launch
The whole problem was in the torn off microUSB connector. As I was told, this connector was broken after several months of work, after which it was taken to an unknown place for repairs, where they were unable to revive the device. Well, let's try to do something too.

We put the connector back in place. We supply power, wait until the battery charges at least a little, press the button, and ...

To my surprise, the screen lit up and Android began loading.

And after half a minute of waiting, the most ordinary lock screen appears. Did the disassembly really leave no trace for this thing?

No, it didn't. There is a message on the screen about some hardware error that cannot be removed. Obviously, the reason for it is the tamper that has been triggered. It is also easy to understand that no service will take this device for repairs after such abuse.

The under-screen buttons work. You can even open running applications, but this message will not go away.

You can get to the cash register application from the lock screen. As you might guess, the acquiring activation was lost along with the keys.

The unsigned button on the right opens this menu.

You can also open the dialer for an emergency call from the lock screen.

However, all service combinations are disabled. Even *#06# does not work, as well as on other Android devices. You can't even enter Recovery on this terminal; if you try to hold down the volume button when turning on, the device simply freezes on the splash screen. And trying to upload your firmware from a computer is useless: due to Secure Boot enabled, loading an unsigned image will brick the terminal.
❯ Keys
Of course, the FSK mentioned in that error is not frequency coding, but some low-level key like IngeTrust in Ingenico terminals.

Telpo support does not answer questions related to this.
The boot process itself is here. However, as expected, the author of the video does not share details, it is possible that this is a scam.
Now there are no payment terminals left where the user can reset the tamper himself. Everywhere you need software available from the manufacturer. Depending on the model, the tamper is reset in different ways, but the essence is the same: you need special keys, which are usually generated for a specific serial number of the terminal or downloaded from the server at the time of boot activation.

Unlike "traditional" pin pads, there are many more attack opportunities here, for example, removing the screen by simply warming it up with a heat gun is not controlled by anything here. Also, no one prevents you from simply unsoldering the SoM installed there and replacing it with a module with a different firmware, where Secure Boot is not activated, thereby turning the protected terminal into a regular phone with a built-in printer. Unlike traditional POS, where for such manipulation it was necessary to throw out all the standard stuffing and assemble your own (by the way, this is not fantasy, such cases have been described, although they are rare), re-soldering a single module is a matter of fifteen minutes, ten of which will be spent on disassembling the device and removing the board.
❯ About aQsi, Square and other methods of protection
Of course, the design shown here is not the only possible option.
This is the American Square Terminal. It also loads and gives an error after opening.
But the most interesting thing is located on the encryption module made on a separate board. There is a separate touchscreen controller, allowing the crypto processor not to receive data on presses from the main processor, but to read them itself. That is, at the moment of the PIN request, the device displays a picture with a keyboard on the screen, and reading and processing of keystrokes and encryption of the PIN is performed by the crypto processor, the system only receives a ready PIN block from it. Next to this chip there is an analog multiplexer, allowing to completely disconnect the sensor from the "android" part at the moment of the PIN request.
It works even more interestingly in aQsi (Ciontek) - when opened, the device simply stops loading, and does not respond to anything when turned on. This is due to the fact that one of the sections on the Flash is encrypted with keys that are taken from the pin-pad controller and are erased when opened.
❯ Pin-pad from a programmer's point of view
SDK and toolkit for payment equipment are usually under NDA, so the only way to download them is to look for leaks, which I could not find for this device. However, for one of the devices (Wizarpos) I did find something interesting in the form of code samples and applications. I do not know the hardware structure of this pin-pad, but I found a code sample for working with it (as I was able to find out, most other vendors have a similar principle):
Code:
PINPadDevice device = (PINPadDevice) POSTerminal.getInstance(mContext)
.getDevice("cloudpos.device.pinpad");
device.open();
device.setupCallbackHandler(new PinPadCallbackHandler() {
@Override
public void processCallback(byte[] data) {
Log.e(TAG, "processCallback ");
mHandler.obtainMessage(PIN_KEY_CALLBACK, data[0]).sendToTarget();
}
@Override
public void processCallback(int nCount, int nExtra){
// don't need implement.
}
});
KeyInfo keyInfo = new KeyInfo(PINPadDevice.KEY_TYPE_MK_SK, 0, 0, 4);
String pan = "0123456789012345678";
OperationResult operationResult = device.waitForPinBlock(keyInfo, pan, false,
TimeConstants.FOREVER);
if (operationResult.getResultCode() == OperationResult.SUCCESS) {
byte[] pinBlock = ((PINPadOperationResult) operationResult).getEncryptedPINBlock();
sendSuccessLog2("PINBlock = " + StringUtility.byteArray2String(pinBlock));
} else {
sendFailedLog2(mContext.getString(R.string.operation_failed));
}
device.close();As you can see, Android does not interact with the pin pad directly, but only gives a command to request a PIN and waits for a callback that the PIN has been entered and that a PIN block can be obtained. The encryption here remains exactly the same, how it works, I already told with examples in the previous post about pin pads.
❯ So what's the bottom line?
It turns out that many of these devices are as secure as traditional POS. As with them, a significant portion of the security is provided by signing applications, the hardware has also adapted to touch screens, although the basic principles remain the same. However, I am sure that all the holes have not yet been plugged, so in the future, with the wider distribution of such devices, we will learn many more interesting things, as it once happened with VeriFone and Ingenico.
That's how things are.

