In May of this year, the Directorate “K” of the Russian Ministry of Internal Affairs, with the assistance of the Group-IB company, detained a 32-year-old resident of the Volgograd region, accused of embezzling funds from clients of Russian banks using a fake application for Internet banking, which in fact turned out to be a malicious program - Android -Trojan. Every day, with its help, from 100,000 to 500,000 rubles were stolen from users; part of the stolen money was transferred into cryptocurrency for further cashing and concealing fraudulent activities.
Analyzing the “digital traces” of the thefts, Group-IB specialists found that the banking Trojan used in the criminal scheme was disguised as the financial application “Banks in the Palm of Your Hand,” which acts as an “aggregator” of the mobile banking systems of the country’s leading banks. You could load all your bank cards into the application so as not to carry them with you, but at the same time be able to view card balances based on incoming SMS for all transactions, transfer money from card to card, pay for online services and purchases in online stores .
Interested in the capabilities of the financial aggregator, bank clients downloaded the “Banking in the Palm of Your Hand” application and entered their card details. The launched Trojan sent bank card data or logins/passwords for logging into Internet banking to the server to the attackers. After this, the criminals transferred money to pre-prepared bank accounts in amounts ranging from 12,000 to 30,000 rubles. for one transfer by entering an SMS transaction confirmation code intercepted from the victim’s phone. The users themselves did not suspect that they had become victims of cybercriminals - all SMS confirmations of transactions were blocked.
Text: Pavel Krylov, head of product development for the Secure Bank Group-IB line
Basic theft schemes through remote banking: why antiviruses do not work
Group-IB forensic experts identify seven common theft schemes that are used by cybercriminals in attacks on remote banking systems:
1) social engineering;
2) transfers from card to card;
3) transfers through online banking;
4) interception of access to mobile banking;
5) fake mobile banking;
6) purchases using Apple Pay and Google Pay;
7) theft through SMS banking.
Conventional anti-virus protection tools are practically useless against such theft schemes. For example, in the case of the use of social engineering, when a client who fell for the bait believed the scammer and independently transferred money to his account (i.e., the person himself was “hacked”), or when the victim’s details are lured out from a third-party device, antiviruses do not help.
The last layer of defense is antifraud. Most anti-fraud systems are focused on analyzing transactional information or data sent directly to the bank’s servers (client’s IP address, information about his browser, the pace of work in a web or mobile application, etc.). If we take into account that fraud as such is a process that includes not only the moment of the transaction, but also the stages of preparing and
withdrawing funds, it becomes obvious that transactional anti-fraud systems “cover” only a limited range of work of fraudsters.
Gartner analysts identify five levels of fraud prevention. We will analyze each of them in detail and with examples:
1) analysis of the user’s device (infected devices, device identification);
2) monitoring of user actions at the session level (anomalies in the user’s work: navigation, time, geography);
3) behavioral analysis of the user in a specific channel (what actions are performed in the channel? how (behavior)? who performs them?);
4) cross-channel analysis of users and their behavior (analysis of user behavior in different channels, data correlation);
5) analysis of the relationships between users and accounts (behavior on different resources, global client profile).
One of the striking examples of attacks on remote banking systems was the activity of the Lurk group, which at the end of its “career” in 2016 reached quite impressive proportions: about 50 people worked for it. Having started its journey with autofill for desktop versions of RBS (“thick” client), at the end of 2014 it implemented this method of theft for Internet banks (“thin” clients that do not require installation on the user’s PC), which significantly expanded the scope activities of the group. The client generated a payment using only the recipient's details, but this payment was received by the bank with the details changed by the Trojan program. Many experts still recognize this type of attack as the most dangerous, since it allows the client’s behavior and data to be manipulated at the most subtle level directly from the client’s device. How did this happen?
The Trojan was embedded directly into the client’s browser and made changes to its code directly in memory, which made it possible, when the client visited the bank’s official website, to intercept and modify the original HTML pages in a manner necessary for the fraudster, even when using an HTTPS connection.
In Fig. Figure 1 shows an example of a malicious injection that was added by a Trojan to the page code. The lines highlighted in gray are the URLs through which this script interacted with the fraudster’s command and control servers, where logins/passwords, balances and other information were sent, and in response the fraudster’s payment details were sent for substitution in the client’s original payment.

Rice. 1 A script embedded by a Trojan on the original Internet banking page in the client’s browser.
A less sophisticated, but effective way to steal funds is to remotely control the client’s device (Fig. 2). After automated collection using a keylogger program (literally “key interceptor”) of all necessary logins/passwords, PINs from tokens, etc. The fraudster connects to the client's device via remote control (Fig. 3) and creates a fraudulent payment directly from the client's device and on his behalf.
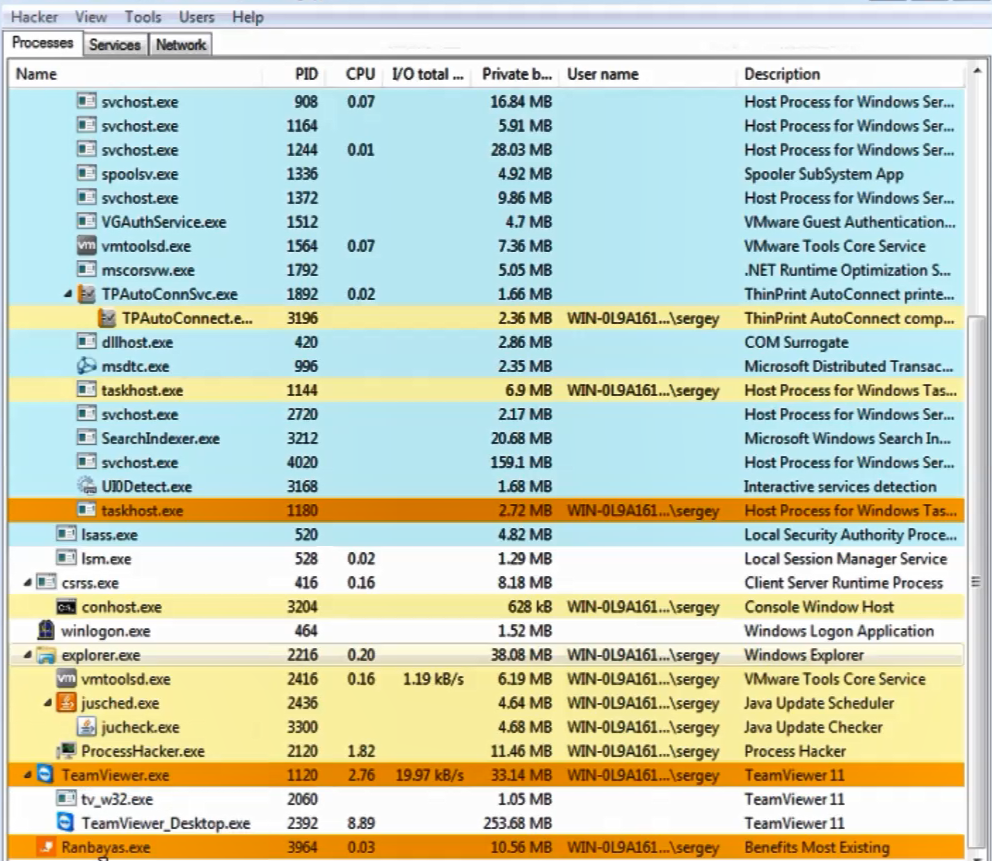
Rice. 2. Example of a computer interface infected with the Ranbayas Trojan
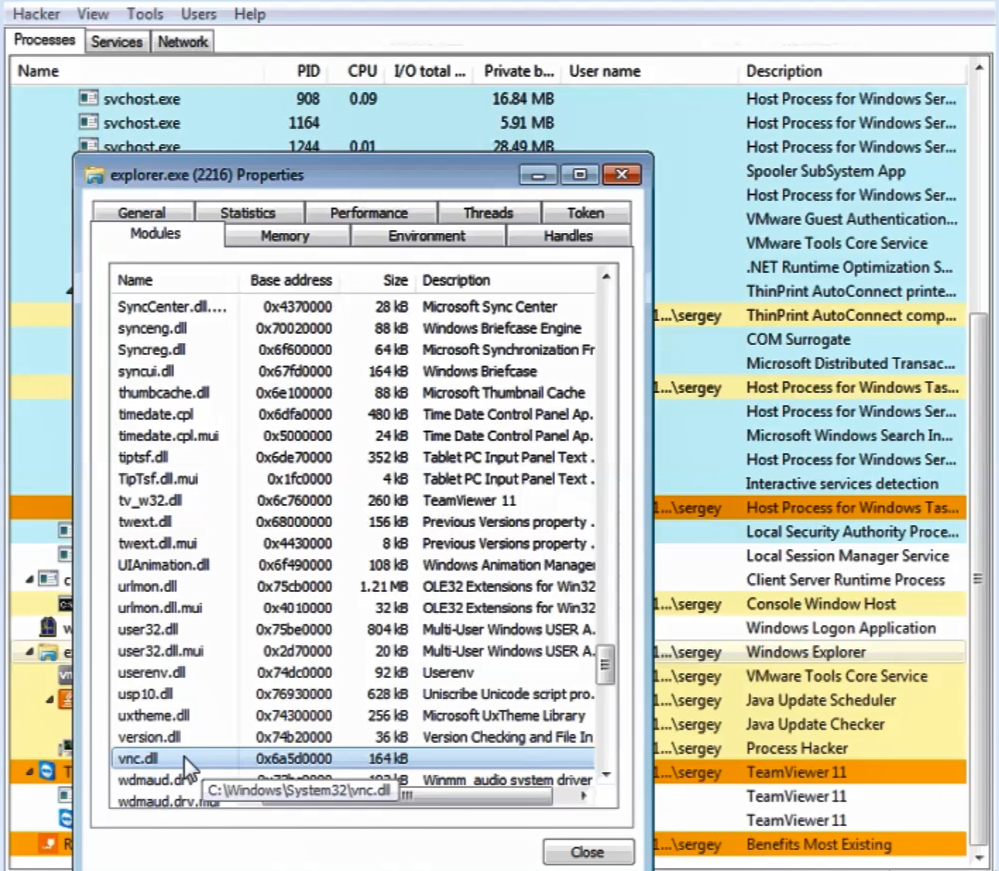
Fig. 3. Implementing a VNC remote control program in Explorer
So what are the first level fraud prevention technologies? First of all, those that allow you to effectively detect remote control when working in remote banking systems using several independent methods. However, they do not require installation of additional software on the client’s device.
Also included in the category of technologies at the first level are systems and solutions that identify the device and the user. This allows you to collect and analyze information about the devices used by a specific client (on the left in Fig. 4 is a fragment of the graph of connections between accounts and the devices they use). For example, the appearance of an unknown device in a client previously known to us is an important factor for making a decision to suspend payment and carry out additional control procedures.
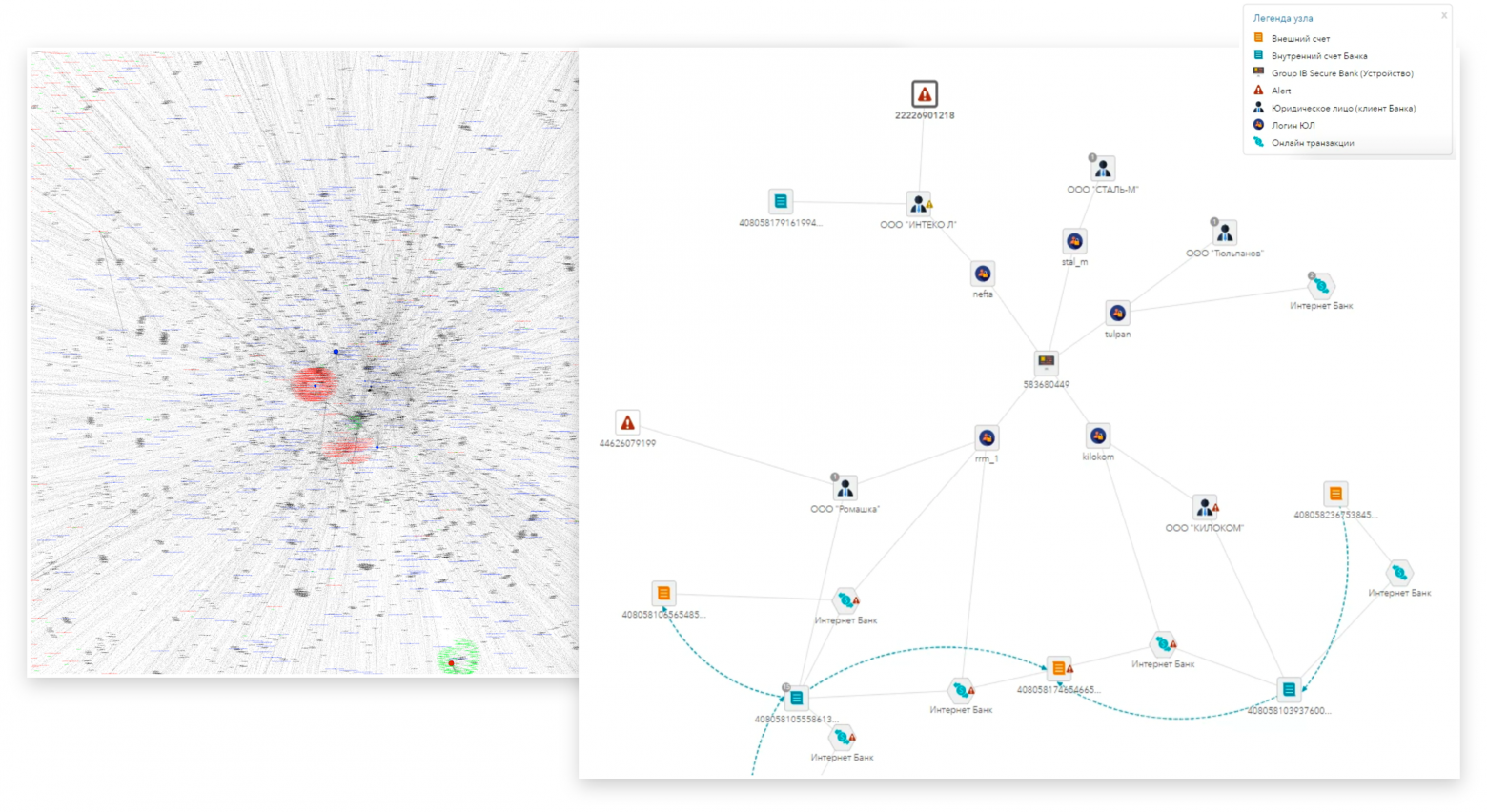
Fig.4. Graphic connections between accounts
In Fig. 4 on the right shows another example of identifying a device for proactively identifying legal entities intended for money laundering. In this example, bank employees identified, using financial analysis, a company that was engaged in money laundering (bottom of the graph on the right). Additionally, using the identifier of a legal entity, you can obtain the identifiers of the devices that were used by it (the center of the right column). And then - all other accounts that were used from the same devices (upper part of the right column) and from which the identified launderer worked. This fits very well with the nature of the work of scammers. The fraudster always has companies in stock that have not yet been used for money laundering. The bank should pay greater attention to the transactions of identified legal entities.
For example, a common case is the deception of card details and SMS codes in the process of purchasing an expensive product through popular ad sites under the pretext of making a deposit. In fact, the fraudster uses this data to go through the registration procedure in the remote banking system and gain access to the victim’s accounts. A real example of such a scenario is shown in Fig. 5.
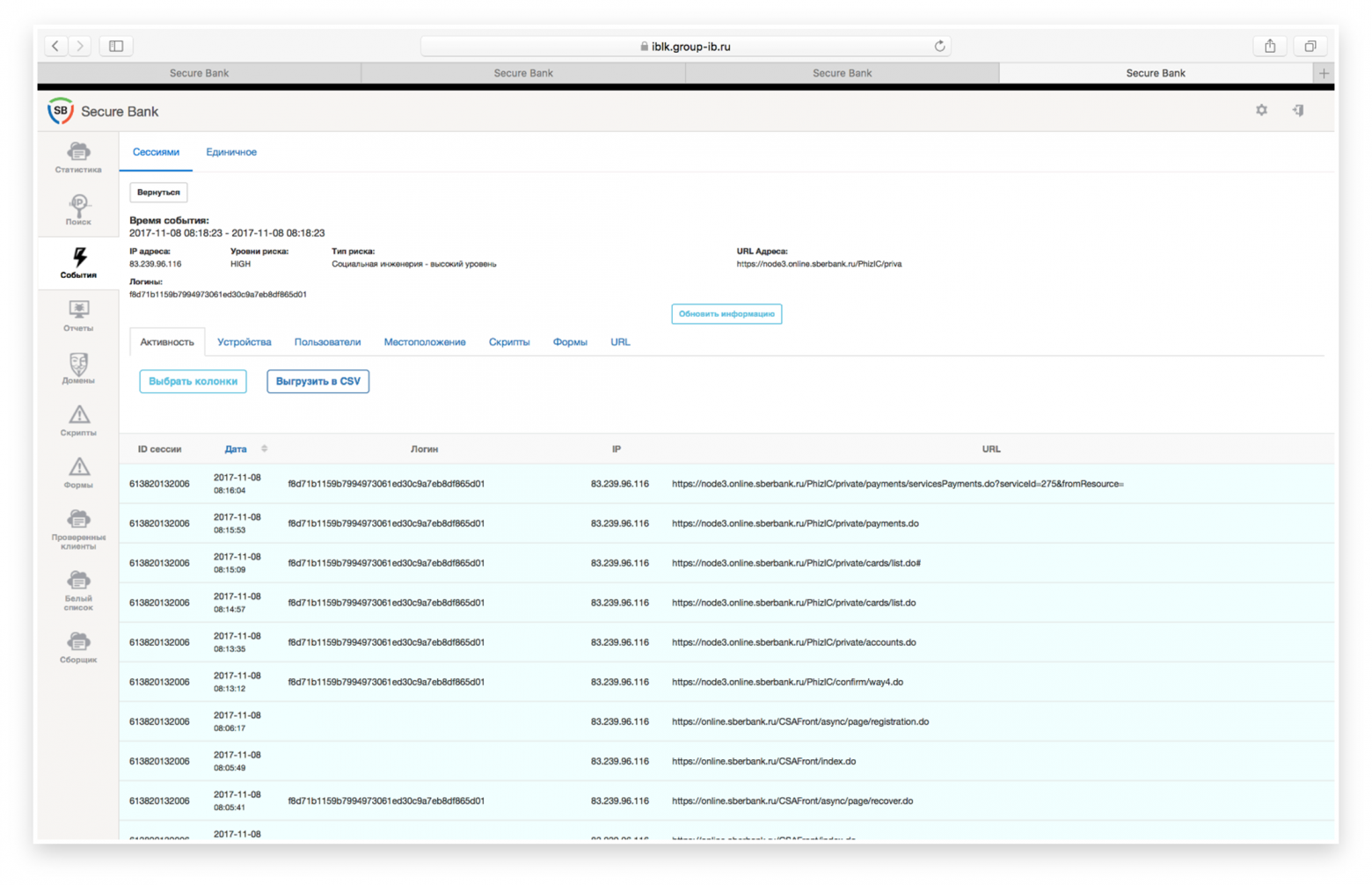
Fig. 5. Going through the procedure of registering a fraudster in RBS and gaining access to the victim’s accounts.
Analysis of the sequence of steps performed by the user in RBS allows us to identify the scenario described above. This process takes into account the results of the first level technologies (analysis of the user’s device): what device was used, whether it is typical for a given client, whether the geography has changed; the session time is taken into account and, additionally, the script used by the scammer.
This also applies to other scammers’ schemes. For example, a similar method is used to identify some of the work scenarios of launderers. It is clear that not all cases of money laundering can be tracked using behavioral characteristics alone. For example, if a company is engaged in transit, then only one analysis of behavior - what a person does in Internet banking - will not be enough to understand whether it is a transit payment or a standard one. But most cases still make it clear that something anomalous is happening and, most likely, this activity is fraudulent.
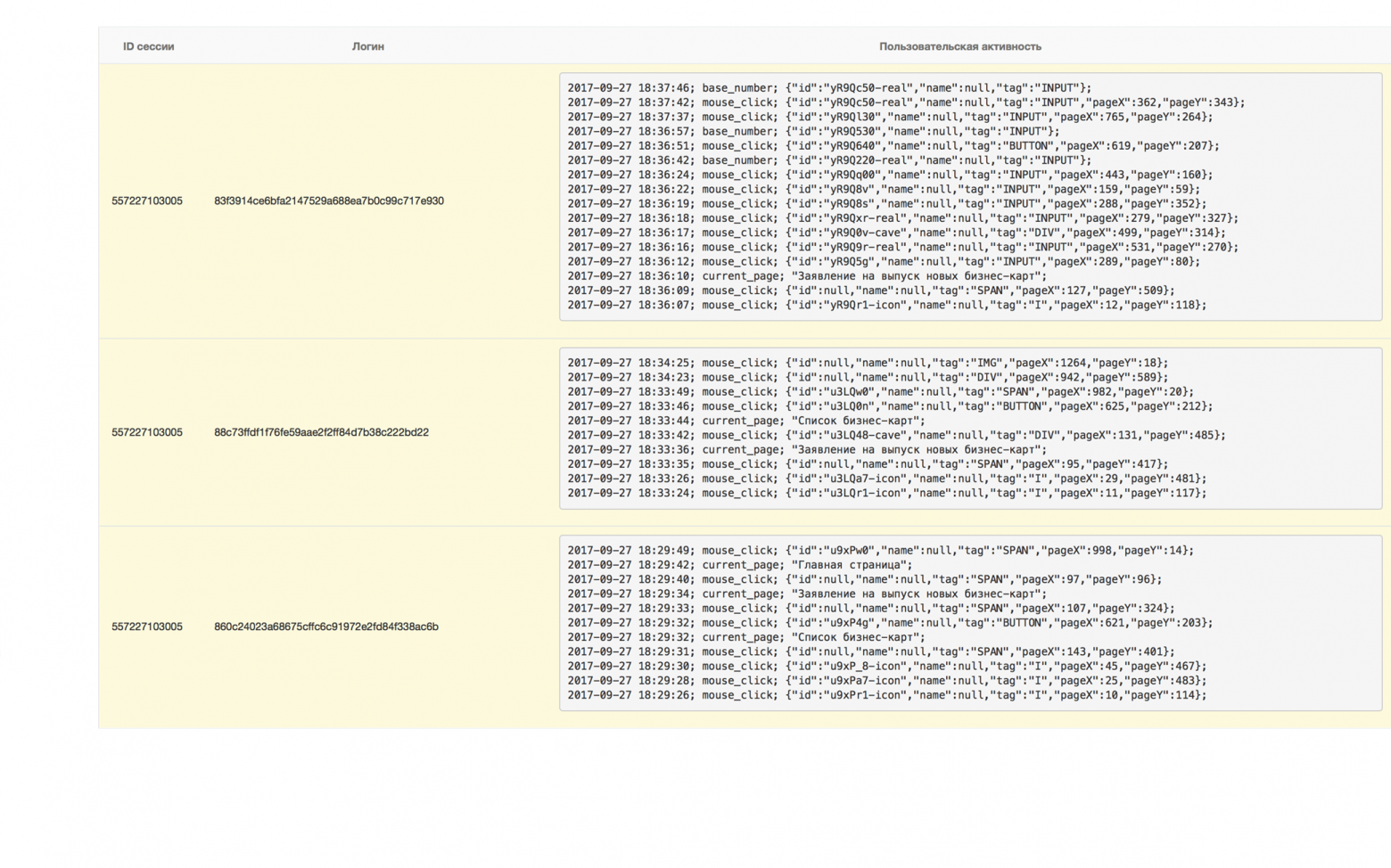
Rice. 6. Preparation for the implementation of a fraudulent scheme: entry of more than 100 legal entities with a request to issue a bank card.
So, in Fig. 6 on the right shows an example when more than a hundred legal entity accounts were logged in from one device, whose only activity was a request to issue a bank card and expand its limit. As was later confirmed, this was the method used to prepare a database of cards for money laundering. The problem of bots can also be attributed to the second level. If the customer does not have any bot protection system installed, then, as a rule, very primitive bots (access directly to the API) perform all the necessary actions (brutforce, password-check), bypassing the bank’s web application. But there are also smarter bots used by scammers to bypass anti-bot protection.
Such bots imitate the user's work. Botnets are often used for this. That is, the work of bots turns out to be distributed, and not concentrated in any specific hosting. Such bots are identified by the scenarios of their work on websites and the nature of their actions. This brings us smoothly to the third level.
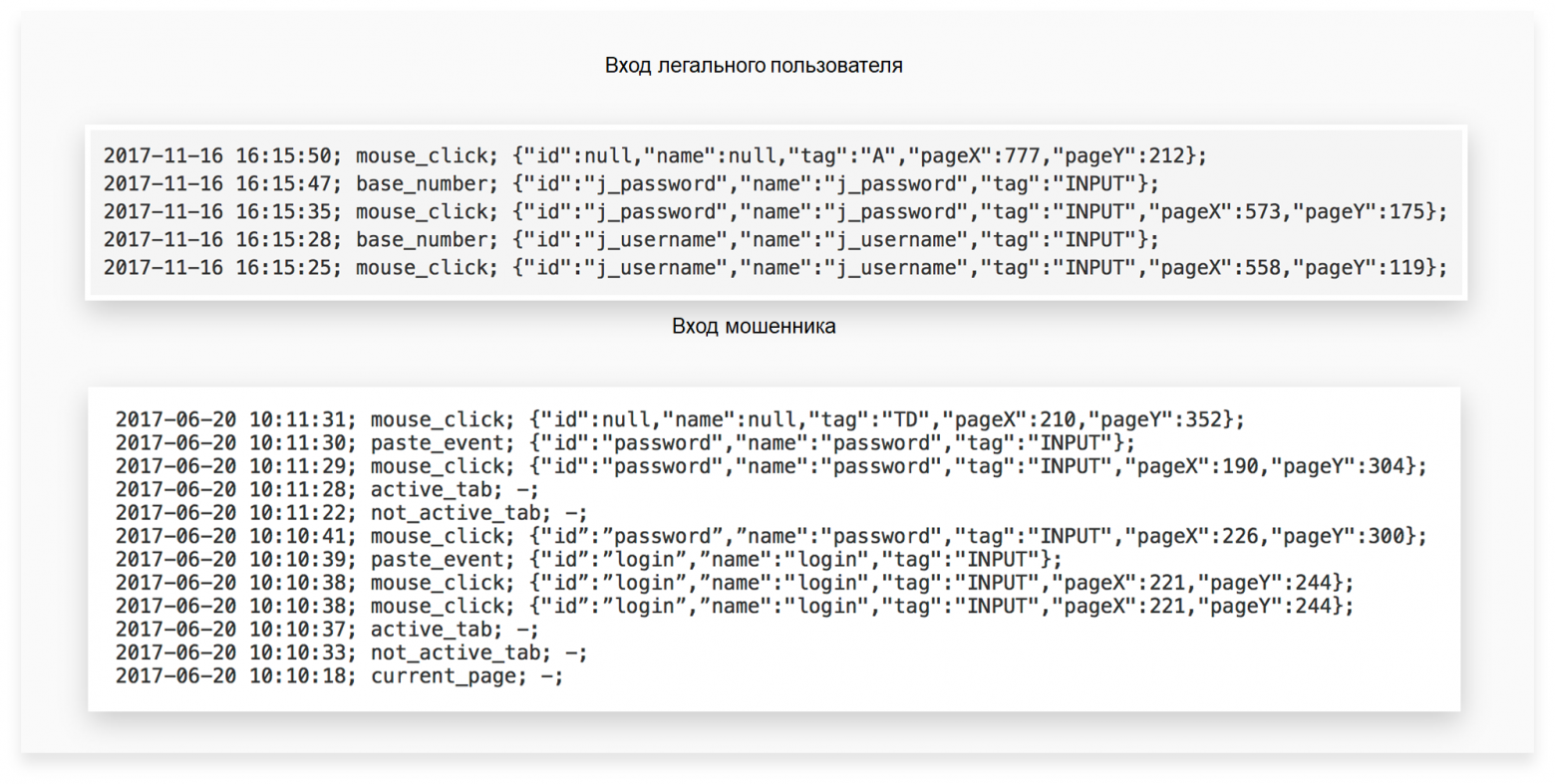
Fig.7. Comparison of work in the system of a legal user and a fraudster: identifying uncharacteristic and suspicious actions.
The sequence of actions of a legal user is visible in the upper part of the figure. That is, he goes to the page to access the RBS system, uses the upper numeric keypad to enter his login and password, then presses “Login.” The lower part of the figure shows a typical example of the work of a fraudster who has somehow collected logins and passwords, for example, using fake (phishing) sites or using a Trojan. He has a whole database of them. Naturally, the fraudster does not retype the data he received, but copies it from the clipboard when entering the RBS. And this is clearly visible in the screenshot.
In addition to this, all the techniques for analyzing the device and user behavior described in the previous levels are used. At this level, machine learning algorithms are actively used. One of the striking examples is the use of biometric technologies such as keyboard and cursor handwriting, which take into account the behavioral nature and habits of the user in the system. In Fig. Figure 8 shows a scenario for using keyboard handwriting on the user authorization page, “captured” from the Group-IB Secure Bank system.
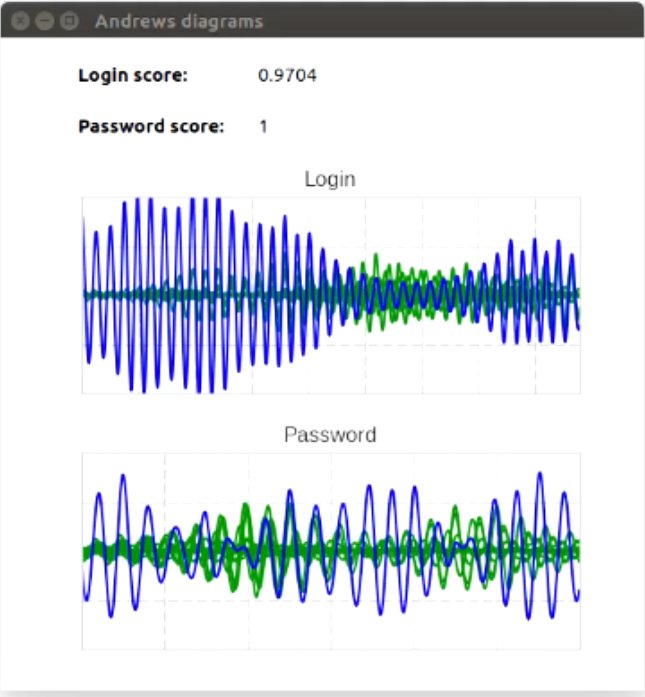
Fig.8. Scenario for using keyboard handwriting on the user login page.
On the graph, the accumulated handwriting of a legitimate user when entering a login and password is highlighted along the axis. More noticeable fluctuations characterize the scammer's keyboard handwriting. It can be seen that the keyboard handwritings are different. Above the graphs are two integral estimates of the differences between them. The rating values exceed the established thresholds, which indicates behavior that is atypical for a legitimate user.
The combination of these behavioral analysis technologies makes it possible to detect fraud committed using social engineering. These technologies also make it possible to reduce the number of false positives of transactional anti-fraud systems. For example, with an accuracy of 91%, it was possible to discard 78% of false positives of the transactional anti-fraud system in cases of social engineering, which significantly frees up the bank’s internal resources, including the mass of calls from irritated clients.
We will demonstrate how effective this is in one of the real cases, the graphical connections for which are shown in Fig. 9.
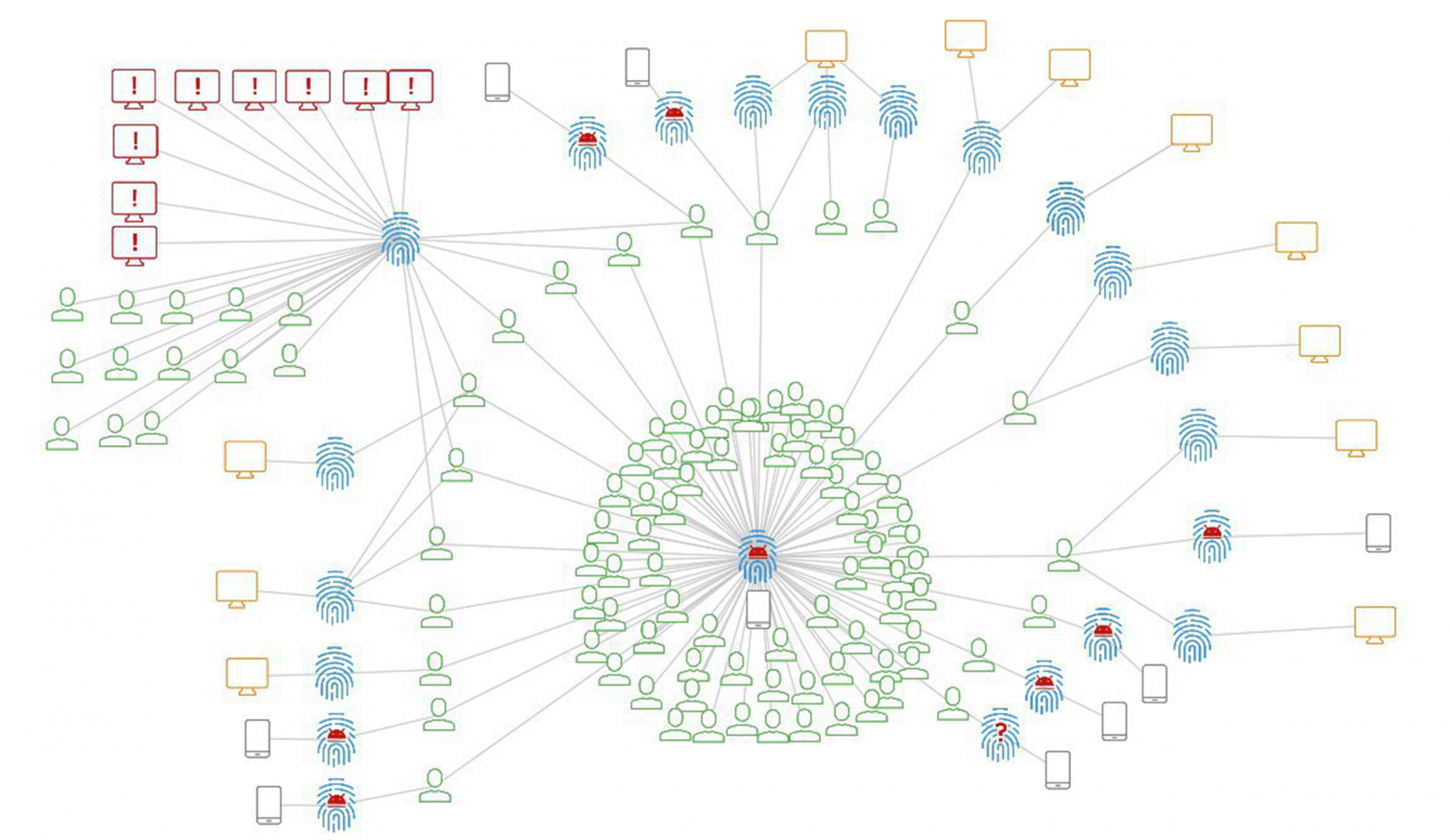
Fig. 9. Graphic links showing the user’s work with various devices, including the scammer’s device.
The scammer was initially detected on a mobile device. He used a mobile Trojan to collect logins and passwords, payment card details and intercept SMS confirmations from the bank to make unauthorized payments. Analysis of the connections between the accounts and the devices they use revealed the fraudster's mobile device, which is depicted in the center and bottom of the picture in the account cloud. As you can see, only a portion of the compromised accounts were previously working through the mobile application. Another significant portion of the identified accounts were previously used in online banking. Later it turned out that the same fraudster used social engineering methods to compromise them. The fraudster’s device, which he used to access the victims’ online bank, was also identified. Their group stands out in the upper left part of the picture.
The scammer erased the browser history after using 3 to 8 accounts in succession, trying to cover up his tracks. But all devices had the same digital fingerprint (remember level 1). It was through this scammer’s device that other victims were identified. Moreover, through this analysis of connections, a case surfaced in which a fraudster, using social engineering methods, “conned” the victim into receiving an express loan with the subsequent theft of the issued loan funds.
Using this example, the following conclusions can be drawn:
That is why, if there are currently very few banking Trojans for desktop computers or iOS, or they are even absent, it is necessary to log and correlate the work of users through these channels, since this allows an order of magnitude wider visibility into the overall picture of the work of users and, as a result, increases the effectiveness of combating fraud .
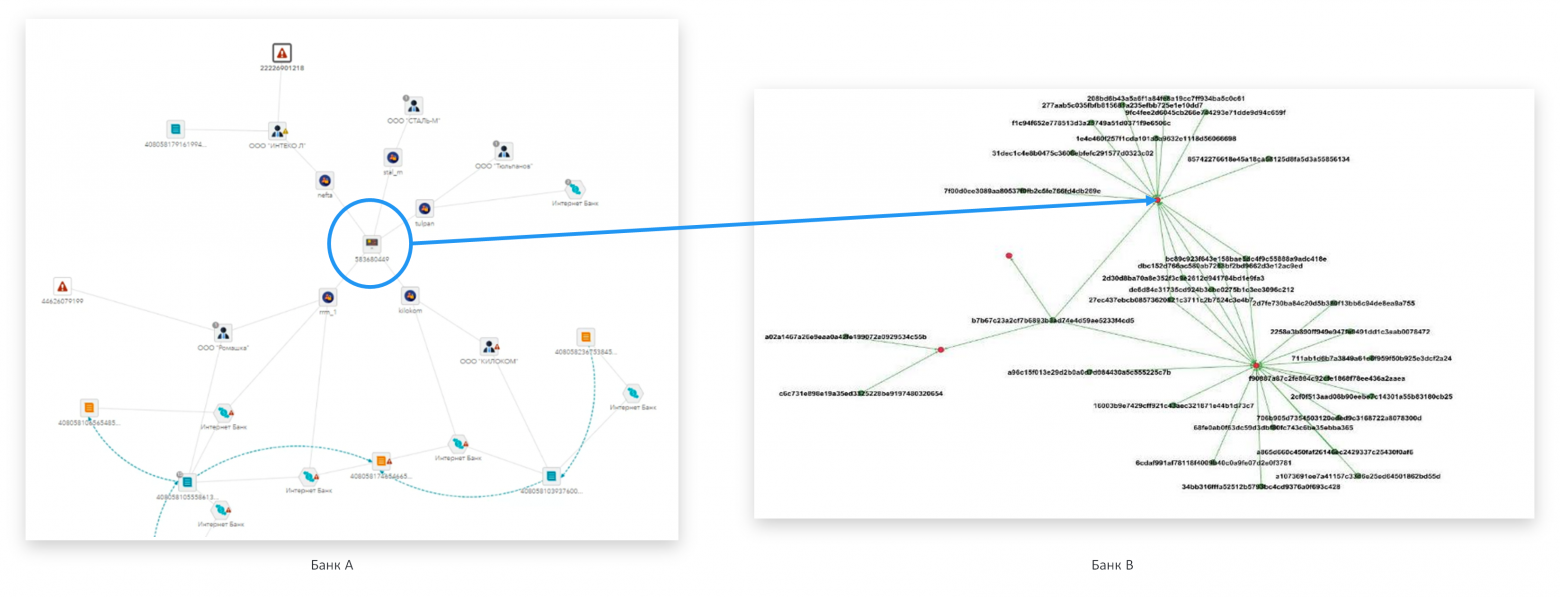
Rice. 10. Example of fraudulent activities in Bank A: the entire pool of accounts and devices can be analyzed in other banks (Bank B)
For example, the same fraudsters are engaged in money laundering. Although they change the legal entities they manipulate, they operate from the same arsenal of computers and other equipment. If fraudulent activity was detected in one bank (in Fig. 10 Bank A), then the entire pool of accounts and devices can be analyzed in other banks (in Fig. 10 Bank B). This analysis, in turn, can identify new accounts, new registration data of legal entities, their other devices and then be reused among banks, revealing more and more details with each iteration and the complete structure of the fraudsters’ work. Note that the described synergistic effect also works in relation to other schemes and types of fraud.
This level also includes technologies and platforms of cyber intelligence (Threat Intelligence), which allow one to obtain both strategic knowledge about what the fraudster is preparing for, and
tactical data about what he has already done in relation to certain users. In the latter case, if the organization's defense systems missed the identified incidents, this makes it possible not only to take proactive action regarding already compromised data, but also to configure its defense systems to respond to the new threat.
The material was published in the journal “Calculations and operational work in a commercial bank”, No. 3 (145)\ 2018.
Analyzing the “digital traces” of the thefts, Group-IB specialists found that the banking Trojan used in the criminal scheme was disguised as the financial application “Banks in the Palm of Your Hand,” which acts as an “aggregator” of the mobile banking systems of the country’s leading banks. You could load all your bank cards into the application so as not to carry them with you, but at the same time be able to view card balances based on incoming SMS for all transactions, transfer money from card to card, pay for online services and purchases in online stores .
Interested in the capabilities of the financial aggregator, bank clients downloaded the “Banking in the Palm of Your Hand” application and entered their card details. The launched Trojan sent bank card data or logins/passwords for logging into Internet banking to the server to the attackers. After this, the criminals transferred money to pre-prepared bank accounts in amounts ranging from 12,000 to 30,000 rubles. for one transfer by entering an SMS transaction confirmation code intercepted from the victim’s phone. The users themselves did not suspect that they had become victims of cybercriminals - all SMS confirmations of transactions were blocked.
Text: Pavel Krylov, head of product development for the Secure Bank Group-IB line
At the moment, the “market” of banking Android Trojans is the most dynamic and fastest growing. According to the Group-IB report for 2017, damage from malware under the Android OS in Russia increased by 136% compared to the previous reporting period - it amounted to $13.7 million. This figure covers the damage from Trojans for personal computers by 30%.
Basic theft schemes through remote banking: why antiviruses do not work
Group-IB forensic experts identify seven common theft schemes that are used by cybercriminals in attacks on remote banking systems:
1) social engineering;
2) transfers from card to card;
3) transfers through online banking;
4) interception of access to mobile banking;
5) fake mobile banking;
6) purchases using Apple Pay and Google Pay;
7) theft through SMS banking.
Conventional anti-virus protection tools are practically useless against such theft schemes. For example, in the case of the use of social engineering, when a client who fell for the bait believed the scammer and independently transferred money to his account (i.e., the person himself was “hacked”), or when the victim’s details are lured out from a third-party device, antiviruses do not help.
The last layer of defense is antifraud. Most anti-fraud systems are focused on analyzing transactional information or data sent directly to the bank’s servers (client’s IP address, information about his browser, the pace of work in a web or mobile application, etc.). If we take into account that fraud as such is a process that includes not only the moment of the transaction, but also the stages of preparing and
withdrawing funds, it becomes obvious that transactional anti-fraud systems “cover” only a limited range of work of fraudsters.
Gartner analysts identify five levels of fraud prevention. We will analyze each of them in detail and with examples:
1) analysis of the user’s device (infected devices, device identification);
2) monitoring of user actions at the session level (anomalies in the user’s work: navigation, time, geography);
3) behavioral analysis of the user in a specific channel (what actions are performed in the channel? how (behavior)? who performs them?);
4) cross-channel analysis of users and their behavior (analysis of user behavior in different channels, data correlation);
5) analysis of the relationships between users and accounts (behavior on different resources, global client profile).
First level: analyzing the user’s device
This level of fraud prevention includes all endpoint protection technologies for the client’s device, such as antiviruses, tokens for generating an electronic signature, two-factor authentication tools, additional means of device identification, etc. This level also includes biometric means of identification by voice, fingerprint or face.One of the striking examples of attacks on remote banking systems was the activity of the Lurk group, which at the end of its “career” in 2016 reached quite impressive proportions: about 50 people worked for it. Having started its journey with autofill for desktop versions of RBS (“thick” client), at the end of 2014 it implemented this method of theft for Internet banks (“thin” clients that do not require installation on the user’s PC), which significantly expanded the scope activities of the group. The client generated a payment using only the recipient's details, but this payment was received by the bank with the details changed by the Trojan program. Many experts still recognize this type of attack as the most dangerous, since it allows the client’s behavior and data to be manipulated at the most subtle level directly from the client’s device. How did this happen?
The Trojan was embedded directly into the client’s browser and made changes to its code directly in memory, which made it possible, when the client visited the bank’s official website, to intercept and modify the original HTML pages in a manner necessary for the fraudster, even when using an HTTPS connection.
In Fig. Figure 1 shows an example of a malicious injection that was added by a Trojan to the page code. The lines highlighted in gray are the URLs through which this script interacted with the fraudster’s command and control servers, where logins/passwords, balances and other information were sent, and in response the fraudster’s payment details were sent for substitution in the client’s original payment.

Rice. 1 A script embedded by a Trojan on the original Internet banking page in the client’s browser.
A less sophisticated, but effective way to steal funds is to remotely control the client’s device (Fig. 2). After automated collection using a keylogger program (literally “key interceptor”) of all necessary logins/passwords, PINs from tokens, etc. The fraudster connects to the client's device via remote control (Fig. 3) and creates a fraudulent payment directly from the client's device and on his behalf.

Rice. 2. Example of a computer interface infected with the Ranbayas Trojan

Fig. 3. Implementing a VNC remote control program in Explorer
So what are the first level fraud prevention technologies? First of all, those that allow you to effectively detect remote control when working in remote banking systems using several independent methods. However, they do not require installation of additional software on the client’s device.
Also included in the category of technologies at the first level are systems and solutions that identify the device and the user. This allows you to collect and analyze information about the devices used by a specific client (on the left in Fig. 4 is a fragment of the graph of connections between accounts and the devices they use). For example, the appearance of an unknown device in a client previously known to us is an important factor for making a decision to suspend payment and carry out additional control procedures.

Fig.4. Graphic connections between accounts
In Fig. 4 on the right shows another example of identifying a device for proactively identifying legal entities intended for money laundering. In this example, bank employees identified, using financial analysis, a company that was engaged in money laundering (bottom of the graph on the right). Additionally, using the identifier of a legal entity, you can obtain the identifiers of the devices that were used by it (the center of the right column). And then - all other accounts that were used from the same devices (upper part of the right column) and from which the identified launderer worked. This fits very well with the nature of the work of scammers. The fraudster always has companies in stock that have not yet been used for money laundering. The bank should pay greater attention to the transactions of identified legal entities.
Second level: we monitor user actions
At this level, it is analyzed what a person does directly within the framework of a work session in a remote banking system or another system. At this level, we can identify abnormal user behavior or typical scammer operating scenarios. In particular, such analysis already makes it possible to increase the effectiveness of detecting fraud using social engineering (that is, when a fraudster uses the user’s gullibility, carelessness or ignorance to lure information from him or force him to take actions that are beneficial to the fraudster).For example, a common case is the deception of card details and SMS codes in the process of purchasing an expensive product through popular ad sites under the pretext of making a deposit. In fact, the fraudster uses this data to go through the registration procedure in the remote banking system and gain access to the victim’s accounts. A real example of such a scenario is shown in Fig. 5.

Fig. 5. Going through the procedure of registering a fraudster in RBS and gaining access to the victim’s accounts.
Analysis of the sequence of steps performed by the user in RBS allows us to identify the scenario described above. This process takes into account the results of the first level technologies (analysis of the user’s device): what device was used, whether it is typical for a given client, whether the geography has changed; the session time is taken into account and, additionally, the script used by the scammer.
This also applies to other scammers’ schemes. For example, a similar method is used to identify some of the work scenarios of launderers. It is clear that not all cases of money laundering can be tracked using behavioral characteristics alone. For example, if a company is engaged in transit, then only one analysis of behavior - what a person does in Internet banking - will not be enough to understand whether it is a transit payment or a standard one. But most cases still make it clear that something anomalous is happening and, most likely, this activity is fraudulent.

Rice. 6. Preparation for the implementation of a fraudulent scheme: entry of more than 100 legal entities with a request to issue a bank card.
So, in Fig. 6 on the right shows an example when more than a hundred legal entity accounts were logged in from one device, whose only activity was a request to issue a bank card and expand its limit. As was later confirmed, this was the method used to prepare a database of cards for money laundering. The problem of bots can also be attributed to the second level. If the customer does not have any bot protection system installed, then, as a rule, very primitive bots (access directly to the API) perform all the necessary actions (brutforce, password-check), bypassing the bank’s web application. But there are also smarter bots used by scammers to bypass anti-bot protection.
Such bots imitate the user's work. Botnets are often used for this. That is, the work of bots turns out to be distributed, and not concentrated in any specific hosting. Such bots are identified by the scenarios of their work on websites and the nature of their actions. This brings us smoothly to the third level.
Third level: analyze user behavior in a specific channel
If at the second level we analyze what the user does in the system, then at the third level we additionally analyze how the user performs certain actions. Let's show this using a real example (Fig. 7).
Fig.7. Comparison of work in the system of a legal user and a fraudster: identifying uncharacteristic and suspicious actions.
The sequence of actions of a legal user is visible in the upper part of the figure. That is, he goes to the page to access the RBS system, uses the upper numeric keypad to enter his login and password, then presses “Login.” The lower part of the figure shows a typical example of the work of a fraudster who has somehow collected logins and passwords, for example, using fake (phishing) sites or using a Trojan. He has a whole database of them. Naturally, the fraudster does not retype the data he received, but copies it from the clipboard when entering the RBS. And this is clearly visible in the screenshot.
In addition to this, all the techniques for analyzing the device and user behavior described in the previous levels are used. At this level, machine learning algorithms are actively used. One of the striking examples is the use of biometric technologies such as keyboard and cursor handwriting, which take into account the behavioral nature and habits of the user in the system. In Fig. Figure 8 shows a scenario for using keyboard handwriting on the user authorization page, “captured” from the Group-IB Secure Bank system.

Fig.8. Scenario for using keyboard handwriting on the user login page.
On the graph, the accumulated handwriting of a legitimate user when entering a login and password is highlighted along the axis. More noticeable fluctuations characterize the scammer's keyboard handwriting. It can be seen that the keyboard handwritings are different. Above the graphs are two integral estimates of the differences between them. The rating values exceed the established thresholds, which indicates behavior that is atypical for a legitimate user.
The combination of these behavioral analysis technologies makes it possible to detect fraud committed using social engineering. These technologies also make it possible to reduce the number of false positives of transactional anti-fraud systems. For example, with an accuracy of 91%, it was possible to discard 78% of false positives of the transactional anti-fraud system in cases of social engineering, which significantly frees up the bank’s internal resources, including the mass of calls from irritated clients.
Fourth level: we implement cross-channel analysis of users and their behavior
At the fourth level, technologies are used to analyze and correlate data on user behavior on his devices when working through various channels of interaction with the bank.We will demonstrate how effective this is in one of the real cases, the graphical connections for which are shown in Fig. 9.

Fig. 9. Graphic links showing the user’s work with various devices, including the scammer’s device.
The scammer was initially detected on a mobile device. He used a mobile Trojan to collect logins and passwords, payment card details and intercept SMS confirmations from the bank to make unauthorized payments. Analysis of the connections between the accounts and the devices they use revealed the fraudster's mobile device, which is depicted in the center and bottom of the picture in the account cloud. As you can see, only a portion of the compromised accounts were previously working through the mobile application. Another significant portion of the identified accounts were previously used in online banking. Later it turned out that the same fraudster used social engineering methods to compromise them. The fraudster’s device, which he used to access the victims’ online bank, was also identified. Their group stands out in the upper left part of the picture.
The scammer erased the browser history after using 3 to 8 accounts in succession, trying to cover up his tracks. But all devices had the same digital fingerprint (remember level 1). It was through this scammer’s device that other victims were identified. Moreover, through this analysis of connections, a case surfaced in which a fraudster, using social engineering methods, “conned” the victim into receiving an express loan with the subsequent theft of the issued loan funds.
Using this example, the following conclusions can be drawn:
- firstly, cross-channel analysis of theft attempts using mobile Trojans made it possible to identify and prevent theft attempts that are in no way related to malicious code, but are committed using social engineering;
- secondly, it also helped to build a complete picture of the fraudster’s work and prevent theft from the entire client base, regardless of the remote banking channel;
- thirdly, we received more data for further investigation.
That is why, if there are currently very few banking Trojans for desktop computers or iOS, or they are even absent, it is necessary to log and correlate the work of users through these channels, since this allows an order of magnitude wider visibility into the overall picture of the work of users and, as a result, increases the effectiveness of combating fraud .
Fifth level: analyzing the relationship between the user and accounts
The fifth level is a continuation of the fourth level, that is, the analysis of data on the behavior of the user and his devices is carried out not only within one specific bank, but more broadly - between banks, e-commerce, offline transactions, etc. This is the most complex, but at the same time the most powerful level of anti-fraud, since it allows not only to stop the same type of actions of fraudsters in different organizations, but also to prevent the general chain of actions of the fraudster, which he carries out through different organizations.
Rice. 10. Example of fraudulent activities in Bank A: the entire pool of accounts and devices can be analyzed in other banks (Bank B)
For example, the same fraudsters are engaged in money laundering. Although they change the legal entities they manipulate, they operate from the same arsenal of computers and other equipment. If fraudulent activity was detected in one bank (in Fig. 10 Bank A), then the entire pool of accounts and devices can be analyzed in other banks (in Fig. 10 Bank B). This analysis, in turn, can identify new accounts, new registration data of legal entities, their other devices and then be reused among banks, revealing more and more details with each iteration and the complete structure of the fraudsters’ work. Note that the described synergistic effect also works in relation to other schemes and types of fraud.
This level also includes technologies and platforms of cyber intelligence (Threat Intelligence), which allow one to obtain both strategic knowledge about what the fraudster is preparing for, and
tactical data about what he has already done in relation to certain users. In the latter case, if the organization's defense systems missed the identified incidents, this makes it possible not only to take proactive action regarding already compromised data, but also to configure its defense systems to respond to the new threat.
In conclusion, we add that each level of protection flows smoothly from one another. Thanks to this, by applying all five levels of cybercrime prevention in the field of remote banking, banks will receive the most effective protection from external and internal malicious influences.
The material was published in the journal “Calculations and operational work in a commercial bank”, No. 3 (145)\ 2018.
