Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,036
- Points
- 113

Positive Technologies experts studied banking mobile applications and found that more than half of all vulnerabilities are found in the server parts of applications, and fraudulent operations and theft of funds are possible in every second mobile bank.
For the study, 14 fully functional banking mobile applications for Android and iOS were selected, downloaded from the official Google Play and App Store at least 500,000 times, the creators and owners of which did not object to testing and the use of its results for research purposes.
The researchers report that none of the tested mobile banking applications have an acceptable level of security. Both client and server parts of banking applications are under threat.
For the client side of applications, the main threat is posed by possible access to user data, because 43% of applications store important data on a mobile device in clear text. At the same time, 76% of vulnerabilities can be exploited without physical access to the device, and more than a third of vulnerabilities do not require administrative rights.
According to experts, all the shortcomings identified in mobile banks for iOS were no higher than the average risk level. While 29% of Android apps contained high-risk vulnerabilities. The most dangerous vulnerabilities have been identified in Android applications and are related to insecure processing of deeplinks. Android application developers are given more options to implement different functionality. Experts see this as the main reason for the greater number of vulnerabilities in Android applications compared to iOS applications.
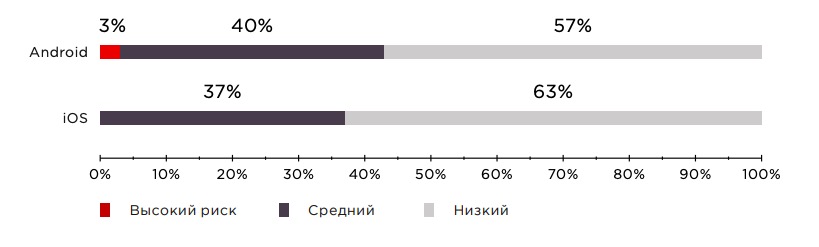
Percentage of vulnerabilities of different risk levels
The analysis showed that 54% of all vulnerabilities are contained in the server parts of a mobile bank, and the server part of each mobile bank contains, on average, 23 vulnerabilities. However, three out of seven application server parts contain business logic errors. This is functionality that can be used by attackers to perform fraudulent transactions or obtain confidential user data. Errors in business logic can bring significant financial losses to the bank and even lead to litigation, experts say.
In every second mobile bank, fraudulent transactions are possible. Authentication data turned out to be the most vulnerable in mobile banking applications.
“Unauthorized access to an application is usually caused by a lack of authentication or authorization,” says Olga Zinenko, an analyst at Positive Technologies. “Our research has shown that mobile banking user accounts are available to cybercriminals on five out of seven server parts. Among the information available to the offender: names and surnames of users, the value of the balance of funds, receipts for transfers, bank card limits, as well as the ability to establish a relationship between a payment card and a mobile phone number. "
Positive Technologies experts advise banks to pay more attention to security issues both at the design stage of mobile applications and at the development stage. Due to the large number of shortcomings in the source code, it is worth revising the development approaches: the solution may be to implement secure development processes and control the application's security at all stages of its life cycle.
It should also be borne in mind that in order to exploit 87% of vulnerabilities, an attacker needs some kind of user action. Experts strongly recommend that users do not elevate privileges in the OS to administrative ones, install applications only from official stores, do not visit suspicious sites and do not follow links from instant messengers or SMS, and also update the OS and mobile software in a timely manner.
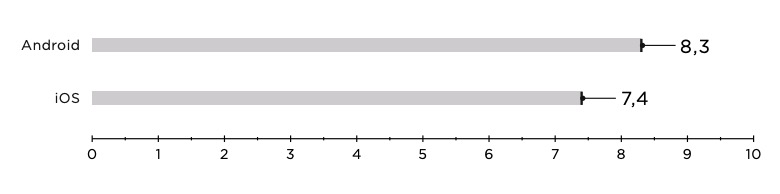
Average number of vulnerabilities per application
(c) xakep.ru

