Lord777
Professional
- Messages
- 2,577
- Reaction score
- 1,556
- Points
- 113
Hackers are trying their best to gain access to e-commerce services to expand the range of their attacks.
Foreign online merchants are being targeted in a new campaign to distribute Vidar malware, which allows attackers to steal credentials to carry out more destructive attacks in the future.
Last week, researchers detected a new malicious campaign in which cyberbandists send complaints to administrators of online stores via email and through the website's contact forms. The emails were allegedly written by customers of online stores who were charged a certain amount from their bank account after the intended order did not go through properly.
According to foreign experts, over the past week, many different organizations have encountered such fraudulent emails.
Online sellers are an attractive target for attackers, since obtaining their credentials gives hackers access to the backend of e-commerce sites, which in the future will significantly expand the range of possible attacks. For example, as soon as cybercriminals gain access to the back-end of an online store, they can implement malicious JavaScript scripts to steal bank card data and personal information of customers right during checkout (the so-called MageCart attacks).
Internal access can also be used to steal information about site customers by creating backups of the store's database. This information can also be used for extortionate purposes.
Below is an example of one of the variants of malicious emails distributed as part of a malicious campaign:
"I am writing to express my deep concern and disappointment over a recent transaction I made on your website. On May 14, 2023, I placed a request in your store to purchase goods worth more than $ 550. However, there is a significant problem that requires your immediate attention. Immediately after I completed the purchase,I found an error message on your web page stating that the payment could not be made and that my bank card simply had not been withdrawn. To my surprise, after checking my bank account, I found that the payment was indeed made and an identical amount was withdrawn. I urge you to address this issue with the utmost urgency and resolve it quickly. It is important that you analyze the reason for this discrepancy and take immediate action to refund the deducted amount of money. For your reference and as proof of purchase, I have provided a copy of my bank statement below, which obviously shows the charge. This should serve as final proof of payment and emphasize the urgency of a full refund. I sincerely appreciate your immediate action. Here is a hyperlink to my statement: bit[.]ly/xxxx"
The text of the email itself is written in such a way as to give a sense of urgency, requiring the seller to immediately return the money and investigate the root cause of the problem. This is classic social engineering.
As you can see, hackers used the service to shorten URLs in order to hide the real link and not arouse suspicion in the victim. Clicking on the link loads a website that pretends to be Google Drive, but is not really Google Drive.
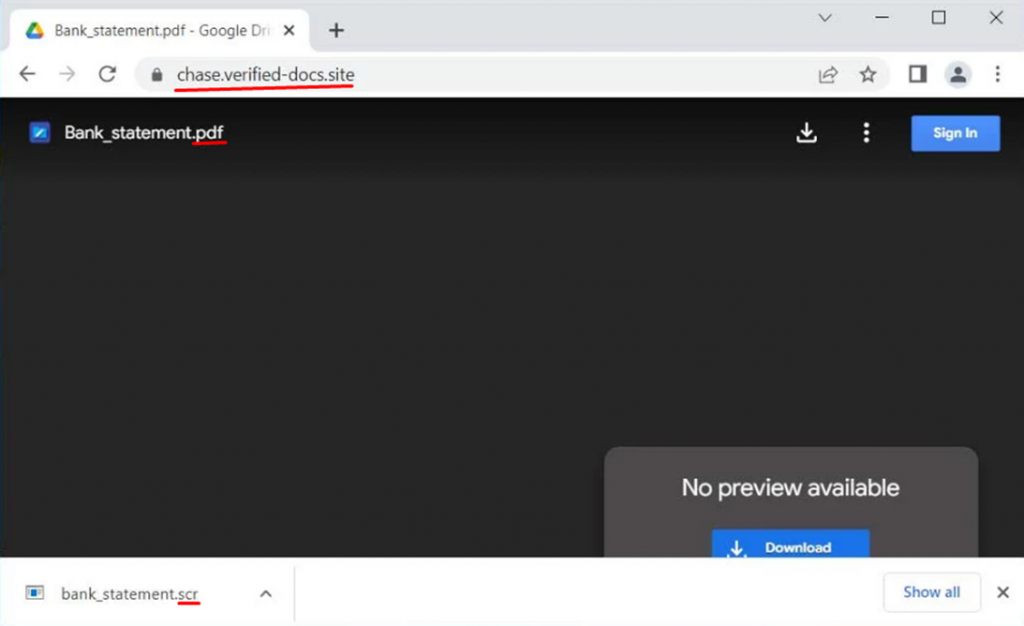
Fake Google Drive site
The site informs the victim that a preview of the document is not available and suggests downloading the bank statement to the computer. The file displayed on the fake site as "Bank_statement. pdf" when actually downloaded is called "bank_statement. scr". In other words, it is an executable script file that loads the Vidar infostiler.
Vidar is an information theft Trojan that can steal session cookies, browser history, saved passwords, cryptocurrency wallet data, text files, Authy 2FA databases, and Windows screen screenshots.
Once cybercriminals receive the stolen information, they either sell it to other attackers or use it on their own to break into the accounts of affected users.
Potential victims of the described malware campaign are advised to scan their computer for malware, change the password for all their accounts, especially those used for work purposes, and also examine their e-commerce site for introducing malicious code into HTML templates, creating new accounts with elevated privileges, or making any changes to the site's source code..
Earlier, we reported on similar malware campaigns aimed at hacking sites on PrestaShopCMS and WooCommerce . And at the beginning of the year, we wrote about hackers who introduced malicious code that steals customer data on the Canadian alcohol production site LCBO.
Foreign online merchants are being targeted in a new campaign to distribute Vidar malware, which allows attackers to steal credentials to carry out more destructive attacks in the future.
Last week, researchers detected a new malicious campaign in which cyberbandists send complaints to administrators of online stores via email and through the website's contact forms. The emails were allegedly written by customers of online stores who were charged a certain amount from their bank account after the intended order did not go through properly.
According to foreign experts, over the past week, many different organizations have encountered such fraudulent emails.
Online sellers are an attractive target for attackers, since obtaining their credentials gives hackers access to the backend of e-commerce sites, which in the future will significantly expand the range of possible attacks. For example, as soon as cybercriminals gain access to the back-end of an online store, they can implement malicious JavaScript scripts to steal bank card data and personal information of customers right during checkout (the so-called MageCart attacks).
Internal access can also be used to steal information about site customers by creating backups of the store's database. This information can also be used for extortionate purposes.
Below is an example of one of the variants of malicious emails distributed as part of a malicious campaign:
"I am writing to express my deep concern and disappointment over a recent transaction I made on your website. On May 14, 2023, I placed a request in your store to purchase goods worth more than $ 550. However, there is a significant problem that requires your immediate attention. Immediately after I completed the purchase,I found an error message on your web page stating that the payment could not be made and that my bank card simply had not been withdrawn. To my surprise, after checking my bank account, I found that the payment was indeed made and an identical amount was withdrawn. I urge you to address this issue with the utmost urgency and resolve it quickly. It is important that you analyze the reason for this discrepancy and take immediate action to refund the deducted amount of money. For your reference and as proof of purchase, I have provided a copy of my bank statement below, which obviously shows the charge. This should serve as final proof of payment and emphasize the urgency of a full refund. I sincerely appreciate your immediate action. Here is a hyperlink to my statement: bit[.]ly/xxxx"
The text of the email itself is written in such a way as to give a sense of urgency, requiring the seller to immediately return the money and investigate the root cause of the problem. This is classic social engineering.
As you can see, hackers used the service to shorten URLs in order to hide the real link and not arouse suspicion in the victim. Clicking on the link loads a website that pretends to be Google Drive, but is not really Google Drive.

Fake Google Drive site
The site informs the victim that a preview of the document is not available and suggests downloading the bank statement to the computer. The file displayed on the fake site as "Bank_statement. pdf" when actually downloaded is called "bank_statement. scr". In other words, it is an executable script file that loads the Vidar infostiler.
Vidar is an information theft Trojan that can steal session cookies, browser history, saved passwords, cryptocurrency wallet data, text files, Authy 2FA databases, and Windows screen screenshots.
Once cybercriminals receive the stolen information, they either sell it to other attackers or use it on their own to break into the accounts of affected users.
Potential victims of the described malware campaign are advised to scan their computer for malware, change the password for all their accounts, especially those used for work purposes, and also examine their e-commerce site for introducing malicious code into HTML templates, creating new accounts with elevated privileges, or making any changes to the site's source code..
Earlier, we reported on similar malware campaigns aimed at hacking sites on PrestaShopCMS and WooCommerce . And at the beginning of the year, we wrote about hackers who introduced malicious code that steals customer data on the Canadian alcohol production site LCBO.

