Father
Professional
- Messages
- 2,602
- Reaction score
- 830
- Points
- 113
Hi, this is Father! In foreign films, it is customary to form stereotypical images of hackers, monitors with green codes, a man in a hood. Because of them, a person has a picture of a "carder" in his head, inspired by watching movies. Today I will tell you a couple of secrets that filmmakers don't know about.
Read the article.
Introduction
I've spent half my life on the darknet and I know this cuisine from the inside out, so it's funny to watch how everything related to hacking appears in pop culture and how it is described. So I decided to write this article for you, don't be deceived.
Operating systems in movies
In all movies, there is some absolutely stupid OS, every time you press a key or mouse button, incomprehensible sounds are heard all over the place. The interface is as flawed as possible.
A separate topic for discussion is search engines, I don't understand why films with multi-million dollar budgets can't use ordinary Google in the frame. Their signature search engines look pathetic, as if they were written on computers of the 90s.
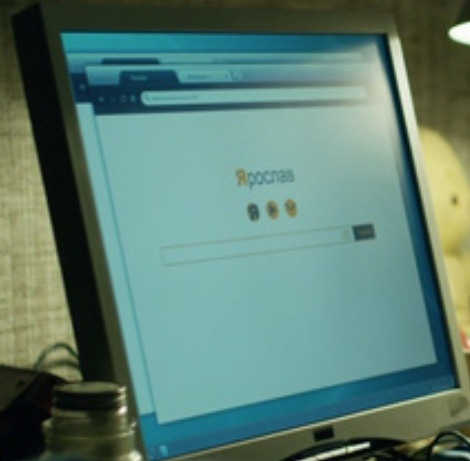
Yaroslav? Are you serious now?)
And what do you think, in the movies, the hacker of course drives the victim's name into a search engine like "Yaroslav", and miraculously" punches " it on the first link. All your data, phone number, address, passport scan, and credit history - just enter your first and last name.
In real life, the procedure is slightly different. I described it in one of my previous articles. You need to spend a lot more effort on this or even work in the authorities, although no one has canceled the purchase of a breakdown.
Perhaps the films show little close to reality hacking methods, using the same SE. So that people have less awareness and interest in this issue.

Carder
From a carder to a movie, they make a clown. They put on a mask of anonymity, or put a finished actor-villain who behaves like a retard, randomly clicking on the keyboard. A black jacket with a hood, a dark room in a closet or somewhere in the basement. Really Hollywood?
Let me tell you a secret, everyone can be a carder. Drysch from the next entrance or cute jock wearing a nice suit. A hacker cannot be identified by their appearance or various habits.
Comparing hackers and carders
As an example, I'll show you a couple of photos to roughly understand the image of a hacker in general, and how it can look in real life.
This guy hacked Twitter:

And this is a clown from Hollywood:

A good movie about hackers and carders
TV series Mr. Robot-mastwatch. Mr. Robot offers the most accurate description of hacking and carding, because he recognizes that humans are often the weakest link in a security system.
Phishing emails, impersonating employees, or other manipulations of social engineering and expectations are often more successful than technical efforts, and given the significant success rate of phishing attacks, it is not surprising that they are used so often.
Result
Of course, there are also excellent works that touch on the topic of hacking. But for the most part, this is selected slag that has nothing to do with hacking. Again, I advise you to watch the TV series Mr. Robot, it directly describes the possible image of a carder as accurately as possible (as it can be) and the approximate technique of performing cybercrimes. In the series, you won't see a lot of codes, because in real life there aren't as many of them as you think, a lot of things are built on social engineering.
Read the article.
Introduction
I've spent half my life on the darknet and I know this cuisine from the inside out, so it's funny to watch how everything related to hacking appears in pop culture and how it is described. So I decided to write this article for you, don't be deceived.
Operating systems in movies
In all movies, there is some absolutely stupid OS, every time you press a key or mouse button, incomprehensible sounds are heard all over the place. The interface is as flawed as possible.
A separate topic for discussion is search engines, I don't understand why films with multi-million dollar budgets can't use ordinary Google in the frame. Their signature search engines look pathetic, as if they were written on computers of the 90s.

Yaroslav? Are you serious now?)
And what do you think, in the movies, the hacker of course drives the victim's name into a search engine like "Yaroslav", and miraculously" punches " it on the first link. All your data, phone number, address, passport scan, and credit history - just enter your first and last name.
In real life, the procedure is slightly different. I described it in one of my previous articles. You need to spend a lot more effort on this or even work in the authorities, although no one has canceled the purchase of a breakdown.
Hacking and carding
Hacking is most often portrayed as a crazy action, with fast music to raise the tension, while various codes and commands flash on the screen, and behind it all is a mad programmer whose fingers are herachat on the keyboard at the speed of light.Perhaps the films show little close to reality hacking methods, using the same SE. So that people have less awareness and interest in this issue.

Carder
From a carder to a movie, they make a clown. They put on a mask of anonymity, or put a finished actor-villain who behaves like a retard, randomly clicking on the keyboard. A black jacket with a hood, a dark room in a closet or somewhere in the basement. Really Hollywood?
Let me tell you a secret, everyone can be a carder. Drysch from the next entrance or cute jock wearing a nice suit. A hacker cannot be identified by their appearance or various habits.

Comparing hackers and carders
As an example, I'll show you a couple of photos to roughly understand the image of a hacker in general, and how it can look in real life.
This guy hacked Twitter:

And this is a clown from Hollywood:

A good movie about hackers and carders
TV series Mr. Robot-mastwatch. Mr. Robot offers the most accurate description of hacking and carding, because he recognizes that humans are often the weakest link in a security system.
Phishing emails, impersonating employees, or other manipulations of social engineering and expectations are often more successful than technical efforts, and given the significant success rate of phishing attacks, it is not surprising that they are used so often.
Result
Of course, there are also excellent works that touch on the topic of hacking. But for the most part, this is selected slag that has nothing to do with hacking. Again, I advise you to watch the TV series Mr. Robot, it directly describes the possible image of a carder as accurately as possible (as it can be) and the approximate technique of performing cybercrimes. In the series, you won't see a lot of codes, because in real life there aren't as many of them as you think, a lot of things are built on social engineering.
