BadB
Professional
- Messages
- 1,981
- Reaction score
- 2,022
- Points
- 113

Today we are waiting for a truly interesting and urgent task, or rather, a whole investigation from the series "where did the big money go": we will consider a case with a corporate laptop on Windows 10, which became a victim of an attack by cyber fraudsters. Or maybe the employees of the company simply embezzled the money, referring to "evil hackers"? We'll find out soon. Forward, in search of truth!
Background to the incident
So, before us is a laptop with Windows 10 installed on board, which was included in the corporate domain and was used as the employee's main work machine. In addition, he could be taken on a business trip, to work at home and outside the main office (that is, in the presence of a VPN or other connections to the corporate perimeter).By default, the user did not have local administrator rights, domain security policies were forced (password policy, BitLocker volume encryption, built-in firewall enabled, UAC enabled), AV of one of the well-known Russian vendors was installed, and Internet access was provided without restrictions. The computer belonged to the treasurer, one of the main tasks of which was the preparation and execution of financial payment documents (transactions in the RBS).
The organization that owned the laptop revealed unauthorized payments in the RBS of one of the connected banks, and all operations were performed on behalf of legitimate users (financial director and chief accountant). Round sums of money were transferred to unknown accounts of third parties in foreign banks. The organization's security systems did not register any suspicious activity at that time (IDS / IPS systems and SEIM connector connected to ERP modules, AV and WAF were silent).
It is believed that the attackers hacked into the laptop remotely over the network or with gaining physical access to it, or it was a collusion of authorized persons and fraud related to insiders. We will deal with all this today.
WARNING:
Always clearly and clearly realize what kind of action and for what purpose you are performing. Incorrect use of the programs given in the text of the article can lead to loss of information (artifacts) or distortion of the obtained data (forensic evidence). Neither the author nor the editors are responsible for any damage caused due to misuse of the materials in this article.
Hypotheses
Let's start unraveling this tangle of events. All we have at the very beginning is the information described above, plus the laptop itself, which, after the fraud was discovered, was immediately confiscated from the employee. There are, in principle, only two hypotheses: either it is an internal conspiracy of the organization's employees, who set all events and conditions so that it looks like an external hack, or it is unauthorized access by hackers to a laptop. In the first case, we will focus on finding artifacts and, possibly, an oversight that clearly indicates an employee. In the second, it is the detection of remote hacking artifacts (disabling protection tools, using exploits and malware).It should be said that the laptop has security features that provide a good basic level of security. This suggests that the crackers are above average. However, as noted, the laptop could be taken out of the office and turned on outside the domain, where corporate security measures do not work. Thus, we get the risks of physical access to the system and the ability to dump all data on the hard disk (including saved passwords, keys in the registry, etc.), "reload" the OS and erase the traces of the crime.
Vulnerabilities and search for a hacking scenario
Before we start forensic procedures, here are a few more links to interesting materials that will give you food for thought and may lead you to "possible scenarios" of hacking:- “ Examining and opening BitLocker. How Windows Disk Protection Works and How to Crack It", as well as news about insecure BitLocker.
- " FUCK UAC! 10 Ways to Bypass User Account Control in Windows ", as well as news about the UAC hack.
- “ Black injection. Bypassing antiviruses using Shellter ", as well as bypassing using Veil.
- The ability to hack a remote RDP connection using Pass-in-the-Hash, another option with Metasploit, as well as news about the finished exploit, the fuzzbunch utility and a guide to it.
- Fun guides for creating PowerShell Payload and Metasploit Payload.
- Reports of the domestic researcher - Positive Technology company - on the (safe) dangers of remote banking systems: Cybersecurity 2018, Attacks on Banks, New Attacks on Banks.
Laboratory preparation
Conventionally, all operations for detecting and extracting artifacts left after hacking can be divided into two large types. These are actions with "volatile memory" - processes in RAM, network connections to the outside world, and so on and work with "non-volatile" - these are HDD and removable media, hidden and deleted files, alternative NTFS streams, installed software , patched system libraries other.All forensic procedures can be performed using various software, but we, as a rule, will use two or three versions of the most popular utilities. Many of the presented tools are open source or freely distributed, others are proprietary, but there's nothing you can do about it, professional packages of specialized programs will always cost money.
Some features of forensics in Windows 10
Since the release of Windows Vista, many of the technical aspects of Windows (the system registry, event logging, and others) have changed somewhat. This is why the tutorials described for Windows XP, for example, do not currently work on later releases of Windows. What can we say about the top ten, for which the developers are constantly releasing Update packs.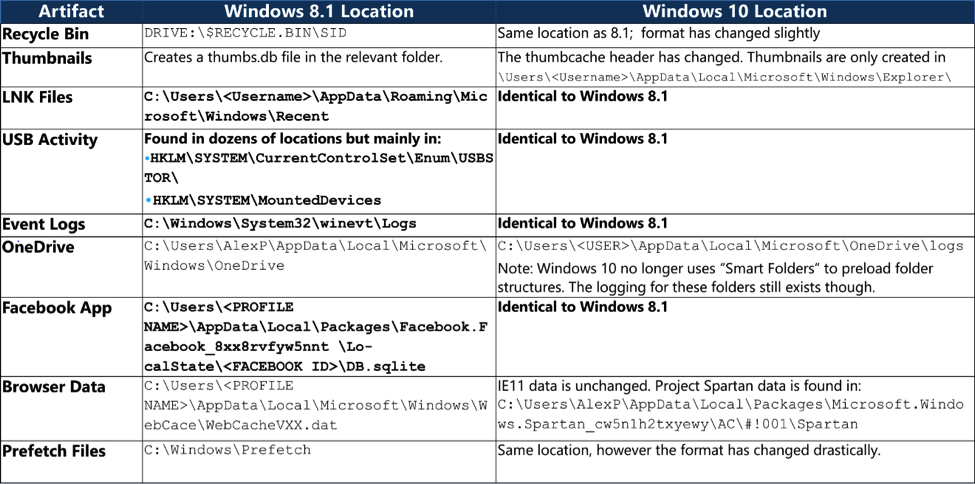
A visual comparison of the changes using the example of Win 10 and Win 8.1
So, compared to all other OS versions, the Top 10 has additional data sources that a forensic expert can use to collect artifacts:
- Edge Browser - the browser that replaced IE;
- Cortana - a voice engine designed to become the new HMI according to Microsoft logic;
- OneDrive - cloud storage, including often used for small backups of personal files and as an application story for mobile devices based on Android;
- Native Applications (Skype, Photo App, Webcam App) - out of the box applications available immediately after system installation;
- Notification - system notifications from the tray, where you can often find information about programs running in standby mode, antivirus software, stopping the firewall, and more;
- Prefetch files - so to speak, cached files for quick launch, this feature is inherent not only in the top ten, but it can also be partially used to get additional bits of information.
General checklist
To search and collect forensic evidence, we will check the following main points on our system:- RAM (system and user processes, injected DLLs, extraneous services and running malicious code);
- hard drive (remote ports, marked disk areas, erased files, shadow copies, "leftovers" from the trash can, LNK and Notification shortcuts, installed software, downloaded files, and so on);
- network stack (raised connections, open ports, "unknown" services on ports, parasitic traffic from our machine);
- system registry (installed and remote software, temporary shortcuts, file associations, etc.);
- system logs (recording events such as logon, escalation of rights, access to directories, changing group policy, creating / deleting an account, crashing and rebooting);
- swap and hibernation files (some of the data in these files is successfully saved unchanged);
- application data (Skype, OneDrive, Xbox), mail and browsers (browsing history, bookmarks, downloaded files, maybe passes).
Capturing an HDD image of a compromised system
First of all, be sure to take a dump of the entire contents of the hard drive of our laptop. Firstly, it will save you from jambs and accidental damage (and, accordingly, the loss of some priceless artifacts), secondly, it will serve as a standard of the state of the system at the time of receiving the equipment for examination, and thirdly , it will allow you to get an image ready for in-depth research, but does not require physical access to the device. In our first article, we have already given examples of software that will help us cope with this task. Today we will be using The Forensic Toolkit Imager (FTK Imager).The program can be downloaded from the official website or found, for example, in specialized distributions DEFT or CAINE (Computer Aided Investigative Environment). For more information on taking an image and other available utilities for this, you can read the document SANS Forensic Images: For Your Viewing Pleasure. And for those who are very tight with English, there is a step-by-step guide with pictures, where everything will be clear for sure.
Let's consider several options for working with the tool. The first (CLI) and second (GUI) options on a working system with the host OS booting. The third option is a safer way to create an HDD image on a turned off machine, but more on that later.
Let's start with the first one. We gut the laptop, take out the HDD from it, then connect it to our laboratory computer and, launching FTK Imager in the console mode, write the commands.
Our disk that we will copy
In the CLI interface of the program, we write:
E: \> ftkimager.exe <HARD DRIVE THAT YOU WANT TO IMAGE> e: \ <Destination path of output file with name NOT extension> --e01 --frag 2G --compress 9 --verify
In our case, it looks like this:
E: \> ftkimager.exe \\. \ PhysicalDrive0 e: \ IMAGE_FORENSIC \ filename --e01 --frag 2G --compress 9 --verify
If everything is correct, then in the end we should get this picture.
FTK Imager CLI window during HDD image creation
GUI lovers will have to move more.
In order to create a disk image, go to the File → Create disk image menu item.
Start creating an HDD image in the GUI version of the FTK Imager utility
Next, select the item "Physical disk".
Selecting a data source for imaging
If there is more than one disk in the system, then select the system one.
Selecting the system drive as the source of the imaging
Do not forget to check the "verification" box after creating the image.
Start menu to start creating an HDD image
The menu for selecting the available formats for saving the disk image of our laptop. For compatibility with other software, select the default option - E01.
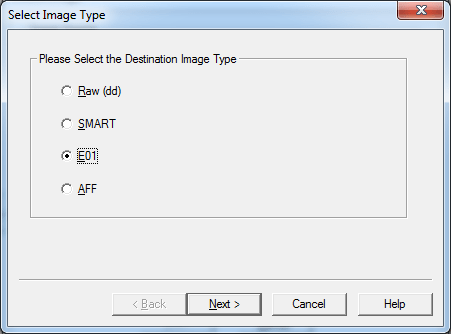
Selecting the type of format in which the HDD image will be saved
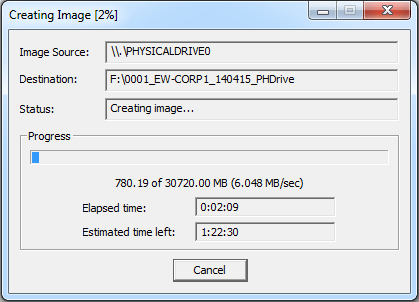
Disk image creation process window
And finally, the third option is to obtain an image without booting the host OS by taking a dump in Live CD mode. This is the safest and preferred way, since we do not need to interfere with the existing system configuration (get admin rights, fill up the system log with unnecessary information), and, more importantly, it will not allow us to destroy any artifact left after hacking. For example, if malware was used, it can, by timer or other event, cover up the traces of its presence in the system (clear logs,% TEMP% -directories, delete its executable file), which can significantly change the picture of what is happening.
For these purposes, we use a special Linux distribution kit CAINE. All actions will be performed in the terminal. We connect an external HDD to our patient, and at the same time simultaneously boot from a USB flash drive to CAINE. Mount the external HDD (/ dev / sdb1) to a temporary directory:
root @ caine: ~ # mkdir / mnt / target
Next, we create a hash value of the laptop hard drive (/ dev / sda) using the MD5 algorithm:
root @ caine: ~ # md5sum / dev / sda> /mnt/target/HDD_Img_Forensic.md5
Use the dd utility to dump the / dev / sda disk into the / mnt / target directory, specifying the name of the image, for example HDD_Img_Forensic.
root @ caine: ~ # dd if = / dev / sda of = / mnt / target / HDD_Img_Forensic.img conv = sync, noerror bs = 8k
And finally, we carry out verification of the resulting image by the sum of the MD5 hash, thus assuring ourselves that everything went well.
root @ caine: ~ # md5sum /mnt/target/HDD_Img_Forensic.img> /mnt/target/HDD_Img_Forensic.img.md5
And before shutting down, unmount our time point:
root @ caine: ~ # umount / mnt / target /
Create a RAM dump of the laptop under study
After we have created a hard disk dump, we should make a similar one, but already in RAM, since there are a lot of artifacts, especially when it comes to searching for traces of infection or installing the left software on the machine. To do this, we will take two tools - DumpIt from the Comae Memory Toolkit and a similar Belkasoft RAM Capturer. The resulting .mem images can be opened for parsing in Volatility, Rekall, or Belkasoft Evidence Center.We make the first dump using DumpIt.
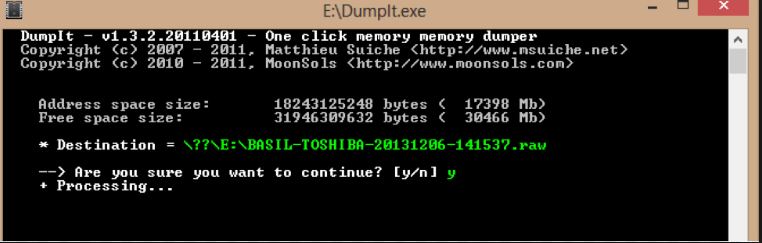
Creating a RAM image in the DumpIt program
We will make the second RAM dump in Belkasoft RAM Capturer.
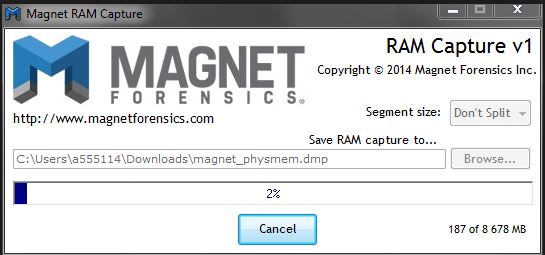
Creating a RAM image in the Belkasoft RAM Capturer program
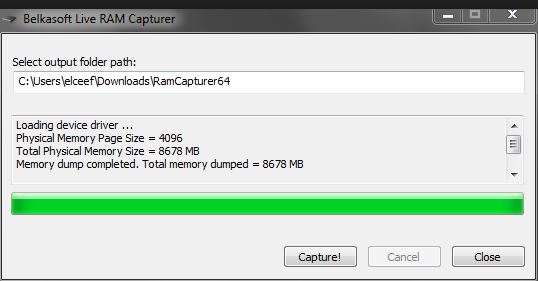
The window of the program for creating a RAM dump in the Belkasoft RAM Capturer program
It's time to open the RAM dump we received in a combine called Belkasoft Evidence Center.
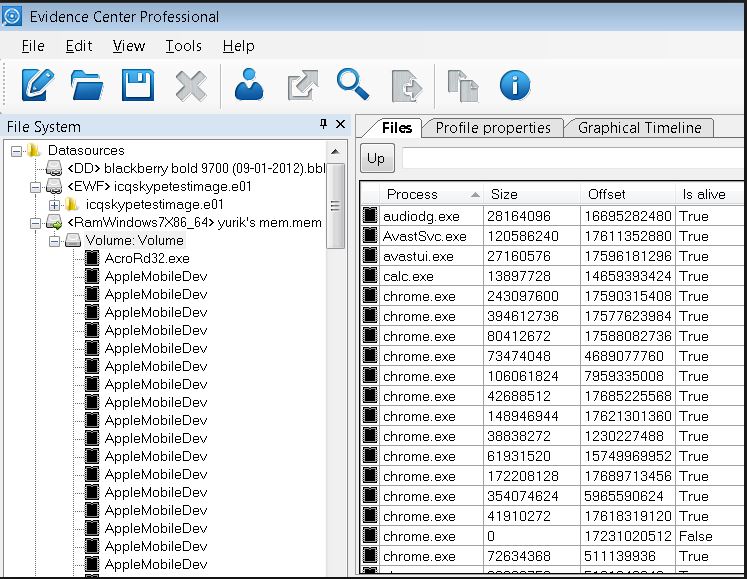
Result of mounting a memory image in Belkasoft Evidence Center
The images of the HDD-disk, obtained at the very first step, can be easily fed to Arsenal Image Mounter.
HDD Image Mount Wizard window in Arsenal Image Mounter
List of ready-to-mount images in Arsenal Image Mounter
Arsenal Image Mounter main window
Search for artifacts
At the very beginning, it would be nice to get some information about the user's profile. We will do this using ForensicUserInfo. The utility extracts system information about RID, account expiration date and password change; LM / NT hash; number of logins, dates of unsuccessful attempts; available groups and the path to the user profile.Let's start with the simplest, namely, look at the list of user and system processes. The fastest way is to run the built-in tasklist utility from CMD:
- c:\>tasklist - displaying a list of all processes in the current window;
- c:\>tasklist /svc - displaying a list of all running services in the system;
- c:\>tasklist > c:\processes_list.txt - output of data about processes (services) to a text file named processes_list.txt.

The result of the tasklist command
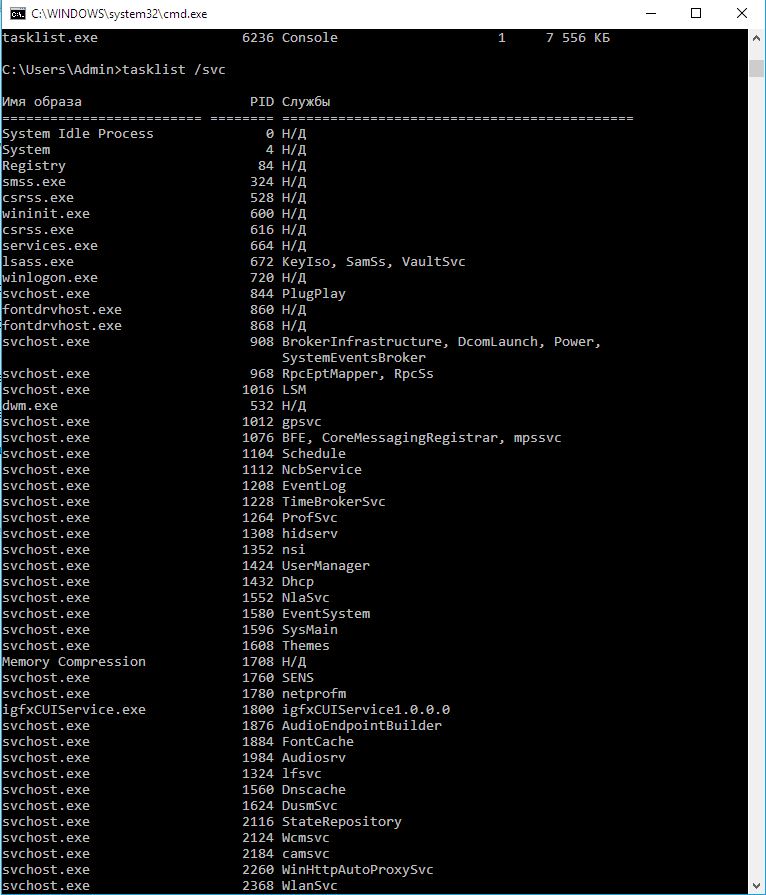
The result of executing the tasklist command with the option to sort by services
Another good option is any alternative Task Manager, for example AnVir Task Manager or Process Explorer.
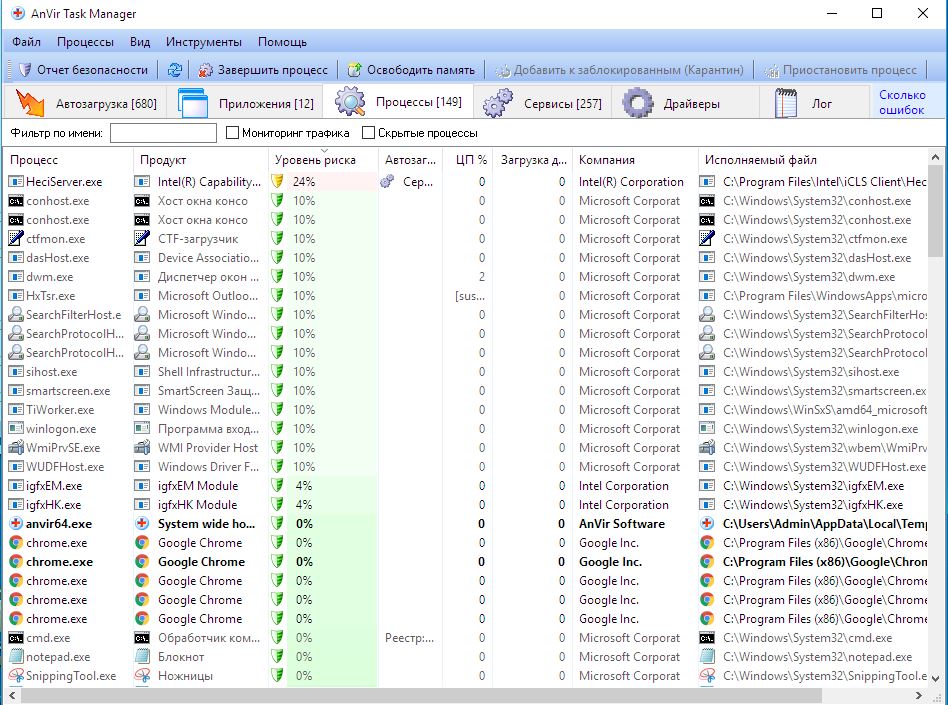
Processes Tab in AnVir Task Manager
Services Tab in AnVir Task Manager
View startup in AnVir Task Manager
And now we will get from the storehouse several utilities specially sharpened for forensics, included in the kit under the general name Sleuth Kit.
To view the available memory information, we type the command mmstat.
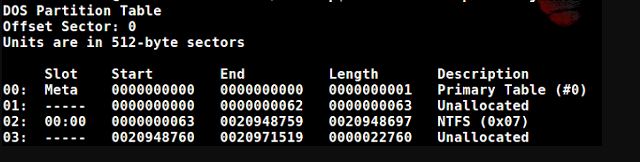
Outputting the results of the mmstat utility
We know the type of the system volume, and after executing the mmls command, it will allow us to view the unallocated areas of the disk:
mmls -t dos X: RAM_Img_Forensic.E01
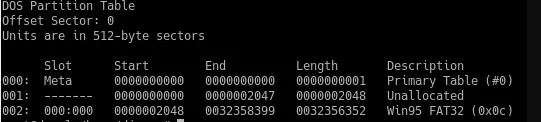
Outputting the results of the mmls utility
Next, we can use the FileName Layer Tools to view deleted files and unallocated segments.
fls -o 1435648 X: RAM_Img_Forensic.E01
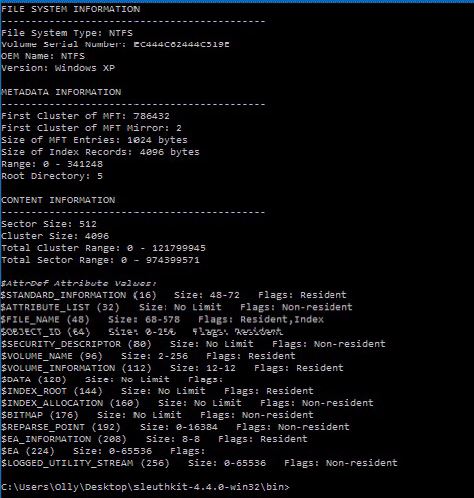
Output of the results of the fls utility
Now what? Let's create a bodyfile - a stub file using the same fls. This will allow us to build timelines of file activity. We write the received data to a file bodyfile.txt.
fls -r -m "/" -o 1435648 X: RAM_Img_Forensic.E01> bodyfile.txt
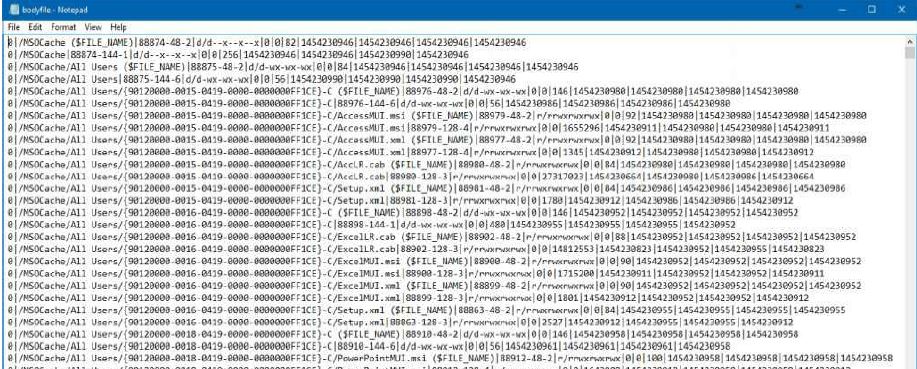
We write the received data using fls to the bodyfile.txt file
After we have created bodyfile.txt, we can use the mactime utility and build a timeline of activity (delete, create, rename) files in the system with export to Excel-like view:
mactime.pl -b bodyfile.txt -d> timeline.csv
Create a timeline diagram using mactime.pl
By the way, here's a little cheat sheet for the utilities used from the Sleuth Kit package:
- mmstat - information about the type of system volumes and the disk partition table;
- mmls - information about occupied space, deleted and allocated files;
- fsstat - file system information, including volume serial number, ID, cluster size, offset from the beginning;
- fls - search for allocated and deleted files in a directory or the entire disk;
- mactime - create a timeline for file system activity from data received from fls.
Autopsy Launch Wizard

Search results for deleted and allocated files in Autopsy
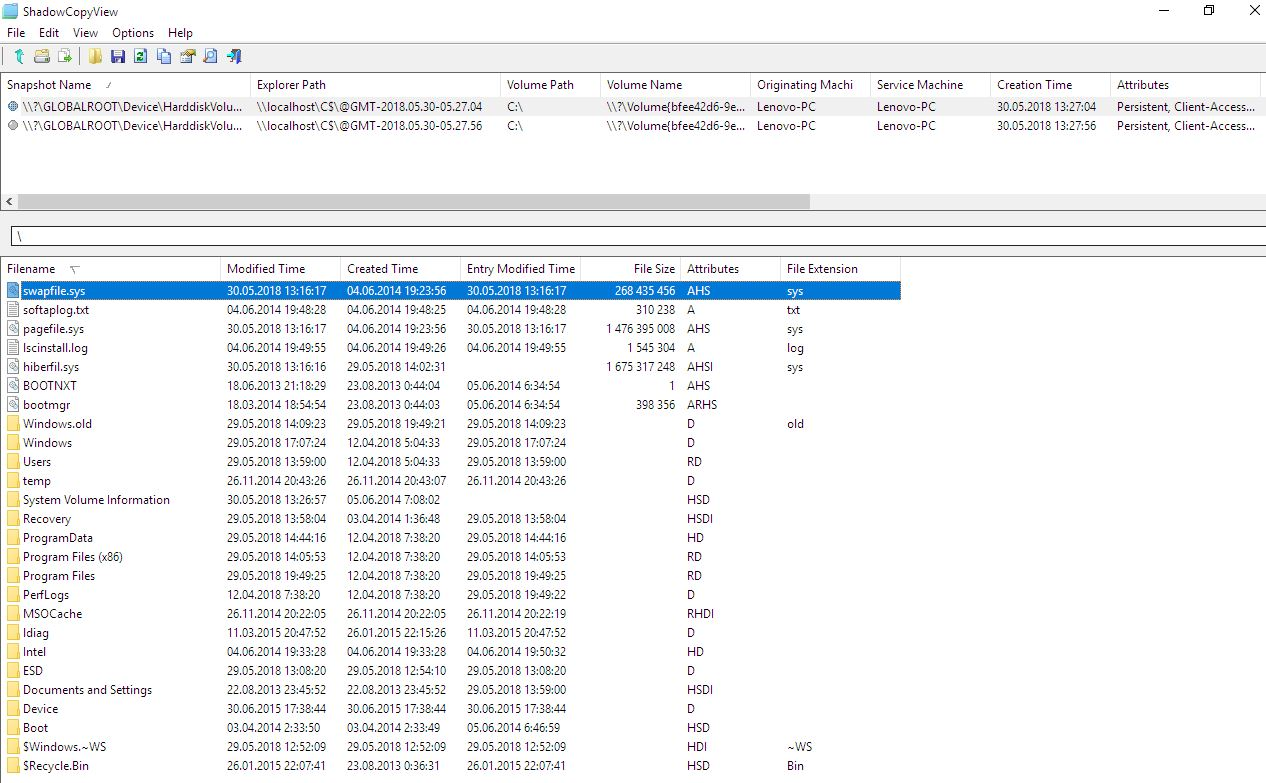
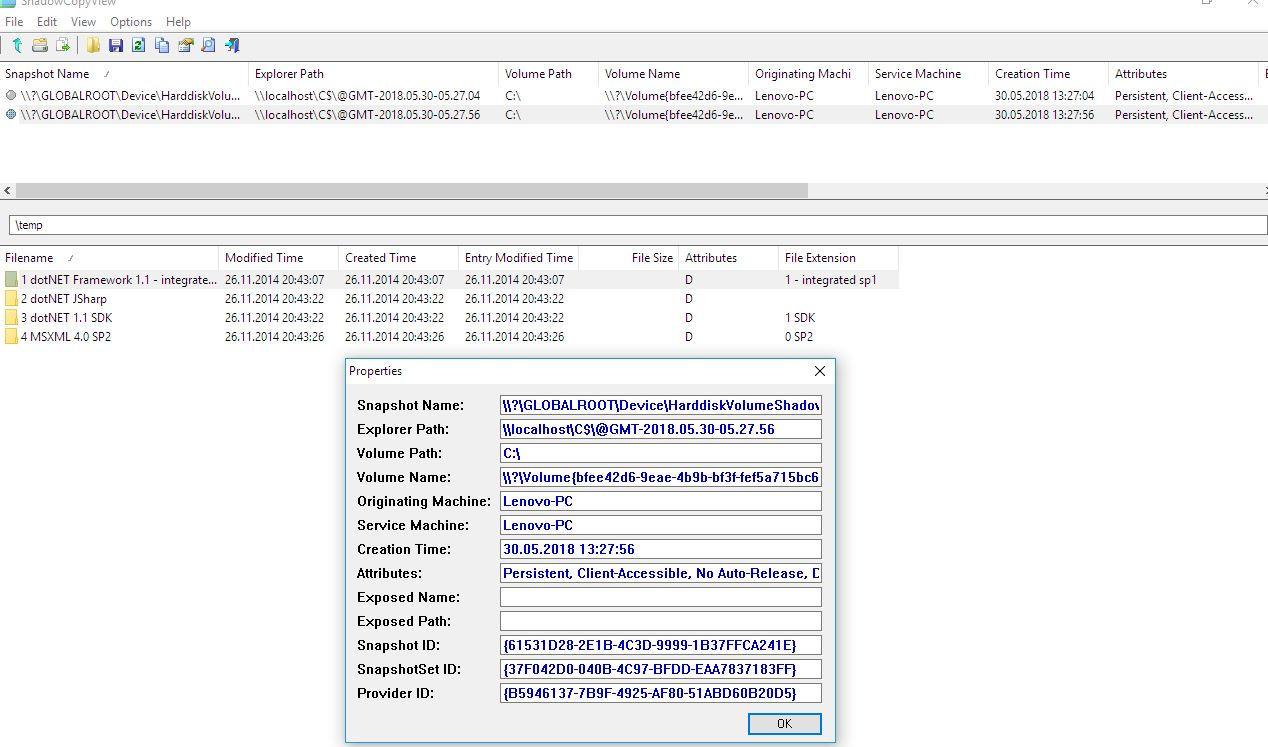
A good option would also go NirSoft'ovskoy utility ShadowCopyView and Poshukayte remains of files that have been preserved in the shadow copies of the Windows.
The next step is to analyze the system registry. Three Windows Registry analysis tools from the Magnet AXIOM package, RegRipper and Registry Explorer will be used.
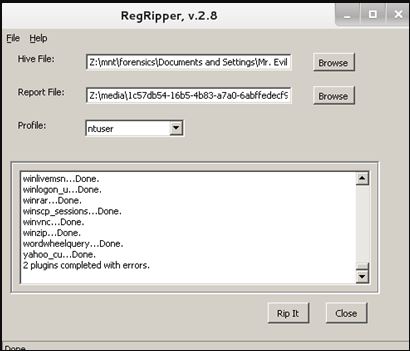
Analysis of the NTUser hive in RegRipper 2.8
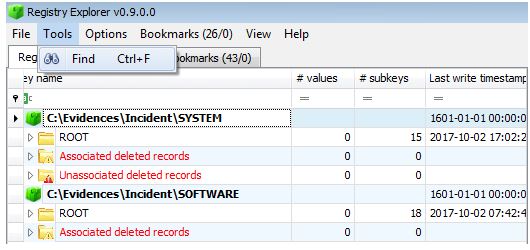
Loading the main registry hive into Registry Explorer
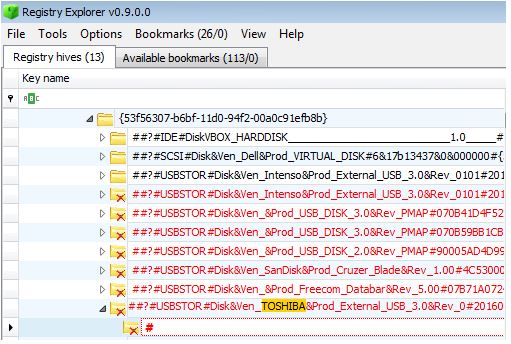
Parsing Registry Key Values Using Registry Explorer
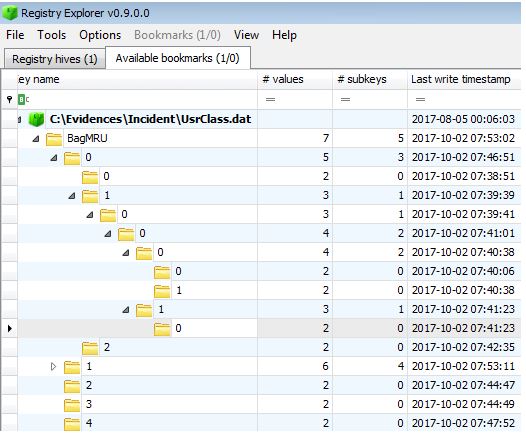
Viewing MRU Values in Registry Explorer
In order to view the remote software, you can pick a file - the NTUSER.DAT database along the path in the system directory:
NTUSER.DAT \ SOFTWARE \ Microsoft \ UserData \ UninstallTimes
And you can also pick up the saved URLs if you were using the good old IE donkey:
NTUSER.DAT \ SOFTWARE \ Microsoft \ InternetExplorer \ TypedURLs
And in the same place, try to get passwords if the user has configured autosaving of the entered data:
NTUSER.DAT \ Software \ Microsoft \ Internet Explorer \ IntelliForms
Explorer's Cheat Sheet: Registry Points of Interest
The list of the most recently used files (Most Recent Used - MRU) is located along the pathHKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Explorer \ RunMRU
Globally unique identifiers (ID), which contain encrypted records of each OS object, application (program), executable exe file that the user accessed on the system, are stored in the branch
HKEY_CURRENT_USER \ Software \ Mcirosoft \ Windows \ CurrentVersion \ Explorer \ UserAssist
The list of IDs and the corresponding software can be found here.
All USB devices that have ever been connected to the computer are also marked in the registry branch
HKEY_LOCAL_MACHINE \ System \ ControlSet00x \ Enum \ USBSTOR
The wireless networks (Wi-Fi SSID) that the computer has ever connected to will be stored in a branch
HKEY_LOCAL_MACHINE \ Software \ microsoft \ WZCSVC \ Parameters \ Interface
For those who want to learn more about the interesting places in the Windows Registry, the article Forensic Analysis Of The Windows Registry is a very good choice.
Network stack
To view network connections in a hurry, you can use the regular netstat shell command:
Code:
netstat -a
Viewing network connections with the netstat command
Among all the output, we are most interested in the following statuses:
- CLOSED - the connection is closed, the socket is not used;
- LISTEN (LISTENING) - waiting for incoming connections;
- ESTABLISHED - connection is established (data is being transmitted).
// List of TCP connections
List of current TCP connections
List of all open incoming ports
A similar output can be viewed in graphical mode using the tiny TCPViewer utility.
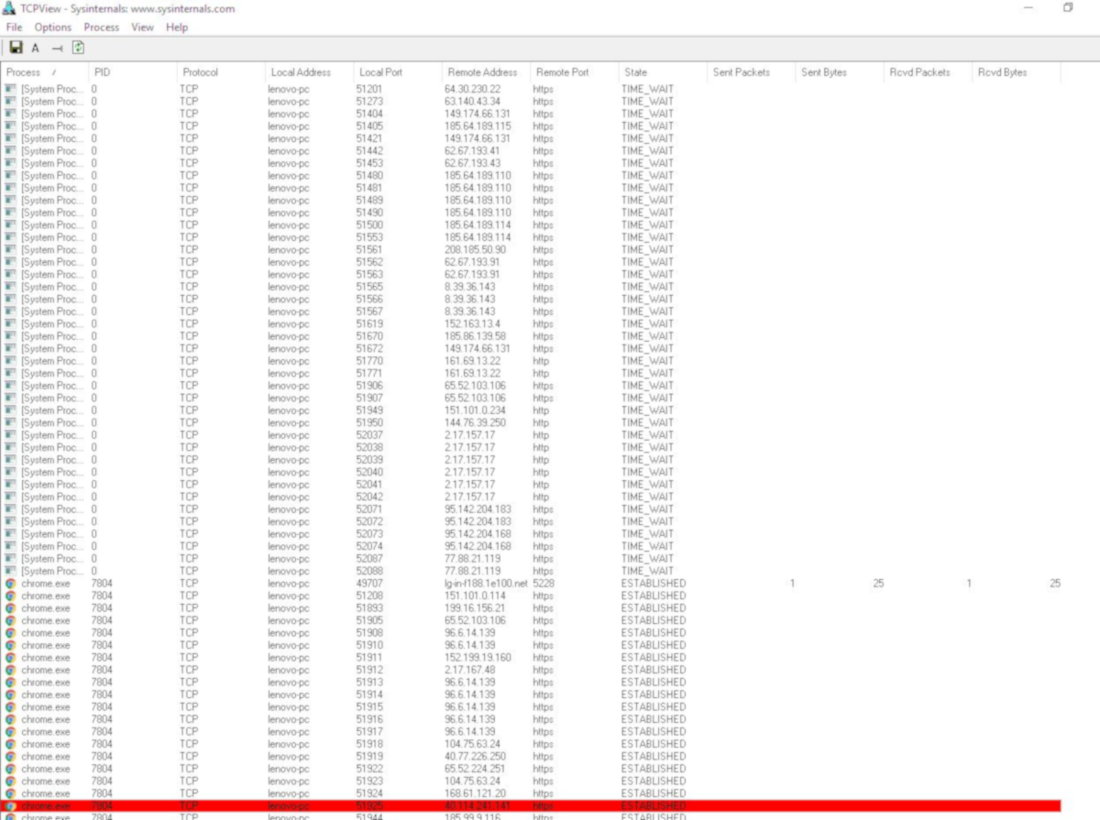
Viewing network connections in TCPViewer
Another special tool is NetworkMiner. In addition to the features that the programs described above have, NetworkMiner has options for extracting files from FTP, TFTP, HTTP, POP3, IMAP protocols, extract X.509 certificates from SSL sessions, GRE decapsulation, 802.1Q, PPPoE, VXLAN, detection geolocation by IP, export of results to CSV, Excel, XML, CASE, JSON-LD.
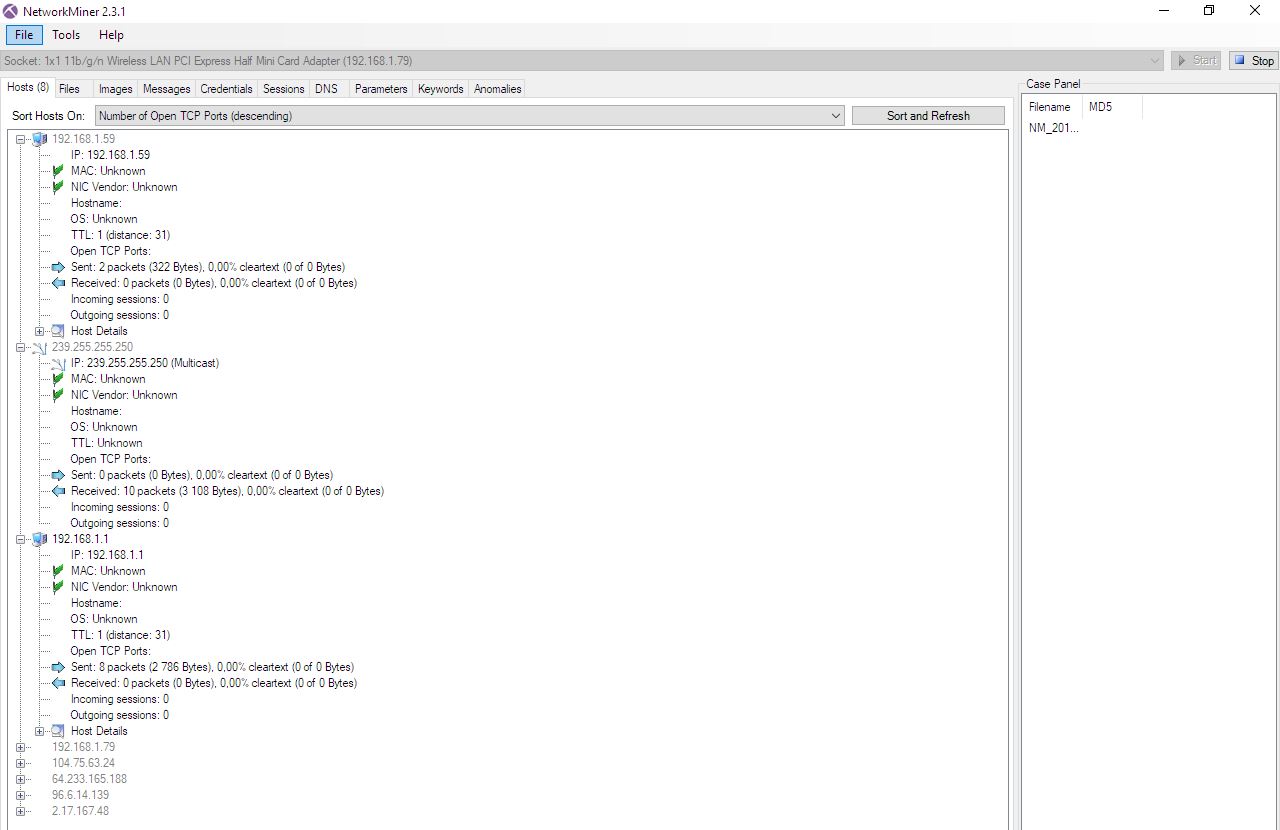
TCP / IP stack data provided by NetworkMiner
Analyzing the Recycle Bin
It's no secret that some of the data that has been in the recycle bin can still be viewed, even if the files have been deleted (in Windows terminology, “the recycle bin is emptied”). We will use a large pack called EnCase Forensic.
EnCase Forensic program interface
So the turn has come to the analysis of logs (system logs). FullEventLogView from the well-known NirSoft development team, as well as Magnet AXIOM for computers will participate in the work.
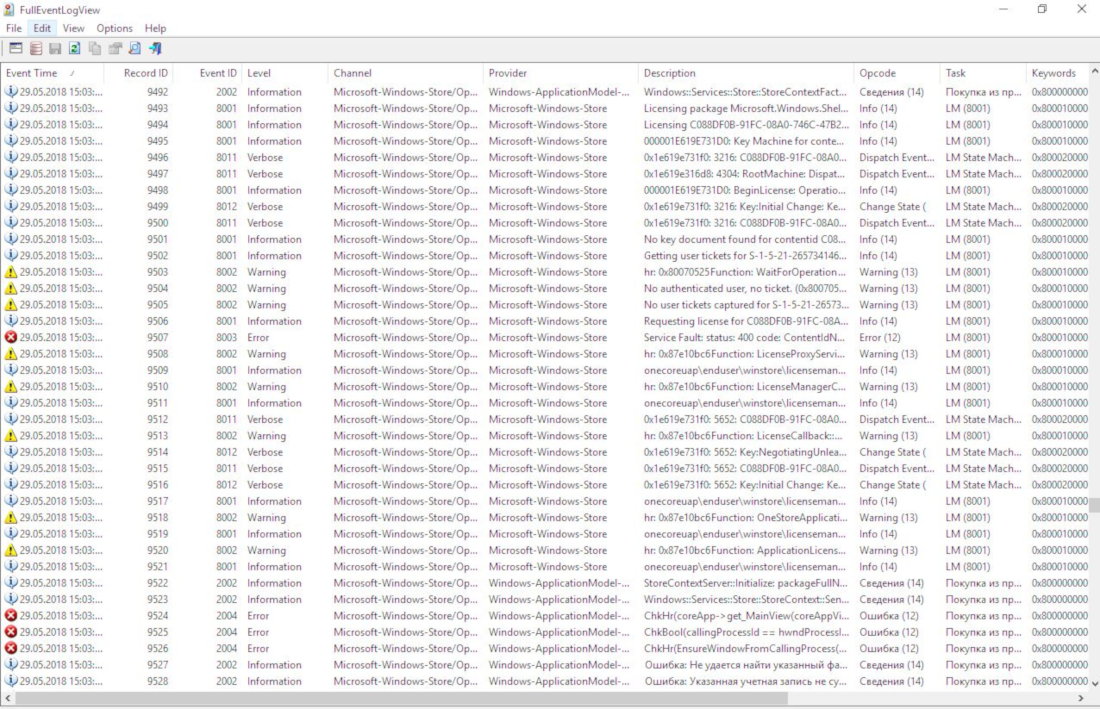
The main window of the FullEventLogView utility for viewing Windows logs

Viewing system logs in Magnet AXIOM for computers
So, what events will interest us in the first place:
- Account Logon - log into the system under a specific account;
- Account Mgmt - changing an account (moving to a group, renaming, assigning rights, and so on);
- Logon Events - login / logout;
- Directory Service - joining objects from Active Directory;
- Object Access - audit of access to any OS object;
- Policy Change - change the security policy;
- Privilege Use - execute any commands on behalf of an administrator or other privileged user;
- Process Tracking - tracking of events related to system processes;
- System Events - loading and shutting down the OS (including crashes).
The next step is LNK file analysis, or search for shortcuts to programs that were installed, launched, or later removed at some point. In our work, we will use the EnCase Forensic package already familiar to us.
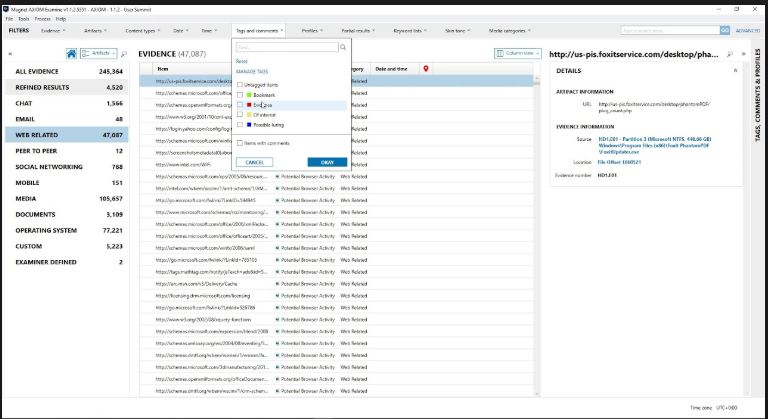
LNK file analysis in Magnet AXIOM for computers
Well, at the end of all the procedures, just in case, we will scan the user App'y built into the system - Skype, OneDrive and Edge, suddenly we will find something interesting there. For the Edge browser, we use the already known Belkasoft Evidence Center. With the same program, we will try to extract some data from the page file Pagefile.sys.
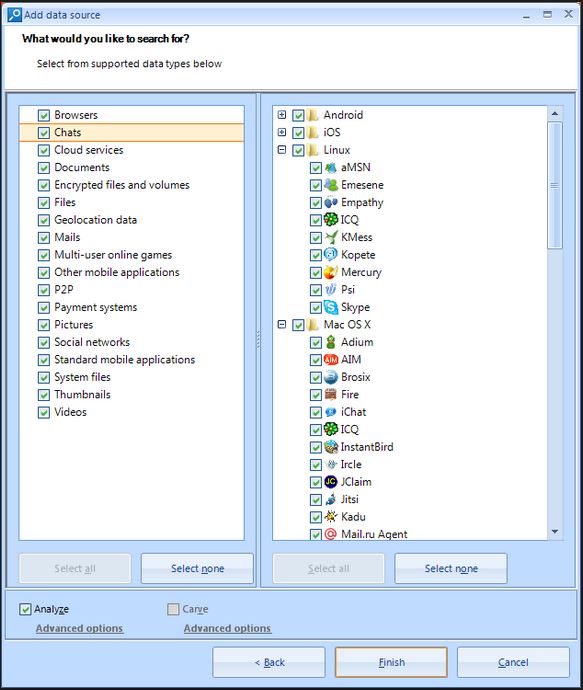
Search object selection window in Belkasoft Evidence Center 2021
Finally, add Skype to all of the above. By the way, for Skype, a profile with useful information for us is stored in the directory
C: \ Users \% USERNAME% \ AppData \ Roaming \ Skype \
although it would not hurt to look for a folder with the name Skype all over the screw, since the messenger could be installed custom or run as a portable version.
Our Belkasoft Evidence Center tool extracts data from the specified profile file, including SQLite sheets, unallocated disk area, synced files from chats, data from pagefile.sys and hiberfil.sys. There is another great utility - SkypeLogView from the same guys from NirSoft.
Results of displaying data from the local Skype profile by the SkypeLogView utility
Although it may seem like child's play, on Windows systems, you can even extract the notification history from the system tray. Information about the notification is stored in the directory
\ Users \% Username% \ AppData \ Local \ Microsoft \ Windows \ Notifications
The name of the database containing the notification history can change on each machine and depends on some internal parameters (the file extension will not necessarily be exactly .db). To open it, you need a SQLite manager. After running SQLite, you need to find the .db files in
C: \ Users \ Username \ AppData \ Local \ Microsoft \ Windows \ Notifications
and, simply adding to the manager, get the built-in viewer window.
A similar theme with the voice assistant Cortana: it also has a database that stores history, and it is located along the way
C: \ Users [User] \ AppData \ Local \ Packages \ Microsoft.Windows.Cortana_xxxx \ LocalState \ ESEDatabase_CortanaCoreInstance \ CortanaCoreDb
A few words about OneDrive. If the synchronization option was enabled (for example, with an Android smartphone), then some of the files can be found in the gadget along the way
/mnt/sdcard/Android/data/com.microsoft.skydrive
If we are talking about the desktop version, then the logs of loading / unloading, synchronization and similar events can be viewed in text documents along the way
C: \ Users \ <USERNAME> \ AppData \ Local \ Microsoft \ OneDrive \ logs
How can I minimize the risks of using my work laptop while traveling?
- Use it only as a thin client and perform all actions on the corporate server as deferred after checking them
- Control potentially dangerous actions through remote administration
- Nothing, since physical access to the laptop is simplified for the attacker
Investigation results
We have collected all the available information, and what is the bottom line?Among other files in Shadow Copy, we found an unknown executable file, which, as it turned out later, was a malware code designed to steal logins / passwords, characters typed from the keyboard, clipboard, coockie files. Moreover, this file is not detected in any way by the installed AV. It was also noticed that established connections are hanging to the outside world on several IP-addresses of servers located in Western Europe, which are not typical for the software installed on the patient. According to the logs of the RBS system, it was noted that the login to the system took place at lunchtime, when the treasurer, who owns this laptop, was absent from the office and could not perform these operations. It was a big mistake of a specialist to leave USB keys with electronic signature permanently inserted into the computer port.
In collaboration with antivirus analysts, we were able to recover a highly likely hack scenario.
So, the laptop was handed over to support for software installation and performance optimization a week before the incident. It was then that malicious code was thrown at the client, which registered itself in startup. Within a week, the malware collected all data entered from the keyboard, dumped the registry, analyzed the user's activity hours, and transmitted all this to the attacker's command and control server. Then the malware worked as a dropper: it pulled backdoor components from the network (which made it possible to establish a secure remote communication channel to the victim's computer), presumably using encapsulation in the DNS protocol .
On day X, when the employee went to lunch, the hacker connected to the infected machine, logged in to the RBS using the connected EP keys on the USB token, carried out financial transactions and covered up the traces: he removed the malware, backdoor modules from the system, cleaned up %TEMP%part of the security and user logs for which there is enough authority.
In view of the "inertia of the accounting system" (everyone who works with accounting, we recommend that you take this euphemism into service.
- Approx. ed.), the corporate security service learned about the incident only two days later, when the attacker had already managed to cash out the transferred funds. However, the artifacts left on the switched off laptop, although they did not return the money, nevertheless made it possible to restore the picture of what was happening.
Conclusion
Our analysis of today's large case has come to an end. You have become familiar with the use of basic forensic utilities in practice, thanks to which, in the event of a hack, you can independently go through the key "checks", collect artifacts and, based on this information, restore the hacking scenario. If we add to this the parsing of malware and backdoors, which were used to unauthorized connections and steal account data from RBS, then voila, we came close to localizing the attacker! Now you know how real forensic experts work and how hard they work bit by bit to collect invaluable information.xakep.ru
