Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,038
- Points
- 113
How did hundreds of Internet users manage to download a Trojan browser instead of a legitimate one?
A new campaign to distribute malware through the Google Ads advertising platform coincided with the launch of the Arc web browser for Windows, which led to the infection of many users with Trojan installers.
Arc Browser is a new web browser with an innovative user interface that sets it apart from traditional Internet browsers. After a successful launch in July 2023 for macOS and a lot of positive feedback from technical publications and users, the release of the Windows version caused universal interest in this product.
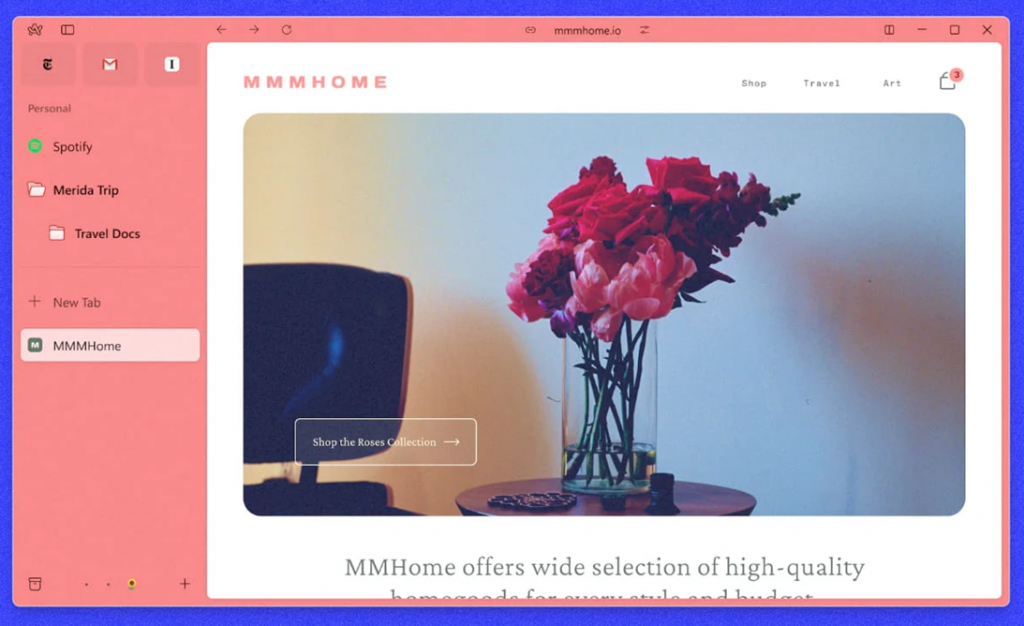
Arc Browser interface for Windows
According to a recent report by Malwarebytes, cybercriminals have prepared well for the launch of Arc for Windows by placing a series of malicious ads in Google Ads in advance to attract users who are targeted for downloading the new web browser.
The secret to their success is simple: the whole point is that the Google advertising platform has long had a significant problem allowing attackers to place ads displaying legitimate URLs, which was previously used for attacks on Amazon, Whales Market, WebEx and YouTube. We described one of these attacks in detail last year.
Malwarebytes researchers found advertising results for the queries "arc installer" and "arc browser windows", showing the official address of the Arc browser. However, after clicking on the ad, users do not get to the official site, but are redirected to malicious domains that visually resemble the real Arc site.
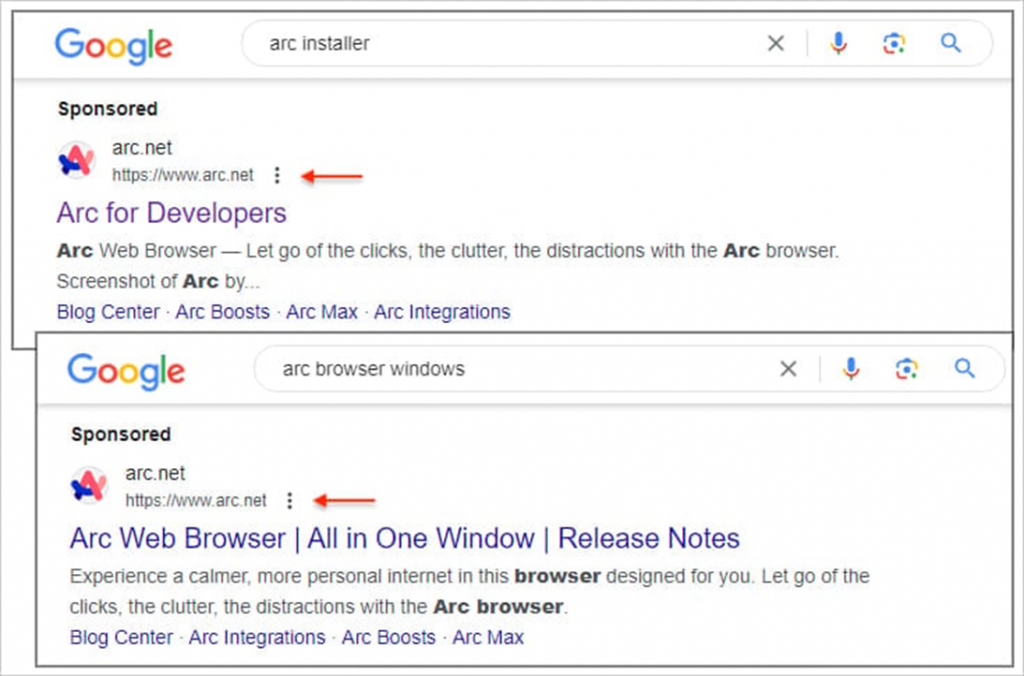
Ad output that displays a legitimate URL, but leads to a third-party site
When the user has passed a series of redirects, the domain in the browser's address bar no longer matches the official one, but since the site's interface looks legitimate, many users simply do not look up at the address bar.
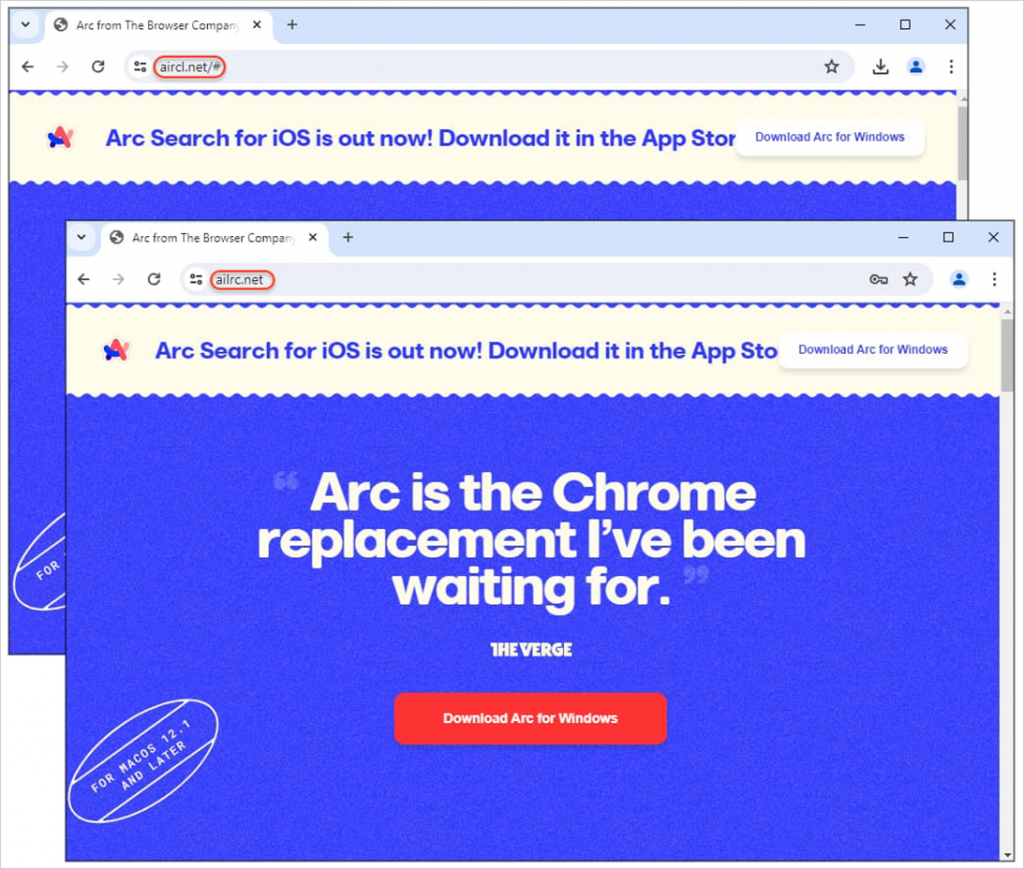
The domain is different after clicking on an advertising link in Google
When you click on the "Download" button, the Trojan installer is downloaded from the MEGA platform, which then downloads an additional piece of malware called "Download". bootstrap.exe" from an external resource. At the same time, a legitimate Arc Browser is actually installed on the target system to avoid suspicion on the part of the user.
This Trojan installer uses the MEGA API to perform C2 operations, sending and receiving operational instructions and data. The malicious file also downloads a PNG file with malicious code, which compiles and discards the final malicious file "JRWeb.exe" to the victim's disk.
Malwarebytes also recorded a separate infection chain, where the installer uses the Python executable file to inject code into "msbuild.exe", which requests commands from an external site for execution.
Analysts assume that the final malware in all the attacks reviewed is an infostiler, although this has not yet been confirmed definitively. Since the real Arc browser is eventually installed on the victim's computer, and malicious files run unnoticed in the background, users are unlikely to realize that their devices are infected.
Cybercriminals often use the hype around new programs or games to spread malware. To avoid such attacks, it is recommended to avoid any advertising results in the search results of both Google and other search engines. Using proven ad blockers will kill the problem in the bud, as it will banally hide all advertising links in the search engine.
In addition, you should always check the authenticity of the domain from which you plan to download any installer, even if you are sure that you initially switched to a legitimate one. Tricks with spoofing the displayed address in Google search results make even tech-savvy users especially vulnerable to this type of attack.
A new campaign to distribute malware through the Google Ads advertising platform coincided with the launch of the Arc web browser for Windows, which led to the infection of many users with Trojan installers.
Arc Browser is a new web browser with an innovative user interface that sets it apart from traditional Internet browsers. After a successful launch in July 2023 for macOS and a lot of positive feedback from technical publications and users, the release of the Windows version caused universal interest in this product.

Arc Browser interface for Windows
According to a recent report by Malwarebytes, cybercriminals have prepared well for the launch of Arc for Windows by placing a series of malicious ads in Google Ads in advance to attract users who are targeted for downloading the new web browser.
The secret to their success is simple: the whole point is that the Google advertising platform has long had a significant problem allowing attackers to place ads displaying legitimate URLs, which was previously used for attacks on Amazon, Whales Market, WebEx and YouTube. We described one of these attacks in detail last year.
Malwarebytes researchers found advertising results for the queries "arc installer" and "arc browser windows", showing the official address of the Arc browser. However, after clicking on the ad, users do not get to the official site, but are redirected to malicious domains that visually resemble the real Arc site.

Ad output that displays a legitimate URL, but leads to a third-party site
When the user has passed a series of redirects, the domain in the browser's address bar no longer matches the official one, but since the site's interface looks legitimate, many users simply do not look up at the address bar.

The domain is different after clicking on an advertising link in Google
When you click on the "Download" button, the Trojan installer is downloaded from the MEGA platform, which then downloads an additional piece of malware called "Download". bootstrap.exe" from an external resource. At the same time, a legitimate Arc Browser is actually installed on the target system to avoid suspicion on the part of the user.
This Trojan installer uses the MEGA API to perform C2 operations, sending and receiving operational instructions and data. The malicious file also downloads a PNG file with malicious code, which compiles and discards the final malicious file "JRWeb.exe" to the victim's disk.
Malwarebytes also recorded a separate infection chain, where the installer uses the Python executable file to inject code into "msbuild.exe", which requests commands from an external site for execution.
Analysts assume that the final malware in all the attacks reviewed is an infostiler, although this has not yet been confirmed definitively. Since the real Arc browser is eventually installed on the victim's computer, and malicious files run unnoticed in the background, users are unlikely to realize that their devices are infected.
Cybercriminals often use the hype around new programs or games to spread malware. To avoid such attacks, it is recommended to avoid any advertising results in the search results of both Google and other search engines. Using proven ad blockers will kill the problem in the bud, as it will banally hide all advertising links in the search engine.
In addition, you should always check the authenticity of the domain from which you plan to download any installer, even if you are sure that you initially switched to a legitimate one. Tricks with spoofing the displayed address in Google search results make even tech-savvy users especially vulnerable to this type of attack.

