Brother
Professional
- Messages
- 2,590
- Reaction score
- 533
- Points
- 113
Hiding under legitimate traffic, malware steals files and installs backdoors.
According to a new report from ESET, the Iranian government-sponsored OilRig group deployed 3 different malware loaders during 2022 to provide permanent access to organizations in Israel.
The deployed tools are named ODAgent, OilCheck, and OilBooster. In addition, the group used an updated version of its bootloader called SampleCheck5000 (SC5k). The uploaders are notable for using Microsoft cloud services to communicate with Command and Control servers (C2) and transfer data, including the Microsoft Graph API for OneDrive and Outlook, as well as the Microsoft Exchange Web Services API (EWS). This tactic allows you to hide the attacker's infrastructure, disguising it as normal network traffic.
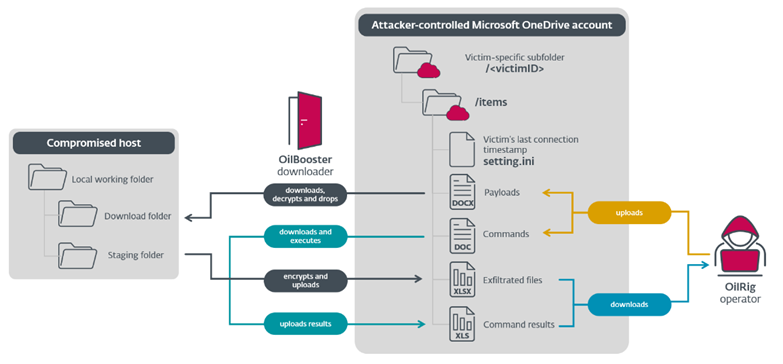
Scheme for establishing communication withC2 server using a shared OneDrive account
Among the targets of the attacks are healthcare organizations, a manufacturing company, and a local government organization. All of them have previously been attacked by OilRig. Details about how exactly the targets were compromised are still unknown, as well as whether the attackers were able to maintain their presence in the networks for deploying uploaders at different points in 2022.
The tools are also similar to the PowerExchange group backdoor in using email to transmit data, although in the case of PowerExchange, data is sent to the attacker's email address using the affected organization's mail server.
In each case, the uploaders use a shared account (mail or cloud storage) managed by OilRig to exchange messages with OilRig operators, and the same account is usually used by multiple victims. Uploaders access this account to download commands and additional payloads, as well as to send the results of commands and prepared files.
According to a new report from ESET, the Iranian government-sponsored OilRig group deployed 3 different malware loaders during 2022 to provide permanent access to organizations in Israel.
The deployed tools are named ODAgent, OilCheck, and OilBooster. In addition, the group used an updated version of its bootloader called SampleCheck5000 (SC5k). The uploaders are notable for using Microsoft cloud services to communicate with Command and Control servers (C2) and transfer data, including the Microsoft Graph API for OneDrive and Outlook, as well as the Microsoft Exchange Web Services API (EWS). This tactic allows you to hide the attacker's infrastructure, disguising it as normal network traffic.

Scheme for establishing communication withC2 server using a shared OneDrive account
Among the targets of the attacks are healthcare organizations, a manufacturing company, and a local government organization. All of them have previously been attacked by OilRig. Details about how exactly the targets were compromised are still unknown, as well as whether the attackers were able to maintain their presence in the networks for deploying uploaders at different points in 2022.
- ODAgent is a C#/.NET loader that uses the Microsoft OneDrive API to communicate as a C2 server, allowing an attacker to download and execute useful data, as well as delete intermediate files.
- OilBooster, like ODAgent, uses the Microsoft OneDrive API as a C2 server. OilBooster also uses the Microsoft Graph API to connect to a Microsoft Office 365 account. The API is used to interact with an attacker's OneDrive account to receive commands and useful data from victim-specific folders.
- The SampleCheck5000 communicates with a shared Microsoft Exchange email account using the Office Exchange Web Services API to download and execute additional OilRig tools.
- OilCheck uses the SampleCheck5000 technique to extract commands from draft messages, but instead of using the EWS API, it uses the Microsoft Graph API for network communications.
The tools are also similar to the PowerExchange group backdoor in using email to transmit data, although in the case of PowerExchange, data is sent to the attacker's email address using the affected organization's mail server.
In each case, the uploaders use a shared account (mail or cloud storage) managed by OilRig to exchange messages with OilRig operators, and the same account is usually used by multiple victims. Uploaders access this account to download commands and additional payloads, as well as to send the results of commands and prepared files.

