Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,038
- Points
- 113
French researchers from the École Normale Supérieure (Ecole Normale Supérieure) have published details of their investigation into the 2011 incident. Then a group of hackers managed to steal more than $680,000 from users of French banks by deceiving the security system of EMV bank cards. Researchers explained how the attackers managed to do this.
In 2011, the police, of course, were investigating the theft of money from bank clients. According to law enforcement agencies, hackers modified about 40 bank cards, managed to carry out more than 7,000 transactions and stole about $680,000.
Then, in search of criminals, law enforcement agencies collected IMSI numbers of devices that appeared in places where criminals used stolen cards. The police then matched the IMSI numbers with the SIM cards and the time of the incidents. As a result of these investigations, a 25-year-old woman was first detained, and then four of her accomplices. Among them was the engineer who came up with the EMV card hacking scheme, which researchers now call one of the most intricate and cunning frauds in history.
In 2011, the École Normale Supérieure team carried out forensic analysis of evidence to assist the police. It was this report that the researchers released on October 20, 2015.
Since the stolen cards were evidence, experts could not simply take them apart and “see what’s inside.” Instead, we had to resort to X-rays and a microscope. The team also determined how the chip behaves during use, using read-only programs to check what information the card reports to the PoS terminal.
According to the published report, hackers managed to implement a man-in-the-middle attack by introducing a second, homemade chip, called FUN or FUNcard, into the original card chip. Due to this modification, the thickness of the chip increased from 0.4 mm to 0.7 mm, but the card still passed into the PoS terminal, albeit with some difficulty.
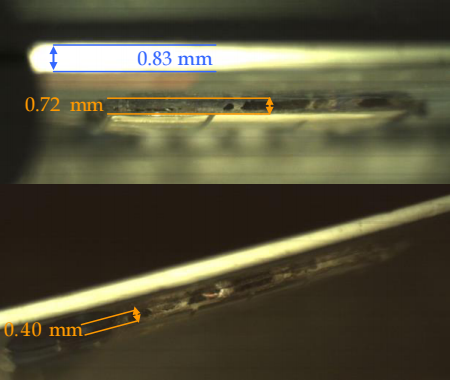
Thickness of a regular card versus thickness of a modified one
The attackers took advantage of a known bug in the chip-and-PIN card system. A vulnerability in the protocol by which the card communicates with the reader was found back in 2006; the bug allows an attacker to use the card without even knowing the PIN code.
A typical EMV transaction is carried out in three stages: card authentication, cardholder verification, transaction authorization. If a card modified by criminals was used, the original chip allowed it to pass authentication. However, at the stage of authorization of the cardholder, the PoS system still asks to enter a PIN code. In the case examined by the École Normale Supérieure, the hackers could enter any PIN code - their homemade chip would come into play and trick the system into believing that any code was correct.
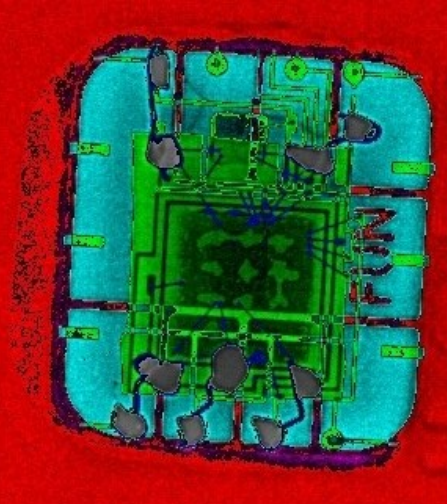
The X-ray clearly shows the use of different materials. The original chip is painted green.
“The attackers intercepted the PIN code request and responded that it was correct, no matter what the code was. This was the core of their attack,” the researchers write.
That is, the hackers acted according to the following scheme. They stole bank cards, removed the chip from them, integrated a FUNcard into it (which, according to the researchers, required “skill, patience and very delicate work”), then inserted the resulting modification into the “body” of another card and went shopping and to ATMs , emptying other people's accounts.
Fortunately, these days the bug, which was exploited by savvy criminals, has already been fixed, at least in most European countries. The researchers declined to disclose details about the new EMV protection in their report, for obvious reasons. You can view the full version of the document here.
(c) https://xakep.ru/2015/10/22/82648/
In 2011, the police, of course, were investigating the theft of money from bank clients. According to law enforcement agencies, hackers modified about 40 bank cards, managed to carry out more than 7,000 transactions and stole about $680,000.
Then, in search of criminals, law enforcement agencies collected IMSI numbers of devices that appeared in places where criminals used stolen cards. The police then matched the IMSI numbers with the SIM cards and the time of the incidents. As a result of these investigations, a 25-year-old woman was first detained, and then four of her accomplices. Among them was the engineer who came up with the EMV card hacking scheme, which researchers now call one of the most intricate and cunning frauds in history.
In 2011, the École Normale Supérieure team carried out forensic analysis of evidence to assist the police. It was this report that the researchers released on October 20, 2015.
Since the stolen cards were evidence, experts could not simply take them apart and “see what’s inside.” Instead, we had to resort to X-rays and a microscope. The team also determined how the chip behaves during use, using read-only programs to check what information the card reports to the PoS terminal.
According to the published report, hackers managed to implement a man-in-the-middle attack by introducing a second, homemade chip, called FUN or FUNcard, into the original card chip. Due to this modification, the thickness of the chip increased from 0.4 mm to 0.7 mm, but the card still passed into the PoS terminal, albeit with some difficulty.

Thickness of a regular card versus thickness of a modified one
The attackers took advantage of a known bug in the chip-and-PIN card system. A vulnerability in the protocol by which the card communicates with the reader was found back in 2006; the bug allows an attacker to use the card without even knowing the PIN code.
A typical EMV transaction is carried out in three stages: card authentication, cardholder verification, transaction authorization. If a card modified by criminals was used, the original chip allowed it to pass authentication. However, at the stage of authorization of the cardholder, the PoS system still asks to enter a PIN code. In the case examined by the École Normale Supérieure, the hackers could enter any PIN code - their homemade chip would come into play and trick the system into believing that any code was correct.

The X-ray clearly shows the use of different materials. The original chip is painted green.
“The attackers intercepted the PIN code request and responded that it was correct, no matter what the code was. This was the core of their attack,” the researchers write.
That is, the hackers acted according to the following scheme. They stole bank cards, removed the chip from them, integrated a FUNcard into it (which, according to the researchers, required “skill, patience and very delicate work”), then inserted the resulting modification into the “body” of another card and went shopping and to ATMs , emptying other people's accounts.
Fortunately, these days the bug, which was exploited by savvy criminals, has already been fixed, at least in most European countries. The researchers declined to disclose details about the new EMV protection in their report, for obvious reasons. You can view the full version of the document here.
(c) https://xakep.ru/2015/10/22/82648/

