Providing an additional layer of security for users' credit and debit cards, 3D Secure Protocol (3DS) is constantly on the radar as cybercriminals seek to circumvent it. That is why, on one of the darkweb forums, attackers shared their proven methods that allow unauthorized purchases of goods in online stores at the expense of cardholders. For those who don't know: 3DS adds an extra layer of protection when shopping online. Thanks to the protocol, the buyer must confirm that he really is the owner of the bank card from which the money is debited.
The second version of the protocol (3DS 2) was developed specifically for smartphones; it allows confirming purchases using banking applications installed on the mobile device. In this case, the user can use biometric authentication: scanning a fingerprint or a face. Nevertheless, the first version of the 3DS is still in use in many stores today, which opens up the possibility of deceiving the cardholder through social engineering. In this case, the main task of the attackers is to force the user to issue a short code or password used to confirm the transaction. As cybercriminals noted on the forum, the successful use of a combination of social engineering and phishing attacks allows you to bypass 3D Secure and buy any product at the expense of an unsuspecting citizen.
In the blog of Gemini Advisory, experts published a post in which they warn users about existing effective methods of bypassing the 3D Secure protocol. At the same time, experts emphasize that cybercriminals are actively discussing these methods, which may lead to a surge in such attacks. To implement the described methods, the attacker will first need to obtain at least a minimum amount of information about the cardholder: his name, phone number, e-mail address, residence address and driver's license number. Having received the necessary data, the criminal can use it in a conversation with the user on behalf of the bank employee. As a rule, gullible citizens fall for such tricks, because the fraudster gives out the right information.
One of the visitors to the darkweb forum described just such a scheme:
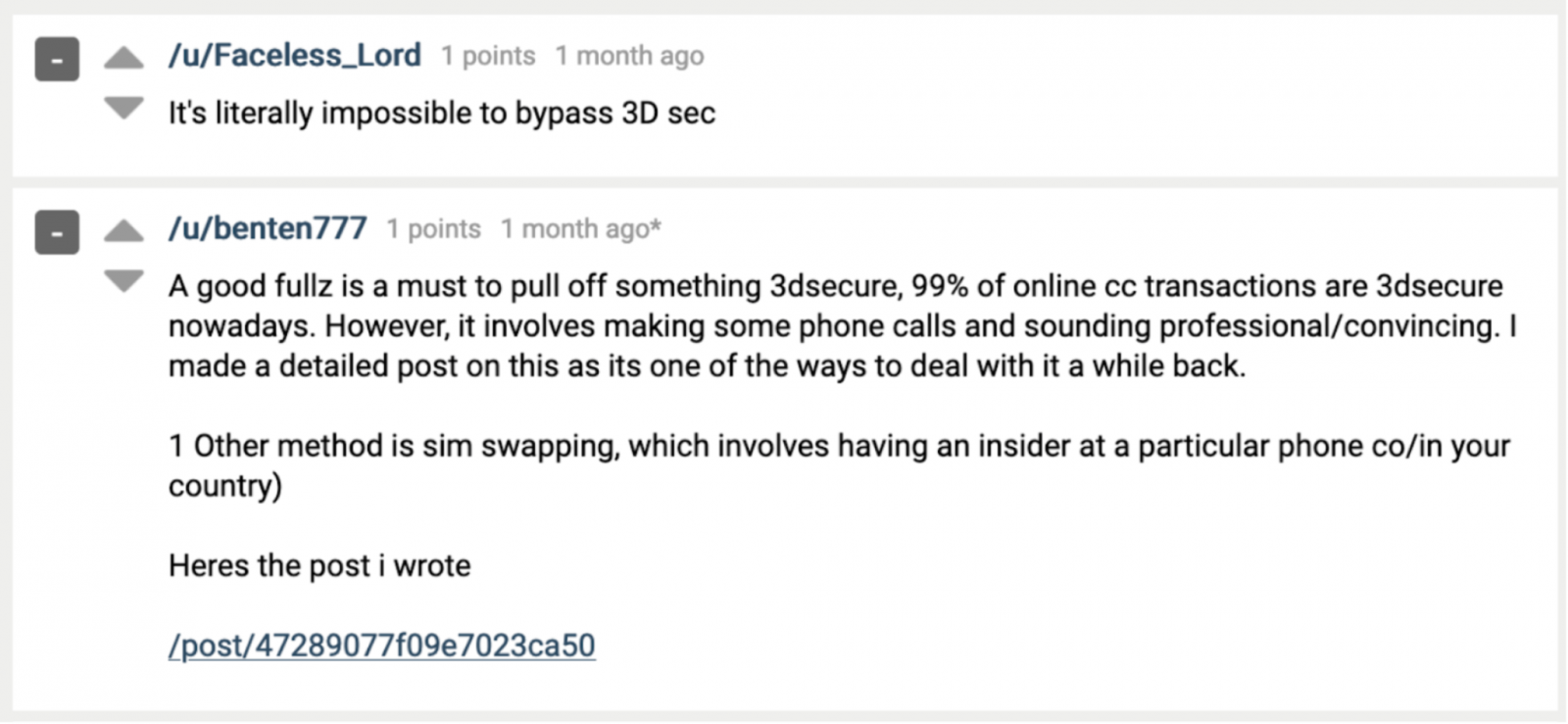
Using user data, voice changing software and an application for spoofing a phone number, a cyber fraudster can make a purchase in an online store, and then call the card holder and find out all the information necessary to confirm the transaction. Cybercriminals also described other ways: to lure a user to a phishing site, install malware on his mobile device, and the like. In general, people need to be more careful when it comes to bank cards. Remember, attackers are on the alert.
The second version of the protocol (3DS 2) was developed specifically for smartphones; it allows confirming purchases using banking applications installed on the mobile device. In this case, the user can use biometric authentication: scanning a fingerprint or a face. Nevertheless, the first version of the 3DS is still in use in many stores today, which opens up the possibility of deceiving the cardholder through social engineering. In this case, the main task of the attackers is to force the user to issue a short code or password used to confirm the transaction. As cybercriminals noted on the forum, the successful use of a combination of social engineering and phishing attacks allows you to bypass 3D Secure and buy any product at the expense of an unsuspecting citizen.
In the blog of Gemini Advisory, experts published a post in which they warn users about existing effective methods of bypassing the 3D Secure protocol. At the same time, experts emphasize that cybercriminals are actively discussing these methods, which may lead to a surge in such attacks. To implement the described methods, the attacker will first need to obtain at least a minimum amount of information about the cardholder: his name, phone number, e-mail address, residence address and driver's license number. Having received the necessary data, the criminal can use it in a conversation with the user on behalf of the bank employee. As a rule, gullible citizens fall for such tricks, because the fraudster gives out the right information.
One of the visitors to the darkweb forum described just such a scheme:

Using user data, voice changing software and an application for spoofing a phone number, a cyber fraudster can make a purchase in an online store, and then call the card holder and find out all the information necessary to confirm the transaction. Cybercriminals also described other ways: to lure a user to a phishing site, install malware on his mobile device, and the like. In general, people need to be more careful when it comes to bank cards. Remember, attackers are on the alert.
