Man
Professional
- Messages
- 3,222
- Reaction score
- 1,201
- Points
- 113
In the world of online privacy, SOCKS5 proxies are a powerful tool for hiding your real IP address. However, the effectiveness of a proxy goes beyond simply hiding your IP – how your traffic is perceived by the destination server is also important. A key factor in this perception is the OS fingerprint, which can significantly affect the authenticity of your internet connection.
For example, the Time To Live (TTL) value in an IP packet, the order of TCP options, or the response to certain network requests may vary depending on the operating system. These subtle differences form the OS fingerprint. Anti-fraud systems use these fingerprints to determine whether the traffic comes from a real user or a suspicious source.

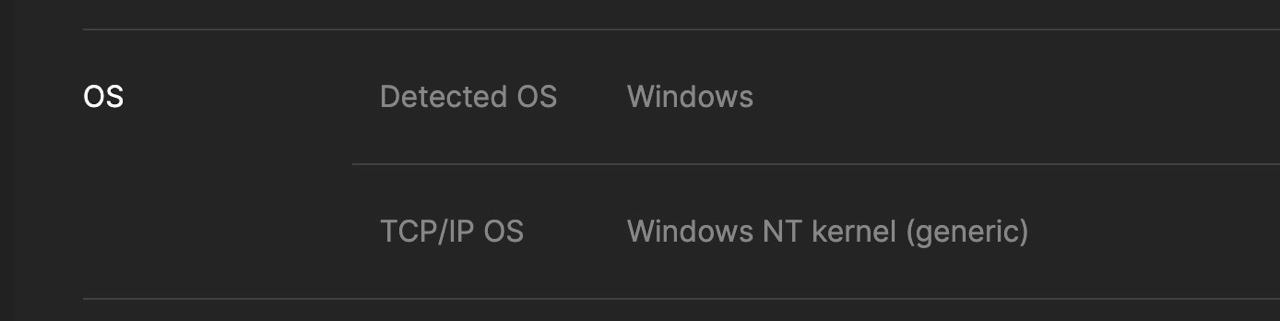
Elusive.sh Proxies (pixelscan.net)
If you are serious about maintaining your anonymity and evading detection, choosing a proxy with a Windows OS fingerprint is a smart decision. Don’t let mediocre proxies expose you to unnecessary risk — choose the authenticity and security of our Windows-based SOCKS5 proxies.
What is OS fingerprint?
An OS fingerprint (operating system fingerprint) is a unique identifier that indicates which operating system is used on the device from which the connection is made. It is determined by analyzing specific characteristics of network traffic, such as the behavior of the TCP/IP stack, packet headers, and the order of certain flags in these headers. Each operating system, be it Windows, Linux, macOS, or others, implements these protocols with some differences, which creates a unique OS fingerprint.For example, the Time To Live (TTL) value in an IP packet, the order of TCP options, or the response to certain network requests may vary depending on the operating system. These subtle differences form the OS fingerprint. Anti-fraud systems use these fingerprints to determine whether the traffic comes from a real user or a suspicious source.
How do OS fingerprints work in practice?
When you connect to a website, the server sees more than just your IP address; it also analyzes network traffic to determine what operating system you're using. This process involves several steps:- Packet sniffing: The server examines the headers of incoming packets. Key fields such as TTL, window size, and TCP options are carefully analyzed.
- Pattern matching: The server compares these packet characteristics to a database of known OS fingerprints. This database is built by analyzing traffic from known operating systems and recording their unique characteristics.
- OS Identification: Based on this comparison, the server determines the most likely operating system you are using. This information is used to decide whether your connection is legitimate or requires additional verification.
Anti-fraud systems and OS fingerprints
Anti-fraud systems use OS fingerprinting as part of a broader strategy to detect and block fraudulent activity. These systems are designed to identify patterns that appear unusual or inconsistent with typical user behavior. For example:- Detecting inconsistencies: If an IP address is associated with a home ISP, but the OS fingerprint indicates that it is coming from a Linux-based server (which is not typical for home users), this may raise suspicion. The system may suspect that the traffic is not coming from a real user, but from a bot or proxy server.
- Behavior Analysis: Anti-fraud systems also analyze the consistency of OS fingerprints between sessions. If a user's OS fingerprint changes frequently (e.g. from Windows to Linux and back), this may indicate the use of multiple proxies or spoofing methods, which will lead to additional checks such as CAPTCHA or multi-factor authentication.
- Traffic profiling: By combining OS fingerprints with other data (such as browser fingerprints, geolocation, and usage patterns), anti-fraud systems can create a detailed user profile. Any deviations from this profile can result in traffic being flagged as suspicious.
Difference between Windows and Linux OS fingerprints
Most SOCKS5 proxies on the market today run on IoT devices or servers running Linux-based operating systems. While Linux is an effective system, it creates a distinctive fingerprint that is not typical for home user devices. This can be a disadvantage in scenarios where authenticity is critical.- Linux fingerprints: Linux-based proxies are often detected due to their characteristic network behavior. IoT devices such as routers or switches, which are often used to host such proxies, add additional features to the traffic. These devices usually do not behave like standard home computers, which makes their traffic more noticeable to anti-fraud systems.

- Windows fingerprints: In contrast, our SOCKS5 proxies work on home Windows computers. Since most home users are on Windows, these proxies create OS fingerprints that closely match the expected traffic patterns of real users. This means that your traffic appears much more authentic, reducing the risk of detection or blocking.

Elusive.sh Proxies (pixelscan.net)
Why Windows-Based SOCKS5 Proxies Offer Superior Anonymity
Using a SOCKS5 proxy with a Windows OS fingerprint provides several benefits:- Authenticity: Since most home users are on Windows, using a Windows-based proxy makes your traffic appear to be coming from a real user, not a server or bot.
- Lower risk of detection: Anti-fraud systems are less likely to flag your traffic as suspicious because the OS fingerprint matches typical home user traffic.
- Improved access: With Windows fingerprinting, you're less likely to encounter CAPTCHAs, account lockouts, or other forms of verification that can disrupt your online experience.
Conclusion
In the competitive online privacy environment, choosing a SOCKS5 proxy is critical. While many providers use Linux-based devices to save money, the trade-off is clear: less authentic traffic that is more easily detected by anti-fraud systems.If you are serious about maintaining your anonymity and evading detection, choosing a proxy with a Windows OS fingerprint is a smart decision. Don’t let mediocre proxies expose you to unnecessary risk — choose the authenticity and security of our Windows-based SOCKS5 proxies.

