New version of TargetCompany with new traceless attack capabilities.
Trend Micro discovered a new version of the TargetCompany ransomware targeted at VMware ESXi. Attackers use a custom shell script to deliver and execute malware.
TargetCompany (Mallox, FARGO, Tohnichi) first appeared in June 2021 and specializes in attacks on MySQL, Oracle, and SQL Server databases, primarily in Taiwan, South Korea, Thailand, and India. In February 2022, Avast released a free decryptor for earlier versions of the ransomware.
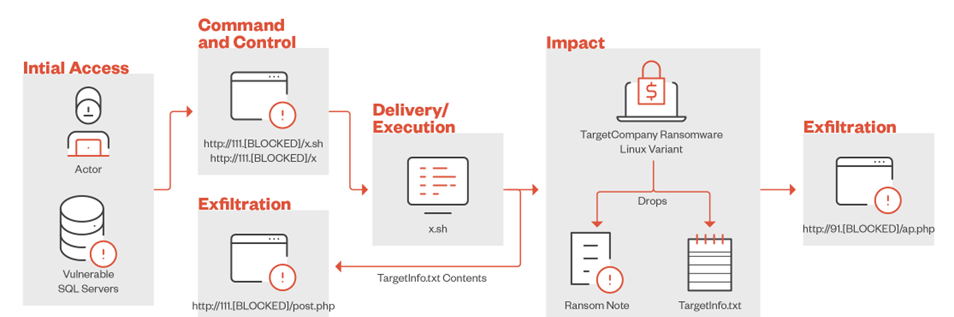
TargetCompany infection chain
According to a Trend Micro report, the new Linux variant of TargetCompany requires administrative privileges before performing malicious actions. To download and execute the ransomware, the attackers use a custom script that can also send data to two different servers, probably to ensure fault tolerance.
After hitting the target system, the script checks the environment for the presence of VMware ESXi by executing the "uname" command and checking for the presence of "vmkernel". Next, a file is created TargetInfo.txt” with information about the victim (host name, IP address, OS data, names of logged-in users and their privileges, unique identifiers and information about encrypted files and directories), which is sent to the C2 server.
The malware encrypts files with extensions associated with virtual machines (vmdk, vmem, vswp, vmx, vmsn, nvram) by adding the ".locked"extension to them. After that, a note is added to the system with instructions for paying the ransom and obtaining the decryption key.
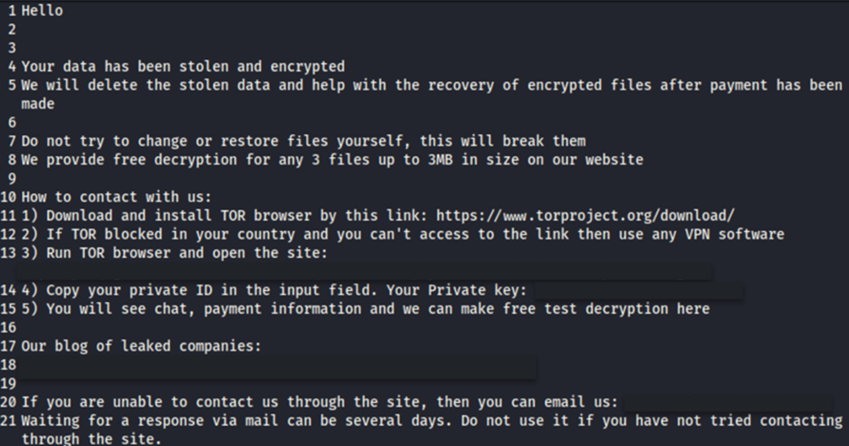
TargetCompany Buyout Note
After all tasks are completed, the script deletes the payload, so all traces that can be used to investigate incidents are removed from the affected computers.
Trend Micro analysts link the attacks of the new Linux version of TargetCompany to a cybercriminal named "vampire" mentioned in the Sekoia report. The IP addresses used to deliver malware and receive files with information about victims were linked to a provider from China, which, however, is not enough to accurately determine the origin of the attackers.
The Trend Micro report provides security recommendations, including installing multi-factor authentication (MFA), creating backups, and updating systems. The researchers also provided a list of indicators of compromise, including hashes for the Linux version of the ransomware, a custom script, and samples associated with the vampire affiliate.
Earlier, Trend Micro specialists found out that Mallox hackers use their own ransomware in combination with the Remcos RAT Trojan and the BatCloak obfuscator, which allows them to gain a foothold in the victim's system and avoid detection.
In addition, in May, the Mallox ransomware virus was used in attacks on Microsoft SQL (MS-SQL) servers. After entering the system, cybercriminals installed Remcos RAT to establish full control of the infected host.
Trend Micro discovered a new version of the TargetCompany ransomware targeted at VMware ESXi. Attackers use a custom shell script to deliver and execute malware.
TargetCompany (Mallox, FARGO, Tohnichi) first appeared in June 2021 and specializes in attacks on MySQL, Oracle, and SQL Server databases, primarily in Taiwan, South Korea, Thailand, and India. In February 2022, Avast released a free decryptor for earlier versions of the ransomware.

TargetCompany infection chain
According to a Trend Micro report, the new Linux variant of TargetCompany requires administrative privileges before performing malicious actions. To download and execute the ransomware, the attackers use a custom script that can also send data to two different servers, probably to ensure fault tolerance.
After hitting the target system, the script checks the environment for the presence of VMware ESXi by executing the "uname" command and checking for the presence of "vmkernel". Next, a file is created TargetInfo.txt” with information about the victim (host name, IP address, OS data, names of logged-in users and their privileges, unique identifiers and information about encrypted files and directories), which is sent to the C2 server.
The malware encrypts files with extensions associated with virtual machines (vmdk, vmem, vswp, vmx, vmsn, nvram) by adding the ".locked"extension to them. After that, a note is added to the system with instructions for paying the ransom and obtaining the decryption key.

TargetCompany Buyout Note
After all tasks are completed, the script deletes the payload, so all traces that can be used to investigate incidents are removed from the affected computers.
Trend Micro analysts link the attacks of the new Linux version of TargetCompany to a cybercriminal named "vampire" mentioned in the Sekoia report. The IP addresses used to deliver malware and receive files with information about victims were linked to a provider from China, which, however, is not enough to accurately determine the origin of the attackers.
The Trend Micro report provides security recommendations, including installing multi-factor authentication (MFA), creating backups, and updating systems. The researchers also provided a list of indicators of compromise, including hashes for the Linux version of the ransomware, a custom script, and samples associated with the vampire affiliate.
Earlier, Trend Micro specialists found out that Mallox hackers use their own ransomware in combination with the Remcos RAT Trojan and the BatCloak obfuscator, which allows them to gain a foothold in the victim's system and avoid detection.
In addition, in May, the Mallox ransomware virus was used in attacks on Microsoft SQL (MS-SQL) servers. After entering the system, cybercriminals installed Remcos RAT to establish full control of the infected host.
