CarderPlanet
Professional
Attackers thank Supermicro for new vulnerabilities in BMC controllers.
Researchers from the information security company Binarly have discovered 7 vulnerabilities in the Baseboard Management Controller (BMC) from Supermicro, which can create dangerous consequences for organizations using Supermicro servers.
One of the vulnerabilities identified as CVE-2023-40289 allows malicious code to be executed inside BMC, but exploiting the error requires administrative access to the web interface used for configuring and managing BMC.
The other 6 vulnerabilities are related to Cross-Site Scripting (XSS) attacks, which can be used in combination with CVE-2023-40289, creating phishing attack scenarios on administrators ' machines.
In response to the researchers report, Supermicro stated that there is no automatic way to install patches, which makes the process of fixing vulnerabilities more time-consuming. It is noted that all vulnerabilities come from a third-party software developer ATEN, who developed the IPMI firmware for Supermicro. Although ATEN has already fixed the CVE vulnerability-2023-40289 6 months ago, the fix was never implemented in the firmware.
The Supermicro report states that the vulnerabilities affect "some X11, H11, B11, CMM, M11 and H12 motherboards. Supermicro said that the company is not aware of any malicious use of the vulnerabilities.
The problem becomes even more acute due to the fact that more than 70,000 copies of Supermicro BMC with an open IPMI web interface are publicly available, as shown by the Shodan search engine. Cybercriminals can use the discovered flaws to gain control over servers if the BMC controllers are not isolated from the Internet.
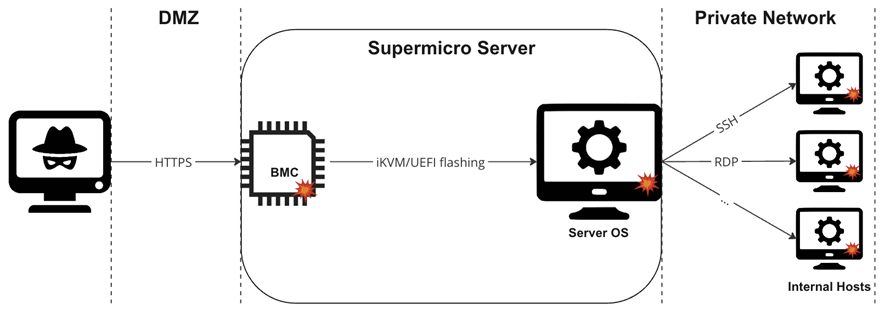
Chain of attack on an Internet-accessible server using vulnerabilities
This raises the question of how high the threat level is. While Supermicro rates vulnerabilities in the range of 7.2 to 8.3 on the CVSSv3 scale, researchers from Binarly assign them higher scores, ranging from 8.3 to 9.6.
Experts point out that the manufacturer's attempts to reduce the final threat level in the process of vulnerability disclosure may lead to the fact that end users will receive incorrect information when evaluating a certain update, which in turn may lead to an underestimation of the threat level.
The incident also highlights the importance of regularly updating and maintaining the security of server equipment, especially in light of the increasing threats in the field of cybersecurity and the complexity of modern attacks.
Researchers from the information security company Binarly have discovered 7 vulnerabilities in the Baseboard Management Controller (BMC) from Supermicro, which can create dangerous consequences for organizations using Supermicro servers.
One of the vulnerabilities identified as CVE-2023-40289 allows malicious code to be executed inside BMC, but exploiting the error requires administrative access to the web interface used for configuring and managing BMC.
The other 6 vulnerabilities are related to Cross-Site Scripting (XSS) attacks, which can be used in combination with CVE-2023-40289, creating phishing attack scenarios on administrators ' machines.
In response to the researchers report, Supermicro stated that there is no automatic way to install patches, which makes the process of fixing vulnerabilities more time-consuming. It is noted that all vulnerabilities come from a third-party software developer ATEN, who developed the IPMI firmware for Supermicro. Although ATEN has already fixed the CVE vulnerability-2023-40289 6 months ago, the fix was never implemented in the firmware.
The Supermicro report states that the vulnerabilities affect "some X11, H11, B11, CMM, M11 and H12 motherboards. Supermicro said that the company is not aware of any malicious use of the vulnerabilities.
The problem becomes even more acute due to the fact that more than 70,000 copies of Supermicro BMC with an open IPMI web interface are publicly available, as shown by the Shodan search engine. Cybercriminals can use the discovered flaws to gain control over servers if the BMC controllers are not isolated from the Internet.

Chain of attack on an Internet-accessible server using vulnerabilities
This raises the question of how high the threat level is. While Supermicro rates vulnerabilities in the range of 7.2 to 8.3 on the CVSSv3 scale, researchers from Binarly assign them higher scores, ranging from 8.3 to 9.6.
Experts point out that the manufacturer's attempts to reduce the final threat level in the process of vulnerability disclosure may lead to the fact that end users will receive incorrect information when evaluating a certain update, which in turn may lead to an underestimation of the threat level.
The incident also highlights the importance of regularly updating and maintaining the security of server equipment, especially in light of the increasing threats in the field of cybersecurity and the complexity of modern attacks.
