Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
Using the Nim language and open tools shows how hackers follow trends.
Kaspersky Lab specialists have discovered the Coyote Banking Trojan, which targets users of more than 60 banking institutions, mainly from Brazil. A distinctive feature of this malware is a complex infection chain that uses various advanced technologies, making Coyote stand out among other banking Trojans.
For distribution, Coyote uses the open-source Squirrel installer, using NodeJS and the relatively new multi-platform programming language Nim to complete the infection. It is noted that cybercriminals are increasingly resorting to the use of less popular and cross-platform languages, which is becoming a trend in the field of cyber threats.
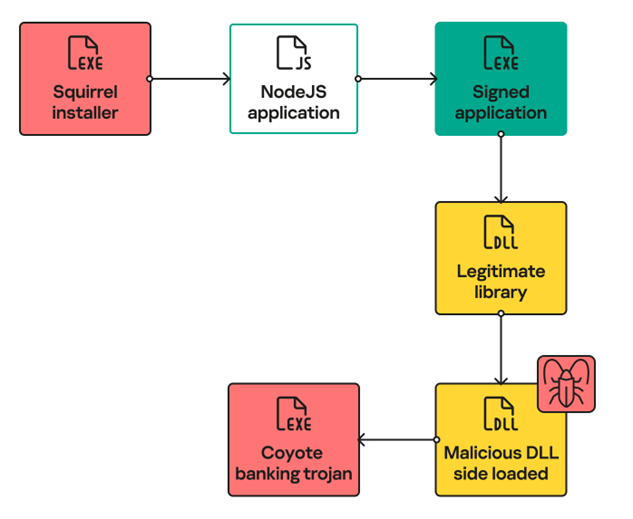
Coyote Infection Chain
The trojan uses the Squirrel tool to install and update Windows applications, hiding its boot loader under the guise of an update. Launched via Squirrel, the NodeJS script executes obfuscated JavaScript code that copies all executable files from the local folder to the user's folder, and then runs the signed application from this directory, providing loading via DLL Sideloading.
Interestingly, to download the last stage of the Trojan, the Nim language is used, the purpose of which is to unpack and execute the executable file .NET in memory. Thus, the Trojan achieves stability by using an entry point that is activated every time the computer is rebooted.
Despite the lack of code obfuscation, Coyote uses string obfuscation with AES encryption to further hide its activity. To decrypt strings, the Trojan creates a table from base64-encoded data, using a randomly generated key and official .NET encryption interfaces.
To maintain activity, Coyote abuses Windows login scripts by checking for the presence and inserting the path to the signed application in the registry. The Trojan's goal is to monitor the victim's running apps while waiting for access to a banking app or website.
When the banking application is activated, the Trojan communicates with the Command and Control Server (C2) using SSL channels with mutual authentication, and transmits the collected information, including the machine name, GUID, and the banking application used. In response, the server can send commands to perform various actions, including keylogging and creating screenshots. In addition, Coyota even requests PIN codes from bank cards and displays phishing pages to collect user credentials.
According to telemetry data, about 90% of Coyote infections occur in Brazil, which has a significant impact on the financial cybersecurity of the region.
Coyote represents a significant shift in the development of banking Trojans, demonstrating the transition to using modern technologies and programming languages. The program highlights the growing sophistication in the threat landscape and the adaptation of attackers to current languages and tools for their cyber campaigns.
Kaspersky Lab specialists have discovered the Coyote Banking Trojan, which targets users of more than 60 banking institutions, mainly from Brazil. A distinctive feature of this malware is a complex infection chain that uses various advanced technologies, making Coyote stand out among other banking Trojans.
For distribution, Coyote uses the open-source Squirrel installer, using NodeJS and the relatively new multi-platform programming language Nim to complete the infection. It is noted that cybercriminals are increasingly resorting to the use of less popular and cross-platform languages, which is becoming a trend in the field of cyber threats.

Coyote Infection Chain
The trojan uses the Squirrel tool to install and update Windows applications, hiding its boot loader under the guise of an update. Launched via Squirrel, the NodeJS script executes obfuscated JavaScript code that copies all executable files from the local folder to the user's folder, and then runs the signed application from this directory, providing loading via DLL Sideloading.
Interestingly, to download the last stage of the Trojan, the Nim language is used, the purpose of which is to unpack and execute the executable file .NET in memory. Thus, the Trojan achieves stability by using an entry point that is activated every time the computer is rebooted.
Despite the lack of code obfuscation, Coyote uses string obfuscation with AES encryption to further hide its activity. To decrypt strings, the Trojan creates a table from base64-encoded data, using a randomly generated key and official .NET encryption interfaces.
To maintain activity, Coyote abuses Windows login scripts by checking for the presence and inserting the path to the signed application in the registry. The Trojan's goal is to monitor the victim's running apps while waiting for access to a banking app or website.
When the banking application is activated, the Trojan communicates with the Command and Control Server (C2) using SSL channels with mutual authentication, and transmits the collected information, including the machine name, GUID, and the banking application used. In response, the server can send commands to perform various actions, including keylogging and creating screenshots. In addition, Coyota even requests PIN codes from bank cards and displays phishing pages to collect user credentials.
According to telemetry data, about 90% of Coyote infections occur in Brazil, which has a significant impact on the financial cybersecurity of the region.
Coyote represents a significant shift in the development of banking Trojans, demonstrating the transition to using modern technologies and programming languages. The program highlights the growing sophistication in the threat landscape and the adaptation of attackers to current languages and tools for their cyber campaigns.

