Carding
Professional
- Messages
- 2,870
- Reaction score
- 2,491
- Points
- 113
The published PoC exploit indicates an error by the VMware developers in the product authentication system.
The Summoning Team presented the PoC code (Proof of Concept) of a recently discovered and resolved critical vulnerability in the VMware Aria Operations for Networks system (formerly known as vRealize Network Insight).
Vulnerability CVE-2023-34039 (CVSS: 9.8) is described as bypassing authentication due to the lack of generating a unique cryptographic key and allows an attacker with network access to Aria Operations for Networks to bypass SSH authentication and gain access to the system's CLI.
According to the Summoning Team, the main cause of the vulnerability is a bash script containing the "refresh_ssh_keys ()" method, which is responsible for overwriting the current SSH keys for support and ubuntu users in the "authorized_keys"file. As the Summoning Team explained, SSH authentication works, but no new keys are generated. In versions 6.0 to 6.10, the keys were hardcoded.
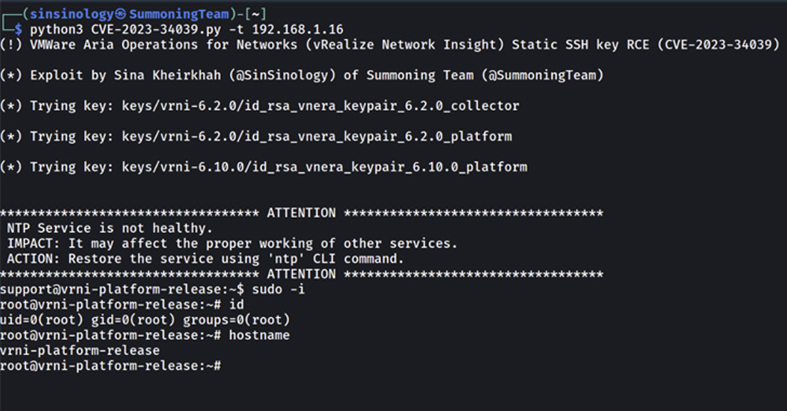
VMware Aria Operations for Networks PoC exploit
The latest patches from VMware also address the vulnerability CVE-2023-20890, which allows an attacker with administrative access to write files to arbitrary locations and execute remote code. Thus, a hacker can use the PoC to gain administrative access to the device and exploit the vulnerability to execute arbitrary code.
In June, VMware reported that a critical vulnerability in Aria Operations for Networks was actively exploited by cybercriminals. The CVE-2023-20887 bug allows an attacker with network access to perform a Command Injection attack and perform remote code execution on a device with a vulnerable product.
The Summoning Team presented the PoC code (Proof of Concept) of a recently discovered and resolved critical vulnerability in the VMware Aria Operations for Networks system (formerly known as vRealize Network Insight).
Vulnerability CVE-2023-34039 (CVSS: 9.8) is described as bypassing authentication due to the lack of generating a unique cryptographic key and allows an attacker with network access to Aria Operations for Networks to bypass SSH authentication and gain access to the system's CLI.
According to the Summoning Team, the main cause of the vulnerability is a bash script containing the "refresh_ssh_keys ()" method, which is responsible for overwriting the current SSH keys for support and ubuntu users in the "authorized_keys"file. As the Summoning Team explained, SSH authentication works, but no new keys are generated. In versions 6.0 to 6.10, the keys were hardcoded.

VMware Aria Operations for Networks PoC exploit
The latest patches from VMware also address the vulnerability CVE-2023-20890, which allows an attacker with administrative access to write files to arbitrary locations and execute remote code. Thus, a hacker can use the PoC to gain administrative access to the device and exploit the vulnerability to execute arbitrary code.
In June, VMware reported that a critical vulnerability in Aria Operations for Networks was actively exploited by cybercriminals. The CVE-2023-20887 bug allows an attacker with network access to perform a Command Injection attack and perform remote code execution on a device with a vulnerable product.

