Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,322
- Points
- 113
The Windows registry has become the Achilles heel of the popular email client.
Recently, TrustedSec introduced a new tool for attacking Microsoft Outlook, called "Specula". This tool allows attackers to execute code remotely using Outlook as a Command and control (C2) platform.
Specula is based on the vulnerability CVE-2017-11774, which was patched by Microsoft in October 2017. This security flaw allows you to bypass Outlook's security mechanisms and create a custom home page using WebView.
According to Microsoft, attackers can provide specially created documents that exploit this vulnerability. Opening such documents by users may compromise the system.
Despite patching the vulnerability and removing the interface for displaying Outlook home pages, attackers can still create malicious pages by changing Windows registry values, even on the latest versions of Office 365.
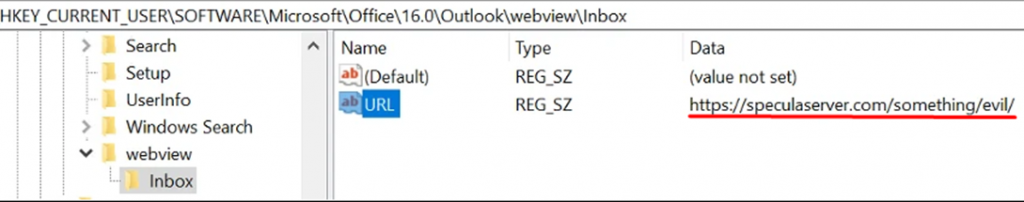
Specula works in the context of Outlook, installing a custom home page through registry keys that point to an external site controlled by attackers. These keys can be found in the registry key " HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\WebView\".
Attackers can use specially created Outlook pages to run VBScript files, which allows them to execute arbitrary commands on compromised systems. TrustedSec notes that this method has been successfully applied to access hundreds of customers, despite having the latest knowledge in digital hygiene and taking preventive measures.
When a custom home page is installed via registry keys, Outlook loads and displays the HTML page instead of standard content such as mail or calendar. From this page, you can run VBScript or JScript with the same privileges as running scripts via cscript or wscript.
For initial registry configuration, the device must be compromised, but after that, attackers can use this method to save access and distribute it to other systems. Since the process "outlook.exe" it is trusted, which makes it easier to bypass existing security features.
Five years ago, the US Cybersecurity Command (US CyberCom) warned that the vulnerability CVE-2017-11774 was used to attack US government agencies. Security researchers from the Chronicle, FireEye, and Palo Alto Networks later linked the attacks to the Iranian hacker group APT33.
FireEye reported that it first observed the use of CVE-2017-11774 by the APT34 group in June 2018, after which APT33 launched a larger campaign in July 2018, which lasted at least a year.
Source
Recently, TrustedSec introduced a new tool for attacking Microsoft Outlook, called "Specula". This tool allows attackers to execute code remotely using Outlook as a Command and control (C2) platform.
Specula is based on the vulnerability CVE-2017-11774, which was patched by Microsoft in October 2017. This security flaw allows you to bypass Outlook's security mechanisms and create a custom home page using WebView.
According to Microsoft, attackers can provide specially created documents that exploit this vulnerability. Opening such documents by users may compromise the system.
Despite patching the vulnerability and removing the interface for displaying Outlook home pages, attackers can still create malicious pages by changing Windows registry values, even on the latest versions of Office 365.
Specula works in the context of Outlook, installing a custom home page through registry keys that point to an external site controlled by attackers. These keys can be found in the registry key " HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\WebView\".

Attackers can use specially created Outlook pages to run VBScript files, which allows them to execute arbitrary commands on compromised systems. TrustedSec notes that this method has been successfully applied to access hundreds of customers, despite having the latest knowledge in digital hygiene and taking preventive measures.
When a custom home page is installed via registry keys, Outlook loads and displays the HTML page instead of standard content such as mail or calendar. From this page, you can run VBScript or JScript with the same privileges as running scripts via cscript or wscript.
For initial registry configuration, the device must be compromised, but after that, attackers can use this method to save access and distribute it to other systems. Since the process "outlook.exe" it is trusted, which makes it easier to bypass existing security features.
Five years ago, the US Cybersecurity Command (US CyberCom) warned that the vulnerability CVE-2017-11774 was used to attack US government agencies. Security researchers from the Chronicle, FireEye, and Palo Alto Networks later linked the attacks to the Iranian hacker group APT33.
FireEye reported that it first observed the use of CVE-2017-11774 by the APT34 group in June 2018, after which APT33 launched a larger campaign in July 2018, which lasted at least a year.
Source

