Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,198
- Points
- 113
How the BOINC platform moved from scientific computing to a cybercrime tool.
Huntress report that the malicious JavaScript loader SocGholish is used to deliver the AsyncRAT Trojan using the open-source project for computing BOINC.
BOINC (Berkeley Open Infrastructure Network Computing Client) is an open platform for "voluntary computing" supported by the University of California, Berkeley for performing high-performance computing in research projects using volunteers ' home computers that have the corresponding application installed. At its core, BOINC is similar to a cryptominer-the platform uses computer resources to work and rewards users with the Gridcoin cryptocurrency developed specifically for this purpose.
In the detected campaign, malicious BOINC installations are configured to connect to the attacker's domains (rosettahome[.] cn and rosettahome [.] top), which serve as C2 servers for collecting host data, transmitting payloads, and sending further commands. As of July 15, 10,032 clients are connected to the two domains.
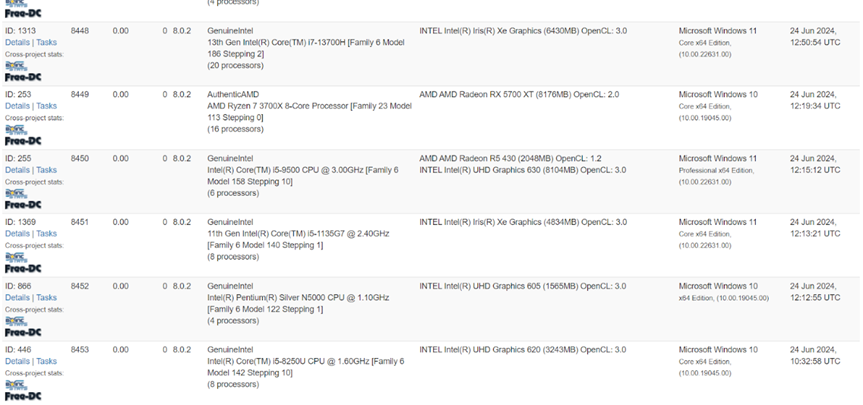
Hosts connected to the malicious BOINC server shown on the server administrator's site
Although experts did not observe any subsequent activity on the infected hosts, it is assumed that connections can be sold to other attackers, which creates the possibility of using the hosts as starting points for the introduction of ransomware.
A typical sequence of SocGholish attacks begins when users visit hacked websites that offer to download a fake browser update. After running the" update", the malware downloads additional components to the infected machines.
In this case, the JavaScript loader activates two separate chains: one leads to the installation of the Fileless malware version of AsyncRAT, and the other leads to the installation of BOINC. The BOINC app is masquerading as "SecurityHealthService.exe" or "trustedinstaller.exe" to avoid detection and maintain its presence via a scheduled task. The BOINC project has already noticed the use of its platform for malicious purposes and is actively investigating the problem. Cases of abuse have been recorded since June 26, 2024.
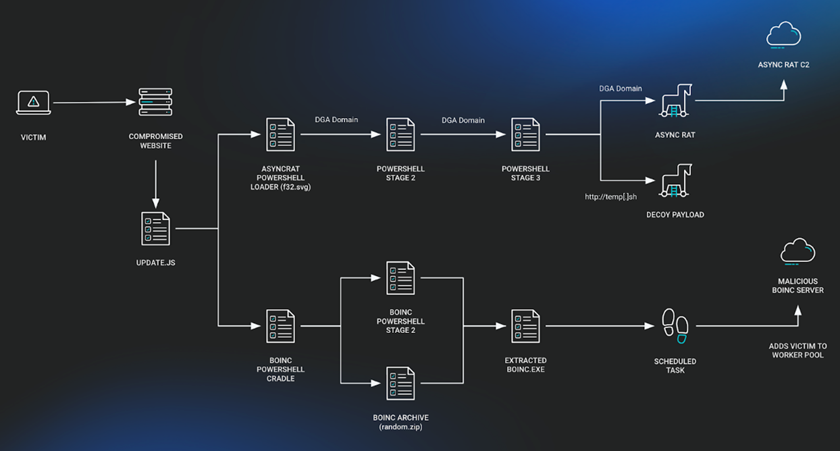
Infection chain
AsyncRAT has many features, such as keystroke logging, audio/video recording, information theft, remote desktop management, password recovery, launching a remote shell, payload delivery, and others.
Active connections of infected clients to malicious BOINC servers pose a significant risk. Attackers can use connections to execute any commands or install malware, which can lead to privilege escalation or spread across the network and compromise the entire domain.
Source
Huntress report that the malicious JavaScript loader SocGholish is used to deliver the AsyncRAT Trojan using the open-source project for computing BOINC.
BOINC (Berkeley Open Infrastructure Network Computing Client) is an open platform for "voluntary computing" supported by the University of California, Berkeley for performing high-performance computing in research projects using volunteers ' home computers that have the corresponding application installed. At its core, BOINC is similar to a cryptominer-the platform uses computer resources to work and rewards users with the Gridcoin cryptocurrency developed specifically for this purpose.
In the detected campaign, malicious BOINC installations are configured to connect to the attacker's domains (rosettahome[.] cn and rosettahome [.] top), which serve as C2 servers for collecting host data, transmitting payloads, and sending further commands. As of July 15, 10,032 clients are connected to the two domains.

Hosts connected to the malicious BOINC server shown on the server administrator's site
Although experts did not observe any subsequent activity on the infected hosts, it is assumed that connections can be sold to other attackers, which creates the possibility of using the hosts as starting points for the introduction of ransomware.
A typical sequence of SocGholish attacks begins when users visit hacked websites that offer to download a fake browser update. After running the" update", the malware downloads additional components to the infected machines.
In this case, the JavaScript loader activates two separate chains: one leads to the installation of the Fileless malware version of AsyncRAT, and the other leads to the installation of BOINC. The BOINC app is masquerading as "SecurityHealthService.exe" or "trustedinstaller.exe" to avoid detection and maintain its presence via a scheduled task. The BOINC project has already noticed the use of its platform for malicious purposes and is actively investigating the problem. Cases of abuse have been recorded since June 26, 2024.

Infection chain
AsyncRAT has many features, such as keystroke logging, audio/video recording, information theft, remote desktop management, password recovery, launching a remote shell, payload delivery, and others.
Active connections of infected clients to malicious BOINC servers pose a significant risk. Attackers can use connections to execute any commands or install malware, which can lead to privilege escalation or spread across the network and compromise the entire domain.
Source
