chushpan
Professional
- Messages
- 1,356
- Reaction score
- 1,632
- Points
- 113
The content of the article:
Traffic analysis is the most important step in penetration testing (or even hacking). In packets transmitted over the network, you can find a lot of interesting things, for example, passwords for accessing various resources and other valuable data. To intercept and analyze traffic, sniffers are used, of which mankind has come up with a great variety. Today we will talk about the most popular sniffers for Windows.
Theoretically, it is possible to collect all packets in the local network segment where the sniffer is installed, but in this case there will be too much data for subsequent analysis, and the log files will quickly swell to completely indecent sizes. Or you can configure the application in such a way that it catches traffic only from certain protocols (HTTP, POP3, IMAP, FTP, Telnet) or analyzes only the first 100 bytes of each packet, where the most interesting things are usually contained: the address of the target host, logins and passwords. Modern sniffers can also listen to encrypted traffic.
Traffic analyzers are often used for “peaceful” purposes - to diagnose a network, identify and troubleshoot problems, detect malware, or to find out what users are doing and what sites they visit. But it is precisely when investigating the security of a network perimeter or penetration testing that a sniffer is an indispensable tool for reconnaissance and data collection. There are sniffers for various operating systems; in addition, similar software can be installed on a router and examine all traffic passing through it. Today we will talk about the most common popular traffic analyzers for the Microsoft Windows platform.
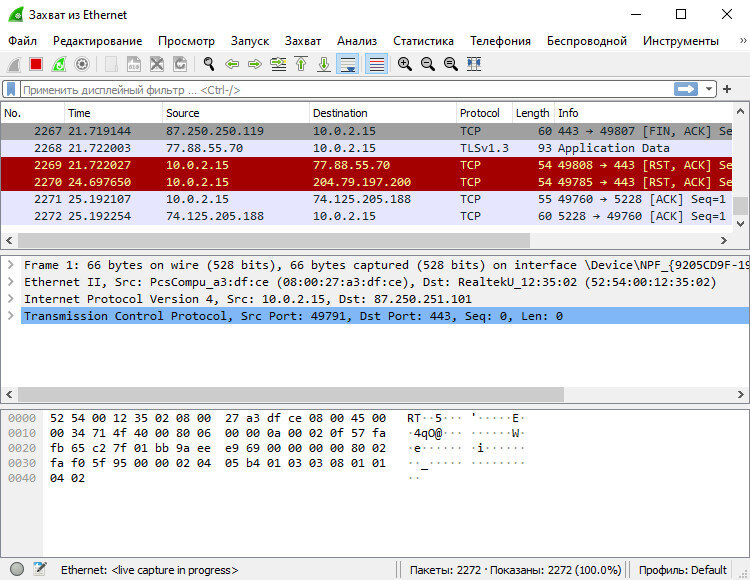
Everyone probably knows what Wireshark is.
This analyzer has a Russian-language interface and can work with a large number of network protocols (it makes no sense to list them all here: the full list can be found on the manufacturer’s website). In Wireshark, you can disassemble each intercepted packet into parts, view its headers and contents. The application has a very convenient mechanism for navigating through packages, including various algorithms for searching and filtering them, and has a powerful statistics collection mechanism. Saved data can be exported to different formats; in addition, it is possible to automate the work of Wireshark using Lua scripts and connect additional (even independently developed) modules for parsing and analyzing traffic.
In addition to Ethernet, the sniffer can intercept traffic from wireless networks (802.11 standards and Bluetooth protocol). The tool allows you to analyze IP telephony traffic and restore TCP streams; analysis of tunneled traffic is supported. Wireshark does an excellent job of decoding protocols, but to understand the results of this decoding, you must, of course, have a good understanding of their structure.
The disadvantages of Wireshark include the fact that the reconstructed streams are not considered by the program as a single memory buffer, which makes their subsequent processing difficult. When analyzing tunneled traffic, several parsing modules are used at once, and each subsequent one in the program window replaces the result of the previous one - as a result, analyzing traffic in multi-level tunnels becomes impossible.
In general, Wireshark is not just a popular, but a very good product that allows you to track the contents of packets traveling on the network, their transmission speed, and find “problem spots” in the network infrastructure. But unlike commercial applications, there are no convenient visualization tools. In addition, using Wireshark it is not so easy, for example, to catch logins and passwords from traffic, and this is one of the typical tasks in penetration testing.
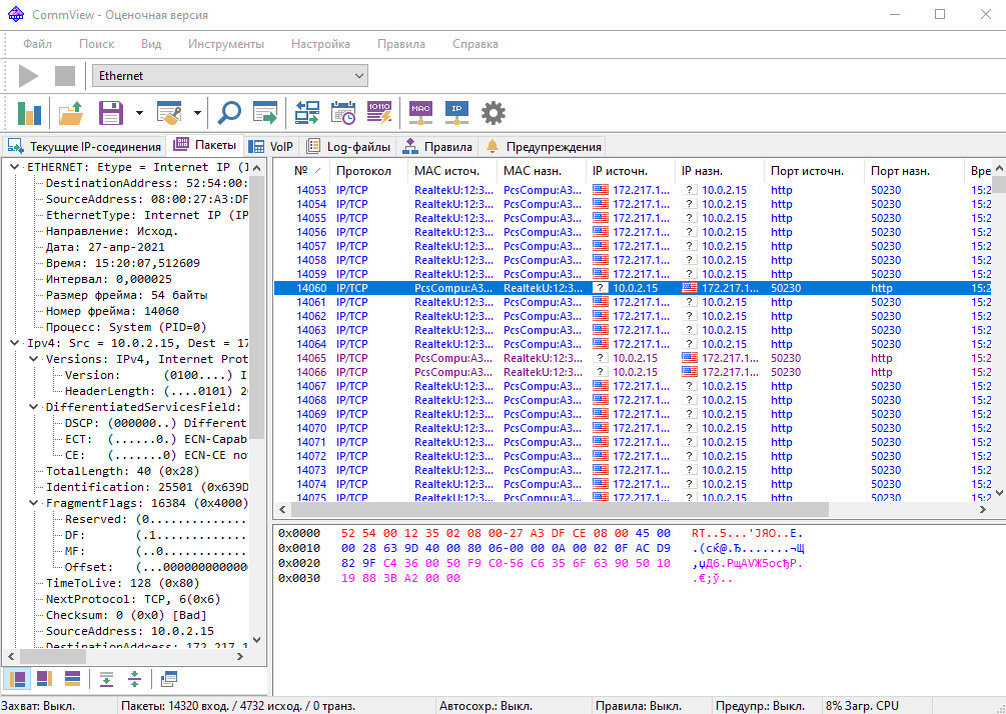
CommView is a well-deserved “veteran” in the world of sniffers
The program has a Russian-language interface, which can be a determining factor when choosing a sniffer for users who do not speak English. The main advantage of CommView is the ability to flexibly configure packet filtering rules: you can select individual protocols that the application will monitor, sort packets by a number of criteria, for example, by size or header. The range of supported protocols is also very large: the sniffer can work with the most common application protocols, as well as reconstruct a TCP session and UDP stream. At the same time, CommView allows you to analyze traffic down to the lowest level protocol packets - TCP, UDP, ICMP, as well as view “raw” data. The program shows the headers of intercepted packets and collects detailed IP traffic statistics. Saved data can be exported to 12 different formats, ranging from .txt and .csv to files from other analyzers like Wireshark.
In addition to traffic on the network card, CommView can monitor VPN connections, as well as traffic passing through modems - analog, mobile, ADSL, ISDN and others, for which a special driver is installed in the system. It is possible to intercept VoIP traffic and SIP telephony sessions. The application includes a packet generator that can be used to send a packet of a specified length, with arbitrary headers and content, to a given Ethernet interface. There is also a fairly convenient log file viewer that allows you to open log files in a separate sniffer window and search their contents.
Toolza, without a doubt, is extremely convenient and useful, if not for the “biting” prices for a license. For a professional pentester, the purchase of such a tool will certainly be justified, but in order to “look at the network” once, you can look for alternative - cheaper or free solutions.
In its work, Intercepter-NG uses the NPcap utility, a portable version of which, according to the developers, it carries with itself. However, practice has shown that they either forgot to put it there, or it does not work in Windows 10 - to launch the sniffer, I had to download NPcap from the site https://nmap.org/npcap/ and install it manually.
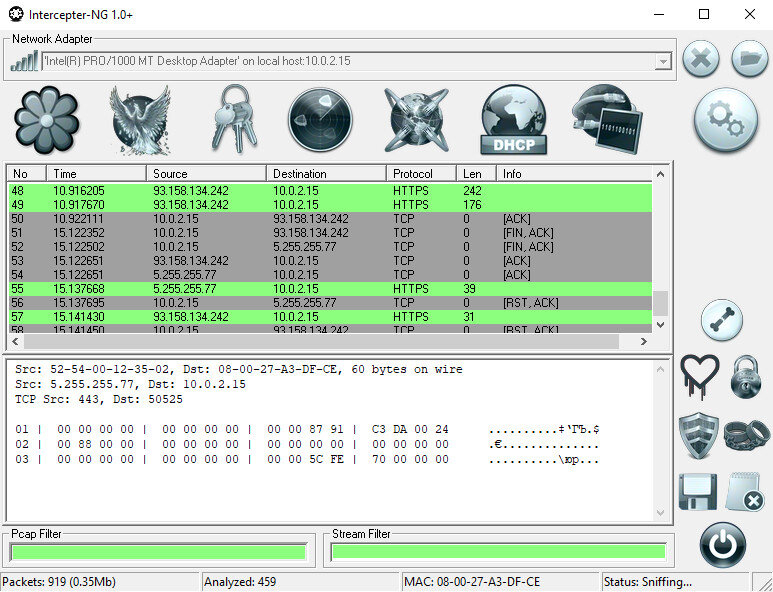
Intercepter-NG
Intercepter-NG has a pretty nice user interface and allows you to view traffic in several modes. There is a regular view of packets and their contents, in which you can filter packets using pcap rules or use the Follow TCP stream function for a detailed analysis of a session. There is a Messengers Mode, in which the tool tries to intercept traffic from instant messengers - primarily ICQ, MSN, Yahoo and AIM, but there is support for the Jabber protocol. With Telegram, the trick failed: the sniffer simply didn’t see it.
There is Passwords Mode, in which the screen displays logins and passwords captured from traffic and transmitted via FTP, HTTP, SMTP, POP3, IMAP, LDAP, Telnet and others. Resurrection mode allows you to recover files transferred via HTTP, FTP, SMB, IMAP, POP3 and SMTP - and only files from completed TCP sessions are successfully recovered.
Intercepter-NG includes additional and very useful tools. This is a simple DHCP server, a NAT service that allows you to broadcast ICMP/UDP/TCP packets between different Ethernet segments of the network. There are several network scanners: ARP, DHCP, “smart” search for gateways is implemented. Another useful tool is a module for organizing MiTM attacks. Spoofing methods are supported (with support for DNS/NBNS/LLMNR protocols), ICMP Redirect, DNS over ICMP Redirect, SSL MiTM, SSLStrip and some others.
Using the program, you can scan a specified range of ports in search of applications running on them, and analyze the protocols associated with these ports. You can switch the sniffer to extreme mode, in which it will intercept all TCP packets without checking ports, which will allow you to detect applications on the network running on non-standard ports overridden by the administrator. However, in this mode the application slows down mercilessly and periodically freezes.
The current version of Intercepter-NG has a built-in tool for exploiting the Heartbleed vulnerability - an error in the OpenSSL cryptographic software, which can be used to unauthorizedly read memory on the server or client, including to extract the server’s private key. The package also included a brute force tool and a multi-threaded vulnerability scanner, X-Scan. In other words, from a simple network analysis application, Intercepter-NG is gradually turning into a kind of harvester, allowing you to scan the network for open ports and unpatched vulnerabilities without leaving the cash register, intercept logins and passwords, and hack something.
The disadvantages of Intercepter-NG include the fact that the program is recognized as malicious by Kaspersky antivirus and Windows Defender, which is why it is killed at the stage of downloading from the manufacturer’s website. So to work with the sniffer you will have to disable antivirus software, but this is a fairly modest price to pay for the opportunity to use such a multifunctional tool.
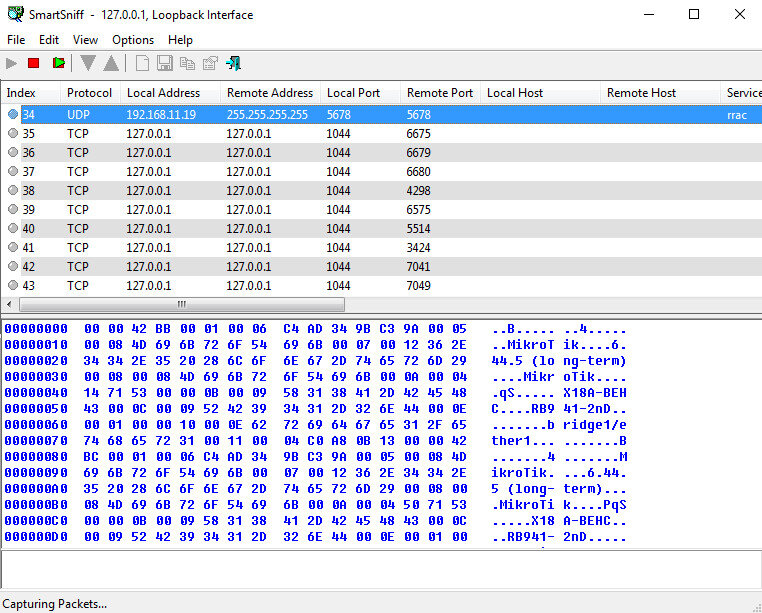
SmartSniff from Nirsoft
The project was initially developed for Windows 2000/XP (which, in general, is noticeable in its interface), but is still alive today - the latest version of the sniffer is dated 2018. The utility allows you to intercept traffic passing through the local machine and view the contents of packets - it actually can’t do anything else.
Actually, Burp is not at all universal as a sniffer - it can only monitor traffic between the browser and a remote web application using an intercepting proxy, for which to work with the HTTPS protocol you need to install an additional certificate on the system. But for certain purposes this may be sufficient.
Burp Suite Community Edition
Burp intercepts all packets that the browser sends and receives and, accordingly, allows you to analyze the traffic of various web applications, including online messengers or social networks. If the infrastructure being examined by a pentester contains services running via HTTP or HTTPS, there is probably no better tool for testing them. But using Burp only as a sniffer for HTTP/HTTPS traffic is like transporting potatoes from a summer cottage in a Lamborghini: it is intended for completely different tasks.
(c) https://xakep.ru/2021/05/17/sniffers-windows/
- Theory
- Wireshark
- CommView
- Intercepter-NG
- SmartSniff
- tcpdump
- Burp Suite
- Conclusion
Traffic analysis is the most important step in penetration testing (or even hacking). In packets transmitted over the network, you can find a lot of interesting things, for example, passwords for accessing various resources and other valuable data. To intercept and analyze traffic, sniffers are used, of which mankind has come up with a great variety. Today we will talk about the most popular sniffers for Windows.
THEORY
To intercept traffic, analyzers can use packet redirection or use the so-called Promiscuous mode - an “indiscriminate” mode of operation of the network adapter, in which filtering is disabled and the adapter accepts all packets regardless of who they are addressed to. In a normal situation, the Ethernet interface filters packets at the data link layer. With this filtering, the network card accepts only broadcast requests and packets whose MAC address in the header matches its own. In Promiscuous mode, all other packets are not discarded, which allows the sniffer to intercept data.Theoretically, it is possible to collect all packets in the local network segment where the sniffer is installed, but in this case there will be too much data for subsequent analysis, and the log files will quickly swell to completely indecent sizes. Or you can configure the application in such a way that it catches traffic only from certain protocols (HTTP, POP3, IMAP, FTP, Telnet) or analyzes only the first 100 bytes of each packet, where the most interesting things are usually contained: the address of the target host, logins and passwords. Modern sniffers can also listen to encrypted traffic.
Traffic analyzers are often used for “peaceful” purposes - to diagnose a network, identify and troubleshoot problems, detect malware, or to find out what users are doing and what sites they visit. But it is precisely when investigating the security of a network perimeter or penetration testing that a sniffer is an indispensable tool for reconnaissance and data collection. There are sniffers for various operating systems; in addition, similar software can be installed on a router and examine all traffic passing through it. Today we will talk about the most common popular traffic analyzers for the Microsoft Windows platform.
WIRESHARK
- Manufacturer: Wireshark Foundation
- Website: https://www.wireshark.org
- License: free
Everyone probably knows what Wireshark is.
This analyzer has a Russian-language interface and can work with a large number of network protocols (it makes no sense to list them all here: the full list can be found on the manufacturer’s website). In Wireshark, you can disassemble each intercepted packet into parts, view its headers and contents. The application has a very convenient mechanism for navigating through packages, including various algorithms for searching and filtering them, and has a powerful statistics collection mechanism. Saved data can be exported to different formats; in addition, it is possible to automate the work of Wireshark using Lua scripts and connect additional (even independently developed) modules for parsing and analyzing traffic.
In addition to Ethernet, the sniffer can intercept traffic from wireless networks (802.11 standards and Bluetooth protocol). The tool allows you to analyze IP telephony traffic and restore TCP streams; analysis of tunneled traffic is supported. Wireshark does an excellent job of decoding protocols, but to understand the results of this decoding, you must, of course, have a good understanding of their structure.
The disadvantages of Wireshark include the fact that the reconstructed streams are not considered by the program as a single memory buffer, which makes their subsequent processing difficult. When analyzing tunneled traffic, several parsing modules are used at once, and each subsequent one in the program window replaces the result of the previous one - as a result, analyzing traffic in multi-level tunnels becomes impossible.
In general, Wireshark is not just a popular, but a very good product that allows you to track the contents of packets traveling on the network, their transmission speed, and find “problem spots” in the network infrastructure. But unlike commercial applications, there are no convenient visualization tools. In addition, using Wireshark it is not so easy, for example, to catch logins and passwords from traffic, and this is one of the typical tasks in penetration testing.
COMMVIEW
- Manufacturer: TamoSoft
- Website: https://www.tamos.ru/products/commview/
- License: paid, license purchase or subscription
CommView is a well-deserved “veteran” in the world of sniffers
The program has a Russian-language interface, which can be a determining factor when choosing a sniffer for users who do not speak English. The main advantage of CommView is the ability to flexibly configure packet filtering rules: you can select individual protocols that the application will monitor, sort packets by a number of criteria, for example, by size or header. The range of supported protocols is also very large: the sniffer can work with the most common application protocols, as well as reconstruct a TCP session and UDP stream. At the same time, CommView allows you to analyze traffic down to the lowest level protocol packets - TCP, UDP, ICMP, as well as view “raw” data. The program shows the headers of intercepted packets and collects detailed IP traffic statistics. Saved data can be exported to 12 different formats, ranging from .txt and .csv to files from other analyzers like Wireshark.
In addition to traffic on the network card, CommView can monitor VPN connections, as well as traffic passing through modems - analog, mobile, ADSL, ISDN and others, for which a special driver is installed in the system. It is possible to intercept VoIP traffic and SIP telephony sessions. The application includes a packet generator that can be used to send a packet of a specified length, with arbitrary headers and content, to a given Ethernet interface. There is also a fairly convenient log file viewer that allows you to open log files in a separate sniffer window and search their contents.
Toolza, without a doubt, is extremely convenient and useful, if not for the “biting” prices for a license. For a professional pentester, the purchase of such a tool will certainly be justified, but in order to “look at the network” once, you can look for alternative - cheaper or free solutions.
INTERCEPTER-NG
- Manufacturer: unknown
- Website: http://sniff.su
- License: free
In its work, Intercepter-NG uses the NPcap utility, a portable version of which, according to the developers, it carries with itself. However, practice has shown that they either forgot to put it there, or it does not work in Windows 10 - to launch the sniffer, I had to download NPcap from the site https://nmap.org/npcap/ and install it manually.
Intercepter-NG
Intercepter-NG has a pretty nice user interface and allows you to view traffic in several modes. There is a regular view of packets and their contents, in which you can filter packets using pcap rules or use the Follow TCP stream function for a detailed analysis of a session. There is a Messengers Mode, in which the tool tries to intercept traffic from instant messengers - primarily ICQ, MSN, Yahoo and AIM, but there is support for the Jabber protocol. With Telegram, the trick failed: the sniffer simply didn’t see it.
There is Passwords Mode, in which the screen displays logins and passwords captured from traffic and transmitted via FTP, HTTP, SMTP, POP3, IMAP, LDAP, Telnet and others. Resurrection mode allows you to recover files transferred via HTTP, FTP, SMB, IMAP, POP3 and SMTP - and only files from completed TCP sessions are successfully recovered.
Intercepter-NG includes additional and very useful tools. This is a simple DHCP server, a NAT service that allows you to broadcast ICMP/UDP/TCP packets between different Ethernet segments of the network. There are several network scanners: ARP, DHCP, “smart” search for gateways is implemented. Another useful tool is a module for organizing MiTM attacks. Spoofing methods are supported (with support for DNS/NBNS/LLMNR protocols), ICMP Redirect, DNS over ICMP Redirect, SSL MiTM, SSLStrip and some others.
Using the program, you can scan a specified range of ports in search of applications running on them, and analyze the protocols associated with these ports. You can switch the sniffer to extreme mode, in which it will intercept all TCP packets without checking ports, which will allow you to detect applications on the network running on non-standard ports overridden by the administrator. However, in this mode the application slows down mercilessly and periodically freezes.
The current version of Intercepter-NG has a built-in tool for exploiting the Heartbleed vulnerability - an error in the OpenSSL cryptographic software, which can be used to unauthorizedly read memory on the server or client, including to extract the server’s private key. The package also included a brute force tool and a multi-threaded vulnerability scanner, X-Scan. In other words, from a simple network analysis application, Intercepter-NG is gradually turning into a kind of harvester, allowing you to scan the network for open ports and unpatched vulnerabilities without leaving the cash register, intercept logins and passwords, and hack something.
The disadvantages of Intercepter-NG include the fact that the program is recognized as malicious by Kaspersky antivirus and Windows Defender, which is why it is killed at the stage of downloading from the manufacturer’s website. So to work with the sniffer you will have to disable antivirus software, but this is a fairly modest price to pay for the opportunity to use such a multifunctional tool.
SMARTSNIF
- Manufacturer: Nirsoft
- Website: http://www.nirsoft.net/utils/smsniff.html
- License: free
SmartSniff from Nirsoft
The project was initially developed for Windows 2000/XP (which, in general, is noticeable in its interface), but is still alive today - the latest version of the sniffer is dated 2018. The utility allows you to intercept traffic passing through the local machine and view the contents of packets - it actually can’t do anything else.
TCPDUMP
- Manufacturer: Tcpdump Group
- Website: tcpdump.org
- License: Free (modified BSD license)
BURP SUITE
- Manufacturer: Portswigger
- Website: https://portswigger.net/burp
- License: free (Community Edition)
Actually, Burp is not at all universal as a sniffer - it can only monitor traffic between the browser and a remote web application using an intercepting proxy, for which to work with the HTTPS protocol you need to install an additional certificate on the system. But for certain purposes this may be sufficient.
Burp Suite Community Edition
Burp intercepts all packets that the browser sends and receives and, accordingly, allows you to analyze the traffic of various web applications, including online messengers or social networks. If the infrastructure being examined by a pentester contains services running via HTTP or HTTPS, there is probably no better tool for testing them. But using Burp only as a sniffer for HTTP/HTTPS traffic is like transporting potatoes from a summer cottage in a Lamborghini: it is intended for completely different tasks.
CONCLUSION
To paraphrase a popular song, there are different sniffers - and each of them is better suited for its tasks. For researching web applications and intercepting local HTTP traffic, there is nothing better than Burp Suite; for finding problem areas in your own local network or getting a list of remote hosts accessed by a program, Wireshark is perfect. And for attacks on network infrastructure, you can use Intercepter-NG - this tool has a whole set of useful tools for penetration testing.(c) https://xakep.ru/2021/05/17/sniffers-windows/

