CarderPlanet
Professional
Who and how steals money from bank cards and how to protect yourself on the Internet? "Paper" spoke with a former carder - a man who was engaged in online fraud with bank cards.
Let's say a person has issued a card at a bank in order to pay via the Internet and immediately went to buy any rubbish. He goes to a dubious perfume store, buys them, they arrived safely - and everything seems to be fine. But the store may not be very secure and retain all the card data. There are two ways further. Either the site will be hacked and gain access to the map database, or the store employees themselves will sell or merge it.
The average price for a credit card varies: for American cards - from 1 to 2 dollars, for Europeans - from 2 to 5, if some rare countries - from 5 to 10
The price rises depending on what data you receive. The more information about the user, the more you can exploit someone else's card. Usually the attacker has special electronic systems: virtual machines or rented servers in other countries. That is, if the card belongs to an American, American servers are used to simulate that the person is buying something in the States.
Bank cards are typically used for petty fraud: $ 10 to $ 200
With your card details, you can pay bills on the Internet, top up your phone and buy almost anything. Bank cards, as a rule, are used for petty fraud: from 10 to 200 dollars, but sometimes they "buy" from one card for more than 1000 dollars.

The most dangerous and profitable type of carding is the one that works with real cards.
To make more purchases and cash out, groups of so-called "drops" are created: these are people who unknowingly participate in fraud. They are found on foreign job search sites or through spam and Internet advertising. They are told something like: "We are representatives of a company from Zimbabwe and want to open a branch in your city - phones and laptops will come for poor children."
A laptop that costs $ 1000 will cost a carder $ 300-400, and he will sell it at market price.
According to the terms, drops can keep one laptop for themselves, and they must send all the rest wherever they are told. Equipment and other goods from stolen credit cards are ordered to their addresses. Then they send them through the network of the same dummies. For example, a laptop that costs $ 1000 will cost a carder $ 300-400, and he will sell it at market price. I bought cards - 10 for $ 10 - and offered them to Russian users who could not buy games on the Steam digital distribution network of games. One game, taking into account the resources spent on it, cost 10 dollars at a real price of 20 and more.
Who is stealing money and how?
They use malicious programs to work with bank accounts. There are two types of Trojans: grabbers and form grabbing. Grabber Trojans simply steal all saved passwords. Gradually, the security system began to evolve: security questions appeared, additional data had to be entered - it became quite difficult to gain access to accounts. But smart people have come up with a phenomenal thing - form grabbers: the virus steals not only what is saved, but also what you enter.
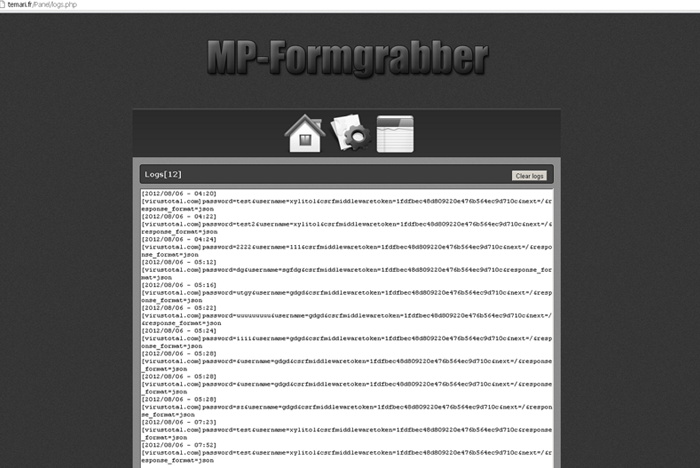
Formgrabbers steal not only what is saved, but also what you enter
It became even easier when it became possible to force the user to enter what is needed. Let's say you have a bank account with online access. You go there twice a week to top up your phone or pay your rent. These are not very large payments that do not empty your account. Some banks (mainly in Europe) have a TANITAN security system. When issuing a card and registering in online banking, the client receives a sheet containing from ten to one hundred passwords. Each of them contains from 4 to 8 characters. Whenever he enters the bank or conducts any financial transaction, the system asks to enter, for example, the 53rd password or the first (fourth, fifth, seventh) character of the 22nd password. At first, the system worked very well: the banks just wrote with boiling water because no one could steal anything.
It is the policy of banks that they do not look for the culprit if the write-offs are up to $ 5,000 from one account. It's cheaper for them to make up for the loss than to look for who stole the money
But still, there was a way to deceive this system. The Trojan simply entered the browser and injected its code into the final page. When all the data is entered, a huge pop-up appears, which says: "Security error, you entered the wrong code, please try again." The user, of course, enters the password again, because outwardly this is the same site with the same design. Then he safely enters his personal account, and everything is in place. But during this time, half of the money was gone, and he did not even notice.
How it works?
When the pop-up appeared, the real bank account page had already loaded. In fact, the client has already been allowed everywhere, but because of the malicious code, the page shows that he did not enter. In fact, the translation has already been generated, the necessary names have already been substituted and the virus is only waiting for the confirmation of the code. The user enters it, and the translation is carried out. Something is spinning on the screen, supposedly the page is loading. During this time, using ordinary mathematical formulas, the system calculates how much a person spends per week and how much it is desirable for him to leave so that in the next two or three days he does not notice the theft and can easily cash everything out. When the client returns, in the same way by changing the page, the transfers are removed from the transaction lists, and the balance looks intact. Carders are caught because of greed, carelessness and stupidity, or a human factor. The main reason is greed. The more you want to steal, the better they will look for you. It is the policy of banks that they do not look for the culprit if the write-offs are up to $ 5,000 from one account. It is cheaper for them to compensate for the loss than to look for who stole the money.
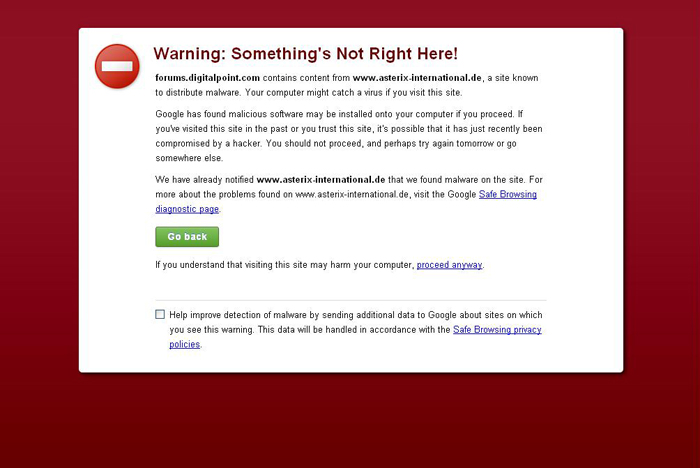
Do not go to questionable sites and believe the warnings of Google Chrome and FireFox
The most dangerous and profitable type of carding is the one that does not use virtual data, but works with real cards. For example, they take a card from a visitor in a cafe and pay. First, there is nothing stopping attackers from overwriting data and paying on the Internet. Secondly, nothing prevents them from using a skimmer - a device that stores data from magnetic tapes. It is put on an ATM or hand-made models are assembled. Criminals buy blank cards and a special machine that programs and writes new cards. By the way, in cashing out from credit cards, all drops are deliberate, they know what they are doing.
How to protect yourself?
Do not install questionable software, use licensed software. Do not go to questionable sites and believe the warnings from Google Chrome and FireFox. The warnings indicate that the page has a frame (that is, an additional page) with malicious content and you can get infected with a virus. On average, 5 to 30% of all visitors are infected. Get a separate card for online payment and top up it as needed. Do not pay with a bank card in questionable establishments. Try not to let your card out of sight.

| No Name Former carder In the past, I used the data of someone else's bank cards on the Internet, engaged in online fraud |
Let's say a person has issued a card at a bank in order to pay via the Internet and immediately went to buy any rubbish. He goes to a dubious perfume store, buys them, they arrived safely - and everything seems to be fine. But the store may not be very secure and retain all the card data. There are two ways further. Either the site will be hacked and gain access to the map database, or the store employees themselves will sell or merge it.
The average price for a credit card varies: for American cards - from 1 to 2 dollars, for Europeans - from 2 to 5, if some rare countries - from 5 to 10
The price rises depending on what data you receive. The more information about the user, the more you can exploit someone else's card. Usually the attacker has special electronic systems: virtual machines or rented servers in other countries. That is, if the card belongs to an American, American servers are used to simulate that the person is buying something in the States.
Bank cards are typically used for petty fraud: $ 10 to $ 200
With your card details, you can pay bills on the Internet, top up your phone and buy almost anything. Bank cards, as a rule, are used for petty fraud: from 10 to 200 dollars, but sometimes they "buy" from one card for more than 1000 dollars.

The most dangerous and profitable type of carding is the one that works with real cards.
To make more purchases and cash out, groups of so-called "drops" are created: these are people who unknowingly participate in fraud. They are found on foreign job search sites or through spam and Internet advertising. They are told something like: "We are representatives of a company from Zimbabwe and want to open a branch in your city - phones and laptops will come for poor children."
A laptop that costs $ 1000 will cost a carder $ 300-400, and he will sell it at market price.
According to the terms, drops can keep one laptop for themselves, and they must send all the rest wherever they are told. Equipment and other goods from stolen credit cards are ordered to their addresses. Then they send them through the network of the same dummies. For example, a laptop that costs $ 1000 will cost a carder $ 300-400, and he will sell it at market price. I bought cards - 10 for $ 10 - and offered them to Russian users who could not buy games on the Steam digital distribution network of games. One game, taking into account the resources spent on it, cost 10 dollars at a real price of 20 and more.
Who is stealing money and how?
They use malicious programs to work with bank accounts. There are two types of Trojans: grabbers and form grabbing. Grabber Trojans simply steal all saved passwords. Gradually, the security system began to evolve: security questions appeared, additional data had to be entered - it became quite difficult to gain access to accounts. But smart people have come up with a phenomenal thing - form grabbers: the virus steals not only what is saved, but also what you enter.

Formgrabbers steal not only what is saved, but also what you enter
It became even easier when it became possible to force the user to enter what is needed. Let's say you have a bank account with online access. You go there twice a week to top up your phone or pay your rent. These are not very large payments that do not empty your account. Some banks (mainly in Europe) have a TANITAN security system. When issuing a card and registering in online banking, the client receives a sheet containing from ten to one hundred passwords. Each of them contains from 4 to 8 characters. Whenever he enters the bank or conducts any financial transaction, the system asks to enter, for example, the 53rd password or the first (fourth, fifth, seventh) character of the 22nd password. At first, the system worked very well: the banks just wrote with boiling water because no one could steal anything.
It is the policy of banks that they do not look for the culprit if the write-offs are up to $ 5,000 from one account. It's cheaper for them to make up for the loss than to look for who stole the money
But still, there was a way to deceive this system. The Trojan simply entered the browser and injected its code into the final page. When all the data is entered, a huge pop-up appears, which says: "Security error, you entered the wrong code, please try again." The user, of course, enters the password again, because outwardly this is the same site with the same design. Then he safely enters his personal account, and everything is in place. But during this time, half of the money was gone, and he did not even notice.
How it works?
When the pop-up appeared, the real bank account page had already loaded. In fact, the client has already been allowed everywhere, but because of the malicious code, the page shows that he did not enter. In fact, the translation has already been generated, the necessary names have already been substituted and the virus is only waiting for the confirmation of the code. The user enters it, and the translation is carried out. Something is spinning on the screen, supposedly the page is loading. During this time, using ordinary mathematical formulas, the system calculates how much a person spends per week and how much it is desirable for him to leave so that in the next two or three days he does not notice the theft and can easily cash everything out. When the client returns, in the same way by changing the page, the transfers are removed from the transaction lists, and the balance looks intact. Carders are caught because of greed, carelessness and stupidity, or a human factor. The main reason is greed. The more you want to steal, the better they will look for you. It is the policy of banks that they do not look for the culprit if the write-offs are up to $ 5,000 from one account. It is cheaper for them to compensate for the loss than to look for who stole the money.

Do not go to questionable sites and believe the warnings of Google Chrome and FireFox
The most dangerous and profitable type of carding is the one that does not use virtual data, but works with real cards. For example, they take a card from a visitor in a cafe and pay. First, there is nothing stopping attackers from overwriting data and paying on the Internet. Secondly, nothing prevents them from using a skimmer - a device that stores data from magnetic tapes. It is put on an ATM or hand-made models are assembled. Criminals buy blank cards and a special machine that programs and writes new cards. By the way, in cashing out from credit cards, all drops are deliberate, they know what they are doing.
How to protect yourself?
Do not install questionable software, use licensed software. Do not go to questionable sites and believe the warnings from Google Chrome and FireFox. The warnings indicate that the page has a frame (that is, an additional page) with malicious content and you can get infected with a virus. On average, 5 to 30% of all visitors are infected. Get a separate card for online payment and top up it as needed. Do not pay with a bank card in questionable establishments. Try not to let your card out of sight.
