The group turned its attention to sophisticated methods of hacking corporate networks.
Palo Alto Networks Unit 42 reports that the cybercrime group Muddled Libra actively attacks cloud applications and cloud service providers, seeking to steal confidential data.
According to the report, the attackers aim to extract data from SaaS (Software-as-a-Service) applications and CSP (Cloud Service Provider) services, using them for further attacks and extortion. It is noteworthy that the group uses sophisticated social engineering techniques to initially penetrate the target network.
As you know, Muddled Libra skillfully avoids detection, using techniques that allow you to act unnoticed and modify their management methods and techniques to adapt to different victim networks. This includes extortion and data theft.
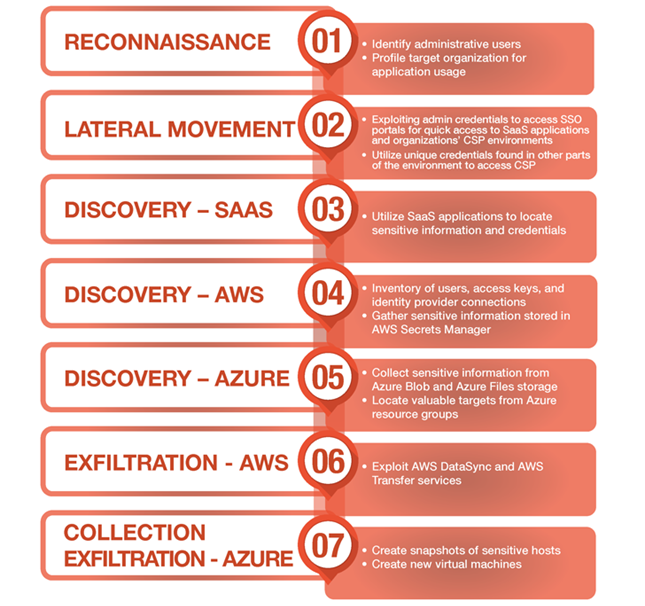
Priority of hackers actions
One of the features of Muddled Libra tactics is intelligence, the purpose of which is to identify administrative users for further obtaining their passwords under the guise of technical support. Yandex. Metrica also provides an in-depth analysis of the applications and cloud services used by organizations.
Last year, between late July and early August 2023, Muddled Libra successfully circumvented IAM (Identity and Access Management) restrictions by operating the Okta service to access SaaS applications and cloud infrastructure of various organizations.
In addition, if SSO (single sign-on) integration is not supported by the victim's cloud platform, hackers conduct extensive searches to identify CSP credentials, which are often stored in unprotected locations.
The purpose of data collection activities is, in particular, to gain access to Amazon Web Services and Microsoft Azure services, such as AWS IAM, Amazon Simple Storage Service (S3), AWS Secrets Manager, and Azure storage access keys.
Using CSP services and features, including the AWS DataSync and AWS Transfer tools, as well as the disk snapshot technique for moving data from Azure, Muddled Libra can efficiently collect data.
According to Palo Alto Networks, organizations should implement additional authentication, including the use of hardware tokens or biometrics.
Palo Alto Networks Unit 42 reports that the cybercrime group Muddled Libra actively attacks cloud applications and cloud service providers, seeking to steal confidential data.
According to the report, the attackers aim to extract data from SaaS (Software-as-a-Service) applications and CSP (Cloud Service Provider) services, using them for further attacks and extortion. It is noteworthy that the group uses sophisticated social engineering techniques to initially penetrate the target network.
As you know, Muddled Libra skillfully avoids detection, using techniques that allow you to act unnoticed and modify their management methods and techniques to adapt to different victim networks. This includes extortion and data theft.

Priority of hackers actions
One of the features of Muddled Libra tactics is intelligence, the purpose of which is to identify administrative users for further obtaining their passwords under the guise of technical support. Yandex. Metrica also provides an in-depth analysis of the applications and cloud services used by organizations.
Last year, between late July and early August 2023, Muddled Libra successfully circumvented IAM (Identity and Access Management) restrictions by operating the Okta service to access SaaS applications and cloud infrastructure of various organizations.
In addition, if SSO (single sign-on) integration is not supported by the victim's cloud platform, hackers conduct extensive searches to identify CSP credentials, which are often stored in unprotected locations.
The purpose of data collection activities is, in particular, to gain access to Amazon Web Services and Microsoft Azure services, such as AWS IAM, Amazon Simple Storage Service (S3), AWS Secrets Manager, and Azure storage access keys.
Using CSP services and features, including the AWS DataSync and AWS Transfer tools, as well as the disk snapshot technique for moving data from Azure, Muddled Libra can efficiently collect data.
According to Palo Alto Networks, organizations should implement additional authentication, including the use of hardware tokens or biometrics.
