Hackers use loopholes in the API to bypass Android's security measures.
A new study in the field of cybersecurity has revealed the activity of the malicious product "SecuriDropper", which is an implementation of the growing service "dropper-as-a-service" or "DaaS", the meaning of which is to purposefully infect certain devices with malware necessary for an attacker through a special dropper.
SecuriDropper in the iteration reviewed by ThreatFabric experts is aimed at Android smartphones and manages to successfully bypass the security measures introduced by Google and deliver malware to the devices needed by hackers.
Android droppers are used as a means to install secondary malicious code on infected devices, and hackers providing DaaS services can easily be compared to Initial access Brokers (IAB), only in the context of mobile devices. This business is very profitable and is clearly in demand from various cybercrime associations.
ThreatFabric researchers claim that the creators of droppers are constantly evolving, trying to get ahead of the efforts of specialists to strengthen security. So, one of the security measures introduced by Google in Android 13 is the "Restrict access to settings" option, which does not allow applications installed from third-party sources to get access permissions to notifications and the accessibility service. Such permissions are often exploited by banking Trojans.
However, SecuriDropper successfully circumvents these restrictions by using a different API to install malicious code, mimicking the process used by app stores to install new programs. The malware itself is distributed outside of Google Play and is often disguised as popular Google apps, including Chrome and Google Search.
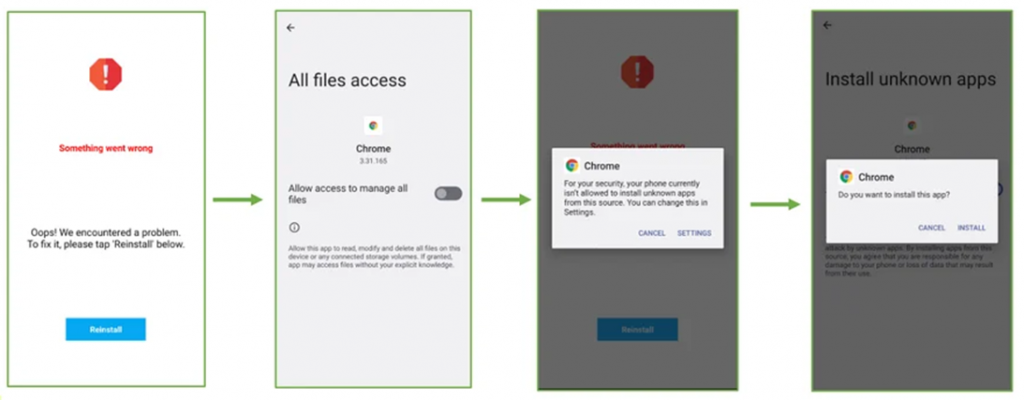
After installing and running the dropper, the user sees a notification that the application is installed incorrectly and needs to be reinstalled. After that, the malware initiates a second installation process, during which the victim is asked to grant the application all necessary access.
ThreatFabric researchers have observed that Android banking Trojans such as Spnote and ERMAC are distributed through SecuriDropper on phishing sites and third-party platforms such as Discord.
In addition to SecuriDropper, researchers have also come across other malware that circumvents the restriction of access to Android settings. One of these malicious programs is Zombinder, which is distributed on cybercrime forums at a price of $ 1,000.
Zombinder got its name due to its feature of "gluing" a legitimate application with the code responsible for installing the payload on an infected device. Basically, Zombiner connects the dropper to a legitimate app.
It is currently unclear if there is any connection between SecuriDropper and Tinder. One thing is clear: as Android continues to raise the security bar with each new version, cybercriminals are also adapting and coming up with ways to circumvent security measures.
"Dropper-as-a-Service platforms are becoming extremely powerful tools that allow attackers to break into target devices to distribute spyware and banking Trojans," ThreatFabric concluded.
A new study in the field of cybersecurity has revealed the activity of the malicious product "SecuriDropper", which is an implementation of the growing service "dropper-as-a-service" or "DaaS", the meaning of which is to purposefully infect certain devices with malware necessary for an attacker through a special dropper.
SecuriDropper in the iteration reviewed by ThreatFabric experts is aimed at Android smartphones and manages to successfully bypass the security measures introduced by Google and deliver malware to the devices needed by hackers.
Android droppers are used as a means to install secondary malicious code on infected devices, and hackers providing DaaS services can easily be compared to Initial access Brokers (IAB), only in the context of mobile devices. This business is very profitable and is clearly in demand from various cybercrime associations.
ThreatFabric researchers claim that the creators of droppers are constantly evolving, trying to get ahead of the efforts of specialists to strengthen security. So, one of the security measures introduced by Google in Android 13 is the "Restrict access to settings" option, which does not allow applications installed from third-party sources to get access permissions to notifications and the accessibility service. Such permissions are often exploited by banking Trojans.
However, SecuriDropper successfully circumvents these restrictions by using a different API to install malicious code, mimicking the process used by app stores to install new programs. The malware itself is distributed outside of Google Play and is often disguised as popular Google apps, including Chrome and Google Search.
After installing and running the dropper, the user sees a notification that the application is installed incorrectly and needs to be reinstalled. After that, the malware initiates a second installation process, during which the victim is asked to grant the application all necessary access.

ThreatFabric researchers have observed that Android banking Trojans such as Spnote and ERMAC are distributed through SecuriDropper on phishing sites and third-party platforms such as Discord.
In addition to SecuriDropper, researchers have also come across other malware that circumvents the restriction of access to Android settings. One of these malicious programs is Zombinder, which is distributed on cybercrime forums at a price of $ 1,000.
Zombinder got its name due to its feature of "gluing" a legitimate application with the code responsible for installing the payload on an infected device. Basically, Zombiner connects the dropper to a legitimate app.
It is currently unclear if there is any connection between SecuriDropper and Tinder. One thing is clear: as Android continues to raise the security bar with each new version, cybercriminals are also adapting and coming up with ways to circumvent security measures.
"Dropper-as-a-Service platforms are becoming extremely powerful tools that allow attackers to break into target devices to distribute spyware and banking Trojans," ThreatFabric concluded.

