Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
North Korea's intelligence goes beyond the peninsula.
According to a report by Rapid7, a new campaign by the North Korean group Kimsuky uses decoy files on the topic of nuclear threats to spread malware.
The campaign aims to gather intelligence on foreign policy, national security, nuclear capabilities, and sanctions on the Korean Peninsula. The attacks target government agencies and think tanks in South Korea, as well as expanding operations to other regions, including the United States and Europe.
Experts report that Kimsuky has updated its tools, starting to use HTML files on the topic of nuclear weapons as bait. Examples of names include: "The escalation model of the nuclear crisis in North Korea and the factors that determine the use of nuclear weapons.html" and "Factors and types of North Korea's use of nuclear weapons.html".
Such decoys, which include files in the Compiled HTML Help (CHM) format, are delivered to victims in ISO, ZIP, RAR, or VHD archives to bypass the first line of defense.
The CHM format, developed by Microsoft, contains a collection of HTML pages along with a table of contents, index, and text search capability, making it easy to document. However, hackers have discovered that CHM can be used to deliver and execute malicious payloads.
When the victim opens the file, a VBScript is executed on the computer, which installs many files .bat and VBS for executing commands and adds entries to the registry for persistence. The collected information, including computer names, OS details, hardware specifications, a list of running processes, the Downloads folder, recent Word files, and directory listings, is sent to the attacker's server.
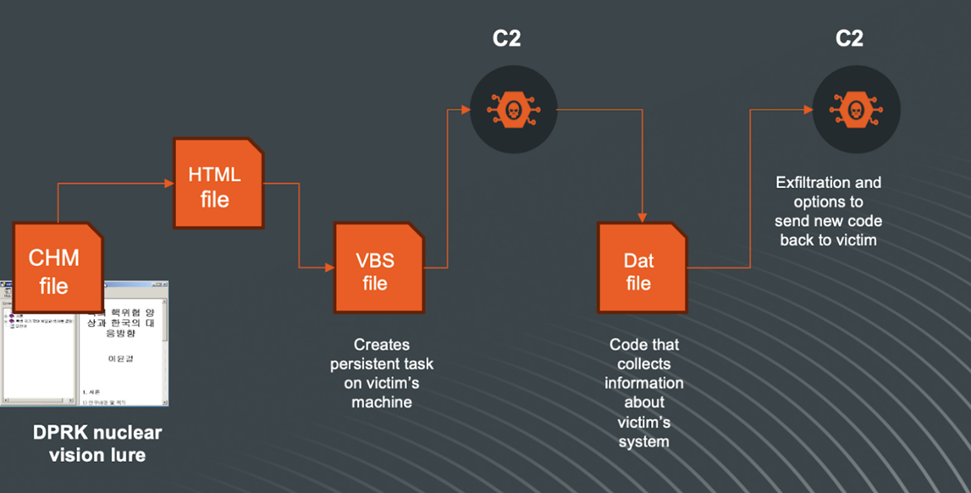
Kimsuky Infection Chain
Researchers note the active use and improvement of Kimsuky techniques for intelligence gathering, emphasizing the dynamism of cyber espionage and the constant arms race between hackers and defenders. The updated Kimsuky arsenal underscores the need to continually strengthen cyber defenses to counter such threats.
According to a report by Rapid7, a new campaign by the North Korean group Kimsuky uses decoy files on the topic of nuclear threats to spread malware.
The campaign aims to gather intelligence on foreign policy, national security, nuclear capabilities, and sanctions on the Korean Peninsula. The attacks target government agencies and think tanks in South Korea, as well as expanding operations to other regions, including the United States and Europe.
Experts report that Kimsuky has updated its tools, starting to use HTML files on the topic of nuclear weapons as bait. Examples of names include: "The escalation model of the nuclear crisis in North Korea and the factors that determine the use of nuclear weapons.html" and "Factors and types of North Korea's use of nuclear weapons.html".
Such decoys, which include files in the Compiled HTML Help (CHM) format, are delivered to victims in ISO, ZIP, RAR, or VHD archives to bypass the first line of defense.
The CHM format, developed by Microsoft, contains a collection of HTML pages along with a table of contents, index, and text search capability, making it easy to document. However, hackers have discovered that CHM can be used to deliver and execute malicious payloads.
When the victim opens the file, a VBScript is executed on the computer, which installs many files .bat and VBS for executing commands and adds entries to the registry for persistence. The collected information, including computer names, OS details, hardware specifications, a list of running processes, the Downloads folder, recent Word files, and directory listings, is sent to the attacker's server.

Kimsuky Infection Chain
Researchers note the active use and improvement of Kimsuky techniques for intelligence gathering, emphasizing the dynamism of cyber espionage and the constant arms race between hackers and defenders. The updated Kimsuky arsenal underscores the need to continually strengthen cyber defenses to counter such threats.

